When you leave the domain (that is, disable Active Directory authentication and disconnect a pool or server from its domain), any users who authenticated to the pool or server with Active Directory credentials are disconnected.
Use XenCenter to leave an AD domain. See the XenCenter help for more information. Alternately run the
Note:
Leaving the domain will not cause the host objects to be removed from the AD database. See this knowledge base article for more information about this and how to remove the disabled host entries.
Role Based Access Control
Note:
The full RBAC feature is only available in Citrix XenServer Enterprise Edition or higher. To learn more about upgrading XenServer, click here.
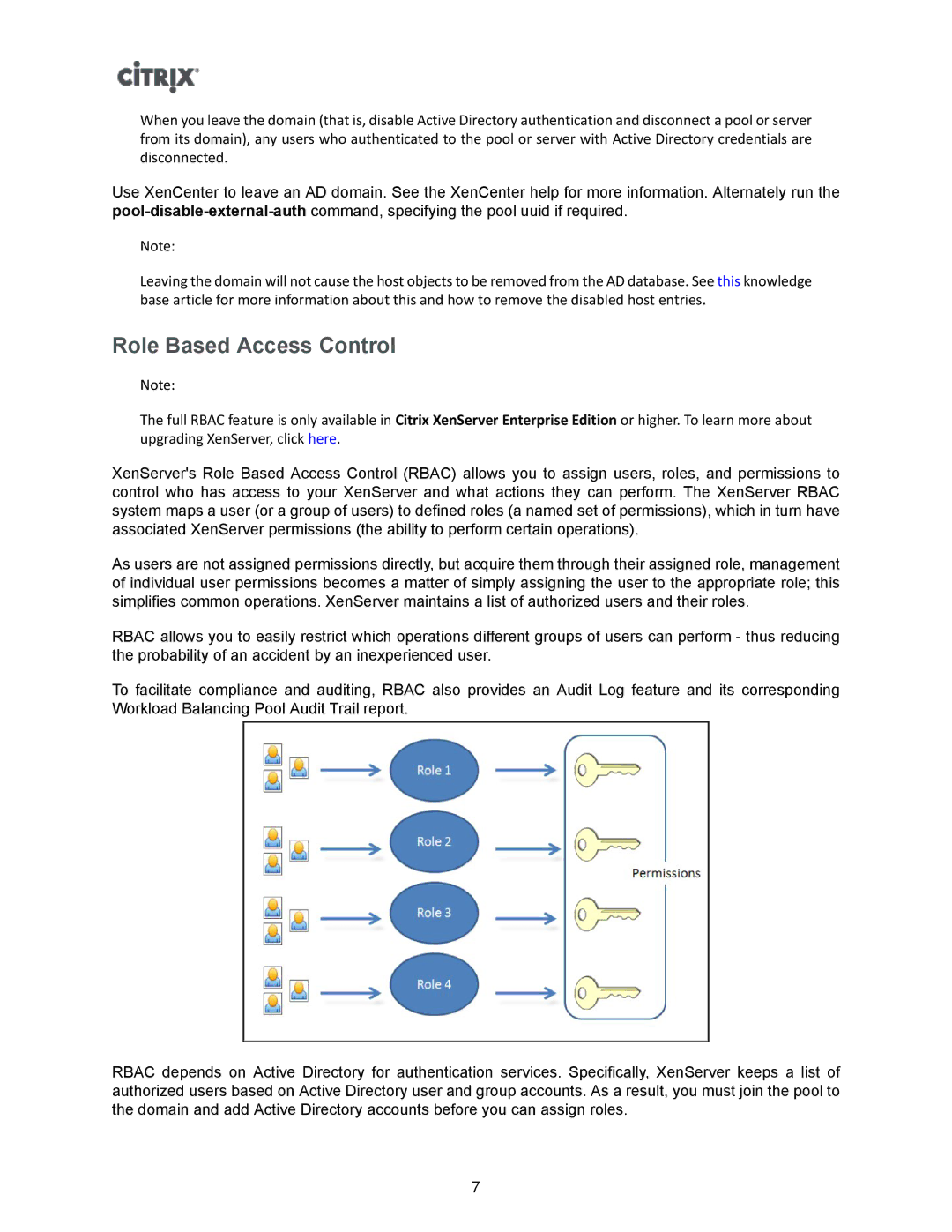
XenServer's Role Based Access Control (RBAC) allows you to assign users, roles, and permissions to control who has access to your XenServer and what actions they can perform. The XenServer RBAC system maps a user (or a group of users) to defined roles (a named set of permissions), which in turn have associated XenServer permissions (the ability to perform certain operations).
As users are not assigned permissions directly, but acquire them through their assigned role, management of individual user permissions becomes a matter of simply assigning the user to the appropriate role; this simplifies common operations. XenServer maintains a list of authorized users and their roles.
RBAC allows you to easily restrict which operations different groups of users can perform - thus reducing the probability of an accident by an inexperienced user.
To facilitate compliance and auditing, RBAC also provides an Audit Log feature and its corresponding Workload Balancing Pool Audit Trail report.
RBAC depends on Active Directory for authentication services. Specifically, XenServer keeps a list of authorized users based on Active Directory user and group accounts. As a result, you must join the pool to the domain and add Active Directory accounts before you can assign roles.
7