TigerSwitch 10/100
Page
TigerSwitch 10/100 Management Guide
Trademarks
Limited Warranty
SMC Networks, Inc Tesla Irvine, CA
Contents
Viii
Contents
Contents
Command Line Interface
Xii
Xiii
Xiv
Contents
Xvi
Xvii
Xviii
Xix
Contents
Xxi
Xxii
Key Features
Chapter Introduction
Description of Software Features
ARP
Description of Software Features
Introduction
Description of Software Features
Introduction
Description of Software Features
System Defaults
Function Parameter Default
Snmp
Pvid
Dhcp
Introduction
Connecting to the Switch
Configuration Options
Required Connections
Connecting to the Switch
Remote Connections
Basic Configuration
Console Connection
Setting Passwords
Setting an IP Address
Manual Configuration
Dynamic Configuration
Enabling Snmp Management Access
Community Strings
Initial Configuration
Saving Configuration Settings
Trap Receivers
Managing System Files
Managing System Files
Initial Configuration
Configuring the Switch
Using the Web Interface
Configuring the Switch
Navigating the Web Browser Interface
Home
Panel Display
Button Action
Main Menu
Menu Description
Vlan
Vlan ID
Sntp
UDP
Routing Protocol 152
222
Displaying System Information
Field Attributes
Basic Configuration
Field Attributes Main Board
Displaying Switch Hardware/Software Versions
Expansion Slot Indicates any installed module type
Management Software
Basic Configuration
Displaying Bridge Extension Capabilities
Setting the Switch’s IP Address
176
Command Usage
Command Attributes
Manual Configuration
Using DHCP/BOOTP
219
Managing Firmware
Downloading System Software from a Server
Saving or Restoring Configuration Settings
Downloading Configuration Settings from a Server
Setting the System Clock
Configuring Sntp
Setting the Time Zone
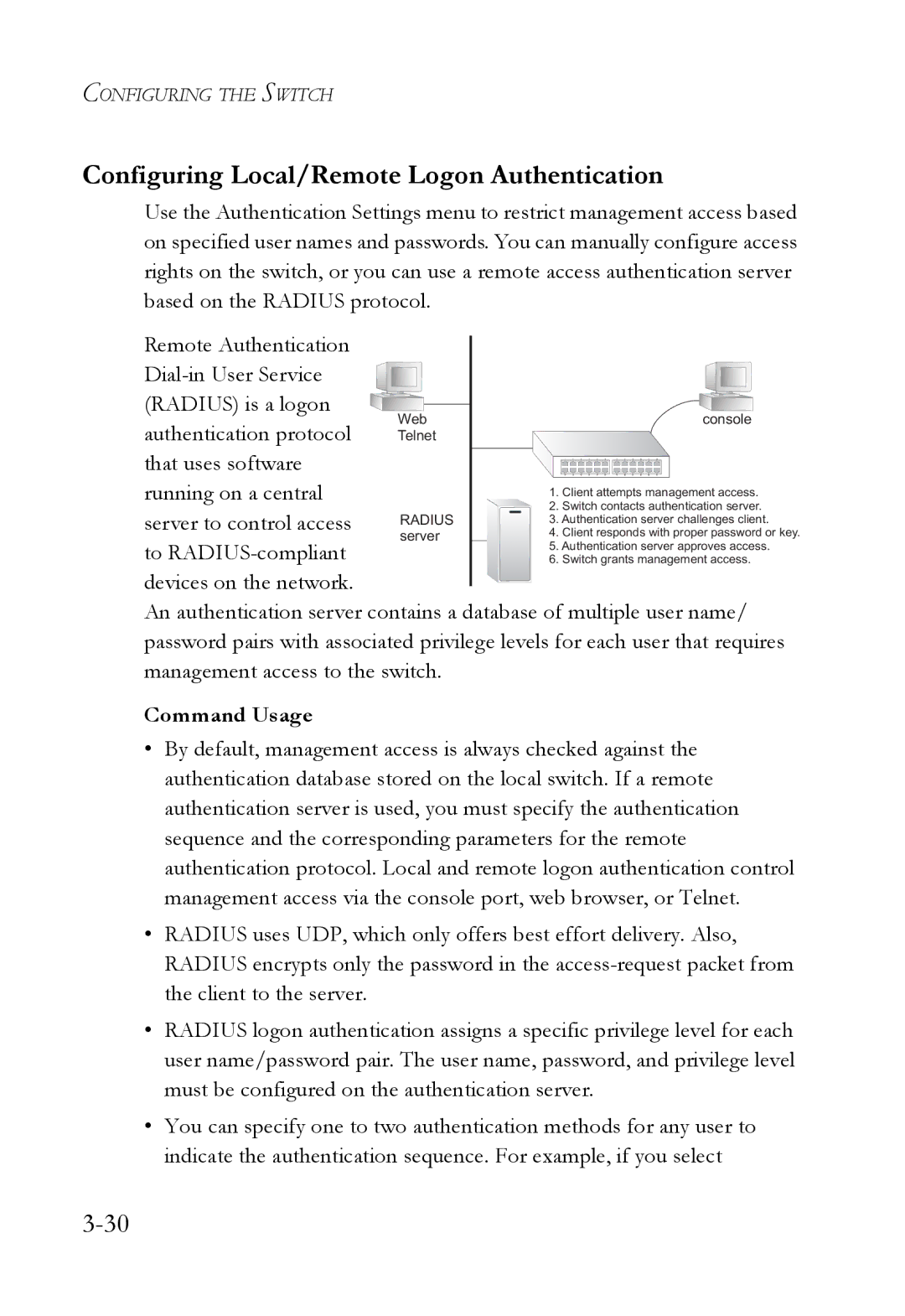
User Authentication
Resetting the System
Configuring the Logon Password
User Authentication
Configuring Local/Remote Logon Authentication
Command Attributes
Configuring 802.1x Port Authentication
User Authentication
Displaying 802.1x Global Settings
User Authentication
Configuring 802.1x Global Settings
CLI only
Configuring Port Authorization Mode
Authorized
Displaying 802.1x Statistics
Statistical Values
Eapol EAP
Access Control Lists
Configuring Access Control Lists
Setting the ACL Name and Type
ACL Configuration Setting the Name and Type
Configuring a Standard IP ACL
Configuring an Extended IP ACL
Access Control Lists
Configuring the Switch
Configuring a MAC ACL
Configuring the Switch
Binding a Port to an Access Control List
Setting Community Access Strings
Simple Network Management Protocol
Access Mode
Specifying Trap Managers and Trap Types
Command Usage
Dynamic Host Configuration Protocol
Configuring Dhcp Relay Service
101
Configuring the Dhcp Server
Address Pool Static Addresses
Enabling the Server, Setting Excluded Addresses
Configuring Address Pools
Setting the Optional Parameters
Setting the Network Parameters
Setting the Host Parameters
Creating a New Address Pool
Examples
Configuring a Network Address Pool
Configuring a Host Address Pool
CLI This example configures a host address pool
Displaying Address Bindings
Port Configuration
Displaying Connection Status
Field Attributes Web
Field Attributes CLI
Configuration
Web Click Port, Port Information or Trunk Information
Basic information
Current status
CLI This example shows the connection status for Port
128
Configuring Interface Connections
125
Setting Broadcast Storm Thresholds
Configuring Port Mirroring
131
Showing Port Statistics
Parameter Description
Etherlike Statistics
Rmon Statistics
Octets long excluding framing bits, but including
Configuring the Switch
Configuring Rate Limits
