Digital Solutions Division
Radio Frequency Interference
FCC Requirements
Important Notice Music-On-Hold
Publication Information
Toshiba America Information SYSTEMS, INC. Tais
Toshiba America Information Systems, Inc
Contents
Strata CTX Configuration
Iii
Strata CTX100-S/CTX100 Installation
Rack Mount Cabinets
PCB Installation
Isdn Interfaces
Vii
IP Telephony and Qsig Over IP
MDF PCB Wiring
11-14
Peripheral Installation
Xii
Xiii
Introduction
Advises you that hardware, software applications, or data
Index
Programming Manual
General Description
User Guides
Quick Reference Guides
Xvi
Inspection
CTX28 Installation
Packaging and Storage
CTX28 FCC/ACTA Registration Numbers
Input Power
Site Requirements
Clearance and Location
Power
Environmental Specifications
Power Converter
Standard Telephone Ring Circuit Gmau and Gstu
CTX28 Cabinet
AC Power and Grounding Requirements
TB2
AC Voltage 90VAC ± 264VAC AC Current Amps max
AC Power Ground Test
To perform the earth ground test procedure
Gmau
Mount the Cabinet on the Wall
Installing the CTX28 Cabinet
To mount the Base KSU
Cover Screws Side Cover
CTX28 Base KSU Interior
Overview Instructions
PCB Installation
PCB Descriptions
CTX28 CHSU28 Cabinet circuit cards Part Title Description
Gcdu CO, CLID, DKT
Set Jumpers on the GMAU1A Motherboard
CTX28 Installation
Jumper Admin PC Real Time Debug Monitor
Install the GVMU1A Voice Mail PCB optional
Busy/Idle On = Busy OFF = Idle
To install the GCTU1A into the CTX28
Install the GCTU1A Processor
Gctu
Control/Indicator Type of Component Description Connector
To install the GCDU1A
Install the GCDU1A DKT and Loop Start Interface
GCDU1A Controls, Indicators and Connectors
GCDU1A PCB
Install the GETS1A
Install the GSTU1A
To install the GETS1A
CD1 LED
Install the HPFB-6 Reserve Power Battery/Charger
Install the BSIS1A optional
12 CTX28 Reserve Power Duration Estimates
Hardware HPFB-6
14 HPFB-6 Reserve Power Installation
Install Wiring
RS-232C Base TX Music On Hold MOH
P10 to Hpfb Battery Cord TB1 to Hpfb FG
Digital Telephone Connection
16 AC Adapter Wiring Procedure
Battery Backup Feet Meters
CTX28 KSU or Maximum line length 24 AWG Mode Pair
Loop Limits
13 Digital Telephone/DIU/DDSS Console/ADM/Loop Limits
Installation
CTX28 Secondary Protection
CTX28
MDF Wiring
14 Station Wiring for Amphenol Connector P1 on GMAU1
Pin No Signal Station
Strata CTX28
Gvmu Administration PC Connections
PPTC25-MDM
PPTC-9
Strata CTX100-S/CTX100 Overview
Strata CTX Configuration
CTX100-S and CTX100 Processors
CTX100 Cabinet Slots
Licensed Software Options
CTX100-S/CTX100 License Control
Strata CTX670 Overview
CTX670 Processor PCBs
Hardware described in this chapter. See
Network Interface
Large-scale Integrated LSI circuits
CTX670 Processor PCB Subassemblies
CTX670 License Control
Strata CTX670 Base Cabinet Interior
CTX670 Cabinet Slots
System Capacities
CTX670 Remote Expansion Cabinet
Cabinet and Slot Capacities
Station/Peripherals System Capacities
Line Capacities and Universal PCB Slots
Base & Expansion
Lines
Station Buttons per System
Station Buttons
Features
System Feature Capacities
Mute External BGM Control Relay4 Zone Relays4
CTX100 Base CTX670 CTX670 Expanded Features
Universal Slot PCBs
Station, Line and Option PCBs
Station PCBs
Digital/Standard Telephone Interface Unit Rdsu
Digital Telephone Interface Unit BWDKU1A
Interface Options
Volt Supply Internal Option R48S
CO Line PCBs Strata Net Over VoIP Interface Unit BIPU-Q1A
Caller ID Interface Subassembly Rcis
Internet Protocol IP Interface Unit Bvpu
Interface Options LAN, Internet, WAN
Isdn Primary Rate Interface Unit BPTU1 or RPTU2
