HP OpenView Storage Data Protector Administrator’s Guide
Legal Notices
Iii
Page
Contents
Configuring Users and User Groups
Backup
Vii
Viii
Restore
Monitoring, Reporting, Notifications, and the Event Log
Manager-of-Managers Environment
Disaster Recovery
Xii
Xiii
Customizing the Data Protector Environment
Xiv
Contents
Integrations with Other Applications
Xvi
ADIC/GRAU DAS and STK ACS Libraries
Xvii
Xviii
Edition History Part Number Manual Edition Product
Xix
Page
Xxi
Data Protector Graphical User Interface
Xxii
Documentation
General
Information Technical Support
Feedback
Xxiv
Manuals
Xxv
HP OpenView Storage Data Protector Unix Integration Guide
Xxvi
Online Help
Xxvii
Xxviii
Licensing Guide
HP OpenView Storage Data Protector Administrator’s Guide
Audience
Xxix
Organization
Xxx
Introducing Data Protector
This Chapter
Data Protector Cell Environment
How a Backup Session Works
How a Restore Session Works
Concepts Guide
Data Protector Cell Environment
Using the Data Protector User Interface
HP OpenView Storage Data Protector Graphical User Interface
Starting GUI on
Graphical User Interface
Platforms
Unix Platforms
Printing from the Data Protector Graphical User Interface
Storage Data Protector Installation and Licensing
Storage Data Protector HP StorageWorks Disk Array
Prerequisite
Elements of the Data Protector Graphical User Interface
Context List
Results Area
Scoping Pane
Results Area
Navigation Tabs
Command-Line Interface
Data Protector Online Resources
Using Microsoft Management Console MMC
Using the Online Manuals
Add
Overview of Tasks to Set Up Data Protector
Overview of Tasks to Set Up Data Protector
Configuring and Using Backup
Configuring and Using Backup Devices
Licensing Guide for details
Guide
Configuring Backup Devices
Systems
Windows
Configuring Backup Devices
How Backup Specifications, Devices, and Media Pools Relate
Configuring Standalone Devices
What Are Standalone Devices? How to Configure
Configuring
Specifying Device Type and Name
Device Chains
Configuring Standalone Devices
Recommended Segment Sizes for Specific Device File Sizes
Configuring File Devices
What Are File
File size GB Segment size MB
Handling Mount
Requests
File Devices
Specifying a Pathname for a File Device
Configuring Library Devices
Drive Index to Scsi Address Mapping
Library Device
Configuring Library Devices
Configuring Libraries with Multiple Systems
Configure a backup. See , Backup, on
Magazine
Configuring Magazine Devices
What Are
What’s Next?
Configuring Stacker Devices
Backup
Restore with
Stacker Devices
Configuring a Library for Mixed Media
Configuring Devices for Direct Backup
Configuration Procedure
Configuring XCopy Engines
Configuring Standalone Devices
Configuring SCSI-II Libraries
Configuring the libtab File
Support of New Devices
Using Several Drive Types in a Library
Using Several Drive Types in a Library
Shared Devices in the SAN Environment
OpenView Storage Data Protector Concepts Guide
Multiple System to Multiple Device Connectivity in SAN
Locking Devices Used Exclusively by Data Protector
Locking Devices Used by Multiple Applications
Direct Library Access Concept
Indirect Library Access Concept
Configuration Overview
Configuration Goals
SAN Environment Configuration
Configuration Methods
Device Autoconfiguration
Limitations
Configuration Using the SANconf Tool
Manually Configuring the Library
Manually Configuring the Devices Drives
Library Robotics
A Cluster
Defining Lock
Names
Setting Advanced Options
Summary of Device Definitions Using Lock Names
Selecting Direct Access
Manually Configuring the libtab Files
File on zala File on oda
Shared Devices and MC/ServiceGuard
Configuration Basics
File on donat
Configuring Drives
B3935-90015MC/ServiceGuard Version A.11.05 Release Notes
Creating the ATS Configuration Files
How to Configure a Floating Drive
How to Configure a Static Drive
Static Drives
Drive Cleaning
Configuring Automatic Drive Cleaning
Conditions for Automatic Cleaning
Testing the Drive Cleaning Configuration
Testing
Configuration
Busy Drive Handling
Abort
Eject
Activating Barcode Support
10 Activating Barcode Reader Support
Activating Cartridge Memory Support
11 Cartridge Memory Support Activation for a Drive
Disabling a Backup Device
Deviceoption
Disable Device
Removing a Backup Device
How to Remove a Backup Device
Renaming a Backup Device
How to Rename a Backup Device
Device Locking
Device Locking
Streaming
Device Concurrency, Segment Size, and Block
Size
Changing
13 Advanced Options Dialog Box Concurrency
14 Device Properties Dialog Box Concurrency
Segment Size
Before Changing
Number of Buffers
Block Size
Block Size in Data
Block size
Configuring Users and User
Configuring Users and User Groups
Data Protector User Rights
Switch session ownership
Start backup specification
Save backup specification
Back up as root
Data Protector User Rights
User Rights Admin Operator
Predefined Data Protector User Groups
Predefined Data Protector User Groups
Adding or Deleting a User Group
Adding a User Group
Adding New User Groups
Deleting a User Group
Adding or Deleting a User
Adding New Users
Modifying a User
Changing User Properties
Moving a User to Another User Group
Changing User Group Rights
When to Use This
Example User Configurations
Allowing Users to Restore Their Own Files
Enabling Users to Back Up Their Systems
Example User Configurations
Example User Configurations Chapter
Managing Media
Managing Media
Overview of Data Protector Media Management
Media Life Cycle
How the Media Pool Relates to Other Components
100
Chapter 101
Creating a Media Pool
Description
Properties of a Media Pool
Pool Name
Media Type
Policymedia
Non
104
Magazine Support
Media Condition
Factors
106
Adding Media to a Media Pool
How to Add
How to Add Used
Unused Media
Formatting Media
How to Format Media
Formatting Media in a Magazine
Cartridge Memory Reformat for Specific Slot
110
Formats
Recognizing Other Data Formats
Recognized
Data Protector Media Format Categories
Cartridge Memory Enabled Recognition
112
How to Import Media
Importing Media
Catalog from
Importing the Catalog from Media
Import Multiple Media
114
Importing Media in a Magazine Device
Import Catalog
How to Import a Single Medium into a Magazine What’s Next?
