TigerSwitch 10/100/1000
Page
TigerSwitch 10/100/1000 Management Guide
Trademarks
Limited Warranty
Limited Warranty
Contents
Contents
Contents
Command Line Interface
Vii
Viii
Contents
Contents
Contents
Xii
Xiii
Xiv
Contents
Xvi
Tables
Xvii
Xviii
Figures
61. Displaying Vlan Information by Port Membership
Xix
Figures
Key Features
Key Features
Description of Software Features
Description of Software Features
Introduction
Description of Software Features
Introduction
System Defaults
System Defaults
System Defaults
Dhcp
Introduction
Configuration Options
Connecting to the Switch
Required Connections
Connecting to the Switch
Console Connection
Basic Configuration
Remote Connections
Setting Passwords
Manual Configuration
Setting an IP Address
Dynamic Configuration
Initial Configuration
Community Strings
Enabling Snmp Management Access
Initial Configuration
Trap Receivers
Saving Configuration Settings
Managing System Files
Managing System Files
Initial Configuration
Using the Web Interface
Configuring the Switch
Configuring the Switch
Home
Navigating the Web Browser Interface
Panel Display
Configuration Options
Main Menu
Main Menu
ACL
Lacp
STA
141
Vlan ID
DNS
Field Attributes
Displaying System Information
CLI Specify the hostname, location and contact information
System Information
Management Software
Displaying Switch Hardware/Software Versions
Main Board
Switch Information
Web Click System, Switch Information
Displaying Bridge Extension Capabilities
Web Click System, Bridge Extension
Setting the Switch’s IP Address
CLI Enter the following command
Command Attributes
Manual IP Configuration
Dhcp IP Configuration
Using DHCP/BOOTP
288
Downloading System Software from a Server
Managing Firmware
Operation Code Image File Transfer
Saving or Restoring Configuration Settings
10. Downloading Configuration Settings from a Server
Downloading Configuration Settings from a Server
CLI Use the reload command to restart the switch
Resetting the System
Configuring Sntp
Setting the System Clock
13. Sntp Configuration
14. Setting the Time Zone
Setting the Time Zone
Simple Network Management Protocol
Setting Community Access Strings
Specifying Trap Managers and Trap Types
Access Mode
16. Specifying Trap Managers and Trap Types
Configuring the Logon Password
User Authentication
17. Configuring the Logon Password
Configuring Local/Remote Logon Authentication
Command Usage
Radius Settings
18. Setting Local, Radius and Tacacs Authentication
Tacacs Settings
Configuring Https
Https Support
19. Https Settings
Replacing the Default Secure-site Certificate
Configuring the Secure Shell
Configuring the Switch
Generating the Host Key Pair
Field Attributes
20. SSH Host-Key Settings
SSH server includes basic settings for authentication
Configuring the SSH Server
21. SSH Server Settings
Configuring Port Security
Command Usage
22. Configuring Port Security
Configuring 802.1x Port Authentication
802.1x client Radius server
Displaying 802.1x Global Settings
23 .1x Information
111
Configuring 802.1x Global Settings
24 .1x Configuration
Configuring Port Authorization Mode
Authorized
25 .1x Port Configuration
1x Statistics
Displaying 802.1x Statistics
Statistical Values
26 .1x Statistics
CLI This example displays the 802.1x statistics for port
Access Control Lists
Configuring Access Control Lists
Setting the ACL Name and Type
CLI This example creates a standard IP ACL named bill
27. Naming and Choosing ACLs
28. Configuring Standard IP ACLs
Configuring a Standard IP ACL Command Attributes
Configuring an Extended IP ACL Command Attributes
Access Control Lists
29. Configuring Extended IP ACLs
120
Configuring a MAC ACL Command Attributes
Command Usage