CLI This example shows statistics for port
Command Attribute
Trunk Configuration
Dynamically Configuring a Trunk
Trunk Configuration
Statically Configuring a Trunk
139
138
Address Table Settings
Setting Static Addresses
Displaying the Address Table
143
Spanning Tree Algorithm Configuration
Changing the Aging Time
Designated Root Bridge Port Root Port
Displaying Global Settings
Configuring the Switch
160
Configuring Global Settings
Global settings apply to the entire switch
Basic Configuration of Global Settings
Root Device Configuration
Advanced Configuration Settings for Rstp
Displaying Interface Settings
AD B
AD B
Configuring the Switch
Configuring Interface Settings
CLI This example shows the STA attributes for port
100
101
Vlan Configuration
Overview
102
103
Assigning Ports to VLANs
104
105
106
Forwarding Tagged/Untagged Frames
Enabling or Disabling Gvrp Global Setting
Displaying Basic Vlan Information
107
Command Attributes Web
Displaying Current VLANs
108
Command Attributes CLI
109
Creating VLANs
110
Adding Static Members to VLANs Vlan Index
111
112
Adding Static Members to VLANs Port Index
113
Configuring Vlan Behavior for Interfaces
114
115
116
117
Configuring Private VLANs
118
Enabling Private VLANs
Configuring Uplink and Downlink Ports
119
Class of Service Configuration
Setting the Default Priority for Interfaces
120
121
131
Mapping CoS Values to Egress Queues
122
123
Setting the Service Weight for Traffic Classes
124
Mapping Layer 3/4 Priorities to CoS Values
125
Selecting IP Precedence/DSCP Priority
126
Mapping IP Precedence
127
128
Mapping Dscp Priority
129
130
Mapping IP Port Priority
131
132
Copying IP Settings to Another Interface
133
Multicast Filtering
134
Igmp Protocol
135
Layer 2 Igmp Snooping and Query
136
Configuring Igmp Snooping Parameters
137
138
139
Displaying Interfaces Attached to a Multicast Router
140
Specifying Static Interfaces for a Multicast Router
141
Displaying Port Members of Multicast Services
142
Assigning Ports to Multicast Services
143
Layer 3 Igmp Query used with Multicast Routing
144
Configuring Igmp Interface Parameters
145
146
147
CLI This example configures the Igmp parameters for Vlan
148
Displaying Multicast Group Information
IP Routing
149
Initial Configuration
150
IP Switching
151
152
Routing Path Management
Routing Protocols
OSPFv2 Dynamic Routing Protocol
153
RIP and RIP-2 Dynamic Routing Protocols
Non-IP Protocol Routing
Basic IP Interface Configuration
154
Configuring IP Routing Interfaces
155
156
Address Resolution Protocol
157
158
Proxy ARP
Basic ARP Configuration
159
Configuring Static ARP Addresses
160
161
Displaying Dynamically Learned ARP Entries
162
163
Displaying Local ARP Entries
164
Displaying ARP Statistics
Web Click IP, ARP, Statistics
Displaying Statistics for IP Protocols
165
IP Statistics
166
167
Web Click IP, Statistics, IP CLI See the example on
168
Icmp Statistics
169
Web Click IP, Statistics, Icmp CLI See the example on
170
UDP Statistics
Web Click IP, Statistics, UDP CLI See the example on
171
TCP Statistics
Configuring Static Routes
172
Web Click IP, Statistics, TCP CLI See the example on
Displaying the Routing Table
173
174
228
Configuring the Routing Information Protocol
175
Configuring General Protocol Settings
176
Global Settings
Timer Settings
177
178
Specifying Network Interfaces for RIP
Configuring Network Interfaces for RIP
179
180
Specifying Receive and Send Protocol Types
Loopback Prevention
Protocol Message Authentication
181
182
183
Displaying RIP Information and Statistics
184
RIP Information and Statistics
185
Web Click Routing Protocol, RIP, Statistics
Configuring the Open Shortest Path First Protocol