Import Magazine
116
Appending Backups to Media
Limitation
Appendable on incrementals only The first medium used in a
118
Using a Pre-Allocation List of Media for Backup
Selecting Media for Backup
Media Selection
120
How Media Are Selected for Backup
OFF
Setting Data Protection for Media
122
Recycling Media
Moving Media to Another Pool
How to Export
What Is Exporting
When to Export
Exporting Media from Data Protector
Modifying Media Locations
What Is a Location?
How to Modify Media Location
126
What Is a Description? Media Label
Modifying Media Descriptions
Verifying Data on a Medium
When to Verify
How to Verify Data
On a Medium
Scanning Media in a Device
List Cartridge Memory for Specific Slots
130
Information on Media
Backup Media
Checking the Condition of a Medium
Selection
Factors Influencing the Condition of Media
132
Good
Statuses of Media
Media Pools
Fair
Changing How Media Condition Is Calculated
Media Condition Property
134
Searching for and Selecting a Medium
Media into a
How to Enter
Entering a Medium into a Device
136
How to Eject
Ejecting a Medium from a Device
Bulk Eject
Notification on
Scheduled Eject of Media
Overview
Mail Slots Full
Chapter 139
Vaulting Media
140
Configuring Vaults
Moving Media to a Vault
Restoring from Media in a Vault
142
Copying Media
Restoring from a
Moving Copies
Exporting Copies
Copy
Automated Media Copying
Devices
Cleanme Request
Selection and Use
Destination Pool
Detection of Write-Protected Media
Using Different Media Format Types
148
Modifying Views in the Media Management Window
150
Backup
152
Configuring a Backup
Prerequisites
Creating a Backup Specification
Backup Session
154
Example of Creating a Backup Specification
Key Points
Create New Backup Dialog Box
156
Source Page of the Backup Wizard
Device Page of the Backup Wizard
158
Backup Object Summary
Final Page of the Backup Wizard
160
Backing Up Unix Systems
Backing Up Unix Filesystems
Files or Directories
How to Back Up
Selecting Specific
Unix Files
Backing Up Clients Using Disk Discovery
Discovery
Selecting an Entire Client to Be Backed Up
Backing Up Disks Using NFS
What Is NFS?
164
NFS Environment
Backing Up Unix Disks as Disk Image Objects
166
Chapter 167
Backing Up Windows Systems
Backing Up Filesystems Logical Disk Drives
What Is Not
Backed Up?
Private exclusion list
Filesystem
Features
Ntfs
VSS Filesystem
Chapter 171
Multiple Disk
Sparse Files
Manual Definition
Agents
Backing Up Configuration
Specifying Objects Using Manual Add
Windows NT
2000/XP/Server
2003
174
Chapter 175
Backing Up
Backing Up the Windows 2000/XP/Server 2003 System State
176
Chapter 177
Dhcp Server
Servers
Wins Server
DNS Server
Backing Up the Windows 2000/XP/Server 2003 Services
Backing Up Windows 2000/XP/Server 2003 Services
Refer to the HP OpenView Storage Data Protector Installation
180
Backing Up a Remote Storage Service Database
Backing Up the DFS
User Profiles
Backing Up Windows User Profiles, Event Logs, and User Disk
Quotas
182
User Disk Quotas
Backing Up Windows Clients Using Disk Discovery
Event Logs
How Are Disks
Selecting the Client
184
When to Use Shared Disks Backup
Backing Up Windows Shared Disks
186
Chapter 187
16 Inet Logon Option on Windows NT
188
Chapter 189
Backing Up Windows Disks as Disk Image Objects
190
Disk Image
How to Specify a
Where to Find a
Section
How to Perform a
192
Chapter 193
Backing Up Novell NetWare Systems
Backing Up Novell NetWare Filesystems Volumes
Prerequisites How to Back Up a Novell NetWare System
194
Chapter 195
Configuration Components
What Is Included
Backup?
An Incremental
Chapter 197
Client Backup with Disk Discovery
198
Backing Up NetWare Directory Services NDS
Adding NDS Objects to a Backup Specification
Mountpoint Configuration File TSANDS.CFG
200
Backing Up OpenVMS Systems
Backing Up OpenVMS Filesystems
OpenVMS System
Equivalent to a BACKUP/PHYSICAL
202
Chapter 203
Protector EVA/VA/MSA Integration Guide
Backing Up in a Direct Backup Environment
Data Protector Installation and Licensing Guide
EVA/VA/MSA Integration Guide
Backup Specification Configuration Procedure
Restore
Backing Up Oracle8i Online and Offline
Starting Direct Backup Using the CLI
Backing Up Rawdisks
206
Scheduling Unattended Backups
Planning Your
Scheduling
Conflicts
Policies
Starting Backups on Specific Dates
Starting Periodic Backups
Editing Your Backup Schedule
Skipping Backups During Holidays
Configuring Backup Options When Scheduling
Backups
Running Consecutive Backups
212
Selecting a Backup Type Full or Incremental
Backup Types
Relative Referencing of Backup Runs
214
Backup Type
How to Read Table
How to Select
Examples
Using Backup Templates
Data Protector Default Backup Templates
Options Offered by Templates
Trees
Schedule
Applying a Backup Template
218
Specification
Integration
Creating a New Template
Modifying an Existing Template
220
Chapter 221
Groups of Backup Specifications
222
26 Example of Backup Specification Groups
Group
224
Using Backup Options
226
Most Frequently Used Backup Options
Backup Options
228
Backup Options Protection
230
Logging Changing Details About Data Stored in the Database
Log All
Log Files
What Is Load
Balancing?
