Configure Employee Access Services 63
Configure Attributes on the RADIUS Server To authenticate users, you will need to configure users either in the local database or on RADIUS servers. To configure services for Employee access, the following items should be configured on the RADIUS server.
To configure the RADIUS server:
1Configure RADIUS server to perform 802.1X using the recommended EAP method PEAP + MS ChapV2.
2Setup each WX switch as a RADIUS client.
3Define any desired 3Com
The
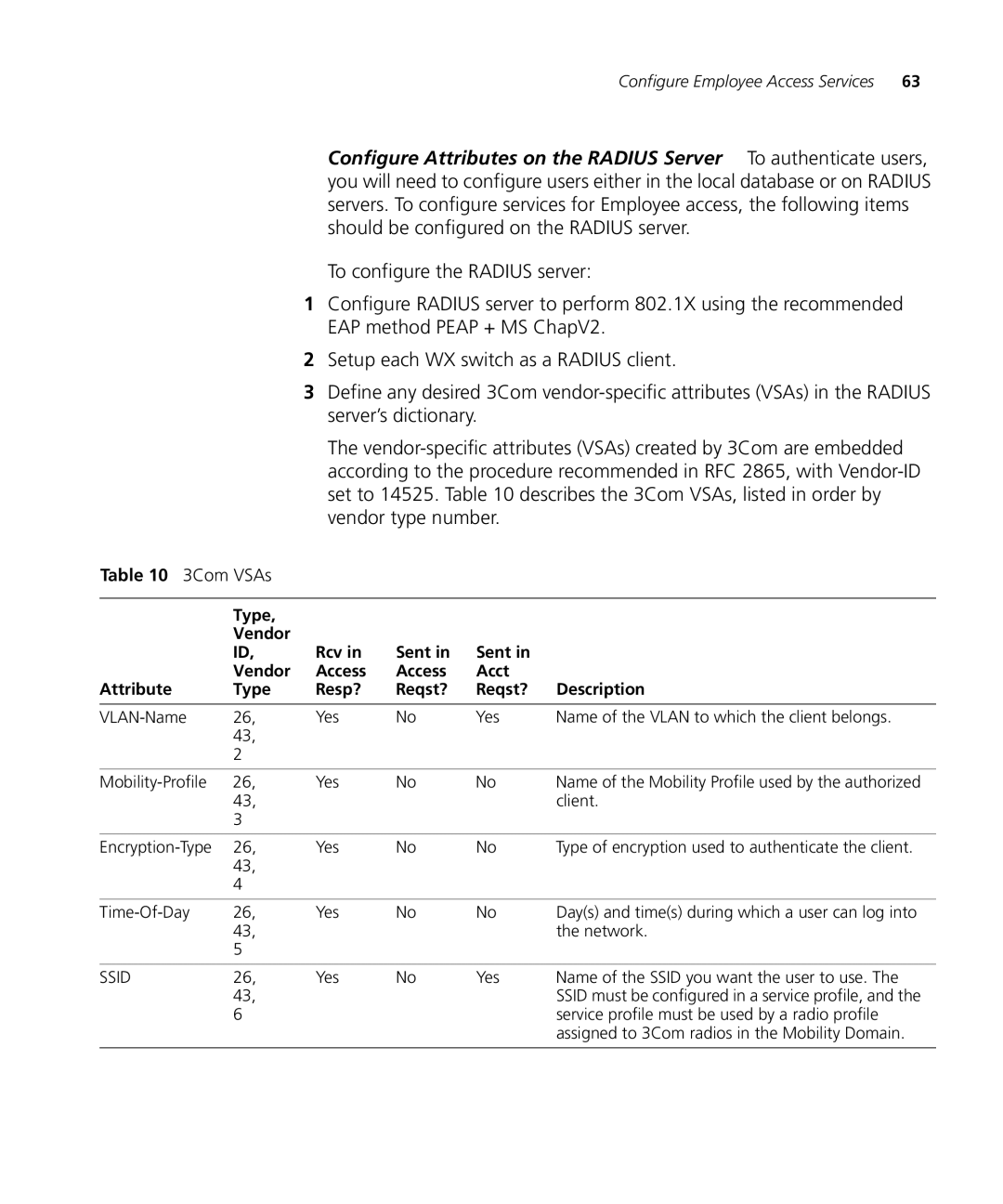
Table 10 3Com VSAs
| Type, |
|
|
|
|
| Vendor |
|
|
|
|
| ID, | Rcv in | Sent in | Sent in |
|
| Vendor | Access | Access | Acct |
|
Attribute | Type | Resp? | Reqst? | Reqst? | Description |
|
|
|
|
|
|
26, | Yes | No | Yes | Name of the VLAN to which the client belongs. | |
| 43, |
|
|
|
|
| 2 |
|
|
|
|
|
|
|
|
|
|
26, | Yes | No | No | Name of the Mobility Profile used by the authorized | |
| 43, |
|
|
| client. |
| 3 |
|
|
|
|
|
|
|
|
|
|
26, | Yes | No | No | Type of encryption used to authenticate the client. | |
| 43, |
|
|
|
|
| 4 |
|
|
|
|
|
|
|
|
|
|
26, | Yes | No | No | Day(s) and time(s) during which a user can log into | |
| 43, |
|
|
| the network. |
| 5 |
|
|
|
|
|
|
|
|
|
|
SSID | 26, | Yes | No | Yes | Name of the SSID you want the user to use. The |
| 43, |
|
|
| SSID must be configured in a service profile, and the |
| 6 |
|
|
| service profile must be used by a radio profile |
|
|
|
|
| assigned to 3Com radios in the Mobility Domain. |
|
|
|
|
|
|