CO Line PCBs Isdn U-type Basic Rate Interface Unit Rbuu
Loop Start CO Line Interface Unit Rcou
T1/DS-1 Interface Unit RDTU2
CTX100 System Processor and Option Interface PCBs
Functional Block Diagrams
BPSU672 Cabinet
CTX100 and CTX670 CO Line Side Functional Block Diagram
CTX100 and CTX670 Station Side Functional Block Diagram
CTX670 Remote Cabinet Configuration Considerations
Worksheet Description
Component Worksheets
Worksheet 1 Toshiba DKT and IP Telephones
Main Location Remote Location 1 2 3 4 5
IP Telephone Qty
Main Location Remote Location 1 2 3 45
Worksheet 2 Standard Telephone, Stratagy DK, IVP8
Miscellaneous Digital Telephone Equipment See Table
Miscellaneous Standard Telephone SLT Equipment Required
PCB
Worksheet 3 CO Line
PCB Name Slots Required Qty
Miscellaneous CO Line Equipment
Worksheet 4 Page/MOH/Control Relay
Worksheet 5 Strata CTX100 Cabinet Slots
Actu
Worksheet 5 Strata CTX100 Cabinet Slots
CTX100 Max. Capacity Configuration Examples
Bdku Adku
Bdks
Bdku Rcou Bdks Rcos
Bdku Rcou RCIU/RCIS Bdks Rcos
Bdku Rcou
Bdks Rcos
Bdku Rcou Adku
RCIU/RCIS Adku
Clid
Rcou RCIU/RCIS
CTX100 Base 40 stations and 24 T1 and/or PRI lines
34 CTX100 Base 16 stations and 48 T1 and/or PRI lines
S102 S103 S104
Bdku Bdks
RDTU2 Bdku Bdks
RDTU2 Adku Bdks
Line Ground Start only
CTX100 Analog Tie, did and/or Ground Start Lines
Strata CTX Configuration
Strata CTX Configuration
Worksheet 6 Strata CTX670 Cabinet Slots
52 Main Processor PCB/ Remote Cabinet Configuration
PCB Placement Guidelines
Rrcu PCBs Remote Cabinet Configuration Rrcu PCBs Needed at
Processor PCBs
54 Rdtu PCB Cabinet Slot Configuration
53 Remote Cabinet Data Cables and Connectors
Biou Interface PCB
T1 Digital Line PCBs
55 Bptu or Rptu PCB Cabinet Slot Configuration
Isdn PRI Digital Line PCBs
PRI Lines Slots Bptu or Rptu Bptu or Rptu cabinet slot
Isdn BRI Digital Station PCBs
Power Factor
Analog and VoIP Tie Line PCBs
Isdn BRI Digital Line PCBs
+5VDC PF
Worksheet 7 System Power Factor Check
+5VDC PF 24VDC PF
58 PCB and Power Supply Power Factors PCB Type
Telephone/Device Power Factors
Total Power Factor PF
Main Location Remote Location 4 5
CTX100
Cabinet Power Factor Check
CTX670 Cabinet 1 base Slot
CTX670
Total Cabinet PF CTX670 Cabinet Slot
24VDC PF
CTX100 AC Power Considerations
Worksheet 8 CTX Primary AC and Reserve Power
CTX670 AC Power Considerations
59 Strata CTX100 Electrical Characteristics
62 CTX100 Typical Reserve Power Duration Estimates
Reserve Power CTX100 and CTX670
CTX670 Cabinet Power Enter the Number Components Required
Number of Cabinets
APSU112
Primary/Reserve Power Cabinet Hardware
ABTC-3M
Abcs
RPSB2
BPSU672
BPSB240
BACL240
Bbdb
Local Electrical Cabinet Cabinets
Local Electrical Code Cabinet Cabinets
Local
Cabinet AC Power Component Installation
Cabinet Cabinets
Local Cabinet
Part Number Strata CTX Comments Qty Software Licenses
Worksheet 9 Software Licenses
71 Hardware Compatibility
Hardware Compatibility
Power Supply Unit
Admin Modem
Battery Distribution
Power Strip
CTX100 Installation Strata CTX100-S
Strata CTX100-S/CTX100 Installation
Cabinet Size and Weight
Side View
Power Considerations
Environmental Considerations
BTU Rating Base plus Expansion Cabinet
Alternate or Additional Ground
AC Power and Third-wire Ground Test
Remove Cabinet Covers
Installing the CTX100 Cabinet
Remove the Back Cover from the Cabinets
Cabinet Cover
Mount the Base Cabinet
Check the Base/Expansion Power Supply Jumper Plug
Base
Mount the Expansion Cabinet if required
Base and Expansion Cabinet Interior
Install Reserve Power
Reserve Battery Considerations