186
187
188
General Information
An area border router runs a
189
Networks in two or more areas
AS Boundary Router
Default Route Information
190
191
Configuring Ospf Areas
192
Single route. The backbone or any
193
194
195
196
271
197
Configuring Ospf Interfaces
198
Detail Interface Configuration
199
Ospf Interface List
200
201
202
203
Configuring Virtual Links
204
205
Configuring Network Area Addresses
206
207
Configuring Summary Addresses for External AS Routes
208
209
210
Redistributing External Routes
211
Configuring Nssa Settings
212
Area ID Identifier for an not-so-stubby area Nssa
213
Displaying Link State Database Information
214
215
216
Displaying Information on Border Routers
217
Displaying Information on Neighbor Routers
Multicast Routing
218
Configuring Global Settings for Multicast Routing
Displaying the Multicast Routing Table
219
220
221
Configuring Dvmrp
222
Configuring Global Dvmrp Settings
223
224
225
226
Configuring Dvmrp Interface Settings
227
Dvmrp Interface Information
228
229
Displaying Neighbor Information
You can display all the neighboring Dvmrp routers
230
Displaying the Routing Table
CLI This example displays the only neighboring Dvmrp router
Configuring PIM-DM
231
Configuring Global PIM-DM Settings
232
Configuring PIM-DM Interface Settings
233
234
235
309
236
Displaying Interface Information
237
You can display all the neighboring PIM-DM routers
238
Using the Command Line Interface
Accessing the CLI
Telnet Connection
Entering Commands
This section describes how to enter CLI commands
Keywords and Arguments
Command Completion
Getting Help on Commands
Minimum Abbreviation
Showing Commands
Understanding Command Modes
Negating the Effect of Commands
Using Command History
Partial Keyword Lookup
Exec Commands
Vlan Database
Configuration Commands
Mode Command Prompt
Command Line Processing
Keystroke Function
Command Groups
Command Group Description
181
Line Commands
Command Function Mode
Line
Login local
Login
Syntax Login local no login
Line Configuration
Syntax Password 0 7 password no password
Password
Username 4-33 password
No password is specified
Syntax Exec-timeout seconds no exec-timeout
Exec-timeout
Login 4-15password-thresh4-18
CLI No timeout Telnet 10 minutes
Syntax Password-thresh threshold no password-thresh
Password-thresh
To set the timeout to two minutes, enter this command
Default value is three attempts
Silent-time
Syntax Silent-time seconds no silent-time
Syntax Databits 7 8 no databits
To specify 7 data bits, enter this command
Databits
Seven data bits per character Eight data bits per character
Syntax Parity none even odd no parity
To specify no parity, enter this command
Parity
None No parity Even Even parity Odd Odd parity
Syntax Speed bps no speed
To specify 57600 bps, enter this command
Speed
9600 bps
Syntax Stopbits 1
Stopbits
Show line
Syntax Show line console vty
General Commands
To show all lines, enter this command
Disable Enable password
Enable
Syntax Enable level
Level
Disable
None
Privileged Exec
Configure
Show history
Use this command to restart the system
Reload
End
Exit
Use this command to exit the configuration program
This example shows how to quit a CLI session
Quit
System Management Commands
Device Designation Commands
Syntax Hostname name no hostname
User Access Commands
Hostname
Name The name of this host. Maximum length 255 characters
Username
Enable password
Default is level Default password is super
Web Server Commands
Ip http port
Syntax Ip http port port-numberno ip http port
Default Setting Command Mode
Syntax Ip http server no ip http server Default Setting
Ip http server
Logging on
Event Logging Commands
