5.3.2.5. Configure HPSS Security Services
This section describes the procedure to configure a Kerberos or UNIX Security Client on the secondary subsystem machine. The security client must match the security mechanism on the root machine.
To configure the security client for the secondary subsystem machine, perform the following steps:
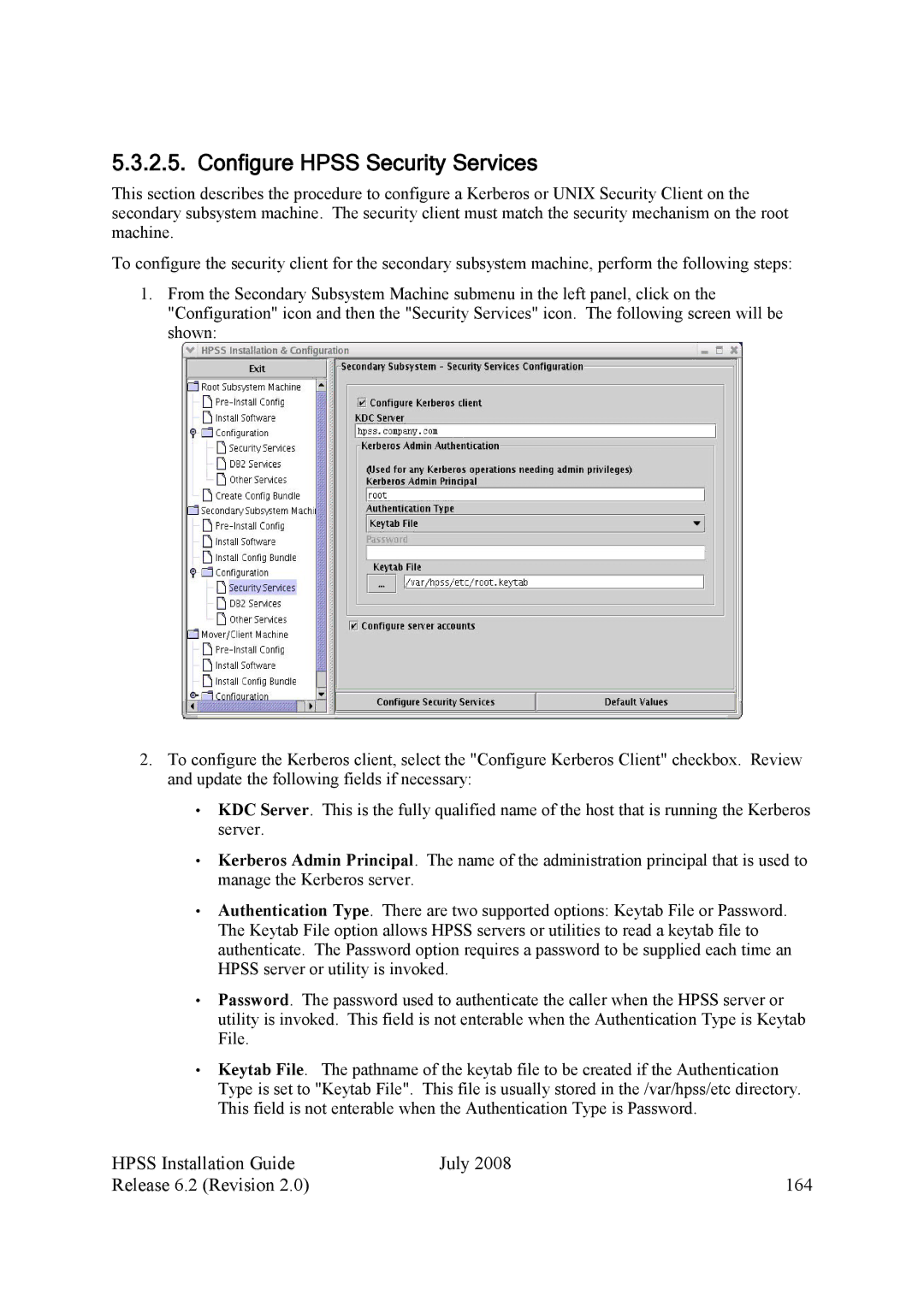
1.From the Secondary Subsystem Machine submenu in the left panel, click on the "Configuration" icon and then the "Security Services" icon. The following screen will be shown:
2.To configure the Kerberos client, select the "Configure Kerberos Client" checkbox. Review and update the following fields if necessary:
•KDC Server. This is the fully qualified name of the host that is running the Kerberos server.
•Kerberos Admin Principal. The name of the administration principal that is used to manage the Kerberos server.
•Authentication Type. There are two supported options: Keytab File or Password. The Keytab File option allows HPSS servers or utilities to read a keytab file to authenticate. The Password option requires a password to be supplied each time an HPSS server or utility is invoked.
•Password. The password used to authenticate the caller when the HPSS server or utility is invoked. This field is not enterable when the Authentication Type is Keytab File.
•Keytab File. The pathname of the keytab file to be created if the Authentication Type is set to "Keytab File". This file is usually stored in the /var/hpss/etc directory. This field is not enterable when the Authentication Type is Password.
HPSS Installation Guide | July 2008 |
Release 6.2 (Revision 2.0) | 164 |