FDDI Applications
The following table summarizes the FDDI connection rules:
!
CAUTION
Table
| A | B | S | M |
|
|
|
|
|
A | V, U | V | V, U | V, P |
|
|
|
|
|
B | V | V, U | V, U | V, P |
|
|
|
|
|
S | V, U | V, U | V | V |
|
|
|
|
|
M | V | V | V | X |
|
|
|
|
|
V – valid connection X – illegal connection
U – undesirable (but legal) connection
P – valid, but when both A and B are connected to M ports (a
Though technically legal under FDDI connection rules, undesirable connections will cause a twisted or wrapped ring.
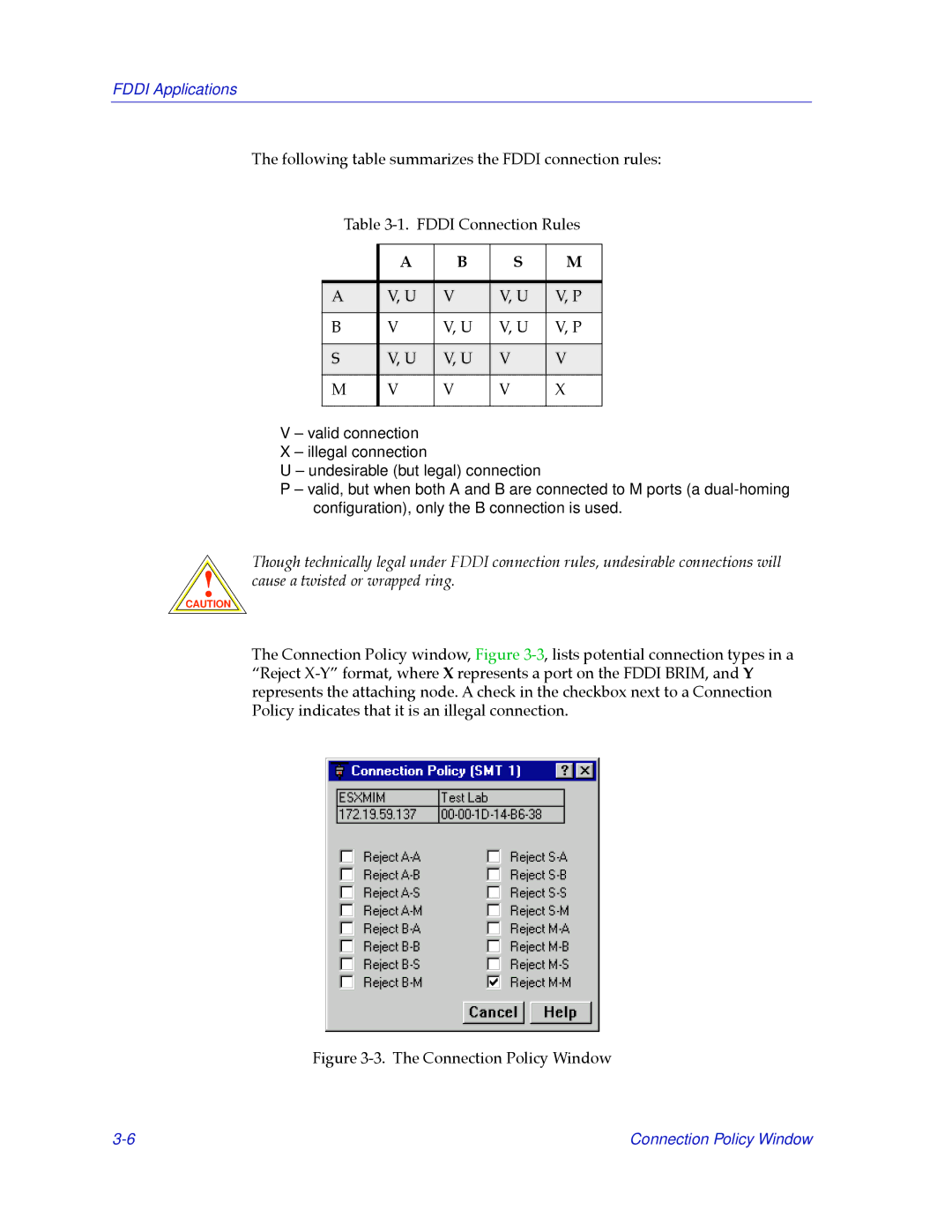
The Connection Policy window, Figure
Figure 3-3. The Connection Policy Window
Connection Policy Window |