1 DNSSEC
DNSSEC
DNSSEC (Domain Name System Security Extensions) is a set of extensions that provide DNS resolvers origin authentication of DNS data, data integrity and authenticated denial of existence. It protects DNS resolvers from forged DNS data (from cache poisoning, etc.). DNSSEC does not provide confidentiality.
With DNSSEC, the responses are signed using public key cryptography. In addition to the answer RRsets, the response contains a RRSIG record which is an encrypted digital signature for the RRset. A DNSSEC aware client (resolver) sets the DO (DNSSEC OK) bit in the EDNS OPT section to indicate that it prefers DNSSEC signed responses. If the DO bit is set and if the server is DNSSEC capable, it copies the OPT section (including the DO bit) to the response and includes the DNSSEC signatures for each RRset in the response. The resolver can validate this signature by obtaining the public key of the ADNS server as a DNSKEY record.
Because the DO bit in EDNS is used to indicate DNSSEC responses and because the responses are in general larger due to the RRSIG records, a DNSSEC capable server (and the ServerIron ADX) must support EDNS and packet sizes of up to 4k. Also, if there are intermediate firewalls that drop fragmented UDP traffic, we'd have more resolvers retrying with TCP.
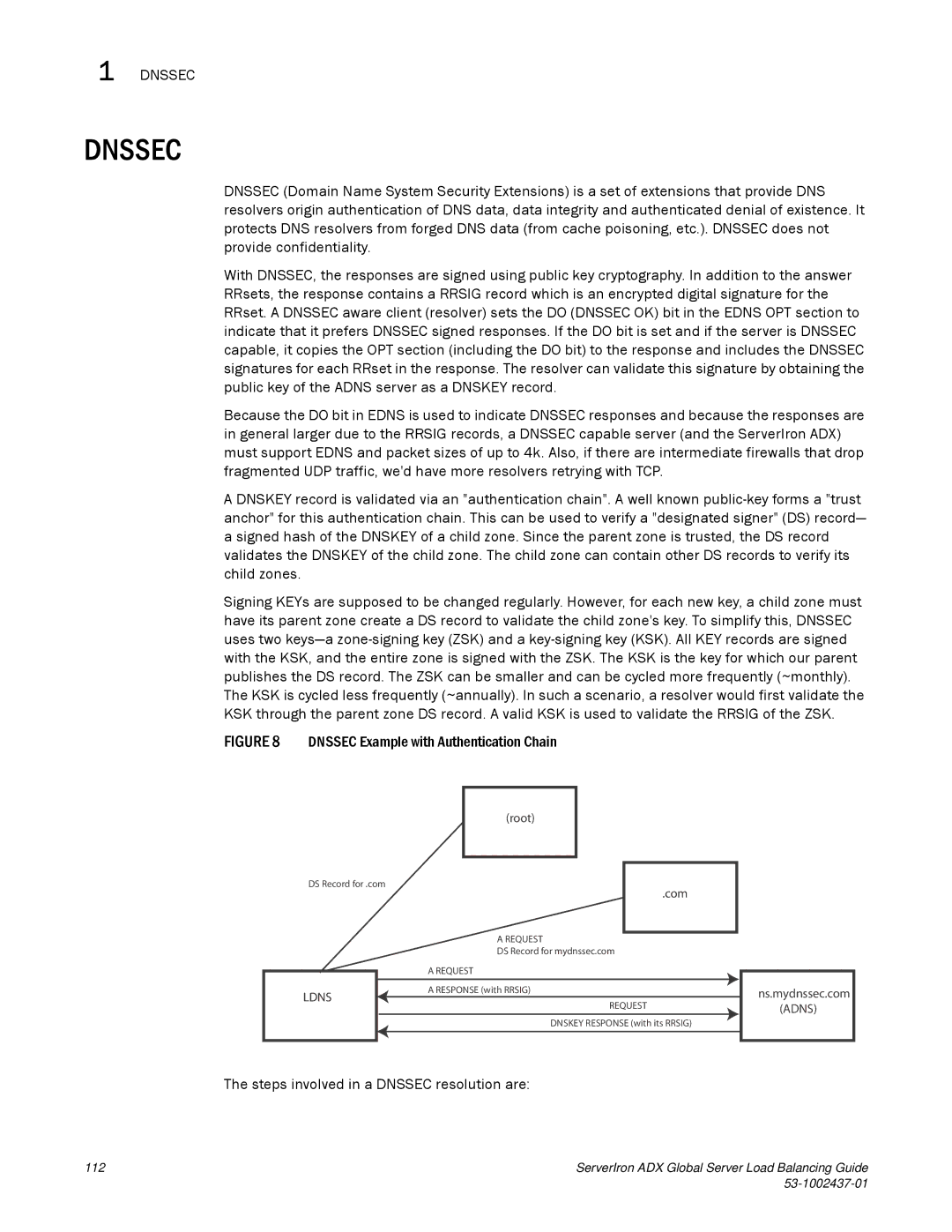
A DNSKEY record is validated via an "authentication chain". A well known
Signing KEYs are supposed to be changed regularly. However, for each new key, a child zone must have its parent zone create a DS record to validate the child zone's key. To simplify this, DNSSEC uses two
FIGURE 8 DNSSEC Example with Authentication Chain
(root)
DS Record for .com
.com
A REQUEST
DS Record for mydnssec.com
LDNS
AREQUEST
ARESPONSE (with RRSIG)
REQUEST
DNSKEY RESPONSE (with its RRSIG)
ns.mydnssec.com
(ADNS)
The steps involved in a DNSSEC resolution are:
112 | ServerIron ADX Global Server Load Balancing Guide |
|