232
Parameters Used?
Load Balancing
How Are
How Are Objects
234
Ownership Who Will Be Able to Restore?
Setting Options for Backup Specification
List of Data Protector Backup Options
Backup Specification Options
236
Load Balancing
Available Backup Specification Options
Backup Specification Options General and Other Description
Ownership
Pre-Exec
Post-Exec
238
Reconnect Broken Connections
Object Options
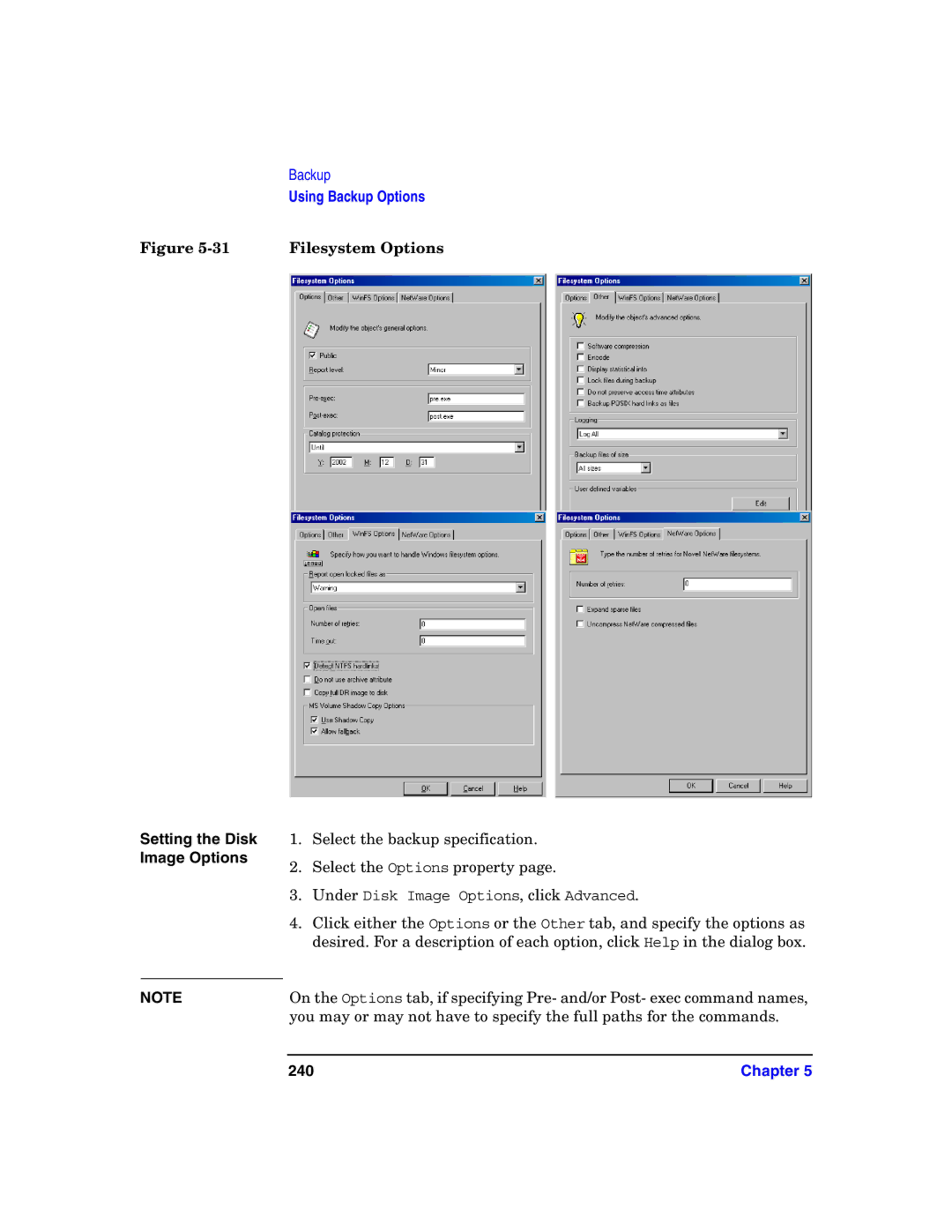
Setting the Disk Image Options
240
Setting the Object Specific Options
32 Disk Image Options
Object Properties General and Trees/Filters
242
Backup Files of Size
Backup Posix Hard Links as Files
Do Not Use Archive Attribute Windows-Specific Option
Do Not Preserve Access Time Attributes
Catalog Protection
244
Lock Files During Backup
Encode
Logging
Report Level
Protection Data Protection
Public/Private
246
Report Open Locked Files As Windows-Specific Option
Software Compression
Uncompress NetWare Compressed Files Novell Netware Specific
User Defined Backup Variables
248
Concurrency
Device Backup Options
CRC Check
Media Pool
Specific Backup Object
Pre- and Post-Exec Commands
Backup Specification
250
Pre- and Post- Exec Commands on Windows Systems
Pre- and Post-Exec Commands for a Backup Specification
Filename or
Pathname
252
Restarted
Value Description
254
Pre- and Post-Exec Commands for a Specific Backup Object
Environment Variables
256
Pre- and Post- Exec Commands on Unix Systems
How to Write the Commands
Pathname?