Syntax Logging on no logging on Default Setting
Logging history 4-38 clear logging
Flash errors level 3 RAM warnings level 7
Logging history
Syntax Clear logging flash ram
Use this command to clear messages from the log buffer
Clear logging
Flash and RAM
Show logging
Syntax Show logging flash ram
Time Commands
Syntax Sntp client no sntp client Default Setting
Disabled
Sntp client
Sntp server
Syntax Sntp server ip1 ip2 ip3
Syntax Sntp poll seconds no sntp poll
Sntp poll
Sntp client 4-42 sntp poll 4-44 show sntp
Seconds
Sntp broadcast client
Show sntp
Clock timezone
System Status Commands
Show startup-config
Command Usage
Show running-config
Show running-config4-49
Show startup-config4-47
Use this command to display system information
Show system
Show users
Show version
Flash/File Commands
Copy
Privileged Exec
Following example shows how to download a configuration file
Delete
Use this command to delete a file or image
Filename Name of the configuration file or image name
Syntax
Use this command to display a list of files in flash memory
Dir
Whichboot
Following example shows how to display all file information
Boot system
Dir 4-57 whichboot
Authentication login
Authentication Commands
Authentication Sequence
Local
Username for setting the local user names and passwords
Radius Client
Radius-server host
Hostipaddress IP address of server
10.1.0.1
Syntax Radius-server port portnumber no radius-server port
Radius-server port
Radius-server key
1812
Radius-server retransmit
Radius-server timeout
Show radius-server
802.1x Port Authentication
Authentication dot1x default
Dot1x default
Dot1x port-control
Default Command Mode
Dot1x max-req
Syntax Dot1x max-req count no dot1x max-req
Dot1x re-authenticate
Dot1x re-authentication
Dot1x timeout quiet-period
Dot1x timeout re-authperiod
Seconds The number of seconds. Range
Dot1x timeout tx-period
Show dot1x
State- Current state including initialize, reauthenticate
Authenticator State Machine
Reauthentication State Machine
Backend State Machine
Access Control List Commands
Access Control List Commands
Access-list ip
IP ACLs
Permit, deny Ip access-group4-81 show ip access-list4-83
Permit, deny Standard ACL
Standard ACL
Permit, deny Extended ACL
Extended ACL
Ip access-group
Syntax Ip access-group aclname in no ip access-group aclname
Show ip access-list4-83
Show ip access-group
Interface Configuration Ethernet
Use this command to show the ports assigned to IP ACLs
Show ip access-list
Syntax Show ip access-list standard extended aclname
Permit, deny 4-78,4-79 ip access-group4-81
Access-list mac
Syntax Access-list mac aclname no access-list mac aclname
MAC ACLs
Permit, deny MAC ACL
No permit deny packet-format any host source source bitmask
MAC ACL
Syntax Mac access-group aclname
Mac access-group
Show mac access-group
Show mac access-list4-88
Syntax Show mac access-list aclname
Show mac access-list
Mac access-group4-87
Permit, deny Mac access-group4-87
Show access-list
Show access-group
ACL Information
Snmp Commands
Snmp-server community
Snmp-server contact
Syntax Snmp-server contact string no snmp-server contact
Snmp-server location
Syntax Snmp-server location text no snmp-server location
Snmp-server host
Snmp-server enable traps
Issue authentication and link-up-down traps
Use this command to check the status of Snmp communications
Show snmp
Example
Dhcp Commands
Dhcp Client
Ip dhcp client-identifier
Interface Configuration Vlan
Use this command to submit a Bootp or Dhcp client request
Ip dhcp restart client
Dhcp Relay
Ip dhcp restart relay
Syntax Ip dhcp relay no ip dhcp relay
100
Ip dhcp relay server
Address IP address of Dhcp server. Range 1-3 addresses
Usage Guidelines
