Installation User’s Guide
Page
Contents
Configuring 802.11g Radio Inbound Filters
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Appendix C
Preface
Document Conventions
Where to Find Web-based Guides
Management Software Updates
Contacting Allied Telesyn
Getting Started
Chapter
Getting Started
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Access Point Architecture
Https
Feature AT-WA7500 AT-WA7501
Ttls
What’s New for Software Releases 2.3?
Description
Understanding the LEDs
Icon
AT-WA7500 LEDs
Understanding the Ports
Port Description
10BaseT/100BaseTx Ethernet port Serial port
Access Point Environment
How the Access Point Fits in Your Network
Using One Access Point in a Simple Wireless Network
Screen
Example Configuring an 802.11g Access Point
Access Point
Using Multiple Access Points Roaming Wireless End Devices
Multiple Access Points with Roaming End Devices
11g Access Point with Roaming End Devices
Radio
Using an Access Point as a WAP
Screen Parameter
Radio Root
Access Point as a WAP
AT-WA7500 and AT-WA7501 Installation and User’s Guide
11g WAP with No Roaming End Devices
Screen Parameter 802.11g Radio-2
Example Configuring an 802.11a WAP With Roaming End Devices
WAP 802.11b
Using Access Points to Create a Point-to-Point Bridge
Screen Parameter Access Point WAP 802.11a
With access points that are acting as point-to-point bridges
Getting Started
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Example Configuring an 802.11g Point-to-Point Bridge
11g Bridge
Bridge
Bridge Secondary Screen Parameter Primary LAN
Example Configuring an 802.11a Point-to-Multipoint Bridge
Using Dual Radio Access Points for Redundancy
Configuring the Access Point Setting the IP Address
Using the ATI AT-WA7500 Configuration Wizard
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Using a Communications Program
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Using a Web Browser Interface
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Using a Telnet Session
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Saving Configuration Changes
Configuration File Description
Browser Interface
This screen appears
Using a Telnet Session
Installing the Access Points
Installation Guidelines
Microwave Ovens Cordless Telephones
Other Access Points
Installing the AT-WA7501
Connecting the AT-WA7501 to Your Wired LAN
Connecting the AT-WA7501 to Power
Installing the AT-WA7500
Connecting the AT-WA7500 to Your Wired LAN and Power
Connecting to Your Fiber Optic Network
Using Purchasing Required Patch Cord Adapter
Connecting to an MT-RJ Network
Connecting to an SC Network
Connecting to an ST Network
Female MT-RJ connector ST connector ST adapter
Connecting Power Over Ethernet
External Antenna Placement Guidelines
Location Recommended Antenna Separation
Positioning Antennas for Dual Radio Access Points
Positioning Antennas for Antenna Diversity
Stacked Antenna Positioning for Dual Radio Access Points
About Antenna Diversity for 802.11g Radios
About Antenna Diversity for 802.11b Radios
