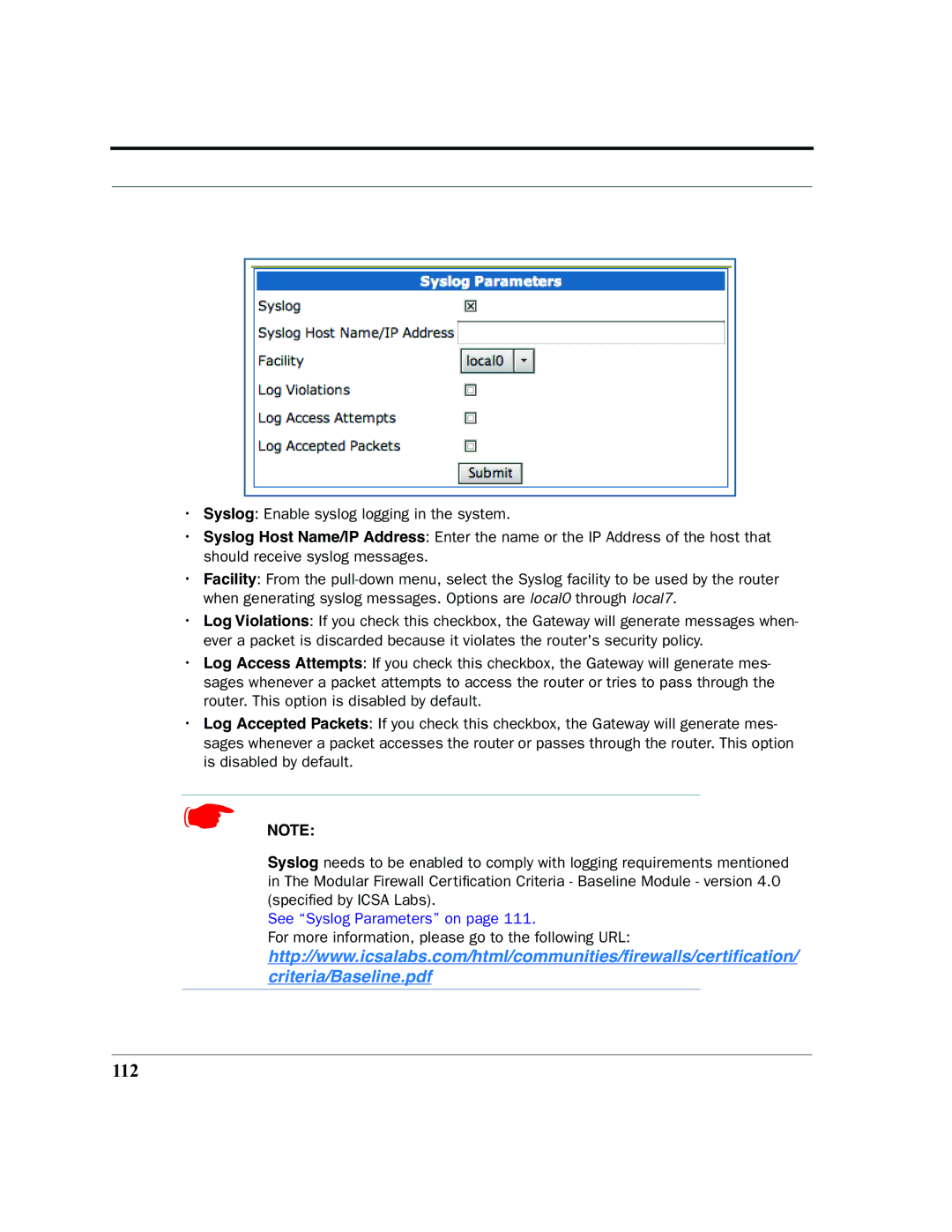
•Syslog: Enable syslog logging in the system.
•Syslog Host Name/IP Address: Enter the name or the IP Address of the host that should receive syslog messages.
•Facility: From the
•Log Violations: If you check this checkbox, the Gateway will generate messages when- ever a packet is discarded because it violates the router's security policy.
•Log Access Attempts: If you check this checkbox, the Gateway will generate mes- sages whenever a packet attempts to access the router or tries to pass through the router. This option is disabled by default.
•Log Accepted Packets: If you check this checkbox, the Gateway will generate mes- sages whenever a packet accesses the router or passes through the router. This option is disabled by default.
☛NOTE:
Syslog needs to be enabled to comply with logging requirements mentioned in The Modular Firewall Certification Criteria - Baseline Module - version 4.0 (specified by ICSA Labs).
See “Syslog Parameters” on page 111.
For more information, please go to the following URL: http://www.icsalabs.com/html/communities/firewalls/certification/ criteria/Baseline.pdf