Dhcp Server
Service dhcp
Syntax Service dhcp no service dhcp Default Setting
Ip dhcp excluded-address
Ip dhcp pool
Syntax Ip dhcp pool name no ip dhcp pool name
Network 4-105 host
Dhcp Pool Configuration
Network
Network network-number mask no network
Default-router
Default-routeraddress1 address2 no default-router
Domain-name
Syntax Domain-name domain no domain-name
Dns-server
Dns-serveraddress1 address2 no dns-server
Next-server
Bootfile
Syntax Bootfile filename no bootfile
Syntax Next-server address no next-server address
Netbios-name-server
Next-server4-109
Mixed Peer-to-peer Default Setting
Netbios-node-type
Syntax Netbios-node-type type no netbios-node-type
Broadcast
Lease days hoursminutes infinite no lease
Command Modes
Lease
One day
Host
Host address mask no host
Client-identifier
Client-identifier4-114hardware-address4-115
Hardware-address
Ethernet Ieee802 Fddi Default Setting
If no type is specified, the default protocol is Ethernet
Hardware-addresshardware-address type no hardware-address
Clear ip dhcp binding
Syntax Clear ip dhcp binding address
Show ip dhcp binding
Syntax Show ip dhcp binding address
Interface Commands
Port-channel channel-idRange
Interface
Description
Syntax Description string no description
Interface Configuration Ethernet, Port Channel
Speed-duplex
Following example adds a description to port
Syntax Negotiation no negotiation Default Setting
Negotiation
Negotiation 4-121 capabilities
Following example configures port 11 to use autonegotiation
Capabilities
Capabilities 4-122speed-duplex4-120
Negotiation 4-121speed-duplex4-120 flowcontrol
Syntax Flowcontrol no flowcontrol Default Setting
Flow control enabled
Flowcontrol
Syntax Shutdown no shutdown Default Setting
Shutdown
Switchport broadcast packet-rate
Clear counters
Use this command to clear statistics on an interface
Port-channel channel-idRange Default Setting
Syntax Clear counters interface
Syntax Show interfaces status interface
Use this command to display the status for an interface
Show interfaces status
Shows the status for all interfaces
Syntax Show interfaces counters interface
Use this command to display interface statistics
Show interfaces counters
Shows the counters for all interfaces
130
This example shows the configuration setting for port
Show interfaces switchport
Syntax Show interfaces switchport interface
Shows all interfaces
Field Description
Port monitor
Mirror Port Commands
Interface Configuration Ethernet, destination port
Interface ethernet unit/port source port
Show port monitor
Use this command to display mirror information
Unit Switch unit Port Port number
Syntax Show port monitor interface
Rate Limit Commands
Following shows mirroring configured from port 6 to port
Rate-limit
Link Aggregation Commands
Guidelines for Creating Trunks
Channel-id- Trunk index Range
Channel-group
Syntax Channel-group channel-idno channel-group
Current port will be added to this trunk
Syntax Lacp no lacp Default Setting
Lacp
140
Mac-address- MAC address
Address Table Commands
Mac-address-table static
Vlan-id- Vlan ID Range
Clear mac-address-table dynamic
Action
Show mac-address-table
Mac-address- MAC address Mask Bits to match in the address
Mac-address-table aging-time
Seconds Time in number of seconds
Show mac-address-table aging-time
Spanning Tree Commands
Syntax Spanning-tree no spanning-tree Default Setting
Spanning tree is enabled
Spanning-tree
Spanning-tree mode
Syntax Spanning-tree mode stp rstp no spanning-tree mode
Rstp
Spanning-tree forward-time
Spanning-tree hello-time
Spanning-tree max-age
Spanning-tree priority
32768
Spanning-tree pathcost method
Long method