Install the Optional ABCS1A Battery Charger
Install the Battery Cable
Batteries/1-Cabinet Batteries/2-Cabinets
10 Cable Wiring for the Base and Expansion Cabinets Top view
12 Cable Wiring for the Base with an Expansion Cabinet
Check Power Supply Circuit Breakers and Fuses
Check the AC Power Fuses
Check the -24 Volt Circuit Breakers
14 Power Supply Connectors Top View
Check the Power Factor Indicator and Reset Button
15 Power Supply APSU112
Remove and Replace the Power Supply if required
Replacing the Power Supply
To install the ACTU2A
Set Jumpers and Install Option PCBs onto the Actu
18 Actu PCB CTX100 Processor
To Install ACTU1A
Install the Main Processor Actu PCB
Provides Comments Installs On
Install Other PCBs into the Cabinets
CTX100 Cabinet and Processor Components
Actu
Bsis
Attach and Route PCB Cables
SMDR, Smdi
Abcs
22 Avoid Improper Cable Routing
Strata CTX670
Strata CTX670 Installation
Strata CTX670 Installation
CTX670 Minimum Clearance Requirements
Installation Strata CTX670
Reserve Power
Power Considerations
Location of Approval Labels
FCC Registration Information
Cabinet Installation Considerations
Recommended Installation Sequence
Step Reference Information
Reset Circuit Breaker
Check the -24 Volt Circuit Breakers
Circuit Breaker Location and Slot Assignments see Figure
Check the Power Factor Indicator and Reset Button
Power Supply BPSU672 Removal
Power Supply Replacement
Power Factor PF alarm LED indicates
Wall Mounting the Base Top Cabinet
Mount Cabinets
Wall Mounting Expansion Cabinets
Cabinet Mounting Surface Diagram
Cabinet Cover Removal and Installation
Hanger Back Cover Hanger Hole Mounting Strip
Marking Hole Trace Upper Arch Back Cover
CTX670 Cabinet Interior
Base Cabinet
B50MT
Cable Shield
Pair Amphenol Cables Knock Out Plastic Top
Pair To MDFAmphenol Cables
Ground the System
11 Cabinet Grounding
AC Power Requirements
Install AC Power Components
Power Cabinet Hardware Option Description
Cabinet AC Power Component Description
BBTC2A-2M battery cables supplied with Bbdb Power Supply
AC/Reserve Power and Data Cabling Overview
Power Strip Cables
BBTC1A-2M Cables To Reserve Power Batteries 2 m
13 208VAC/240VAC Power/Data Cabling for up to Seven Cabinets
Cabinet AC Power Considerations
Local Electrical Code Cabinets
Local Cabinets
14 AC Power Strip Installation
15 AC Power Cords for One to Five Cabinets
16 AC Power Cords in Six or Seven Cabinets
RPSB2 or BPSB240 Power Strip
Right Side AC Power Cables Front
To AC Outlet
Bonding Connection Plates
Typical Reserve Power Duration Estimate Number of Cabinets
Install Reserve Power
Reserve Battery Cabinet Components/Cables
Reserve Power for One or Two Cabinets Wall Mount
Bbdb
Reserve Power for Three or More Cabinets Wall Mount
Batteries/1~7 Cabinets with Bbdb
Floor Mounting One or Two Cabinets
Cabinet Floor Mounting
BCCB240
Bfif
Floor Mounting Three or More Cabinets
Anchor Bolts
Mounting Screws Anchor Bolts Bfif is inside of cabinet edge
Floor Fixture Bfif
Mounting Screws
Drilled holes
Bolt Cabinets to Concrete Floor
Bolt Cabinets to Computer Room Floor
Bolt Cabinets to Wooden Floor
Strata CTX670 Installation
Three or more BCCB120 Cabinets Bfif
Strata
Batt Bccb
Battery Wire Specifications #10 AWG minimum 2 pairs 42A max
Conduit Holes to 1/2 inch trade size From
20A dedicated
Strata CTX670 Installation
PCB Option Considerations
PCB Installation Considerations
Hardware Options
Software Options
BCTU1A/BEXU1A Installation
P601
Strata CTX670 Installation
Bexu
P601 Batt
RJ45 LAN
LINK, TX, RX LED
P901 Batt
BEXU1A
To adjust the CTX670 MOH/BGM source
BECU/BBCU Installation