About Antenna Diversity for 802.11a Radios
Configuring the Ethernet Network
Configuring the TCP/IP Settings
Parameter Explanation
ABC.XYZ.COM
Configuring Access Point as a Dhcp Client
ABC.UVW.COM
Configuring the Ethernet Network
Parameter Explanation
Only Use Access Point Dhcp Server Access
Configuring Access Point as a Dhcp Server
Use Any Available Dhcp Server Access points
Parameter Explanation
Parameter Explanation
Parameter Explanation
Supported Dhcp Server Options
Unsupported Dhcp Server Options
About Network Address Translation NAT
Configuring Access Point to Send ARP Requests
Configuring Other Ethernet or Fiber Optic Settings
Ethernet Parameter Descriptions
Configuring Ethernet Address
Configuring Ethernet Filters
Using Ethernet Frame Type Filters
AT-WA7500 and AT-WA7501 Installation and User’s Guide
Frame Type Explanation
Using Predefined Subtype Filters Customizing Subtype Filters
SubType Value
Example
Filter Parameter Value Explanation
Configuring Advanced Filters
Setting Filter Values
Dhcp
Setting Filter Expressions
Parameter Explanation
Example
Value ID Description
Parameter Value Explanation
Check for a DIX IP frame
Parameter Value Explanation
Parameter Value Explanation
Parameter Value Explanation
Configuring the Radios
802.11a Independent
Access Radio Supported Dual Point 802.11g
About the Radios
Configuring the 802.11g Radio
Parameter Explanation
Enter a unique Ssid for each enabled service
Channel
France Japan Israel
Configuring 802.11g Radio Advanced Parameters
Parameter Description
104
105
106
Configuring 802.11g Radio Inbound Filters
Applying Hot Settings
WTP
109
Configuring the 802.11b Radio
11b Radio Parameter Descriptions
Configuring 802.11b Radio Advanced Parameters
113
‘ANY’
Configuring 802.11b Radio Inbound Filters
SVP
Number of Phones
Configuring a SpectraLink Network
Number
Supported Voice Supported Voice and Data
118
Configuring the 802.11a Radio
120
121
Enter a unique Ssid for each service set. You
Worldwide Frequencies for the 802.11a Radio
Configuring 802.11a Radio Advanced Parameters
125
Configuring 802.11a Radio Inbound Filters
127
128
Configuring the Spanning Tree
About the Access Point Spanning Tree
About Primary LAN Root Access Point
Wireless Secondary LANs Remote IP Subnets
About Secondary LANs Designated Bridges
133
About Ethernet Bridging/Data Link Tunneling
About Routable Non Network Protocols
Configuring the Spanning Tree Parameters
Vlan
138
139
About IP Tunnels
AP4
Creating IP Tunnels
ˆ DIX ARP ˆ Icmp
Using One IP Multicast Address for Multiple IP Tunnels
How Frames Are Forwarded Through IP Tunnels
Outbound Frames
Inbound Frames
Frame Types That Are Never Forwarded
Configuring IP Tunnels
Configuring the IP Address List
Iapp
Configuring IP Tunnel Filters
Using IP Tunnel Frame Type Filters
151
152
Using Predefined Subtype Filters
Customizing Subtype Filters
154
155
Filter Examples
Example
158
159
Igmp
Issue IP Tunneling Mobile IP
Comparing IP Tunnels to Mobile IP
161
Configuring Global Parameters
Configuring Global Flooding
163
164
