15.3 VPN using IPSec Protocol
WinRoute’s IPSec configuration
Generally, communication through IPSec must be permitted by firewall policy (for details refer to chapter 6.3). IPSec protocol uses two traffic channels:
•IKE (Internet Key Exchange — exchange of encryption keys and other information).
IKE
•encrypted data (IP protocol number 50 is used)
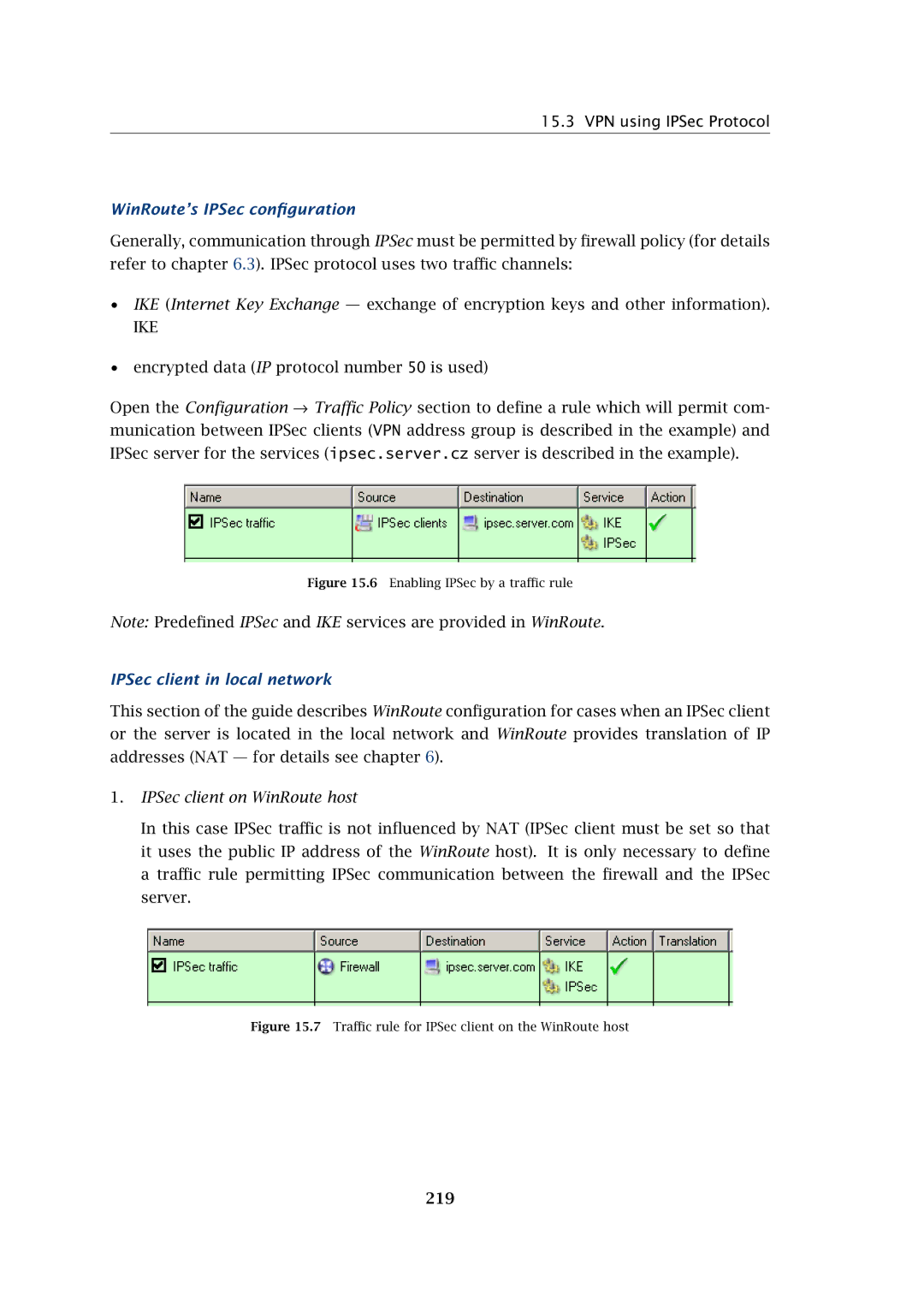
Open the Configuration → Traffic Policy section to define a rule which will permit com- munication between IPSec clients (VPN address group is described in the example) and IPSec server for the services (ipsec.server.cz server is described in the example).
Figure 15.6 Enabling IPSec by a traffic rule
Note: Predefined IPSec and IKE services are provided in WinRoute.
IPSec client in local network
This section of the guide describes WinRoute configuration for cases when an IPSec client or the server is located in the local network and WinRoute provides translation of IP addresses (NAT — for details see chapter 6).
1.IPSec client on WinRoute host
In this case IPSec traffic is not influenced by NAT (IPSec client must be set so that it uses the public IP address of the WinRoute host). It is only necessary to define a traffic rule permitting IPSec communication between the firewall and the IPSec server.