31 Bbcu Processor PCB
33 Installing Bexs onto Becu
Base Cabinet see Figure
Control/Indicator/Connector Type of Component Description
12 Bbcu Controls, Indicators, and Interface Connectors
Bexs
Batt
38 Remote Expansion Cabinet Connection
Remote Expansion Cabinet Unit
39 Remove/Replace Remote Cabinet Cover
Remote Cabinet Installation Instructions
Close the data cable doors
RRCU1A
Specification
42 ROMS1A Subassembly 15 Fiber Optic Specification
Status Indicators
BIT
LED
Monitor Port Pin Assignments
Monitor Port Communication Parameters
Strata CTX670 Installation
Basic Specifications
Ventilation
Space
Environmental Conditions
Location
Rack Mount Cabinets
Model BRPSU672AE135386
Move Flange Position Optional
Assemble Rack
Take Off Front and Back Covers
Take Off Base of Cabinet
Attach Cabinet to Rack
Rack Hole Positions
Reattach Cabinet to Base
Install and Attach Cabinets to Rack
Attach Amphenol Cable
Attach the AC Cable
Connect Data and Ground Cables
Verify Power Supply Settings
Install Power Strip BRPSB120A
Optional Install Reserve Power
BBDB1A
PBTC1A-3M
Install Reserve Power for Three or More Cabinets
Install Reserve Power for One or Two Cabinets
Rack Mount
Install Reserve Power Battery Distribution Box if required
Attach Front and Back Covers
Rack Mount Cabinet Grounding
Bottom Up Configuration Center back wiring
Wiring for 7 Cabinet Configuration
Top Down Configuration Back View
Front View Side View
Top Down Configuration Left Front wiring
BRPSB120A
Primary Power Cabinet Hardware
BRPSB240A
BACL240A
Front View
Front View Back View
AC Power Component Requirements
Cabinet AC Power Considerations
Power Supply Unit BRPSU672A
DC Voltage Connector Plug Pin Wires Yellow Blue White Green
Red
Circuit Breaker Location and Slot Assignments
Remove Nema 6-20P from Power Strip
Changing Plug for Power Strip BRPSB240A
Attach Nema L6-20P Plug to Power Strip
Rack Mount Cabinets
14 AC Cabling One to Five Cabinets
AC Cabling
15 AC Cabling Six to Seven Cabinets
Rrcu
Remote Cabinet Data Cables and Connectors
PCB Chapter Layout
PCB Installation
PCB Hardware/Software Options
PCB Installation Power Supply Considerations
CTX100 Actu Processor PCBs
CTX670 BCTU/BEXU Processor PCBs
Adku Installation
Adku Digital Telephone Interface Unit
Adku Hardware Options
Astu Installation
ASTU1 Wiring
Astu Standard Telephone Interface Unit CTX100 only
Astu Electrical Characteristics Description
SW2
FG1
Wire from Astu P2 plugs into Actu P8
To install the Bdks
Bdku Installation
BDKU/BDKS Digital Telephone Interface Unit
Bdku Hardware Options
BDKU/BDKS PCB
Bdku Controls, Indicators, and Interface Connectors
Biou Option Interface Units
Biou Installation
N.O
MOH1, MOH2, MOH3
R48S -48 Volt Supply Subassembly Installation
BSTU/RSTU Installation
BSTU/RSTU Standard Telephone Interface Unit
Bstu Controls and Interface Connectors
RSTU1, 2 and 3 Controls, Indicators, and Connectors
RSTU3 Controls and Interface Connectors PCB Installation
Rstu or RSTU2 Controls and Interface Connectors
Bvpu Configuration
Bvpu Installation
Bvpu Internet Protocol IP Interface Unit
11 Bvpu PCB
SW0
BWDKU1A Digital Telephone Interface Unit
BWDKU1A Installation
BWDKU1A BDKU/BDKS
BWDKU1A and BDKU/BDKS Comparison
PDKU2 Installation
PDKU2 Digital Telephone Interface Unit
PDKU2 Hardware Options
RCIU1/RCIS or RCIU2/RCIS Installation
RCIU1 or RCIU2 Installation
RCIU1, RCIU2, Rcis Caller ID Interface
14 RCIU1/RCIS PCB
To install an RCOS3A PCB
Rcos Installation Internal Option
Lights to indicate that line circuit is in operation
16 RCOS3A PCB
To install an RCOU3A or RCOU1A PCB
Rcou Installation
18 RCOU3A PCB