258
Chapter 259
Pathname 260
Environment
Variables
262
Managing Failed Backups
Preventing Backup Failure
264
Enabling Wake Onlan Support
Restarting Failed Backups
266
Restore
268
Standard Restore Procedure
Restoring Your Data
Selecting Your Data for Restore
270
Selecting Data for Restore
Selecting a Backup Version
Handling File Conflicts
Restoring Under Another Device
Specifying Restore Location
Setting Restore Options
272
Restoring Disk Images
Previewing and Starting a Restore
Aborting a Restore
Finding Needed Media
Procedure
Disk Image Objects
274
Restoring Your Data to a Shared Disk
Restoring Unix Systems
Restoring Windows Systems
Windows Filesystem Restore Limitations
How to Read This
278
Directories
Images
Restoring the Windows Configuration
Restoring Windows Configuration
280
Restoring the Windows 2000/XP/Server 2003 System State
Restoring the SysVol
Restoring the Windows Registry
Selecting System State Items
282
Restoring Windows 2000/XP/Server 2003 Services
Active Directory
Certificate
Active Directory Restore Modes
Services Restore
284
Deleted User
Restoring DFS
Restoring Windows User Profiles and Event Logs
Profiles
Restoring Windows TCP/ IP Services
286
Restoring Novell Netware Filesystems
Restoring the Novell NetWare Configuration
Restoring File Ownerships and Trustees
288
Restoring the NetWare Configuration
Restoring Novell NDS
290
What is Restored?
Restoring OpenVMS Filesystems
292
Chapter 293
General Restore
Restore Options
List of Restore Options
294
Chapter 295
Post-Exec
Commands
Pre-
296
File Conflict
Handling Options
Specific Options
User Defined Restore Variables
298
Restore Techniques
Restoring Files to Different Paths
Restoring Files in Parallel
300
When to Restore Directly from Media
Viewing Files Not in the IDB
Restoring Files in Parallel
Restoring by Query
How to Restore
Restoring Files in Use
Directly from
Restore by Query
By Query
Skipping Files for Restore
Selecting Only Specific Files Matching for Restore
304
How to Add Files
Restoring Files and Directories Manually
Manually
306
Monitoring, Reporting
308
Monitoring Sessions
Viewing Currently Running Sessions
Viewing Finished Sessions
Responding to Mount Requests
310
Chapter 311
Aborting Running Sessions
Changing the Amount of Messages Shown
312
Chapter 313
Monitoring Several Cells Simultaneously
314
Data Protector Reporting
Methods
Report Formats
Report Send
316
Backup Specification Reports
Report Types
Backup Specification Reports
318
Chapter 319
Configuration Reports
Configuration Reports
320
IDB Reports
IDB Reports
322
Chapter 323
Pools and Media Reports
Pools and Media Reports
324
Chapter 325
Sessions in Timeframe Reports
Sessions in Timeframe Reports
326
Chapter 327
Single Session Report
Single Session Reports
328
Report Formats
Html
330
Creating a New
Report Send Methods
Email Send Method
Microsoft
Snmp Send Method
Broadcast Message Send Method
Log to File Send Method
332
Chapter 333
External Send Method
334
Configuring Reports Using the Data Protector
Configuring Report Groups and Adding Reports
336
Chapter 337
Running Individual Reports
Running Report Groups
338
Chapter 339
Session Flow Report
Media Statistics Report
340
Device Flow Report
Chapter 341
Notification Types
What Are Notifications? Configuring Notifications
Data Protector Notifications
342
Data Protector Notifications
344
Chapter 345
Explanation of Some Notifications
346
Notification Send Methods
Email Send Method
348
Broadcast Message Send Method
Log to File Send Method
Snmp Send Method
350
Use Report Group Send Method
Configuring Notifications
External Send Method
Data Protector Event Log Send Method
352
Configuring Reports and Notifications on the Web
Restricting Access to Web Reporting
Copying Data Protector Java Programs to the Web Server
354
Configuring Report Groups
Generating the Reports
Event Log Deleting Event Log Contents
Data Protector Event Log
356
Event Log Message
358
Manager-of-Managers Environment
360
Centralized Media Management Database
Manager-of-Managers
Centralized management of all tasks
Centralized licensing
Configuring the Manager-of-Managers
362
Setting Up MoM Manager
Importing Data Protector Cells
Adding a MoM Administrator
Restarting Data Protector Services
364
Chapter 365
Centralized Media Management Database Cmmdb
366
Central Media Management Database
Configuring a Centralized Media Management Database
368
Configuring the Cmmdb on the MoM Manager
Cmmdb
Configuring the Cmmdb on the Client Cell
370
Chapter 371
Centralized Licensing
Setting Up Centralized Licensing
Why Use Centralized Licensing? Prerequisite Configuring
372
Releasing
Licenses
Assigning
374
Before
Moving Licenses in the MoM Environment
Enterprise
Reorganization
Deactivating Centralized Licensing
Deactivation
376
Working with a MoM Environment
Importing and Exporting Data Protector Cells
Importing a Cell Manager Exporting a Cell Manager
Moving Client Systems Among Cells
Distributing the MoM Configuration
How to Distribute the MoM Configuration
378
Configuring Data Protector Users
Managing Devices and Media for a Specific Cell
380
Managing the Data Protector
382
About the Data Protector Internal Database
Used?