30. Configuring MAC ACLs
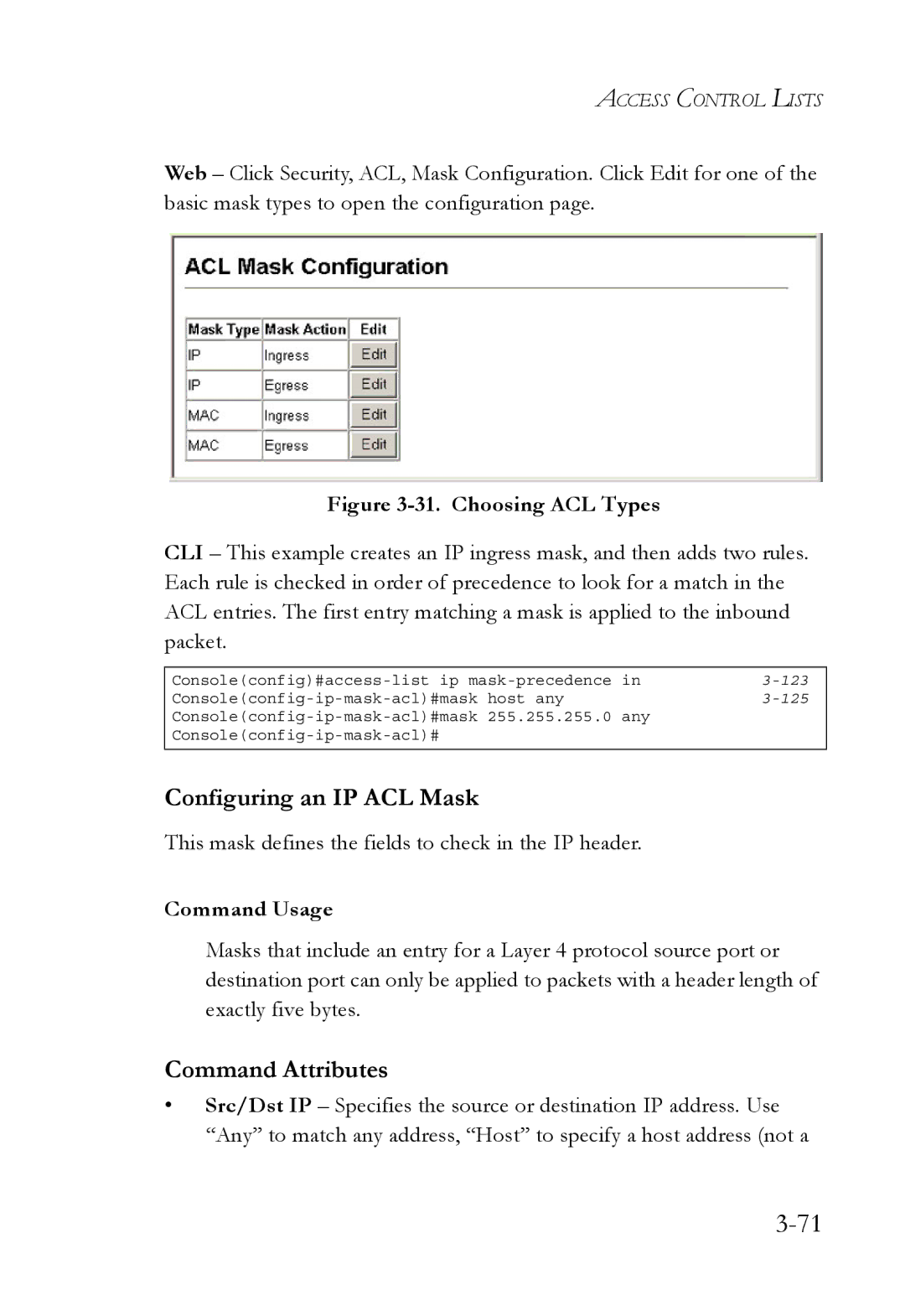
Specifying the Mask Type
Configuring ACL Masks
Command Usage
This mask defines the fields to check in the IP header
Configuring an IP ACL Mask
Configuring the Switch
32. Configuring an IP based ACL
This mask defines the fields to check in the packet header
Configuring a MAC ACL Mask
33. Configuring a MAC based ACL
148
Binding a Port to an Access Control List
34. Mapping ACLs to Port Ingress/Egress Queues
Filtering Management Access
35. Filtering Management Access
Field Attributes Web
Port Configuration
Displaying Connection Status
Web Click Port, Port Information or Trunk Information
Field Attributes CLI
Current status
178
CLI This example shows the connection status for Port
Configuring Interface Connections
Port Configuration
Creating Trunk Groups
37. Configuring Port Attributes
Command Usage
38. Static Trunk Configuration
Statically Configuring a Trunk Command Usage
189
Enabling Lacp on Selected Ports Command Usage
39. Lacp Port Configuratio
190
Command Attributes
40. Lacp Aggregation Port Configuration
Lacp Port Counter Information
Displaying Lacp Port Counters
Counter Information
You can display statistics for Lacp protocol messages
41. Displaying Lacp Port Counters Information
Lacp Settings
Displaying Lacp Settings and Status for the Local Side
Internal Configuration Information
Link Passive 1 Active
42. Displaying Lacp Port Information
Lacp Remote Side Settings
Displaying Lacp Settings and Status for the Remote Side
Neighbor Configuration Information
43. Displaying Remote Lacp Port Information
100
101
Setting Broadcast Storm Thresholds
44. Enabling Port Broadcast Control
102
103
Configuring Port Mirroring
104
Configuring Rate Limits
105
Command Attribute
106
Showing Port Statistics
Port Statistics
107
108
Rmon Statistics
109
47. Displaying Port Statistics
110
48. Displaying Etherlike and Rmon Statistics
111
CLI This example shows statistics for port
Address Table Settings
Setting Static Addresses
112
49. Mapping Ports to Static Addresses
113
114
Displaying the Address Table
CLI This example sets the aging time to 400 seconds
Changing the Aging Time
115
116
Spanning Tree Algorithm Configuration
117
Displaying Global Settings
118
119
52. Displaying the Spanning Tree Algorithm
120
121
Configuring Global Settings
Global settings apply to the entire switch
122
Basic Configuration of Global Settings
123
Root Device Configuration
124
Configuration Settings for Rstp
125
53. Configuring the Spanning Tree Algorithm
126
Displaying Interface Settings
Rules defining port status are
127
AD B
128
129
CLI This example shows the STA attributes for port
Configuring Interface Settings
130
131
132
CLI This example sets STA attributes for port
Configuring Multiple Spanning Trees
133
134
Vlan ID Vlan to assign to this selected MST instance. Range
135
136
137
Displaying Interface Settings for Mstp
138
139
Configuring Interface Settings for Mstp
140
58. Mstp Port Configuration
CLI This example sets the Mstp attributes for port
Vlan Configuration
Overview
141
Assigning Ports to VLANs
142
143
144
Forwarding Tagged/Untagged Frames
145
146
Enabling or Disabling Gvrp Global Setting
CLI This example enables Gvrp for the switch
Displaying Basic Vlan Information
Web Click VLAN, 802.1Q VLAN, Basic Information
Command Attributes Web
Displaying Current VLANs
147
148
Command Attributes CLI
149
Creating VLANs
CLI This example creates a new Vlan
150
151
Adding Static Members to VLANs Vlan Index
152
63. Configuring Vlan Port Attributes
153
Adding Static Members to VLANs Port Index
154
Configuring Vlan Behavior for Interfaces
155
156
157
65. Configuring Vlan Ports
