Step 6: Configure WLAN Security
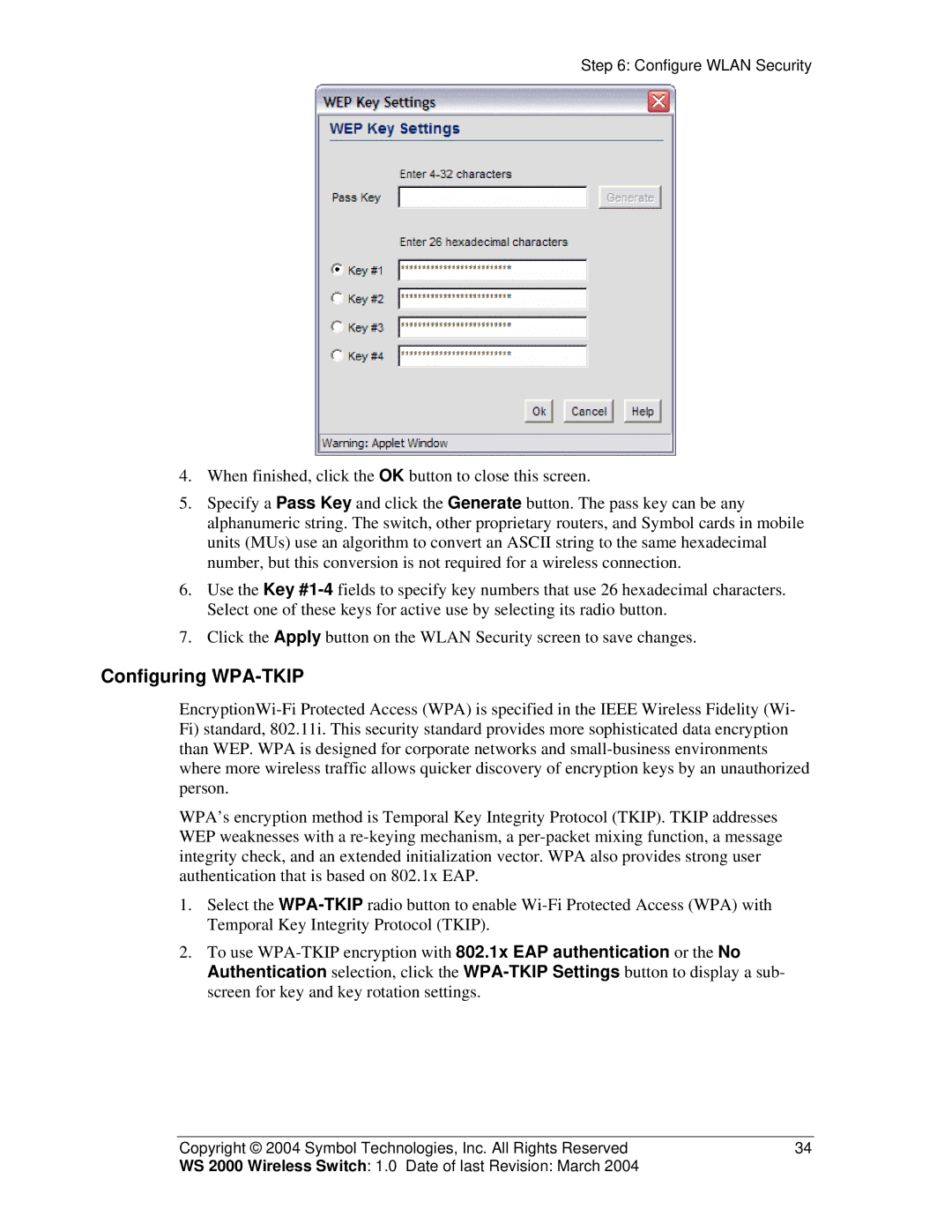
4.When finished, click the OK button to close this screen.
5.Specify a Pass Key and click the Generate button. The pass key can be any alphanumeric string. The switch, other proprietary routers, and Symbol cards in mobile units (MUs) use an algorithm to convert an ASCII string to the same hexadecimal number, but this conversion is not required for a wireless connection.
6.Use the Key #1-4fields to specify key numbers that use 26 hexadecimal characters. Select one of these keys for active use by selecting its radio button.
7.Click the Apply button on the WLAN Security screen to save changes.
Configuring WPA-TKIP
EncryptionWi-Fi Protected Access (WPA) is specified in the IEEE Wireless Fidelity (Wi- Fi) standard, 802.11i. This security standard provides more sophisticated data encryption than WEP. WPA is designed for corporate networks and small-business environments where more wireless traffic allows quicker discovery of encryption keys by an unauthorized person.
WPA’s encryption method is Temporal Key Integrity Protocol (TKIP). TKIP addresses WEP weaknesses with a re-keying mechanism, a per-packet mixing function, a message integrity check, and an extended initialization vector. WPA also provides strong user authentication that is based on 802.1x EAP.
1.Select the WPA-TKIPradio button to enable Wi-Fi Protected Access (WPA) with Temporal Key Integrity Protocol (TKIP).
2.To use WPA-TKIP encryption with 802.1x EAP authentication or the No Authentication selection, click the WPA-TKIP Settings button to display a sub- screen for key and key rotation settings.