Data Protector Software Release Notes
IDB Architecture
384
IDB Architecture
Mmdb
Dcbf
386
Chapter 387
Configuring the IDB
Allocating Disk Space for Future Use
388
What to Plan for in Advance
Preparing for IDB Recovery
Robustness Considerations
390
Robustness
Recommendations
To Optimize
IDB Directories
Location of IDB Directories on Unix
Location on Unix
392
Recommended Location of IDB Directories
Relocating the IDB Directories
394
Creating an Additional Copy of the IDB Recovery File
Creating a DC Directory
Creating or Relocating DC Directories
Directory
Enabling Transaction Logs
Disk Space
Why Enable
Transaction Logs?
Considerations
Selecting the Internal Database Object
Configuring the Database Backup
Recommended IDB Backup Configuration
398
During the IDB
Configuring the Database Reports and Notifications
IDB Reports
400
Chapter 401
Maintaining the IDB
402
Chapter 403
404
Reducing the IDB Growth
IDB Growth
Reducing the IDB Size
When Does Change Take Effect?
Changing Logging Level and Catalog Protection Settings
406
Changing Catalog Protection for a Session
Changing Catalog Protection for an Object
Filenames
Purging Obsolete Filenames
Extending the Database Size
Creating New DC Directories
Files?
How to Create
Creating New fnames.dat Files
Creating a New fnames.dat File
Checking the Database Size
410
Checking the Consistency of the Database
Moving the Database to a Different Cell Manager
412
Chapter 413
Restoring the IDB
Restoring the IDB to a Temporary Directory
414
Moving the IDB to the Original Location
On an Unix Cell
Manager
416
Recovering the IDB
Overview of IDB Recovery Methods
Omitting
Most
Convenient
Removing
Identifying the Level of Database Corruption
IDB Corruption
Levels
How to Identify
Corruption Level
420
Performing Guided Autorecovery
Recovery Procedure
Handling Minor Database Corruption in the Dcbf Part
422
Handling Major Database Corruption Filenames Part
Recovering the IDB Using IDB Recovery File Changed Device
424
Chapter 425
Recovering the IDB Without the IDB Recovery File
426
Chapter 427
Recovering the IDB from a Specific IDB Session
428
Chapter 429
Replaying IDB Transaction Logs
430
Recovering the IDB to a Different Disk Layout
How to Replay
432
Updating the IDB by Importing Media
434
Disaster Recovery
436
Supported Disaster Recovery Methods and Operating Systems
Introduction
Cell Manager Client
438
Computer
What Is a
Order to recover other user data
Disaster?
440
What is Offline
What is Online
Recovery?
Local/Remote
442
Planning
Preparing for a Disaster Recovery
Prepare for recovery
Plan
Consistent and Relevant Backup
Perform recovery procedures
444
Updating the System Recovery Data SRD
How to Create a Consistent and Relevant Backup?
What Is SRD?
Using
Omnisrdupdate
446
Chapter 447
Script
448
Chapter 449
Assisted Manual Disaster Recovery of a Windows System
450
Preparation
Requirements
Limitation
Has occurred
452
How to Determine the Filesystem Type from the SRD File
Type number Filesystem
454
Chapter 455
Recovery
456
Other Windows Systems
458
Disk Delivery Disaster Recovery of a Windows Client
Limitations
460
Chapter 461
462
Enhanced Automated Disaster Recovery of a Windows System
464
Chapter 465
Disk and Partition
DR Image File
466
Chapter 467
468
ISO Image
Eadr of a
Windows Client
470
Chapter 471
One Button Disaster Recovery of a Windows System
472
Chapter 473
474
Obdr Backup
Modifying an
476
Chapter 477
478
Chapter 479
Automated System Recovery
480
ASR. See the HP OpenView Storage Data Protector Installation
Hardware
482
Prerequisite Creation of ASR Set
484
Chapter 485
486
Enhanced Automated Disaster Recovery Specifics
Restoring the Data Protector Cell Manager Specifics
Making IDB consistent all methods
One Button Disaster Recovery Specifics
488
Automated System Recovery Specifics
Possible Scenarios
Advanced Recovery Tasks
Restoring the Microsoft Cluster Server Specifics
490
Disaster Recovery of a Secondary Node
Disaster Recovery of the Primary Node
Mmerge p1sApath ... p1sXpath
492
Chapter 493
494
Restoring Hard Disk Signatures On Windows
Restoring Internet Information Server IIS Specifics
496
Troubleshooting
Manual Disaster Recovery of an HP-UX Client
Concept
498
Using Custom Installation Medium
Overview
Creating a Golden Image
Swsource section
500
Chapter 501
Golden Image
502
Using System Recovery Tools
Creating Recovery Archives
504
Via the Network in the Ignite-UX Administration Guide
506
Disk Delivery Disaster Recovery of an Unix Client
Storage Data Protector Software Release Notes
Gathering
Tru64
HP-UX Example
Solaris Example
508
Preparing Backup Specification
Creating an
Auxiliary Disk
510
Chapter 511
Manual Disaster Recovery of an Unix Cell Manager
512
Chapter 513
Troubleshooting Disaster Recovery on
General Troubleshooting
Windows
Drstart reports Can not copy filename
Troubleshooting Assisted Manual Disaster Recovery
Troubleshooting Disk Delivery Disaster Recovery
Cannot Find Physical Location of Drives Selected for Disk
No Operating System Found
Troubleshooting Eadr and Obdr
Disk Delivery Disaster Recovery of a Media Agent Client
Automatic DR information could not be collected
Some Non-critical Errors Were Detected
Message
Blank Screen During Recovery
Network is Not Available During Restore
518
Auto Logon Does Not Work
Computer Freezes During Eadr
Cannot Create a CD ISO Image for Eadr of Mscs
520
Customizing the Data Protector Environment
522
How to Use Global Options
Global Options File
Most Often Used Variables
524
Locations
Using Omnirc Options
How to Use
Omnirc Options?