Enabling Private VLANs
Configuring Private VLANs
CLI This example enables private VLANs
158
159
Configuring Protocol-Based VLANs
Configuring Uplink and Downlink Ports
Create a protocol group for one or more protocols
Configuring Protocol Groups
160
Mapping Protocols to VLANs
161
69. Mapping Protocols to VLANs
162
163
Class of Service Configuration
Setting the Default Priority for Interfaces
164
CLI This example assigns a default priority of 5 to port
10. CoS Priority Levels
Mapping CoS Values to Egress Queues
165
Egress Queue Priority Mapping
166
71. Configuring Ports and Trunks for Class of Service
167
Selecting the Queue Mode
168
Setting the Service Weight for Traffic Classes
169
Mapping Layer 3/4 Priorities to CoS Values
170
Selecting IP Precedence/DSCP Priority
11. IP Precedence Prioruty
Mapping IP Precedence
171
172
75. Mapping IP Precedence to Class of Service Values
173
Mapping Dscp Priority
174
76. Mapping IP Dscp Priority to Class of Service Values
175
Mapping IP Port Priority
78. IP Port Priority Mapping
176
13. CoS to ACL Mapping
Mapping CoS Values to ACLs
177
178
Changing Priorities Based on ACL Rules
179
79. Changing Priorities Based on ACL Rules
180
181
Multicast Filtering
182
Configuring Igmp Snooping and Query Parameters
Layer 2 Igmp Snooping and Query
183
184
80. Configuring Internet Group Management Protocol
Displaying Interfaces Attached to a Multicast Router
Command Attributes
185
Specifying Static Interfaces for a Multicast Router
186
187
Displaying Port Members of Multicast Services
188
Assigning Ports to Multicast Services
84. Specifying Multicast Port Membership
189
190
Configuring Domain Name Service
Configuring General DNS Server Parameters
191
192
85. Configuring DNS
193
Configuring Static DNS Host to Address Entries
86. Mapping IP Addresses to a Host Name
194
195
Displaying the DNS Cache
Web Select DNS, Cache
196
Accessing the CLI
Using the Command Line Interface
Telnet Connection
Using the Command Line Interface
Minimum Abbreviation
Entering Commands
This section describes how to enter CLI commands
Keywords and Arguments
Getting Help on Commands
Command Completion
Showing Commands
Partial Keyword Lookup
Negating the Effect of Commands
Using Command History
Command Modes
Understanding Command Modes
Exec Commands
Configuration Commands
Mode Command Prompt
Configuration Commands
Keystroke Function
Command Line Processing
Command Group Index
Command Groups
255
Line Command Syntax
Line Commands
Syntax Line console vty
Default Setting
Command Mode
Line
Syntax Login local no login
Login
Related Commands
No password is specified
Password
Username 4-35 password
Syntax Password 0 7 password no password
CLI No timeout Telnet 10 minutes
Exec-timeout
Login 4-16password-thresh4-19
Syntax Exec-timeout seconds no exec-timeout
Default value is three attempts
Password-thresh
To set the timeout to two minutes, enter this command
Syntax Password-thresh threshold no password-thresh
Syntax Silent-time seconds no silent-time
Silent-time
Seven data bits per character Eight data bits per character
To specify 7 data bits, enter this command
Databits
Syntax Databits 7 8 no databits
None No parity Even Even parity Odd Odd parity
To specify no parity, enter this command
Parity
Syntax Parity none even odd no parity
Auto
To specify 57600 bps, enter this command
Speed
Syntax Speed bps no speed
Syntax Disconnect session-id
Stopbits
Disconnect
Syntax Stopbits 1
Syntax Show line console vty
Show line
Syntax Enable level
General Commands
Enable
General Commands
None
Disable
Disable Enable password
Normal Exec
Show history
Configure
Reload
This command restarts the system
End
This command resets the entire system