20 PCOU2 PCB
Rddu Direct Inward Dialing Line Interface Unit
Rddu Installation
Rddu
Installing Rsts Internal Option
Installing R48S Ring Generator Internal Option
Rdsu Installation
To install the R48S on the Rdsu
22 RDSU, Rsts PCBs PCB Installation
Pemu Installation
REMU2A and Remu Installation
RDTU2 T1 Interface Unit
REMU2A Tie Line Unit
REMU2A Tie Line Unit
24 Remu PCB
25 Pemu PCB PCB Installation
RGLU2 Installation
To install an RGLU2 PCB
RGLU2 Loop/Ground Start CO Line Interface Unit
PCB Installation
RMCU/RCMS E911 Cama Trunk Direct Interface
Rcms Subassemblies Installation
28 Rcms Subassembly stand-alone
Rmcu Installation
29 Rmcu Interface Card
20 LED Indications Normal Operation Status
Rcms LEDs
NB LED CB LED
Network Busy Customer Busy
Network Requirements
21 PCB Network Requirements
PCB/Interface Facility Interface Code Network Jack Ringer
BRI S/T Overview
PRI Overview
BRI U Overview
Isdn Interfaces
Isdn Reference Model
Strata CTX Isdn Reference Model
BPTU/RPTU Overview
CSU Requirements
Slot Assignments
Power Factor
Bptu Installation
To install an Bptu PCB
Bptu Interface Unit
BPTU1A
Bptu Cable Length Equalizer Switches
Bptu Self Test
SW4 SW5 SW6
Bptu Loop Back Jumper Plugs
Bptu Front Panel Indicators
Ferrite Core
Bptu Cabling
To install an Rptu PCB
Rptu Installation
Rptu Switches, Jumpers, and Connectors
Switches/Jumpers/Connector Description
Interfaces
Isdn
Rptu LED Functions
Rptu SW1 Cable Length Settings
Functions
SW1
Cable Length
Bptu and Rptu Cabling
Fifteen feet of CAT5 unshielded cable
Cable Installation
Ferrite Core
Ferrite Core Installation
RBSU/RBSS Interface Units
Overview
Rbsu Connection Options
RBSU/RBSS Interfaces between the S/T Reference Points
Capacity and Cabinet Slot Information
RBSU/RBSS Installation
PS-1 Backup Power Option
Set Option Switches/Jumpers
Run Related Programs
Circuit Option Type Circuit Type Description Switch
RBSU/RBSS Option Switches, Jumpers, and Connectors
Install the Rebs
Install the Rbss
Install the R40S
Modular Jack Pin Configurations
Install RBSU/RBSS PCBs into Cabinet
BRI S/T Circuit Jack TE or NT Mode
CKT1 CKT3
Monitor Jack
Power Failure Terminal Screws
RBSU/RBSS Premise Wiring Guidelines
BRI Wire Type Recommendations
RBSU/RBSS BRI Cable Jacks and Connectors
TX+
RX+
Strata CTX BRI Circuit EMC Ferrite Core Requirement
Connecting Rbsu to Network Side TE-Mode
17 Rbsu to NT1 Point-to-point Connection
Connecting RBSU/RBSS Station Devices NT-Mode
18 RBSU/RBSS NT Circuit Pinout on Passive Bus
19 Simplified Short-branched Passive Bus
RBSU/RBSS Passive Bus Configurations
To install the subassemblies Rbus
Rbuu Installation
To install an Rbuu PCB
RBUU/RBUS Interface Unit
23 Rbuu PCB
PSI1
Definition LED Off LED On LED Blinking
RBUU/RBUS Wiring Guidelines
Line-side cabling
RJ45 Jack
RJ45 Demarc Jack
Isdn Interfaces RJ11 Demarc Jack
Call Monitor Jack Cabling
Station-Side Cabling
Isdn Testing and Troubleshooting
BRI-U, LT Interface Terminal Loop Back Test
Strata System
30 Loop-back Test
Loop-back Test
Loop-back Test
Timing and Synchronization
31 Primary and Secondary References
Call Monitor Output for Isdn
PRI/BRI Call Monitoring
33 PRI Start-up and Synchronization Sequences
34 PRI Outgoing Call Connect and Release
BRI Call Monitor
35 Outgoing Call Setup Output of BRI Call Monitor
36 Incoming Call Setup Output of BRI Call Monitor
Isdn Interfaces
Select Slot Assignments
Program Channels
RDTU3 PCB
RDTU3 T1 Interface Unit
RDTU3 LED Functions RDTU3 LEDs Indication
To install an Rdtu PCB
Rdtu Installation
RDTU3 to Network
RDTU3 Cabling
RDTU3 to PBX T1 Separated More Than 655 ft
