80386
4.4PROTECTION
4.4.1Protection Concepts
APPLICATIONS
CPU
ENFORCED
SOFTWARE
INTERFACES
HIGH SPEED
OPERATING
SYSTEM
INTERFACE
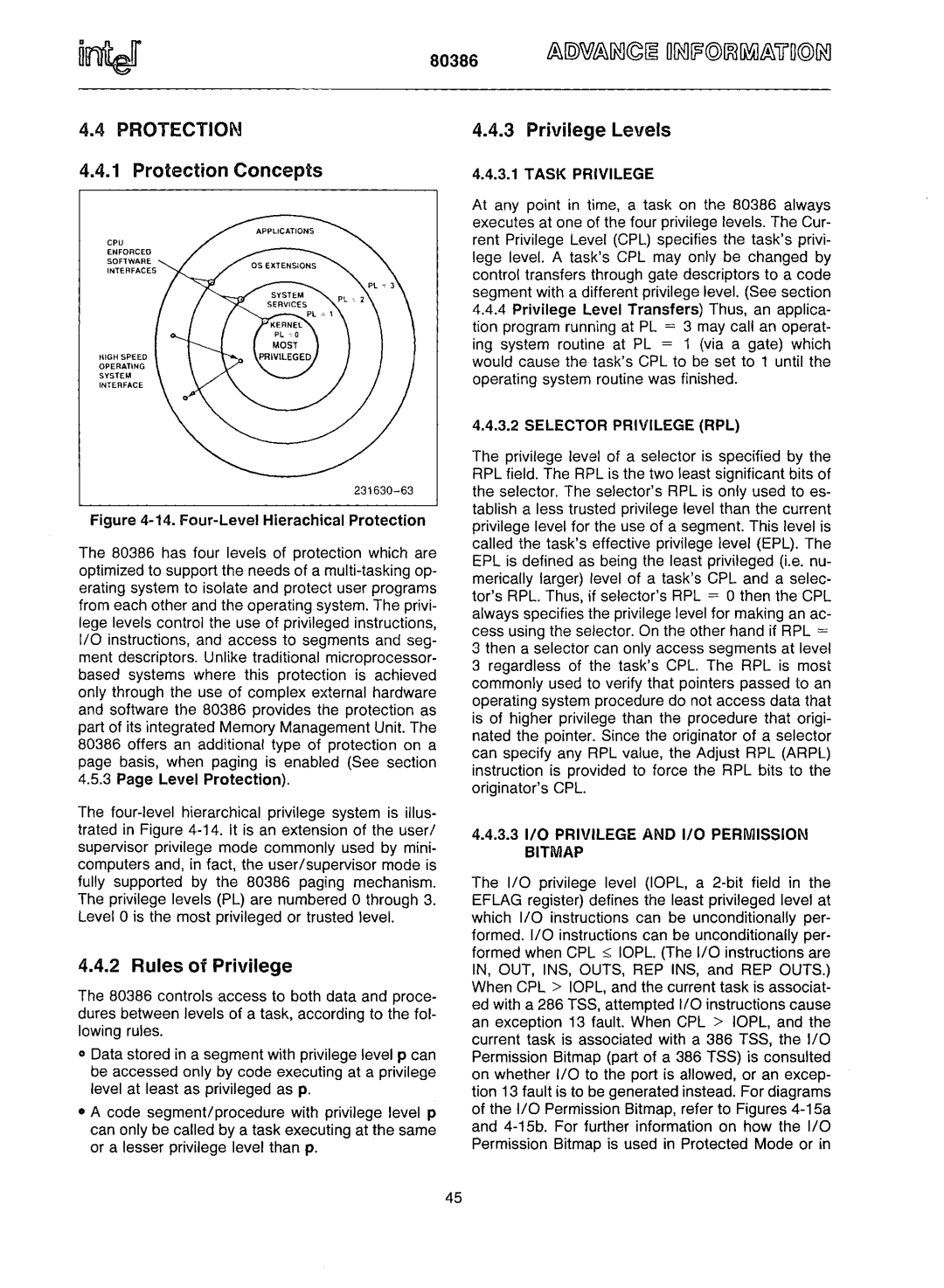
Figure 4-14. Four-Level Hierachical Protection
The 80386 has four levels of protection which are optimized to support the needs of a mUlti-tasking op- erating system to isolate and protect user programs from each other and the operating system. The privi- lege levels control the use of privileged instructions, I/O instructions, and access to segments and seg- ment descriptors. Unlike traditional microprocessor- based systems where this protection is achieved only through the use of complex external hardware and software the 80386 provides the protection as part of its integrated Memory Management Unit. The 80386 offers an additional type of protection on a page basis, when paging is enabled (See section 4.5.3 Page Level Protection).
The four-level hierarchical privilege system is illus- trated in Figure 4-14. It is an extension of the user/ supervisor privilege mode commonly used by mini- computers and, in fact, the user/supervisor mode is fully supported by the 80386 paging mechanism. The privilege levels (PL) are numbered 0 through 3. Level 0 is the most privileged or trusted level.
4.4.2 Rules of Privilege
The 80386 controls access to both data and proce- dures between levels of a task, according to the fol- lowing rules.
oData stored in a segment with privilege level p can be accessed only by code executing at a privilege level at least as privileged as p.
•A code segment/procedure with privilege level p can only be called by a task executing at the same or a lesser privilege level than p.
45
4.4.3 Privilege Levels
4.4_3.1 TASK PRIVILEGE
At any point in time, a task on the 80386 always executes at one of the four privilege levels. The Cur- rent Privilege Level (CPL) specifies the task'sprivi- lege level. A task'sCPL may only be changed by control transfers through gate descriptors to a code segment with a different privilege level. (See section
4.4.4Privilege Level Transfers) Thus, an applica- tion program running at PL = 3 may call an operat- ing system routine at PL = 1 (via a gate) which would cause the task'sCPL to be set to 1 until the operating system routine was finished.
4.4.3.2 SELECTOR PRIVILEGE (RPL)
The privilege level of a selector is specified by the RPL field. The RPL is the two least significant bits of the selector. The selector'sRPL is only used to es- tablish a less trusted privilege level than the current privilege level for the use of a segment. This level is called the task'seffective privilege level (EPL). The EPL is defined as being the least privileged (i.e. nu- merically larger) level of a task'sCPL and a selec- tor'sRPL. Thus, if selector'sRPL = 0 then the CPL always specifies the privilege level for making an ac- cess using the selector. On the other hand if RPL = 3 then a selector can only access segments at level 3 regardless of the task'sCPL. The RPL is most commonly used to verify that pointers passed to an operating system procedure do not access data that is of higher privilege than the procedure that origi- nated the pointer. Since the originator of a selector can specify any RPL value, the Adjust RPL (ARPL) instruction is provided to force the RPL bits to the originator'sCPL.
4.4.3_3 I/O PRIVILEGE AND 1/0 PERMISSION BITMAP
The 110 privilege level (IOPL, a