This command limits the maximum transmission rate for BPDUs
Spanning-tree transmission-limit
Count The transmission limit in seconds. Range
Spanning-tree cost
Syntax Spanning-tree cost cost no spanning-tree cost
Spanning-tree port-priority
Priority The priority for a port. Range 0-240, in steps
Spanning-tree edge-port
Spanning-tree portfast
Spanning-tree link-type
Spanning-treeedge-port4-156
Auto
Port-channel channel-idRange Command Mode
Spanning-tree protocol-migration
Syntax Spanning-tree protocol-migration interface
Use this command to show the spanning tree configuration
Show spanning-tree
Syntax Show spanning-tree interface
161
Vlan Commands
Editing Vlan Groups
Vlan database
Vlan
Configuring Vlan Interfaces
By default only Vlan 1 exists and is active
Vlan Database Configuration
Interface vlan
Syntax Interface vlan vlan-id
All ports are in hybrid mode with the Pvid set to Vlan
Switchport mode
Syntax Switchport mode trunk hybrid no switchport mode
Switchport acceptable-frame-types4-167
Switchport acceptable-frame-types
Switchport mode
All frame types
Switchport ingress-filtering
Switchport native vlan
Switchport allowed vlan
Switchport forbidden vlan
No VLANs are included in the forbidden list
Show vlan
Use this command to show Vlan information
Displaying Vlan Information
Syntax Show vlan id vlan-idname vlan-name
Pvlan up-linkinterface-list down-linkinterface-listno pvlan
Following example shows how to display information for Vlan
Pvlan
No private VLANs are defined
Use this command to display the configured private Vlan
Show pvlan
Gvrp and Bridge Extension Commands
Syntax Bridge-ext gvrp no bridge-ext gvrp Default Setting
Bridge-ext gvrp
Show bridge-ext
Switchport gvrp
Syntax Switchport gvrp no switchport gvrp Default Setting
Use this command to show if Gvrp is enabled
Show gvrp configuration
Garp timer
Syntax Show gvrp configuration interface
179
Show garp timer
Syntax Show garp timer interface
Shows all Garp timers
Priority Commands
Priority Commands Layer
Switchport priority default
Queue bandwidth weight1...weight4 no queue bandwidth
Queue bandwidth
Queue cos-map
Queue cos-mapqueueid cos1 ... cosn no queue cos-map
Show queue bandwidth
Show queue cos-map4-186
Use this command to show the class of service priority map
Show queue cos-map
Syntax Show queue cos-map interface
Priority Commands Layer 3
Map ip port Global Configuration
Syntax Map ip port no map ip port Default Setting
Map ip port Interface Configuration
Following example shows how to map Http traffic to CoS value
Map ip precedence Global Configuration
Map ip precedence Interface Configuration
List below shows the default priority mapping
Syntax Map ip dscp no map ip dscp Default Setting
Map ip dscp Global Configuration
Map ip dscp Interface Configuration
Map ip dscp dscp-value cos cos-value no map ip dscp
192
Use this command to show the IP port priority map
Show map ip port
Syntax Show map ip port interface
Use this command to show the IP precedence priority map
Show map ip precedence
Syntax Show map ip precedence interface
Use this command to show the IP Dscp priority map
Show map ip dscp
Syntax Show map ip dscp interface
Multicast Filtering Commands
Igmp Snooping Commands
Ip igmp snooping
Syntax Ip igmp snooping no ip igmp snooping Default Setting
Following example enables Igmp snooping
Ip igmp snooping vlan static
Ip igmp snooping version
Igmp Version
Following shows the current Igmp snooping configuration
Following configures the switch to use Igmp Version
Use this command to show the Igmp snooping configuration
Show ip igmp snooping
Use this command to show known multicast addresses
Show mac-address-table multicast
Igmp Query Commands Layer