Rdtu to PBX T1 Direct Back-to-back Connection up to 655 ft
Network Jack/RDTU3 Modular Jack Pin Function
Connecting two RDTU3 PCBs
RDTU3 Equalizer Switches
RDTU3 Self Test and CSU Test Switch
RDTU3 Front Panel Indicators
RDTU3 Loop Back Jumper Plugs
Loop Back
Call Data Monitor Jack
Commands
RDTU3 Status Commands Function Format Indication
RDTU3A Call Data Information
Indicators
ALARMYAON/OFF BAON/OFF FSLON/OFF
RDTU3 Indications Timing Type
DT DHin Data Code Data Hex Meaning
DT DHin Data Code Data Hex Meaning
10 DR DHout Data Code Data Hex Meaning
RDTU1 & 2 Installation
SW1 Equalizer Switch and Loop Back Jumpers Internal Option
RDTU1 & 2 T1 Interface Unit
CTX
RDTU1A
Falm
12 RDTU1 and 2 LED Functions Alarm LED
Mfalm
Yalm
Rdtu Cable Connections
RDTU1 and 2 Cable Installation
CSU Installation
Loop Back Testing
Rdtu Self Test
Network/CSU/RDTU Span Test
Network/CSU T1 Span Test
Test Rdtu Lines
Loop Back Testing
IP Telephony and Qsig Over IP
Pre-installation Guidelines
Client Firewall Considerations
Dos and Don’ts for Setting Up the System
Methods of Estimating Bandwidth Requirements
Perform a LAN Voice Readiness Assessment
CTX
Prgs
Review Voice Quality Considerations
Above and the Codec parameters
711 at 20ms
Connect BIPU-M2A to LAN or VPN Server
Install BIPU-M2A
Indicator Definition
BIPU-M2A Interface Unit
BIPU-M2A or BIPU-Q1A Buttons, LEDs and Jumpers
Install IP Telephones
IPT Operation Notes
Over IP IP Telephony
Qsig
IPT Telephone Options
Tilt Stand Installation
IP Telephone Add-on Modules
External Speaker Unit Hesb Option
Handset/Headset Option Straps
Station Option Interface PCB Compatibility
Strap on IPT PCB Explanation
Handset Hanger
To wall mount IP telephones
Connect IPTs to Network
IPT Connections
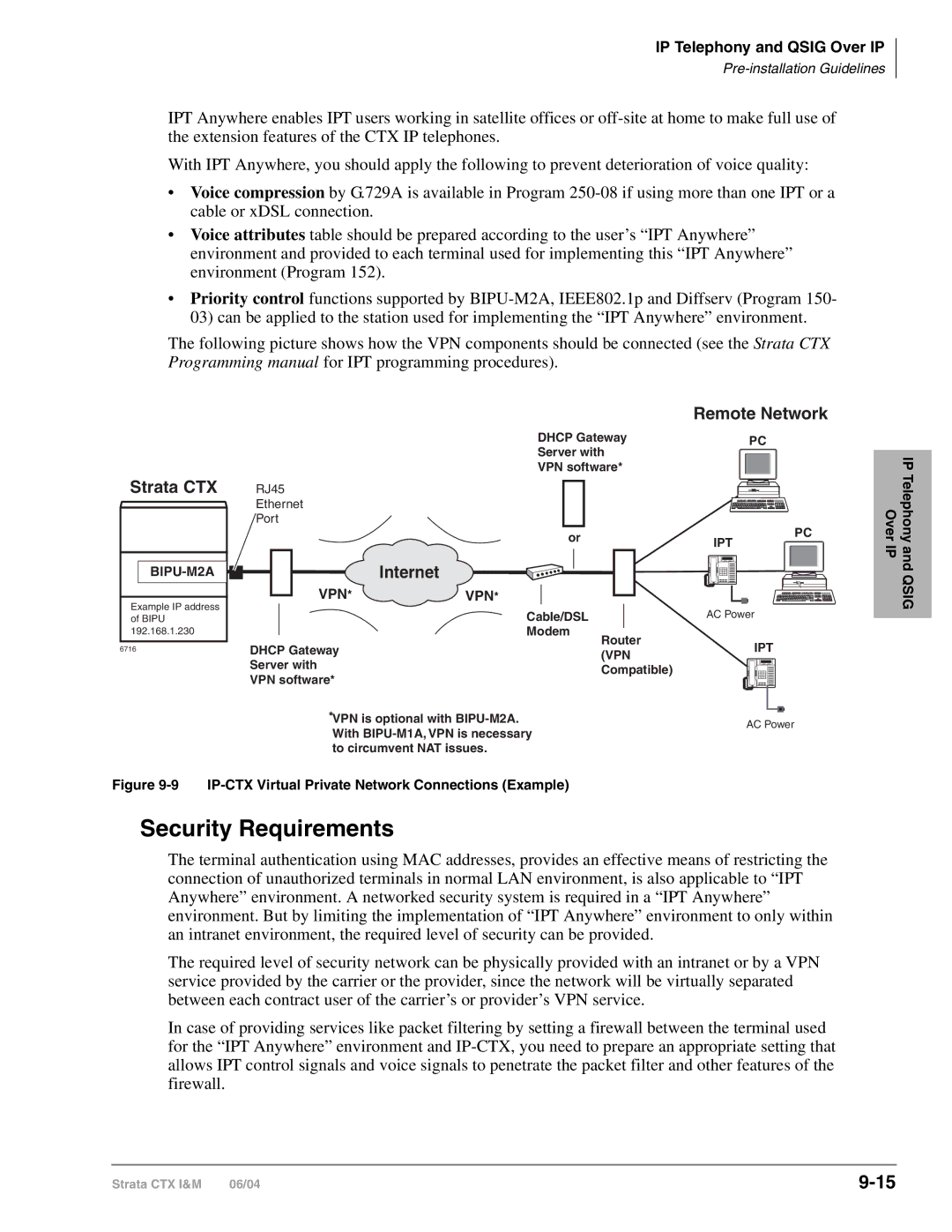
IPT Anywhere
IP Telephony and Qsig Over IP
IP-CTX Virtual Private Network Connections Example
Security Requirements
Addressing
Power over LAN
OUT
CAT5
OUT CAT5
IPT
Installing and Operating the SoftIPT
Before You Begin
Hardware/Software Required
Install SoftIPT
Start the SoftIPT
Upgrading the SoftIPT
Switching a Call to Your Headset
Making a Call
To make a call
Creating a Directory
Using the Directory to Call
To change Feature Button Labels
Labeling Feature Buttons
Uninstalling the SoftIPT
Using the Call Log
To access the Call Log
To remove SoftIPT from your PC
Application Notes for Wireless 802.11 Networks
Considerations
Wireless Recommendations
Tested Platforms
Audio Devices
PC Platforms
IP Telephone Ping Test
CTX IP Troubleshooting
7Ping Test Action LCD Indication Remarks
Ping to
Collect CTX Trace Data on CTX SmartMedia Card
LCD Network Failure Displays
Collect Bipu Logs
8LCD Network Failure Conditions LCD Indication Remarks
Bipu Reset
Check Log0.log/Log0.err for Error Message Output
Optional Data for Program Update
CTX System Configuration
Verify CTX/BIPU/IPT Hardware, Software and Firmware Version
Mandatory Data
Network Information
Network Diagram
Network Equipment that BIPU/IPT Directly Connects To
CTX100 Slot Base Exp
Protocol Name Type Use, Purpose
Capture Packets
Using Repeater Hub Dumb Hub
How To Capture Packets
Using Switching Hub with Mirroring Function
Capture Points
Using PC or Workstation With Multiple Network Interfaces
IP Troubleshooting Resolutions
10 IP Troubleshooting Problems and Resolutions
Problem Action Cause How to Resolve
LAN Problems
Problem Action Cause How to Resolve IPT Problems
Connect Error
BIPU-Q1A Strata Net Qsig over IP Interface Unit
Private Networking Over Internet Protocol
Strata Net Qsig Over IP and IPT Bandwidth Requirements
