Professional Access Point
Administrator Guide
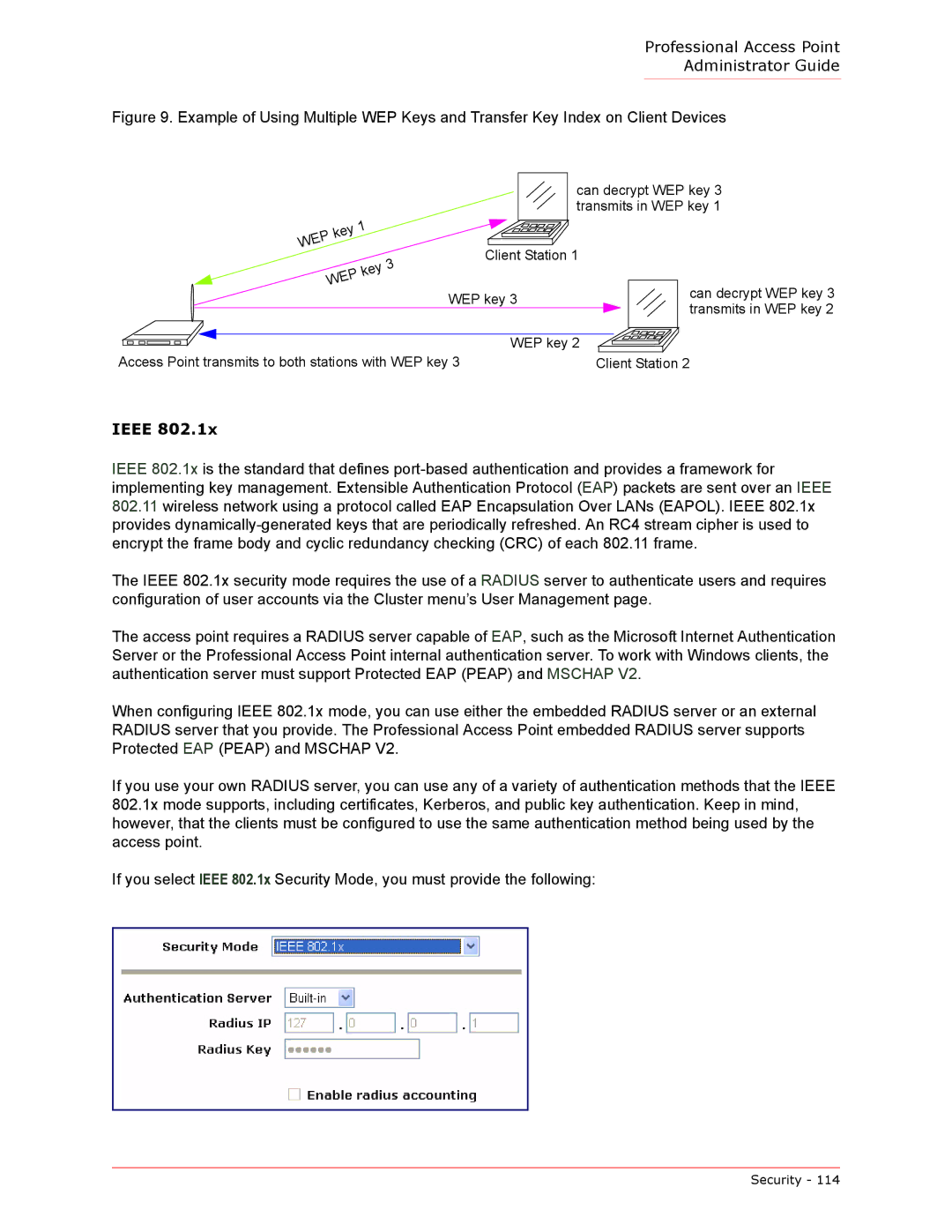
Figure 9. Example of Using Multiple WEP Keys and Transfer Key Index on Client Devices
|
|
| y1 |
| |
|
| e |
|
| |
| Pk |
|
|
| |
E |
|
|
|
| |
W |
|
|
|
|
|
|
|
|
|
| y3 |
|
|
|
| e | |
|
|
| Pk |
| |
|
| E |
|
| |
|
| W |
|
|
|
can decrypt WEP key 3 transmits in WEP key 1
Client Station 1 |
|
|
WEP key 3 |
| can decrypt WEP key 3 |
| ||
| transmits in WEP key 2 | |
|
| |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| WEP key 2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
Access Point transmits to both stations with WEP key 3 |
|
|
| ||||||||||||||
Client Station 2 | |||||||||||||||||
IEEE 802.1x
IEEE 802.1x is the standard that defines
802.11wireless network using a protocol called EAP Encapsulation Over LANs (EAPOL). IEEE 802.1x provides
The IEEE 802.1x security mode requires the use of a RADIUS server to authenticate users and requires configuration of user accounts via the Cluster menu’s User Management page.
The access point requires a RADIUS server capable of EAP, such as the Microsoft Internet Authentication Server or the Professional Access Point internal authentication server. To work with Windows clients, the authentication server must support Protected EAP (PEAP) and MSCHAP V2.
When configuring IEEE 802.1x mode, you can use either the embedded RADIUS server or an external RADIUS server that you provide. The Professional Access Point embedded RADIUS server supports Protected EAP (PEAP) and MSCHAP V2.
If you use your own RADIUS server, you can use any of a variety of authentication methods that the IEEE 802.1x mode supports, including certificates, Kerberos, and public key authentication. Keep in mind, however, that the clients must be configured to use the same authentication method being used by the access point.
If you select IEEE 802.1x Security Mode, you must provide the following:
Security - 114