Professional Access Point Administrator Guide
Field
Description
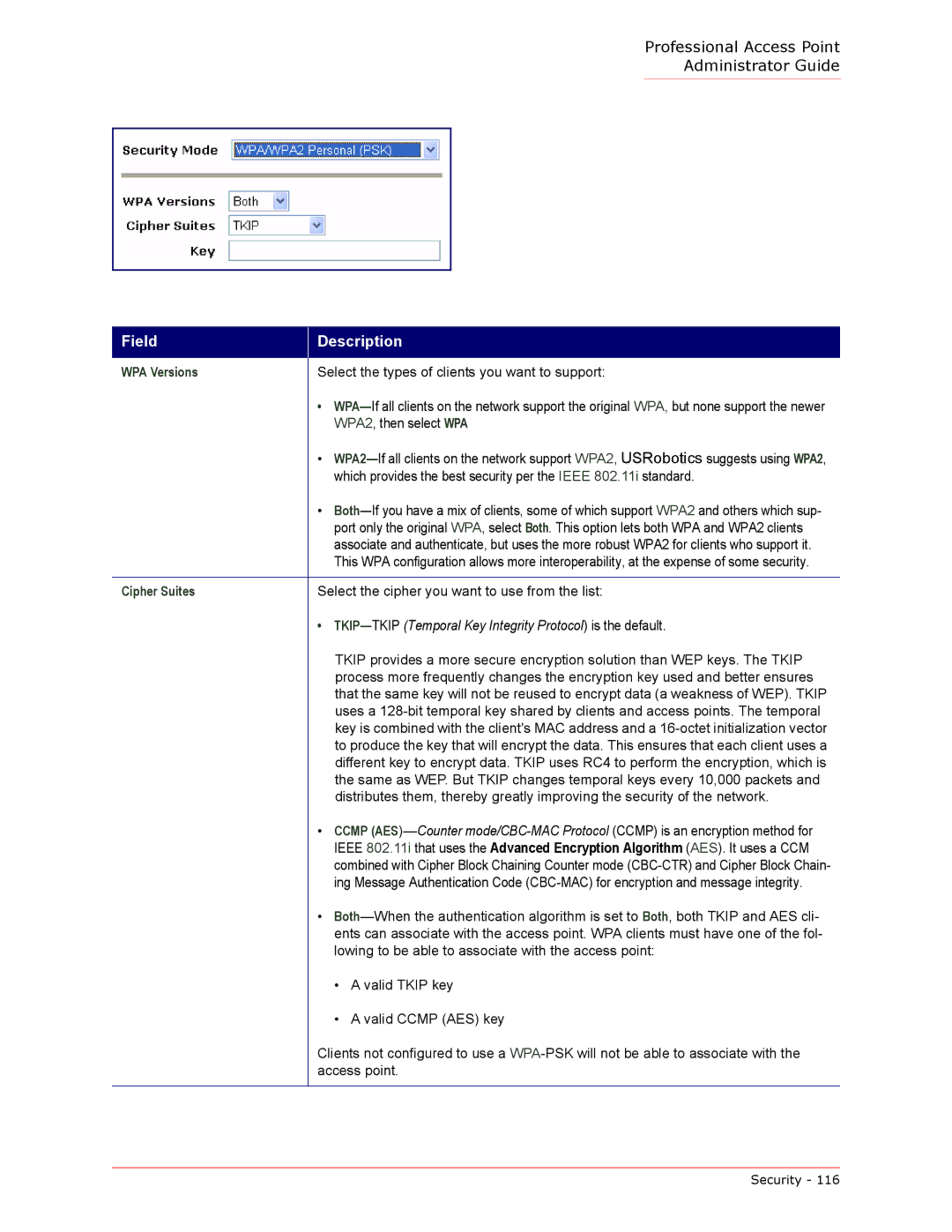
WPA Versions | Select the types of clients you want to support: | |
| • | |
|
| WPA2, then select WPA |
| • | |
|
| which provides the best security per the IEEE 802.11i standard. |
| • | |
|
| port only the original WPA, select Both. This option lets both WPA and WPA2 clients |
|
| associate and authenticate, but uses the more robust WPA2 for clients who support it. |
|
| This WPA configuration allows more interoperability, at the expense of some security. |
|
| |
Cipher Suites | Select the cipher you want to use from the list: | |
| • |
|
|
| TKIP provides a more secure encryption solution than WEP keys. The TKIP |
|
| process more frequently changes the encryption key used and better ensures |
|
| that the same key will not be reused to encrypt data (a weakness of WEP). TKIP |
|
| uses a |
|
| key is combined with the client's MAC address and a |
|
| to produce the key that will encrypt the data. This ensures that each client uses a |
|
| different key to encrypt data. TKIP uses RC4 to perform the encryption, which is |
|
| the same as WEP. But TKIP changes temporal keys every 10,000 packets and |
|
| distributes them, thereby greatly improving the security of the network. |
| • | CCMP |
|
| IEEE 802.11i that uses the Advanced Encryption Algorithm (AES). It uses a CCM |
|
| combined with Cipher Block Chaining Counter mode |
|
| ing Message Authentication Code |
| • | |
|
| ents can associate with the access point. WPA clients must have one of the fol- |
|
| lowing to be able to associate with the access point: |
|
| • A valid TKIP key |
|
| • A valid CCMP (AES) key |
| Clients not configured to use a | |
| access point. | |
|
|
|
Security - 116