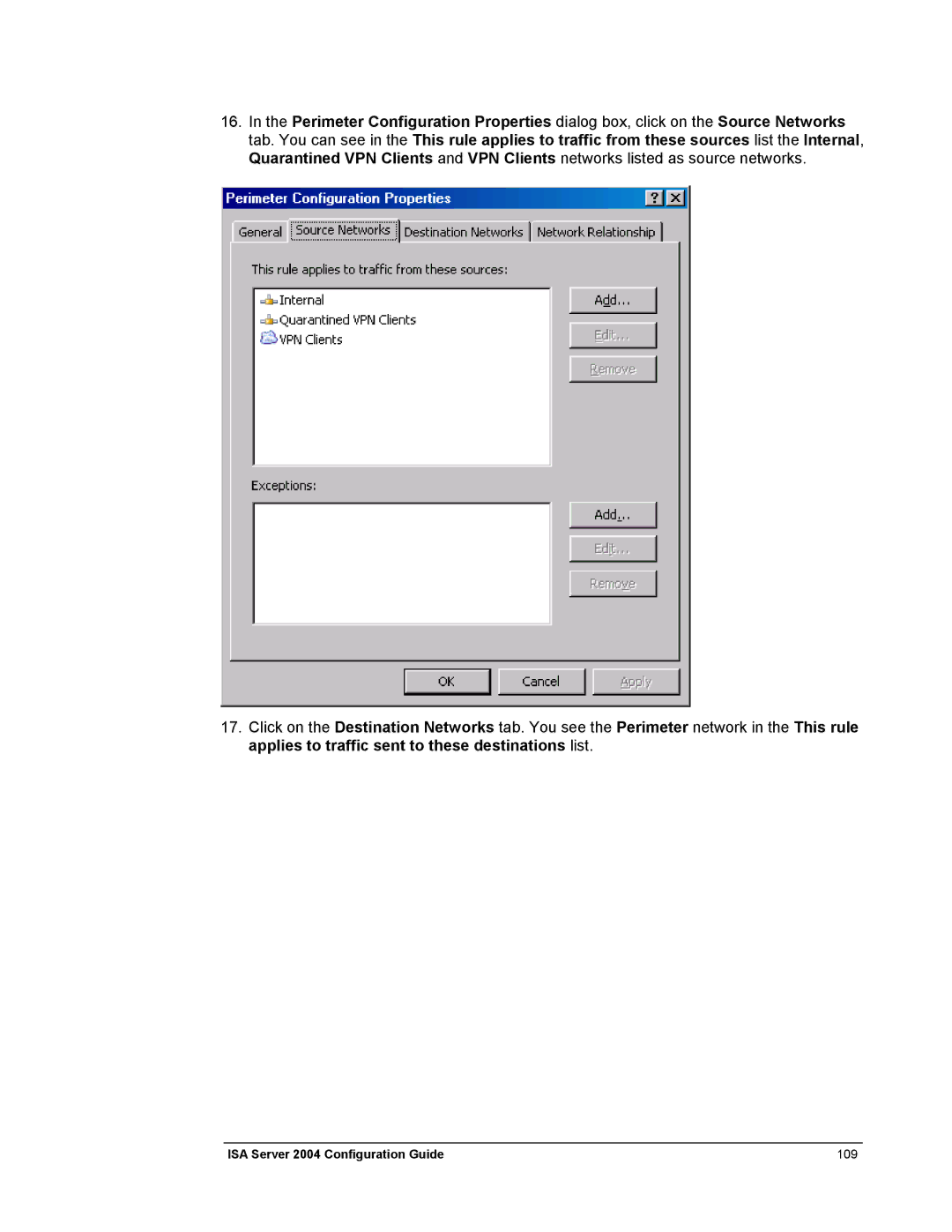
16.In the Perimeter Configuration Properties dialog box, click on the Source Networks tab. You can see in the This rule applies to traffic from these sources list the Internal, Quarantined VPN Clients and VPN Clients networks listed as source networks.
17.Click on the Destination Networks tab. You see the Perimeter network in the This rule applies to traffic sent to these destinations list.
ISA Server 2004 Configuration Guide | 109 |