21.3 Interconnection of two private networks via the Internet (VPN tunnel)
the tunnel).
•Passive — this end of the tunnel will only listen for an incoming connection from
the remote (active) side.
The passive mode is only useful when the local end of the tunnel has a fixed IP address and when it is allowed to accept incoming connections.
At least one end of each VPN tunnel must be switched to the active mode (passive servers cannot initialize connection).
Configuration of a remote end of the tunnel
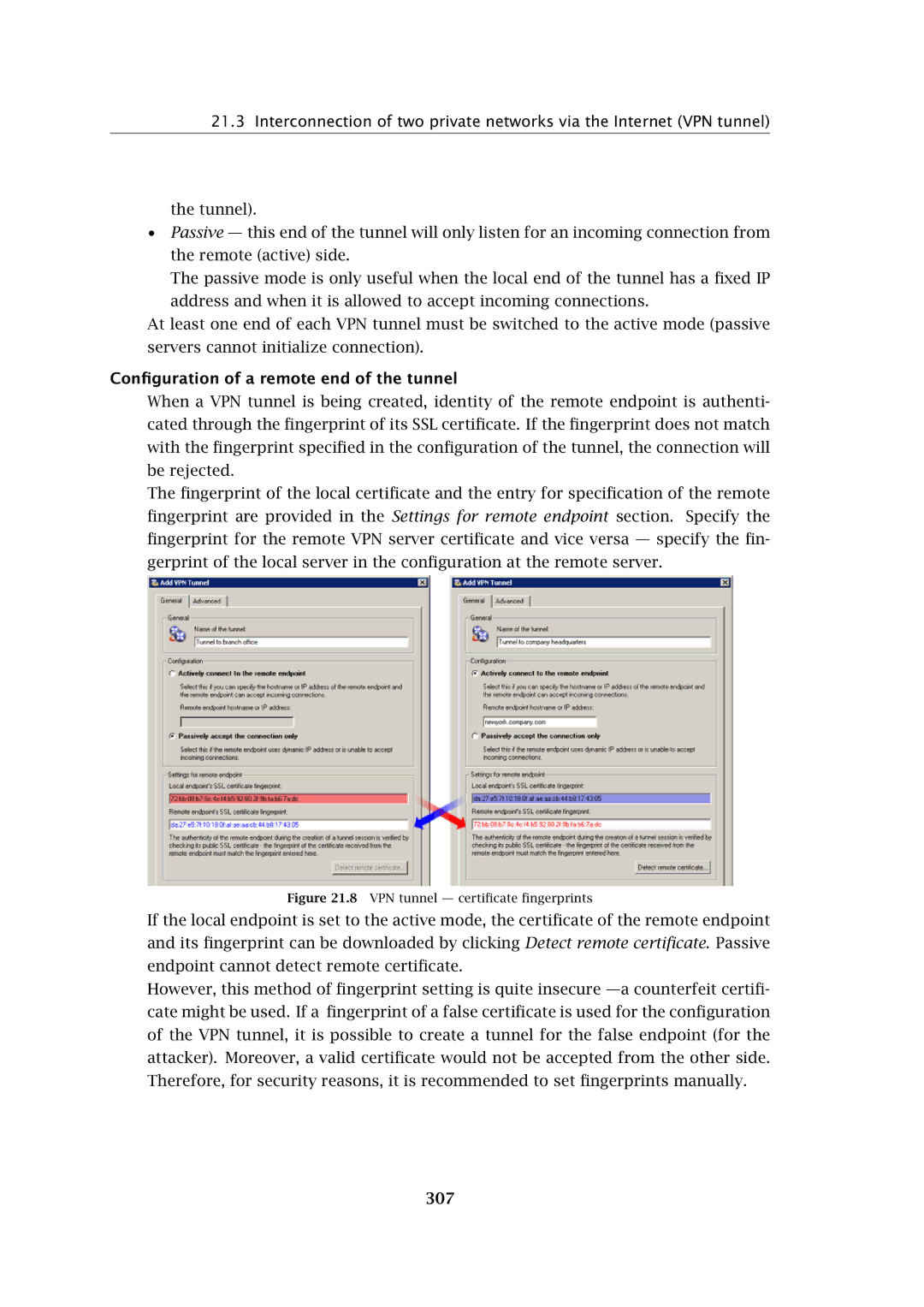
When a VPN tunnel is being created, identity of the remote endpoint is authenti- cated through the fingerprint of its SSL certificate. If the fingerprint does not match with the fingerprint specified in the configuration of the tunnel, the connection will be rejected.
The fingerprint of the local certificate and the entry for specification of the remote fingerprint are provided in the Settings for remote endpoint section. Specify the fingerprint for the remote VPN server certificate and vice versa — specify the fin- gerprint of the local server in the configuration at the remote server.
Figure 21.8 VPN tunnel — certificate fingerprints
If the local endpoint is set to the active mode, the certificate of the remote endpoint and its fingerprint can be downloaded by clicking Detect remote certificate. Passive endpoint cannot detect remote certificate.
However, this method of fingerprint setting is quite insecure