12 Qsig over IPClass Definitions Delay ms Jitter ms
Class
Kbps
Connect BIPU-Q1A to LAN, Server or Router
BIPU-Q1A Installation
MDF
10-1
Station Loop Lengths
Mode Pair Pair plus
10-2
Station Loop Lengths1
MDF PCB Wiring
10-3
Loop Limits for DKT3000-series Telephones
10-4
Station Wiring Diagrams
10-5
Adku and BDKU/BDKS Digital Station Wiring
10-6
Bwdku Digital Station Wiring
10-7
Astu Wiring
Pdku Wiring
Pdku Digital Station Wiring
Digital Telephone DSS and Ddcb External Power Connection
10-9
MDF PCB
Bdku Station MDF Cross Connect Record
10-10
KSU Slot Number
Adku Bdku Pdku Bdks
10-11
Rdsu Wiring
10-12
CKT
Port Directory Device/Standard Telephone Location Number
10-13
Rstu or Pstu Analog Devices Wiring
Port Intercom Device/Standard Telephone Location Number
10-14
10-15
Power Failure Cut Through Dpft Wiring Pin-outs
10-16
10-17
RGLU2, Rcou or Pcou Wiring
10-18
RCOU/RCOS Wiring
Wiring
10-19
10-20
RMCU/RMCS Wiring Diagram
10-21
RCIU1/RCIS or RCIU2/RCIS Wiring
10-22
Did and Tie Line Wiring
Lead PIN #
10-23
4WR1 2 4WT1
Line #4 Line #3 Line #2
10-24
Pemu Wiring
10-25
17 MDF Wiring/4-Wire Tie Line to Pemu
10-26
Option Interface PCB Wiring Diagram
Series Digital Telephones Telephone
11-1
Station Apparatus
Series Telephone Installation
Digital Telephone System Connection
11-2
Subassembly No. per Function Phone
3000 Telephone Subassembly Upgrades
Series Telephone Option PCBs
11-3
Bpci Bheu Bvsu ADM Hheu BHEU/HHEU
11-4
DKT3000 and DKT2000 Component Compatibility Series DKT
CTI
Telephone Speaker Off-hook Call Announce Upgrade Bvsu
Bvsu Upgrade Installation for DKT3000-series Telephones
11-5
Removing Telephone Base
Bvsu Installation
Telephone Headset Bheu Upgrade
Bheu Installation
11-7
11-8
Bheu Installation
Telephone Option Straps
Connector Locations
11-9
DKT3020-SD
11-10
DKT3001 Bheu Connector Location
11-11
Bpci Installation
11-12
Install Tapi Service Provider
Test/Use Tapi Service Provider
Add/Edit TSP Configuration Information
IPT Telephone
11-13
11-14
Series, IPT1020-SD Button Layouts
13 DKT3014-SDL Buttons
11-15
14 DKT3001 Buttons
11-16
Telephone Settings
Series/IPT Telephones
11-17
Speakerphone/Microphone Sensitivity Adjustment
Reset LCD Contrast for the DKT3014-SDL
11-18
Turn DKT2000 Mode On/Off
DKT2000 Mode On/Off
Msg/Feature Button Activation/Deactivation DKT3001 only
Series Telephones
Country Code Settings for Mu Law/A Law
Country Settings On/Off
11-20
Test the Display on Large LCD Telephones DKT3014-SDL only
To install DADMs
Digital Add-on Module Installation
11-21
Dadm Comparison Add-on Module DADM3020 DADM3120
15 Digital Add-On-Module
11-22
11-23
Tilt Stands
11-24
Tilt Stand Installation with Add-on Modules
11-25
21 Release Adjustment Button Station Apparatus
11-26
Tilt Stand for DKT/IPT + Two ADMs
Telephone Wall Mounting
11-27
To mount digital telephones
To wall mount DKT3001 or DKT2001 digital SLTs
11-28
Standard Telephones
Direct Station Selection DSS Console/System Connection
DSS Console Connections
11-29
11-30
Cordless Digital Telephones
Cordless Telephone Compatibility
Bdks D2
Cordless Telephone Installation
Review Safety Instructions
11-31
11-32
Place DKT3000-series Telephones into 2000-Mode
Select Location
11-33
To change DKT3000-series telephones into 2000-mode
11-34
Connect Telephone Cables
To connect as a stand-alone telephone
To connect to a Strata DKT
11-35
Connect and Apply Power
Base Unit
Charging Unit
Wall Installation Optional
11-36
Standard Wall Plate Mounting
11-37
Direct Wall Mounting
To wall mount the base unit
Charging Unit Wall Mounting
11-38
Raise the Base Unit Antenna
Install Handset Battery Pack
Charge Batteries for First Time
