Administration Guide
Published 2012-09-24 SWD-20120924140022907
Contents
Configuring security options
101
111
136
168
206
217
247
266
292
328
337
369
392
423
493
498
Document revision history
Overview BlackBerry Enterprise Server
Date Description
Device before assigning the device to a new user
Task Chapter Create administrator accounts
Troubleshooting IT policies
User account
On BlackBerry devices
Task Chapter
Optional tasks Task Chapter
Task Chapter
Database
Components and for the BlackBerry Configuration
Server
Files
Related information
There is a problem with this websites security certificate
Click Log
Click View certificates
This connection is untrusted
Click Trusted Root Certification Authorities. d Click OK
Close and reopen the browser
Close and reopen the browser
Preconfigured administrative roles
Creating administrator Accounts
Administrative roles and permissions
Administration GuideCreating administrator accounts
Administration GuideCreating administrator accounts
Administration GuideCreating administrator accounts
Administration GuideCreating administrator accounts
Create a role
Creating roles
Create a role based on an existing role
Create an administrator account
Click Create an administrator user
Add an administrator account to a group
Click Manage users
Click Edit user
Create a group to manage similar user accounts
Assign a BlackBerry device to an administrator account
Administration Guide
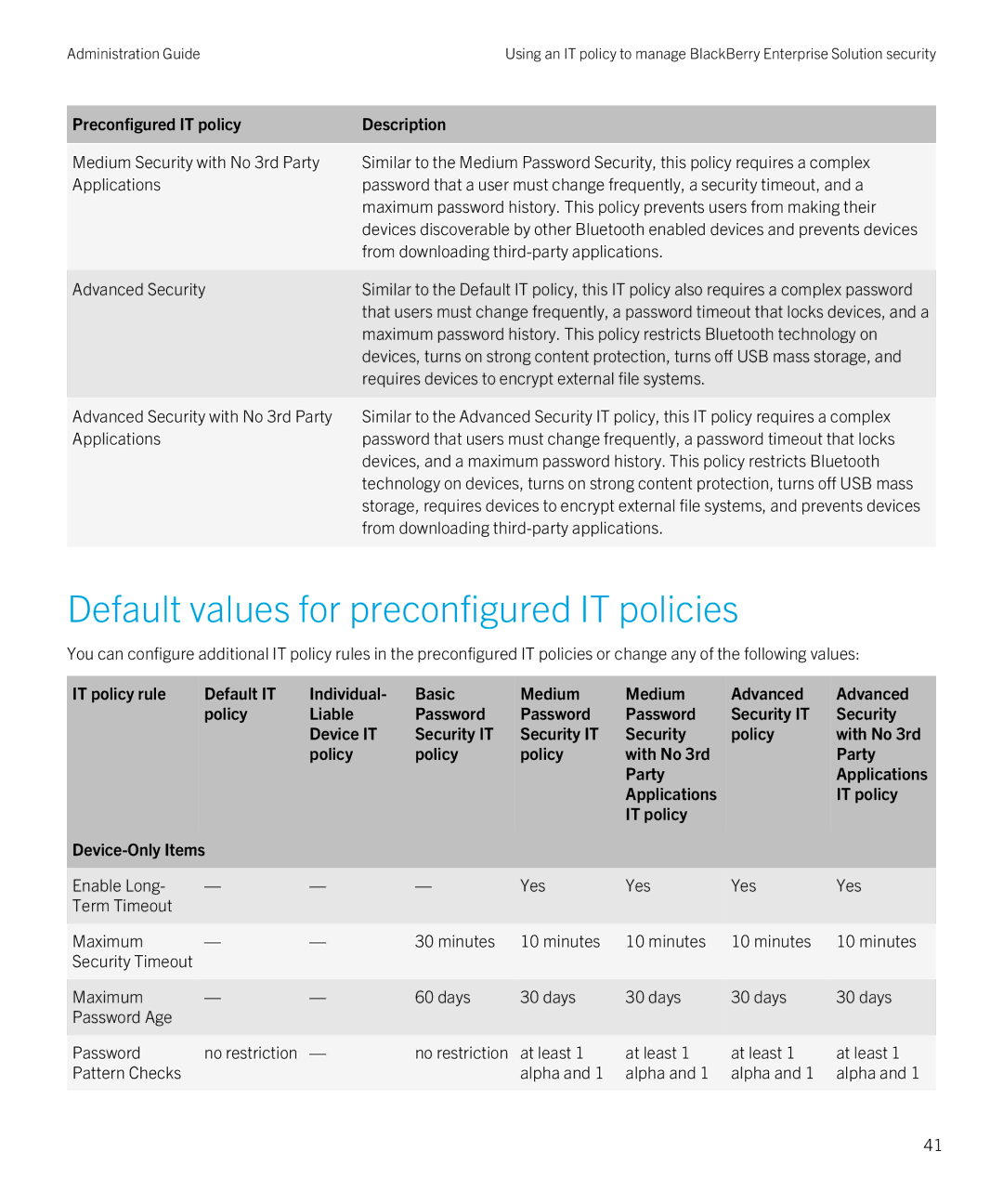
Preconfigured IT policy Description
Preconfigured IT policies
From downloading third-party applications
Default values for preconfigured IT policies
Advanced Security
Requires devices to encrypt external file systems
Maximum Password History
Password policy group
RIM Value-Added Applications policy group
Security policy group
Disable Address Yes Book Transfer Discoverable Mode
Allow Other Yes Calendar Services Message
Bluetooth policy group
Creating and importing IT policies
Wireless Software Upgrades policy group
Create an IT policy
Click Create an IT policy
Import IT policy data
Create an IT policy based on an existing IT policy
Click Edit IT policy
Click Manage IT policies
Click Add all IT policies Related information
Change the value for an IT policy rule
Import IT policy rules from an IT policy pack
Assign an IT policy to a user account
Assign an IT policy to a group
Click Manage groups
Click Save all Related information
Resend an IT policy to a BlackBerry device automatically
Sending an IT policy over the wireless network
Resend an IT policy to a BlackBerry device manually
Expand BlackBerry Domain Component view
Assigning IT policies and resolving IT policy conflicts
Click Edit instance
Method Description
Scenario Rule
Option 1 Applying one IT policy to each user account
Click Manage IT policies Click Set priority of IT policies
Option 2 Applying multiple IT policies to each user account
Rank IT policies
Yes setting is applied for this rule
Highest in the BlackBerry Administration Service
You add a new user account to a
Groups that the user account belongs
To No. You ranked IT policy a higher
Default value of Yes. You assign
Select two or more IT policies Click Preview
Click Manage IT policies Click Preview resolved IT policies
Click Create an IT policy rule
Create an IT policy rule for a third-party application