OB2INCRDIFFTIME and OB2CHECKCHANGETIME
526
Chapter 527
Firewall Support
Limiting the Range of Port Numbers
Chapter 529
Agent Identifiers
530
Using Both
Port Usage in Data Protector
Variables Together
532
Chapter 533
534
User Interface
Chapter 535
Configuration Diagram
536
Settings
Port Range
538
Chapter 539
Example 3 GUI Installed Inside, Other Components Installed
Outside a Firewall
540
Chapter 541
Process Port
542
Outside, Other Components Installed Inside a Firewall
Settings on
Example 4 Application Agent and Media Agent Installed
Cell Manager
544
Chapter 545
Port Range Setting on the Cell Manager Limitations
546
Troubleshooting
548
Before Calling Your Support Representative
Format of Data Protector Log Files
Data Protector Log Files
Location of Data Protector Log Files
550
Log Files and Their Contents
552
Debugging
Limiting the Maximum Size of Debugs
Ways of Debugging
554
Debug Syntax
Modified Schedule -full
Trace File Name
556
Inet Debug on Unix
Inet Debug on Windows
CRS Debug on Windows
CRS Debug in the Microsoft Cluster Environment
Sample Debugging
558
Chapter 559
560
Browsing Troubleshooting Messages
Sample Error Message Dialog
When You Cannot Access Online Troubleshooting
562
Chapter 563
Description of Common Problems
564
Data Protector Components Name Resolution
Troubleshooting Networking Communication
Hostname Resolution Problems
Host a Host B
DNS Resolution Problem
566
Client Fails with Connection Reset by Peer
Checking the TCP/IP setup
Hosts file resolution problem
568
You do not have permission to start the services
Troubleshooting Data Protector Services and Daemons
Problems Starting Data Protector Services on
Windows
MMD fails upon starting the CRS service
Changed service account properties
Specific service has not been found
570
Problems Starting Data Protector Daemons on Unix
Data Protector Cell Manager daemon could not be started
Raima Velocis server daemon could not be started
Raima Velocis server daemon is apparently not running
572
Data Protector Processes
Which Processes Run Where, and When
2000/XP/Server
Troubleshooting Devices and Media
Cannot Access Exchanger Control Device on Windows
574
Device Open Problem
Using Unsupported Scsi Adapters on Windows
Medium Quality Statistics
Error statistics Explanation
576
Medium Header Sanity Check
Protector A.05.10
Command Syntax
Cannot Use Devices After Upgrading to Data
578
Other Common Problems
Filenames Are Not Displayed Correctly in GUI
Troubleshooting Backup and Restore Sessions
Full Backups Are Performed Instead of Incrementals
580
Unexpected Mount Request for a Standalone Device
No previous full backup
Backup owner is different
Description has changed
Unexpected Mount Request for a Library Device
582
Media in the library are not formatted and the media pool
With the media used for backup has a Strict policy
Unexpected Mounted Filesystems Detected
Media in the library are formatted but are different from
Licenses available
Data Protector Fails to Start a Scheduled Session
Scheduled sessions no longer run
584
Data Protector Fails to Start an Interactive Session
Poor Backup Performance on Novell NetWare Server
Data Protector Fails to Start Parallel Restore Media
Agent on Novell NetWare Clients
Backup Protection Expiration
Troubleshooting Application Database Restores
586
Problems with non-ASCII Characters in Filenames
Licensing Guide for information
Clients
Troubleshooting Data Protector Installation
Problems with Remote Installation of Windows
588
Name resolution fails when using DNS or Lmhosts
TCP/IP protocol is not installed and configured on your
Installation and Licensing Guide
Troubleshooting User Interface Startup
No Permissions to Access the Cell Manager
Inet Is Not Responding on the Cell Manager
Connection to a Remote System Refused on Windows
Or Novell NetWare
Connection to Windows 98 Clients Fails
Troubleshooting the IDB
Problems During the Upgrade of the IDB on Solaris
592
Cell Manager crashes during the core upgrade
Core upgrade runs out of disk space
Detail upgrade runs out of memory on the system
Detail upgrade runs out of disk space on the system
594
IDB is corrupted
Problems While Running the User Interface
Libraries Executables Missing
IDB Session Manager is not running on the Cell Manager
One or several IDB data files or directories are missing
RDS service/process cannot be started
Data Files Directories Missing
596
Temporary Directory Missing
Data Protector GUI cannot connect to the Cell Manager
Problems During Backup and Import
MMD is terminated during the IDB backup or import session
598
Performance Problems
DC binary files are corrupted or missing
Number of IDB objects and IDB objects sizes are too large
Mmdb and CDB Are Not Synchronized
600
Chapter 601
Troubleshooting Reporting and Notifications
602
Troubleshooting Data Protector Online Help
Troubleshooting Online Help on Windows
Troubleshooting Online Help on Unix
Viewing
604
Check Whether Data Protector Functions Properly
Data Protector Checking and Maintenance Mechanism
Maintenance
Tasks
User Check Failed Notification
606
Overview of Items to Be Checked
Check the Data Protector Cell Manager
Inspect the Data Protector log files
Check whether backups are configured properly
Verify the Data Protector installation
Run the Notifications Checks
Check Other System Resources
610
Integrations with Other Applications
612
Cluster Integrations with Data Protector
Cluster Concepts and Terminology
Typical Cluster
614
Or Group?
What is a Package
What Is a Virtual
Server?