Configuring Global RF Parameters
166
167
168
Configuring Security
Understanding Security
171
172
173
ˆ Tftp
Controlling Access to Access Point Menus
Enabling Access Methods
175
176
Configuring the Access Point to Use a Password Server
Changing the Default Login
179
Password Parameter Descriptions
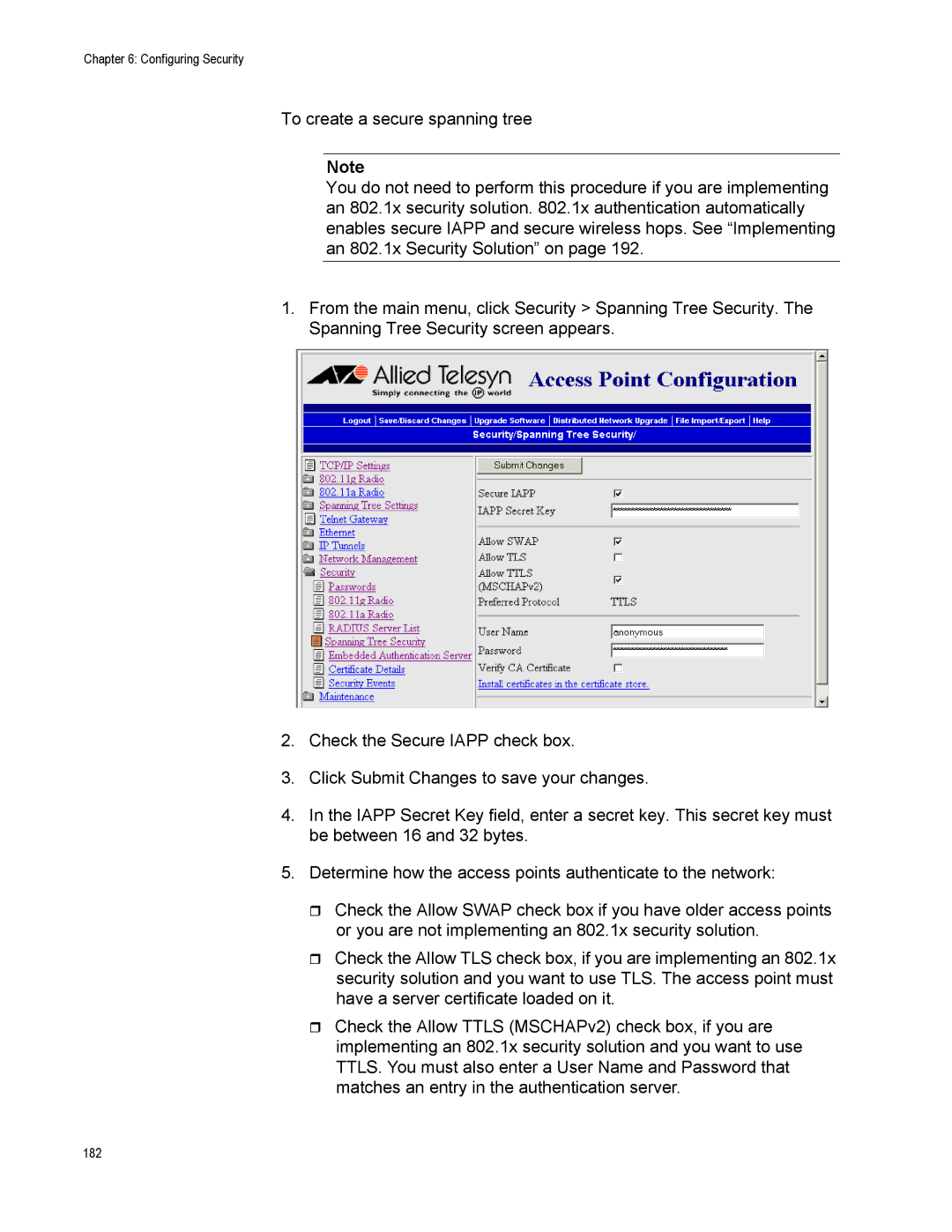
Creating a Secure Spanning Tree
182
183
Using an Access Control List
ACL
185
186
Configuring VLANs
188
Configuring WEP 64/128/152 Security
190
191
Implementing an 802.1x Security Solution
Configuring the Access Point as an Authenticator
194
195
When the Access Point Is the Authenticator
Enabling Secure Communications Between Access Points
When the Access Point Is the Supplicant
Configuring Spanning Tree Security
198
Configuring Wi Fi Protected Access WPA Security
200
201
Configuring WPA PSK Security
Configuring WPA 802.1x Security
Configuring the Embedded Authentication Server EAS
About the Embedded Authentication Server EAS
Type of Radius Server Maximum Authentications
About Certificates
Server
Viewing the Certificates Installed on an Access Point
Installing Uninstalling Certificates
209
Configuring the EAS
211
Configuring the Database
213
ACL
Type Field Description User Name Password
Radius
MAC
TLS
Using the Rejected List
Peap
TTLS/MSCHAP, TTLS/MSCHAP-V2, PEAP/MSCHAP
Adding Entries to the Database
Column Description
NAS IP
Exporting Importing Databases
Clearing the Rejected List
218
219
Managing, Troubleshooting, and Upgrading Access Points
Component Description
Managing the Access Points
Using Wavelink Avalanche Client Management System
Configuring Your Access Points to Use Avalanche
223
Managing Your Access Points Using Avalanche
Important Information When Using Avalanche
Using Simple Network Management Protocol Snmp
227
Maintaining the Access Points
Viewing AP Connections
Display Field Description
230
Viewing AP Neighbors
Displays the Ssid advertised in the beacon. This
233
Viewing Port Statistics
Viewing Dhcp Status
Viewing the Events Log
Viewing About This Access Point Screen
Using the LEDs to Locate Access Points
Restoring the Access Point to the Default Configuration
Troubleshooting the Access Points
Using Configuration Error Messages
Configuration Error Message Additional Information
242
243
244
Troubleshooting With the LEDs
General Troubleshooting
Problem/Question Possible Solution/Answer
247
248
249
250
Using a Communications Program or a Telnet Session
Troubleshooting the Radios
Using LEDs
Using Radio MAC Ping 802.11g and 802.11b Radios
Error Message Explanation
253
Using Icmp Echo
Troubleshooting Security
Viewing the Security Events Log
256
General Security Troubleshooting
Exporting the Security Events Log
Recovering a Failed Access Point
Using a Windows NT4/2000/XP PC
Arp -dIPaddress
Upgrading the Access Points
Troubleshooting the Upgrade
Additional Access Point Features
Understanding the Access Point Segments
Understanding Transparent Files
Entering the AP Monitor
Using the AP Monitor
Using AP Monitor Commands
267
