ProSafe Premium 3 x 3
Table 24. IDS/IPS policies and policy rules (continued)
Policy |
| Description | Policy Rule | |||
|
|
|
|
| Threshold | Notification |
|
|
|
|
|
|
|
Known client |
| • | Detection. Clients that should be connected to the secured | 0 | Trap | |
associating with |
|
| wireless network are instead connected to wireless access |
|
| |
|
| points that are part of an ad hoc network. |
|
| ||
|
| • | Result. Wireless security might be compromised. |
|
| |
|
| • | Solution. The clients are disconnected from the ad hoc |
|
| |
|
|
| network. |
|
| |
AP property |
| • | Detection. Unauthorized changes such as a change of SSID, | 0 | Trap | |
changed |
|
| security settings, or channel are made on a known wireless |
|
| |
|
|
| access point in the network. |
|
| |
|
| • | Result. Wireless security is compromised and clients cannot |
|
| |
|
|
| connect to the wireless access point. |
|
| |
|
| Note: The IDS detects that the properties of a known wireless |
|
| ||
|
| access point in the network are changed, but the IPS does not take |
|
| ||
|
| action. |
|
| ||
|
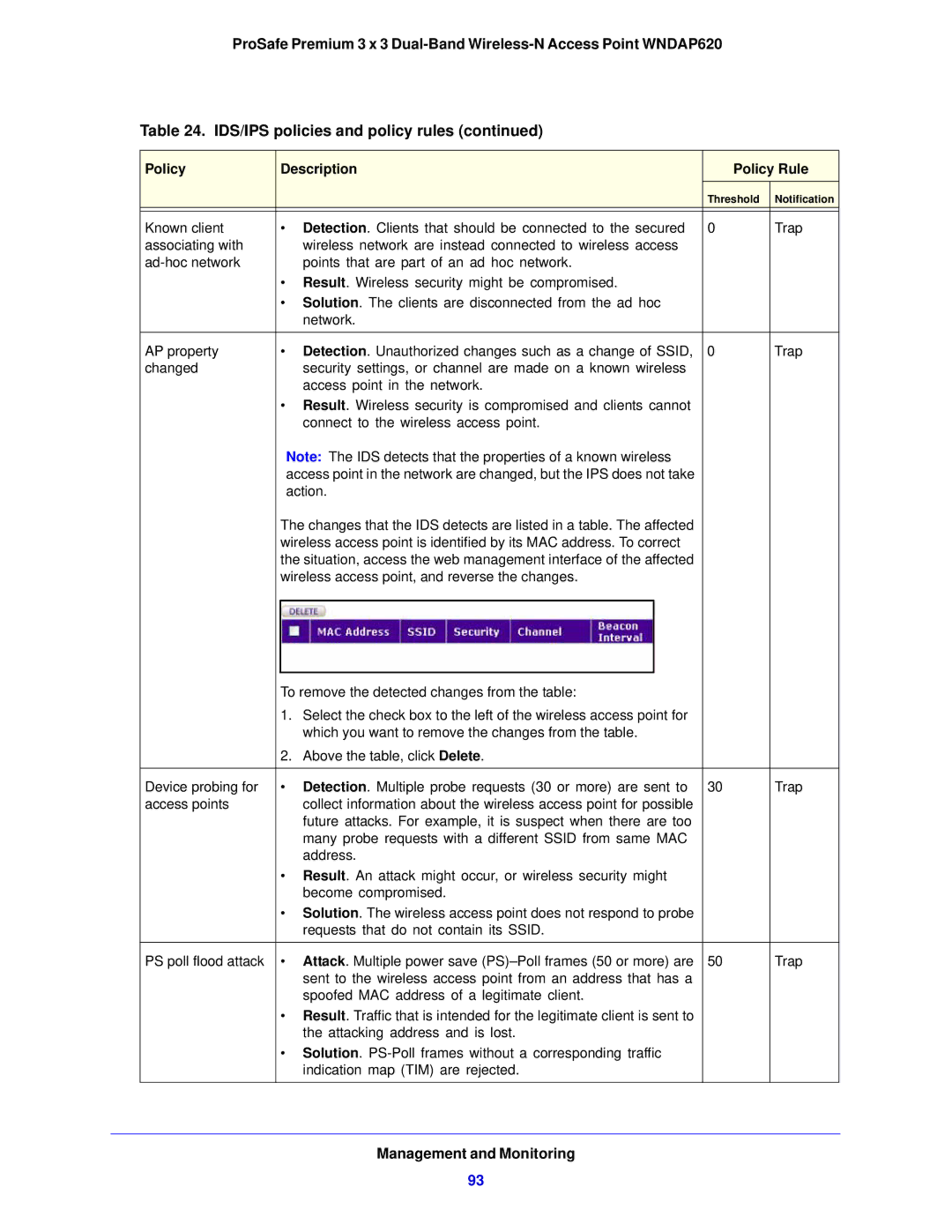
| The changes that the IDS detects are listed in a table. The affected |
|
| ||
|
| wireless access point is identified by its MAC address. To correct |
|
| ||
|
| the situation, access the web management interface of the affected |
|
| ||
|
| wireless access point, and reverse the changes. |
|
| ||
|
|
|
|
|
| |
|
|
|
|
|
| |
|
| To remove the detected changes from the table: |
|
| ||
| 1. | Select the check box to the left of the wireless access point for |
|
| ||
|
|
| which you want to remove the changes from the table. |
|
| |
| 2. | Above the table, click Delete. |
|
| ||
|
|
|
|
|
|
|
Device probing for |
| • | Detection. Multiple probe requests (30 or more) are sent to | 30 | Trap | |
access points |
|
| collect information about the wireless access point for possible |
|
| |
|
|
| future attacks. For example, it is suspect when there are too |
|
| |
|
|
| many probe requests with a different SSID from same MAC |
|
| |
|
|
| address. |
|
| |
|
| • | Result. An attack might occur, or wireless security might |
|
| |
|
|
| become compromised. |
|
| |
|
| • | Solution. The wireless access point does not respond to probe |
|
| |
|
|
| requests that do not contain its SSID. |
|
| |
PS poll flood attack |
| • | Attack. Multiple power save | 50 | Trap | |
|
|
| sent to the wireless access point from an address that has a |
|
| |
|
|
| spoofed MAC address of a legitimate client. |
|
| |
|
| • | Result. Traffic that is intended for the legitimate client is sent to |
|
| |
|
|
| the attacking address and is lost. |
|
| |
|
| • | Solution. |
|
| |
|
|
| indication map (TIM) are rejected. |
|
| |
Management and Monitoring
93