Cluster-Aware Databases and Applications
616
Microsoft Cluster Server Integration
Licensing Microsoft Cluster Server
Clients on Microsoft Cluster Server
Installation
Cell Manager on Microsoft Cluster Server
618
Backing Up Data in a Cluster Mscs
Backing Up Shared Disks
Managing Cluster-Aware Backups
Backing Up Local Disks
620
Failover of Data Protector
Failover
622
Failover of Application Other Than Data Protector
624
Aborting Sessions Based on Elapsed Session Time To balance
Command Line
626
MC/ServiceGuard Integration
Cell Manager on MC/ServiceGuard
Licensing and MC/ServiceGuard
Prerequisites for Configuration
Protector Installation and Licensing Guide for instructions
628
Configuring the Primary and Secondary Cell Managers
Configuring Primary Cell Manager
630
Secondary Cell Manager
632
Configuring the Cell Manager Package
Protector Package
Configuration File
Modifying
634
Modifying the Control File
636
Clients on MC/ServiceGuard
Installation
Configuration
Backing Up Data in a Cluster MC/SG
638
About Backing Up Database Applications
Veritas Cluster Integration
Clients on Veritas Cluster
640
Chapter 641
Novell NetWare Cluster Integration
Clients on Novell NetWare Cluster
642
Backing Up Shared Cluster Pools
What Can You
What Is DSI?
Data Source Integration DSI
Measure?
Chapter 645
Application Response Measurement ARM Integration
Measured?
646
Chapter 647
Integration?
ManageX Integration
ManageX
Supported?
Introduction
Access Points for System and Management Applications
Data Protector Access Points
Snmp Traps
Enterprise Event ID
650
Variables
Generic Event ID
Specific Event ID
Data Protector Snmp Traps Format
Data Protector Log Files
Windows Application Log
652
Examples
Verifying Data Protector Processes
Data Protector Health Check Failed Notification
Getting the Results of the Last Night’s Backup
654
ADIC/GRAU DAS and STK ACS Libraries
656
ADIC/GRAU DAS and STK ACS Integrations
Data Protector and ADIC/GRAU DAS Library Systems Integration
Data Protector and StorageTek ACS Library Integration
Configuration Basics
Media Management Basics
660
Additional Media Management Tips
Preparing for Installation
Direct Access to the Library Installation and Configuration
Connecting Library Drives
ADIC/GRAU DAS Library Device
Chapter 663
Installing the DAS Media Agent
Installing the DAS Media Agent on a Windows System
664
Remote
Installing the DAS Media Agent on a 32-bit HP-UX System
666
Chapter 667
Installing the DAS Media Agent on an AIX System
668
Using the Data Protector GUI
Using Data Protector to Configure Drives
670
Using Data Protector to Access the ADIC/GRAU Library
Searching for a Medium
Entering Media
Ejecting Media
672
Initializing
Adding Media to a Media Pool
Initializing Media
Individual Media
Initializing Multiple
Media in a Library
674
Querying the ADIC/GRAU DAS Server
Verifying Media
Scanning Media
Modifying Media Attributes
676
Read-only window
Moving Media
Getting Information about Media
Recycling Media
Removing Volsers
Exporting Media
678
Importing Media
Direct Access to the Library Installation Configuration
STK ACS Library Device
680
Installing the ACS Media Agent to Use the StorageTek
Installing the ACS Media Agent on a Windows System
Library
682
Chapter 683
Installing the ACS Media Agent on a 32-bit HP-UX System
684
Chapter 685
Using Data Protector to Configure the STK ACS Library
686
Using Data Protector to Access the STK ACS Library
Searching for Media
688
Chapter 689
Initializing Multiple Media in a Library Device
690
Chapter 691
692
Querying the STK Acslm Host
Removing Media
694
Chapter 695
696
Troubleshooting Library Installation Configuration
698
Chapter 699
700
Further Information
This Appendix
Backing Up and Restoring Unix Specifics
VxFS Snapshot
Pre- and Post- exec Script Templates
Example A-1 Pre- exec Script Template
Example A-2 Post- exec Script Template
MOUNTPOINT=$1
Data Protector Commands
Network
Performance Considerations
Infrastructure
Datastream Local Datastream
Using Hardware in Parallel
High Performance Hardware Other Than Devices
Configuring Backups and Restores
Device Streaming
Block Size
Full and Incremental Backups
Hardware Compression
Image Backup Versus Filesystem
Object Distribution to Media
Miscellaneous Performance Hints
On Novell NetWare
Add the Report to the Report Group and Configure It
Example of Scheduled Eject of Media
Schedule the Report Group
Copy the Script to the Specified Directory
Arguments
Example of Scheduled Eject of Media
Function
Main
Example of Scheduled Eject of Media
Examples of Pre-Exec and Post-Exec Commands for Unix
Session Pre-Exec Shut Down Application
Filesystem #!/bin/sh Pre-Exec Report Usage
Session Post-Exec Application Startup
Disk Image Post-Exec Mount Disk After Raw Volume Backup
Filesystem Post-Exec Log Backup for the Record
Post-Exec Notify User
Examples of Pre-Exec and Post-Exec Commands for Unix
Disaster Recovery Move Kill Links on HP-UX
Creating a libaci.o on AIX
OmniBack
03.5x and A.04.x
Full path to the library archive file is Daspath /libaci.a
Example of the Package Configuration File
Configurednode
Failbackpolicy Manual
Haltscript /etc/cmcluster/ob2cl/ob2cl.cntl
Dbservice
Deferred
# RESOURCEUPVALUE= Upup
# Resourceupvalue
#RESOURCESTARTAUTOMATIC/DEFERRED
Nodefailfastenabledno
# Volume Group Activation
Example of the Package Control File
# Volume Groups
# Filesystems
FSMOUNTOPT0= # Filesystem Unmount Count
# Service Names and Commands
Example of the Package Control File
Data Protector Log Files Example Entries