This example shows how to reset the switch
This command returns to Privileged Exec mode
Any
This command exits the configuration program
Exit
Quit
System Mangement Commands
System Management Commands
This example shows how to quit a CLI session
Syntax Prompt string no prompt
Device Designation Commands
Device Designation Commands
Prompt
Syntax Hostname name no hostname
User Access Commands
User Access Commands
Hostname
Username
Default is level Default password is super
Enable password
10. IP Filter Commands
IP Filter Commands
All addresses
Management
Show management
11. Web Server Command
Web Server Commands
Ip http server
Default Setting Command Mode
Syntax No ip http server Default Setting
Ip http port
Ip http port Copy tftp https-certificate
Syntax No ip http secure-server Default Setting
Ip http secure-server
Ip http secure-port4-44 Copy tftp https-certificate
Ip http secure-server4-42
Ip http secure-port
Portnumber The UDP port used for HTTPS/SSL. Range
443
12. Secure Shell Commands
Secure Shell Commands
12. Secure Shell Commands
System Management Commands
Ip ssh server
Syntax Ip ssh server no ip ssh server Default Setting
Disabled
Seconds
Ip ssh timeout
Syntax Ip ssh timeout seconds no ip ssh timeout
Ip ssh crypto host-key generate 4-52 show ssh
Show ip ssh
Ip ssh authentication-retries
Exec-timeout4-18 show ip ssh
Syntax Delete public-key username dsa rsa
Ip ssh server-key size
Delete public-key
Generates both the DSA and RSA key pairs
Ip ssh crypto host-key generate
Syntax Ip ssh crypto host-key generate dsa rsa
Dsa DSA key type Rsa RSA key type
Syntax Ip ssh crypto zeroize dsa rsa
Use this command to clear the host key from memory i.e. RAM
Ip ssh crypto zeroize
Ip ssh crypto zeroize 4-53 ip ssh save host-key4-54
Syntax Ip ssh save host-key dsa rsa
Ip ssh save host-key
Show ip ssh
13. SSH Information
Show ssh
Username Name of an SSH user. Range 1-8 characters
Show public-key
Syntax Show public-key user username host
RSA
Shows all public keys
Logging on
Event Logging Commands
14. Event Logging Commands
Syntax No logging on Default Setting
Logging history 4-59 clear logging
Logging history
Hostipaddress The IP address of a syslog server
Flash errors level 3 RAM warnings level 7
Logging host
Syntax No logging host hostipaddress
Syntax No logging facility type
Logging facility
Syntax Clear logging flash ram
Logging trap
Clear logging
Syntax Logging trap level no logging trap
Syntax Show logging flash ram sendmail trap
Show logging
Show logging
Following example displays settings for the trap function
Show logging sendmail
Smtp Alert Commands
15. Smtp Alert Commands
Syntax No logging sendmail host ipaddress
Logging sendmail host
Syntax Logging sendmail source-email email-address
Logging sendmail level
Logging sendmail source-email
Syntax Logging sendmail level level
Syntax No logging sendmail destination-email email-address
Logging sendmail destination-email
Show logging sendmail
Syntax No logging sendmail Default Setting
Logging sendmail
16. Time Commands
Time Commands
Sntp poll 4-72 show sntp
Sntp server
Syntax Sntp server ip1 ip2 ip3
Syntax Sntp poll seconds no sntp poll
Related Commands
Sntp poll
Sntp client
Disabled
Show sntp
Syntax No sntp broadcast client Default Setting
Sntp broadcast client
Show sntp
Clock timezone
Syntax
This command displays the system clock
Calendar set
Show calendar
17. System Status Commands
System Status Commands
Show startup-config
Command Usage
Show running-config4-80
Show running-config
Show startup-config4-77
Show system
This command displays system information
Show version
Show users
Jumbo frame
Frame Size Commands
18. Frame Size Commands