11-39
Attach Belt Clip Optional
Install Headset Optional
11-40
To remove the belt clip
Troubleshooting
Cordless Telephone Troubleshooting and Specifications
Troubleshooting Suggestions Condition
11-41
Cleaning Charging Unit Contacts
Low Battery
11-42
DKT2204-CT Charging Unit pictured
Simultaneous Conversation Channels
Charging Spare Battery Packs DKT2204-CT only
DKT2204-CT
DKT2304-CT
Range and Performance
Telephone Line Problems
Radio Interference
Privacy
Specifications Feature DKT2204-CT DKT2304-CT General
Specifications
11-45
Base Unit
2000 Telephone Subassembly Upgrades No. per Function Phone
Telephone Speaker Off-hook Call Announce Upgrade DVSU/ Bvsu
Series Telephones
Series Telephone Option PCBs
31 BVSU/DVSU Installation Station Apparatus
30 Speaker Off-hook Call Announce Upgrade BVSU1A
11-48
Hheu Installation
Feed Through To Hesb For HESC-65A Cable Block
SW601 HESC-65 Cable HESC-65A Cable
11-49
Locations DKT2020-SD Strap and Connector
Carbon Headset/Handset Straps
Beep Strap
11-50
11-51
External Power Straps
DIP Switches
10 DKT International DIP Switch Settings
11-52
11-53
DIP Switches
11 DKT2020-FDSP DIP Switch Settings
11-54
To use the External Microphone
37 Rfdm Plug on DKT2020-FDSP
11-55
Speech Training Mode
11-56
Special Button Operation Button
DKT 2001 Installation
To toggle full/half-duplex mode
Digital Single Line Telephone DKT2001 only
11-57
11-58
Peripheral Installation
Application PC and Server Interfaces
12-1
Network Interface Connections
12-2
Network Jack LED Indications
12-3
Network Interface Connections Peripheral Installation
Application PC or Server Direct Connection
12-4
12-5
TIA Network Wall Jack Wire Color Codes
CTX Modem Programs and Dialing Numbers
12-6
PPTC-25F
12-7
Pptc
DTE
12-8
Music-On-Hold/Background Music Interfaces
MOH/BGM Interface Connection
12-9
12-10
External Page with Biou Interface
Biou 1 or
12-11
12 Zone Page with Multiple Amplifiers
12-12
12-13
Control Relays with Biou Interface
Ddcb and Mdfb Cabling
Door Phone Wire Connections
Ddcb Wall Mounting
12-14
Calling a Door Phone
Calling from a Door Phone
Door Lock Control
Door Phone/Lock Programming
12-16
16 DDCB3 Wiring and Ddcu Door Lock PCB
To Turn the Loud Ringing Bell Feature On/Off Default is Off
Set Up the Telephone for the External Ringer Option
External Speaker Unit Hesb Options
Telephone External Ringer
Modular connector SW601 HESC-65 Cable HESC-65A Cable
HESC-65A and Bheu Installation
Telephone Bheu to External Speaker Hesb Cable Connection
12-18
Strap and Connector Locations Installation
12-19
Peripheral
12-20
21 Wiring the Telephone External Ringer with Hesb Interface
Amplified Page Speaker Option
To install the Hesb amplified speaker option
12-21
Test the Telephone External Ringer Option
To test the amplified speaker option
12-22
Talkback Amplified Page Speaker with Talkback Option
To install the Hesb amplified page speaker with talkback
12-23
To test the talkback amplified speaker
12-24
Hesb Wall Mounting
To wall mount the Hesb
One Wall Mounting Hole
Power Failure Options
Power Failure Transfer Unit
12-25
Power Failure Emergency Transfer Dpft Installation
12-26
To test the operation of the Dpft
Smdr Record Types
Station Message Detail Recording Smdr
12-27
Call Record Types
Smdr Record Format Line Column Name
12-28
Sample Call Record Explanation Rel .02 or lower Field
12-29
12-30
Record Formats Release
Smdr Record Format Software Release Line Column Name
Sample Call Record Explanation Software Release R1.03 Field
12-31
12-32
Index
IN-1
IN-2
Dtmf
IN-3
IN-4
IN-5
QSIG, 2-10,2-17,2-56,7-9
IN-6
RSTU/PSTU/RSTU2
IN-7