Ip igmp snooping querier
Times
Following shows how to configure the query count to
Ip igmp snooping query-count
Ip igmp snooping query-max-response-time4-203
Seconds The report delay advertised in Igmp queries. Range
Ip igmp snooping query-interval
Ip igmp snooping query-max-response-time
Ip igmp snooping router-port-expire-time
Igmp Commands Layer
Switch must use IGMPv2 for this command to take effect
Syntax Ip igmp no ip igmp Default Setting
Ip igmp
Ip igmp snooping 4-197 show ip igmp snooping
Syntax Ip igmp robustval robust-valueno ip igmp robustval
Ip igmp robustval
Ip igmp query-interval
Robust-value- The robustness of this interface. Range
Ip igmp max-resp-interval
Seconds The report delay for the last member query. Range
Ip igmp last-memb-query-interval
Ip igmp version Ip igmp query-interval4-207
Ip igmp version
Second
Syntax Ip igmp version 1 2 no ip igmp version
Show ip igmp interface
Syntax Show ip igmp interface vlan vlan-id
Use this command to delete entries from the Igmp cache
Clear ip igmp group
Deletes all entries in the cache if no options are selected
Show ip igmp groups
Displays information for all known groups
Following shows the Igmp groups currently active on Vlan
IP Interface Commands
Basic IP Configuration
Ip address
IP address Netmask
Following example, the device is assigned an address in Vlan
Ip default-gateway
Syntax Ip default-gateway gateway no ip default-gateway
Show ip interface
Use this command to display the settings of an IP interface
Ip default-gateway4-218
Show ip redirects
This command has no default for the host
Ping
Syntax Ping host count countsize size
Address Resolution Protocol ARP
Interface
Arp ip-address hardware-address no arp ip-address
No default entries
Arp
Clear arp-cache show arp
Clear arp-cache
Arp-timeout
Syntax Arp-timeout seconds no arp-timeout
Seconds 20 minutes
Ip proxy-arp
Syntax Ip proxy-arp no ip proxy-arp Default Setting
Show arp
This example displays all entries in the ARP cache
IP Routing Commands
Global Routing Configuration
Syntax Ip routing no ip routing Default Setting
Ip routing
No static routes are configured
Ip route
Show ip route
Syntax Show ip route config address netmask
Clear ip route
Syntax Clear ip route network netmask
Show ip traffic
230
Routing Information Protocol RIP
Router rip
Syntax Router rip no router rip
Timers basic
Timers basic update-seconds no timers basic
Router Configuration
Network subnet-address no network subnet-address
Router rip
Neighbor
No networks are specified
Syntax Neighbor ip-addressno neighbor ip-address
Version
Syntax Version 1 2 no version
RIP Version
Ip rip receive version
Ip rip receive version 4-236 ip rip send version
Ip rip send version
Version
238
Syntax Ip split-horizon poison-reverseno ip split-horizon
Ip split-horizon
239
Split-horizon
Ip rip authentication mode
Ip rip authentication key
No authentication
240
This example sets the authentication mode to plain text
Ip rip authentication mode
Text Indicates that a simple password will be used
Ip rip authentication key
Show ip rip
Syntax Show ip rip configuration status peer
Show rip globals
242
Show ip rip configuration
243
Open Shortest Path First Ospf
244
245
Display Information
246
Syntax Router ospf no router ospf Command Mode
Router ospf
Network area
Router-id
247
Router-idip-address no router-id
248
Default-information originate
Compatible rfc1583
RFC 1583 compatible
249
Ip route 4-227 redistribute
Timers spf
Timers spf spf-holdtime no timers spf
250
Area range
251
252
Area default-cost
Default Setting Command Usage
Area stub
Summary-address
253
Area range
Redistribute
254
Type-value
Default-information originate
Network area