Syntax No jumbo frame Default Setting
19. Flash/File Commands
Flash/File Commands
Copy
Command Usage
Following example shows how to download a configuration file
Delete
This command deletes a file or image
Filename Name of the configuration file or image name
Dir Delete public-key4-51
This command displays a list of files in flash memory
Syntax Dir boot-rom config opcode filename
Dir
Following example shows how to display all file information
Whichboot
Syntax Boot system boot-romconfig opcode filename
Boot system
20. Authentication Commands
Authentication Commands
Authentication Sequence
Dir 4-90 whichboot
Local
Authentication login
Radius-server host
Username for setting the local user names and passwords
22. Radius Client Commands
Radius Client
1812
Radius-server port
10.1.0.1
Syntax Radius-server port portnumber no radius-server port
Syntax Radius-server key keystring no radius-server key
Radius-server key
Radius-server retransmit
Show radius-server
Radius-server timeout
Hostipaddress IP address of a TACACS+ server
23. TACACS+ Client Commands
TACACS+ Client
Tacacs-server host
Syntax Tacacs-server port portnumber no tacacs-server port
Tacacs-server port
Syntax Tacacs-server key keystring no tacacs-server key
Tacacs-server key
Show tacacs-server
Port security
Port Security Commands
24. Port Security Commands
Interface Configuration Ethernet
Status Disabled Action None Maximum Addresses
25 .1x Port Authentication Commands
802.1x Port Authentication
Authentication dot1x default
Dot1x max-req
Dot1x default
Syntax Dot1x default Command Mode
Default Command Mode
Force-authorized
Default
Interface Configuration
Dot1x port-control
Ethernet unit/port
Dot1x re-authenticate
Syntax Dot1x re-authenticate interface
Dot1x operation-mode
Seconds The number of seconds. Range
Dot1x re-authentication
Dot1x timeout quiet-period
Syntax No dot1x re-authentication Command Mode
Dot1x timeout tx-period
Dot1x timeout re-authperiod
Show dot1x statistics interface interface
Show dot1x
State- Current state including initialize, reauthenticate
Authenticator State Machine
113
Access Control Lists
Access Control List Commands
Access Control List Commands
IP ACLs
Masks for Access Control Lists
26. Access Control List Commands
27. IP ACL Commands
EXT-ACL
Syntax No access-list ip standard extended aclname
Access-list ip
Standard ACL
Permit, deny Ip access-group4-129 show ip access-list4-123
No permit deny tcp
Access-list ip
Extended ACL
122
Syntax No access-list ip mask-precedence in out
Show ip access-list
Access-list ip mask-precedence
Syntax Show ip access-list standard extended aclname
Mask IP ACL 4-125 ip access-group4-129
IP Mask
Syntax No mask protocol
126
127
Syntax Show access-list ip mask-precedence in out
Show access-list ip mask-precedence
Mask IP ACL
Ip access-group
Syntax No ip access-group aclname in out
This command shows the ports assigned to IP ACLs
Show ip access-group
Map access-list ip
Show ip access-list4-123
Queue cos-map4-260 Show map access-list ip
Map access-list ip
Show map access-list ip
Syntax Show map access-list ip interface
Match access-list ip
Show marking
Match access-list ip
Show marking
MAC ACLs
28. MAC ACL Commands
Syntax No access-list mac aclname
Access-list mac
Any host destination destination address-bitmask
Permit, deny MAC ACL
MAC ACL
Syntax Show mac access-list aclname
Show mac access-list
Access-list mac mask-precedence
This command displays the rules for configured MAC ACLs
Mask MAC ACL
Mask MAC ACL 4-140 mac access-group4-144
MAC Mask
142
This example creates an Egress MAC ACL
Show access-list mac mask-precedence
Syntax Show access-list mac mask-precedence in out
Show mac access-list4-139
Mac access-group