Debug.log
IpcGetPeer Could not expand ConnectionIP
Sm.log
Inet.log
Media.log
Upgrade.log
Data Protector Log Files Example Entries
Windows Manual Disaster Recovery Preparation Template
Table A-1
Changing Block Size on Windows Media Agent
Changing Block Size on Windows Media Agent Appendix a
Glossary
Backup device
Backup API
Backup chain
Backup generation
Backup specification
See also HP StorageWorks Virtual Array LUN
BC HP StorageWorks Disk Array XP specific term
BC HP StorageWorks Virtual Array specific term
BC Process EMC Symmetrix specific term
See also BC and BC Process Boolean operators
Boot volume/disk/partition
See also SAPDBA, Brbackup
See also SAPDBA, Brarchive
Cell
See also data protection
See also Mmdb CDF file Unix specific term
Cell Manager
Centralized Media Management Database Cmmdb See Cmmdb
Client backup
Client backup with disk discovery
Client or client system
Concurrency See Disk Agent concurrency
Command-line interface
COM+ Registration Database
Data protection
Database library
Data Protector user account
Data stream
Database parallelism
Differential backup
Delta backup
See also backup types Device
See incremental backup Differential backup MS SQL specific
Directory Store DS MS Exchange specific term
See also Information Store MDB Disaster recovery
Directory junction Windows specific term
Disk Agent
Distributed File System DFS
Disk image rawdisk backup
Disk quota
Domain controller
Drive
EMC Symmetrix Command-Line Interface Symcli EMC Symmetrix
Enterprise Backup Environment
Drive index
Extensible Storage Engine ESE MS
Event Logs
Exchanger
Failover
Full backup
File Replication Service FRS
See also Primary Volume, and MU numbers Fnames.dat
See also backup types
Host backup See client backup with disk discovery
Full database backup
Full mailbox backup
Global options file
HP OpenView Smart Plug-In SPI
Hosting system
HP OpC
HP StorageWorks Virtual Array
See also backup types Incremental mailbox backup
See also exporting media Incremental backup
See also backup types Incremental backup MS Exchange
Incremental1 mailbox backup
Information Store MDB MS Exchange specific term
Initializing See formatting Installation Server
Inet
See also Directory Store DS Initialization Parameter File
IP address
Internet Information Server IIS
Windows specific term
Isql Sybase specific term
Lights-out operation or unattended operation
Local and remote recovery
Library
LISTENER.ORA Oracle specific term
Logging level
Login information to the Oracle Target
Logfull shell script Informix Unix
Logical-log files
Lotus C API Lotus Domino Server specific term
Magic Packet See Wake Onlan
Media condition factors
Media allocation policy
Media condition
Media ID
Media usage policy
Media set
Media type
Merging
MoM
Microsoft Volume Shadow Copy service VSS
See also shadow copy, shadow copy provider, writer
Mount point
Obdrindex.dat
Offline recovery
See also first level mirror Multi-drive server
Obdr capable device
See also archived redo log
Online backup
On-BarInformix specific term
OpC
Original system
Original unit ZDB specific term
See also merging
Package MC/ServiceGuard and Veritas Cluster specific term
Parallel restore
Pair status HP StorageWorks Disk Array XP specific term
Physical device
Pre- and post-exec commands
Parallelism
See also pre-exec
Public/private backed up data
Rawdisk backup See disk image backup
Public folder store MS Exchange 2000 Server specific term
RAID Manager XP HP StorageWorks Disk Array XP specific term
RecoveryInfo
Recovery Catalog Oracle specific term
Recovery Catalog Database Oracle specific term
Recovery Manager Rman Oracle specific term
Reparse point Windows specific term
Removable Storage Management
Database Windows specific term
Replica unit ZDB specific term
Scan
See also replica storage pool Restore session
Rman Oracle specific term See Recovery Manager
Scanning
Shadow copy set MS VSS specific term
Scheduler
Session key
See also shadow copy
See ZDB tape backup
See split mirror backup
Split mirror backup EMC Symmetrix
Shared disks
SRD file
Split mirror backup HP StorageWorks
Disk Array XP specific term
Sst.conf file
See also integrated security Storage Group
Stackers
Standard security MS SQL specific term
StorageTek ACS library
Symmetrix CLI Database File
Symmetrix Command-Line Interface
System Backup to Tape Oracle specific term
System databases Sybase specific
Tablespace
System volume/disk/partition
See ZDB disk backup
Target R2 device EMC Symmetrix
Transaction backup Sybase and SQL specific term
Terminal Services Windows specific term
Transaction backup
Transaction log backup
Unattended operation See lights-out operation User account
Transaction log table Sybase specific term
TSANDS.CFG file Novell NetWare specific term
User disk quotas
Verify
Volume group
Vaulting media
See also original unit and replica unit Virtual server
VxVM Veritas Volume Manager
Volume mountpoint Windows specific term
See Microsoft Volume Shadow Copy service VxFS
Windows Configuration backup
XCopy engine direct backup specific term
See zero downtime backup ZDB
Xbsa interface Informix specific term
See also zero downtime backup ZDB
ZDB part of the IDB ZDB specific term
Glossary
Index
Index
626
Bdacc
633
See Centralized Media Management Database
340
See IDB
440
Preparation, Windows NT/2000 client
111
116
618
Limiting port range, firewall environment
Index
149
NDS
622
Index
174
Index
Scsi ID
NT Configuration
Use Shadow Copy, object specific option
Index
VSS
XCopy engine, 39