Using Content Addressable Memory CAM Mode Commands
Using Test Mode Commands
Using Service Mode Commands
Syntax FB bootsegment datasegment
FB IB ID
Fdel
FFR
275
Using Command Console Mode
Entering Command Console Mode
Using the Commands
To delete the file FILE.DAT from the memory card, enter
Using Tftp Commands
Script
Tftp GET
Tftp PUT
Tftp Server LOG
Tftp Server Stop
Sdvars set scriptfilename
Using sdvars Commands
Sdvars set serveripaddress
Sdvars set starttime
Sdvars set checkpoint
Sdvars set terminate
Sdvars set setactivepointers
Sdvars set nextpoweruptime
Creating Script Files
New Sample Script for Upgrading an Access Point
Sample script file for upgrading an access point
289
Legacy Sample Script for Upgrading Any Access Point
Copying Files To and From the Access Point
Importing or Exporting an
EAS Radius Database File
Transferring Files Using Your Web Browser
Viewing Copying Files Using Your Web Browser
Transferring Files to and from a Tftp Server
Automatically Upgrading Software
Starting or Stopping the Tftp Server
297
Specifications
Appendix a
AT-7500 Access Point
CSMA/CD
AT-7501 Access Point
MT-RJ
301
Ieee 802.11b
Radio Specifications
Ieee 802.11g
DQPSK, Dbpsk
Ieee 802.11a
304
Default Settings
Appendix B
TCP/IP Settings Menu Defaults
Parameter Range Default Your Site? Name
307
Dhcp Server Setup Menu Defaults
Ieee 802.11g Radio Menu Defaults
Parameter Name Range Default Your Site?
310
Ieee 802.11b Radio Menu Defaults
Allow Check/Clear SpectraLink Voice Protocol
Ieee 802.11a Radio Menu Defaults
314
Spanning Tree Settings Menu Defaults
Global Flooding Menu Defaults
Global RF Parameters Menu Defaults
RFC1042/DIX
Through Two sets Hexadecimal Pairs Through FF
Telnet Gateway Configuration Menu Defaults
Ethernet Configuration Menu Defaults
Ethernet Advanced Filters Menu Defaults
EQ, NE, GT, LE
NNL
IP Tunnels Menu Defaults
Tunnels Filter Menu Defaults
Snap -IP-UDP
DIX-IP-TCP
SNAP-IP-TCP
Network Management Menu Defaults
Instant On Menu Defaults
Security Menu Defaults
Passwords Menu Defaults
ACL Radius
Ieee 802.11 g, b Or a Radio Security Menu Defaults
Range Default Your Site? Name
WPA/PSK
Tkip
Ascii
Acsii
WEP, Tkip
Radius Server List Menu Defaults Spanning Tree Security Menu
SWAP/TLS Ttls
Embedded Authentication Server Menu Defaults
Bfsk Binary Frequency Shift Key
ARP Address Resolution Protocol cache
Appendix C
Broadcast
Designated bridge
Dhcp Dynamic Host Configuration Protocol
EAP Extensible Authentication Protocol
Directional antenna
Flooding
Iapp Inter Access Point Protocol
Ethernet bridging
Hello period
IP subnet
Igmp Internet Group Management Protocol
IP router
IP tunneling
Non-bridging secondary LAN
Multicast address
NAT Network Address Translation
Omni antenna
Point-to-point bridge
Power bridge
Root access point
Primary bridging
Root IP subnet
Service set
Root port
Secondary bridging
Splitter
Swap Secure Wireless Authentication Protocol
Spanning tree
Telnet Gateway
Wireless bridge
WAP Wireless Access Point
WEP Wired Equivalent Privacy encryption
Wireless hop
WPA Wi-Fi Protected Access