Syntax Mac access-group aclname in out
Syntax No map access-list mac aclname cos cos-value
Show mac access-group
Map access-list mac
This command shows the ports assigned to MAC ACLs
Syntax Show map access-list mac interface
Show map access-list mac
Queue cos-map4-260 Show map access-list mac
Match access-list mac
29. ACL Information
Show access-list
ACL Information
30. Snmp Commands
Snmp Commands
Show access-group
This command shows the port assignments of ACLs
Syntax Snmp community string rorw no snmp community string
Snmp community
Syntax Snmp-server location text no snmp-server location
Snmp contact
Snmp location
Syntax Snmp contact string no snmp contact
Host Address None Snmp Version
Snmp host
Consoleconfig#snmp-server host 10.1.19.23 batman
Issue authentication and link-up-down traps
Snmp enable traps
Syntax No snmp enable traps authentication link-up-down
Show snmp
This command checks the status of Snmp communications
156
31. DNS Commands
DNS Commands
This example maps two address to a host name
Ip host
No static entries
Syntax Ip domain-name name no ip domain-name
Clear host
Ip domain-name
Syntax Clear host name
Syntax No ip domain-list name
Ip domain-list
Ip domain-name4-159
Server-address1- IP address of domain-name server
Ip name-server
Ip domain-name4-159 ip domain-lookup4-163
Syntax No ip domain-lookup Default Setting
Ip domain-lookup
Ip domain-name4-159 ip name-server4-162
Show hosts
Show dns cache
This command displays the configuration of the DNS server
This command displays entries in the DNS cache
Show dns
Clear dns cache
This command clears all entries in the DNS cache
167
32. Interface Commands
Interface Commands
Syntax Description string no description
Interface
Description
Port-channel channel-idRange
Following example adds a description to port
Interface Configuration Ethernet, Port Channel
Speed-duplex
Negotiation 4 -170 capabilities 4
Syntax No negotiation Default Setting
Negotiation
Capabilities 4 -172speed-duplex 4
Following example configures port 11 to use autonegotiation
Capabilities
Negotiation 4 -170speed-duplex 4 -169 flowcontrol 4
Syntax No flowcontrol Default Setting
Flow control enabled
Flowcontrol
Negotiation 4 Capabilities flowcontrol, symmetric
Following example enables flow control on port
Syntax Combo-forced-mode mode no combo-forced-mode
Combo-forced-mode
Shutdown
Syntax No shutdown Default Setting
All interfaces are enabled
Following example disables port
Switchport broadcast packet-rate
Following example clears statistics on port
This command clears statistics on an interface
Port-channel channel-idRange Default Setting
Clear counters
Shows the status for all interfaces
This command displays the status for an interface
Show interfaces status
Syntax Show interfaces status interface
Shows the counters for all interfaces
This command displays interface statistics
Show interfaces counters
Syntax Show interfaces counters interface
180
Shows all interfaces
Show interfaces switchport
Syntax Show interfaces switchport interface
This example shows the configuration setting for port
Shows if acceptable Vlan frames include all types or
Port monitor
Mirror Port Commands
33. Mirror Port Commands
Interface Configuration Ethernet, destination port
Syntax Show port monitor interface
This command displays mirror information
Unit Switch unit Port Port number
Show port monitor
34. Rate Limit Commands
Rate Limit Commands
Following shows mirroring configured from port 6 to port
Mbps
Rate-limit
35. Link Aggregation Commands
Link Aggregation Commands
General Guidelines
Guidelines for Creating Trunks
Current port will be added to this trunk
Channel-group