255
256
257
No stub is configured
Area stub
Syntax Area area-idstub summary no area area-idstub summary
Area nssa
Area default-cost4-252
No Nssa is configured
258
259
Area virtual-link
260
261
262
Area-id None Router-id None
Show ip ospf virtual-links4-284
Ip ospf authentication
263
Ip ospf authentication-key
264
MD5 authentication is disabled
Ip ospf message-digest-key
265
Ip ospf cost
266
Syntax Ip ospf cost cost no ip ospf cost
Ip ospf dead-interval
267
Ip ospf hello-interval4-268
268
Ip ospf hello-interval
Ip ospf priority
Syntax Ip ospf priority priority no ip ospf priority
Ip ospf retransmit-interval
269
Ip ospf transmit-delay
270
Show ip ospf
271
Show ip ospf border-routers
272
Show ip ospf database
273
Following shows output for the show ip ospf database command
274
Following shows output when using the asbr-summarykeyword
275
Following shows output when using the external keyword
276
277
Following shows output when using the network keyword
278
Following shows output when using the router keyword
279
Following shows output when using the summary keyword
280
Show ip ospf interface
281
Syntax Show ip ospf neighbor Command Mode
Show ip ospf neighbor
282
Show ip ospf summary-address
Use this command to display all summary address information
Syntax Show ip ospf summary-address Command Mode
283
284
Syntax Show ip ospf virtual-links Command Mode
Show ip ospf virtual-links
Summary-address4-253
Multicast Routing Commands
Static Multicast Routing Commands
285
No static multicast router ports are configured
Ip igmp snooping vlan mrouter
286
Show ip igmp snooping mrouter
General Multicast Routing Commands
Displays multicast router ports for all configured VLANs
287
Show ip mroute
Use this command to display the IP multicast routing table
Ip multicast-routing
288
289
Dvmrp Multicast Routing Commands
290
Syntax Router dvmrp no router dvmrp Command Mode
Router dvmrp
291
Ip dvmrp Show router dvmrp
Probe-interval
292
Syntax Probe-interval seconds
Report-interval
Nbr-timeout
Syntax Nbr-timeout seconds
293
Prune-lifetime
Flash-update-interval
Syntax Flash-update-interval seconds
294
Ip-address- IP address of the default Dvmrp gateway
Default-gateway
Syntax Default-gateway ip-addressno default-gateway
295
Syntax Ip dvmrp no ip dvmrp Default Setting
Ip dvmrp
296
Ip dvmrp metric
297
Ip dvmrp metric interface-metric no ip dvmrp metric
Clear ip dvmrp route
Show router dvmrp
298
299
Default settings are shown in the following example
Show ip dvmrp route
Dmvrp routes are shown in the following example
Show ip dvmrp neighbor
300
PIM-DM Multicast Routing Commands
Show ip dvmrp interface
301
Syntax Router pim no router pim Default Setting
Router pim
302
Syntax Ip pim dense-mode no pim dense-mode Default Setting
Ip pim dense-mode
303
Syntax Ip pim hello-interval seconds no pim hello-interval
Ip pim hello-interval
304
Seconds Interval between sending PIM hello messages. Range
305
Ip pim hello-holdtime
Ip pim trigger-hello-interval
Seconds The hold time for PIM hello messages. Range
Ip pim join-prune-holdtime
306
Seconds The hold time for the prune state. Range
Ip pim graft-retry-interval
307
Seconds The time before resending a Graft. Range
Ip pim max-graft-retries
Show router pim
308
309
Show ip pim interface
Show ip pim neighbor
Syntax Show ip pim interface vlan-id
310
Appendix a Troubleshooting
Troubleshooting
Appendix B Upgrading Firmware VIA Serial Port
Upgrading Firmware VIA the Serial Port
Page
Upgrading Firmware VIA the Serial Port
Glossary-1
Glossary-2
Glossary-3
Glossary-4
Glossary-5
Glossary-6
Glossary-7
Glossary-8
XModem
Index
Index-1
Index-2
Index-3
Index-4
Snmp Snmp
Index-5
Index-6
Page
Internet