Use HTTP Policy to Prevent Access to Suspect Web Sites
You can block access to Web sites based on virtually any component of the HTTP communication using ISA Server 2004 HTTP policy. For example, you might want to prevent access to all Web sites that contain a reference to the popular
In the following walkthrough, you will configure the HTTP policy for the Administrator Internet Access and Limited Access Web Users rules to block all Web connections to sites that contain the string “Kaaza” in them. While this example uses a blunt approach to blocking
Perform the following steps to prevent users from accessing
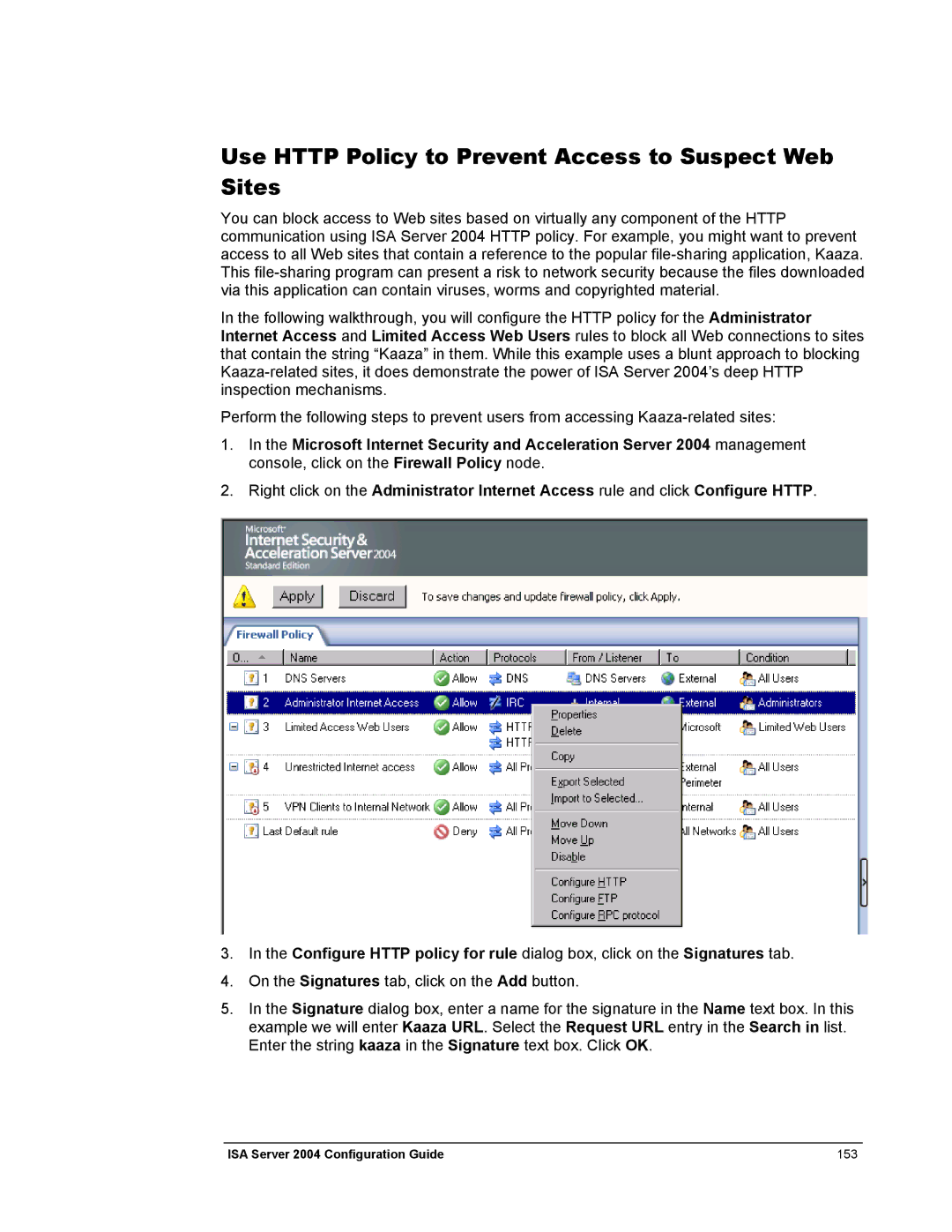
1.In the Microsoft Internet Security and Acceleration Server 2004 management console, click on the Firewall Policy node.
2.Right click on the Administrator Internet Access rule and click Configure HTTP.
3.In the Configure HTTP policy for rule dialog box, click on the Signatures tab.
4.On the Signatures tab, click on the Add button.
5.In the Signature dialog box, enter a name for the signature in the Name text box. In this example we will enter Kaaza URL. Select the Request URL entry in the Search in list. Enter the string kaaza in the Signature text box. Click OK.
ISA Server 2004 Configuration Guide | 153 |