Syntax Channel-group channel-idno channel-group
Channel-id- Trunk index Range
Lacp
Syntax No lacp Default Setting
191
32768
Lacp system-priority
Lacp admin-keyEthernet Interface
Interface Configuration Port Channel
Lacp admin-key Port Channel
Syntax Lacp admin-key key no lacp admin-key
Lacp port-priority
Port Channel all
This command displays Lacp information
Show lacp
197
198
199
200
Address Table Commands
36. Adress Table Commands
Vlan-id- Vlan ID Range
Mac-address-table static
201
Mac-address- MAC address
Mac-address- MAC address Mask Bits to match in the address
Clear mac-address-table dynamic
Show mac-address-table
202
203
Mac-address-table aging-time
204
Show mac-address-table aging-time
205
Spanning Tree Commands
37. Spanning Tree Commands
No spanning-tree
Spanning tree is enabled
Spanning-tree
206
Rstp
Spanning-tree mode
207
208
209
Spanning-tree forward-time
210
Spanning-tree hello-time
Spanning-tree max-age
211
Spanning-tree priority
Long method
Spanning-tree pathcost method
212
213
Spanning-tree mst-configuration
This command limits the maximum transmission rate for BPDUs
Spanning-tree transmission-limit
214
MST Configuration
Mst vlan
215
Mst priority
Syntax Name name
Switch’s MAC address
Name
216
Syntax Revision number
Revision
217
Revision 4
Name 4
Max-hops
218
219
Spanning-tree spanning-disabled
Syntax No spanning-tree spanning-disabled Default Setting
Spanning-tree cost
128
Spanning-tree port-priority
220
Priority The priority for a port. Range 0-240, in steps
Spanning-tree cost 4
Syntax No spanning-tree edge-port Default Setting
Spanning-tree edge-port
221
Spanning-tree portfast 4
Syntax No spanning-tree portfast Default Setting
Spanning-tree portfast
222
Spanning-treeedge-port 4
Spanning-tree link-type
223
224
Spanning-tree mst cost
Spanning-tree mst port-priority 4
225
Spanning-tree mst cost 4
Spanning-tree mst port-priority
226
Syntax Spanning-tree protocol-migration interface
Port-channel channel-idRange Command Mode
Spanning-tree protocol-migration
227
Syntax Show spanning-tree interface mst instanceid
Show spanning-tree
228
229
230
Show spanning-tree mst configuration
This command shows the multiple spanning tree configuration
Syntax Show spanning-tree mst configuration Command Mode
231
Vlan Commands
38. Vlan Commands
Editing Vlan Groups
Show vlan 4
232
Vlan database
Vlan
By default only Vlan 1 exists and is active
Vlan Database Configuration
233
234
Configuring Vlan Interfaces
40. Configuring Vlan Interfaces
Shutdown 4
235
Interface vlan
Syntax Interface vlan vlan-id
Switchport acceptable-frame-types 4
Switchport mode
Syntax Switchport mode trunk hybrid no switchport mode
All ports are in hybrid mode with the Pvid set to Vlan
All frame types
Switchport acceptable-frame-types
Switchport mode 4
237
238
Switchport ingress-filtering
Syntax No switchport ingress-filtering Default Setting
239
Switchport native vlan
240
Switchport allowed vlan
No VLANs are included in the forbidden list
Switchport forbidden vlan
241
41. Displaying Vlan Information
Displaying Vlan Information
242
Show vlan
243
Following example shows how to display information for Vlan
42. Protocol-based Vlan Commands
244
Protocol-vlan protocol-group Configuring Groups
No protocol groups are configured
No protocol groups are mapped for any interface
Protocol-vlan protocol-group Configuring Interfaces
245
Group-id- Group identifier for a protocol group. Range
246
Show protocol-vlan protocol-group
Syntax Show protocol-vlan protocol-group group-id
Mapping for all interfaces is displayed
This shows protocol group 1 configured for IP over Ethernet
247
Show interfaces protocol-vlan protocol-group
No private VLANs are defined
43. Private Vlan Commands
248
Pvlan
Show pvlan
This command displays the configured private Vlan
249
250
Gvrp and Bridge Extension Commands
44. Gvrp and Bridge Extension Commands
Syntax No bridge-ext gvrp Default Setting
Show bridge-ext
251
Syntax Show gvrp configuration interface
Switchport gvrp
Show gvrp configuration
Syntax No switchport gvrp Default Setting
253
Garp timer
Shows all Garp timers
Show garp timer
Show garp timer 4
Syntax Show garp timer interface
255
Priority Commands
Garp timer 4
45. Priority Commands
256
Priority Commands Layer
Switchport priority default
46. Priority Commands Layer
257
258
Queue mode
Syntax Queue mode strict wrr no queue mode
Weighted Round Robin
Show queue bandwidth 4
259
Queue bandwidth
Queue cos-map
260
Show queue cos-map 4
Show queue mode
This command shows the current queue mode
261
Show queue cos-map
This command shows the class of service priority map
262
Show queue bandwidth
263
Priority Commands Layer 3
47. Priority Commands Layer 3
264
Syntax Map ip port no map ip port Default Setting
265
Syntax No map ip precedence Default Setting
266
List below shows the default priority mapping
267
Syntax No map ip dscp Default Setting
268
Map ip dscp Interface Configuration
Syntax Show map ip port interface
Use this command to show the IP port priority map
269
Show map ip port
Syntax Show map ip precedence interface
This command shows the IP precedence priority map
270
Show map ip precedence
Syntax Show map ip dscp interface
This command shows the IP Dscp priority map
271
Show map ip dscp
49. Igmp Snooping Commands
Multicast Filtering Commands
Igmp Snooping Commands
48. Multicast Filtering Commands
No ip igmp snooping
Following example enables Igmp snooping
273
Ip igmp snooping
Ip igmp snooping vlan static
274
Igmp Version
Following configures the switch to use Igmp Version
275
Ip igmp snooping version
Show mac-address-table multicast
276
Show ip igmp snooping
277
Igmp Query Commands Layer
50. Igmp Query Commands Layer
Ip igmp snooping query-count
Syntax No ip igmp snooping querier Default Setting
278
Ip igmp snooping querier
Ip igmp snooping query-max-response-time 4
Following shows how to configure the query count to
279
Ip igmp snooping query-interval
Ip igmp snooping query-max-response-time
Seconds The report delay advertised in Igmp queries. Range
280
Ip igmp snooping router-port-expire-time
Switch must use IGMPv2 for this command to take effect
281
Ip igmp snooping vlan mrouter
Static Multicast Routing Commands
51. Static Multicast Routing Commands
282
Syntax Show ip igmp snooping mrouter vlan vlan-id
Displays multicast router ports for all configured VLANs
283
Show ip igmp snooping mrouter
284
IP Interface Commands
Basic IP Configuration
52. Basic IP Configuration commands
IP address Netmask
Interface Configuration Vlan
285
Ip address
Ip dhcp restart 4
This command submits a Bootp or Dhcp client request
286
Ip dhcp restart
287
Ip default-gateway
Syntax Ip default-gateway gateway no ip default-gateway
Show ip redirects
288
Show ip interface
Syntax Ping host count countsize size
This command has no default for the host
289
Ping
Interface 4
290
291
Flow Control
Software Features
Authentication
Dhcp Client Port Configuration
Rate Limits
Class of Service
Additional Features
Port Mirroring
Out-of-Band Management
Management Features
Standards
In-Band Management
Management Information Bases
Table B-1. Troubleshooting Chart
Appendix B Troubleshooting
Troubleshooting
Glossary-1
Glossary-2
Glossary-3
Glossary-4
Glossary-5
Glossary-6
Glossary-7
XModem
Glossary-8
User Datagram Protocol UDP
Virtual LAN Vlan
Index-1
Numerics
Igmp
Index-2
Snmp Snmp
Index-3
Index-4
Page
For Technical SUPPORT, Call