Click Manage IT policy rules
Export all IT policy data to a data file
Click Export
Click Download file
List of IT policies, click an IT policy
Delete an IT policy
Configuring security options
Managing device access to the BlackBerry Enterprise Server
Click BlackBerry Enterprise Server Click Edit component
Turn on the Enterprise Service Policy
Configure the Enterprise Service Policy
Extending messaging security to a BlackBerry device
Permit a user to override the Enterprise Service Policy
Extending messaging security using PGP encryption
Extending messaging security using S/MIME encryption
Configure encryption options for S/MIME-protected messages
Click Restart instance Related information
Create a message classification
Enforcing secure messaging using classifications
Order message classifications
Click BlackBerry Domain
Delete a message classification
Generate a PIN encryption key
Restart the BlackBerry Enterprise Server
External services turned on drop-down list, click No
Administration Guide
Has elapsed To the desired time for example, 10 minutes
Remove decrypted content from BlackBerry device
Scenario Recommendation
Best practice Description
Configuring the BlackBerry Enterprise Server environment
Best practice Running the BlackBerry Enterprise Server
Click Edit instance
Click Save all
Click Save all Related information
Administration Guide
Before you begin
Turn off Web Proxy Autodiscovery Protocol
Address field, type the URL for the PAC file Click OK
Task Steps
Delete credentials for Http basic authentication
Type traittool -global -trait BASProxyBasicAuthUID -erase
Type traittool -BASServer name -trait BASProxyBasicAuthUID
Click Save all Related information
Configure support for Unicode languages
Configuring support for Unicode languages
Type regedit
Click OK Perform one of the following actions
Restarting BlackBerry Enterprise Server components
Related information
Type regedit
Creating user groups
Configuring user accounts
Create a group to manage similar user accounts
Add user accounts to a group
Adding a user account to the BlackBerry Enterprise Server
Add to user configuration list, click Add group
Add a user account
Click Create a user
Click Create a user with generated activation password
Click Create a user with activation password
Click Create a user without activation password
Option Step
Save the .csv file
Export a list of user accounts
Field Description
Fields in a .csv file that contain user account information
Elapses
Import multiple user accounts from a .csv file
Click Continue
Preparing to distribute a BlackBerry device
Assigning BlackBerry devices To users
Method
BlackBerry Administration Service
Assigning BlackBerry devices to user accounts
Click Associate user Click Assign current device
Wi-Fi network
Save bandwidth by synchronizing organizer data over the LAN
Wireless activation
Click Default
Password expire earlier than the default value of 48 hours
Activation passwords
Intended user
Cannot reuse it to activate another BlackBerry device
Customize the activation message
Customize the activation password
Send an activation password to a user
Option 3 Activating BlackBerry devices over the LAN
Send an activation password to multiple users
Click Specify an activation password
Administration Guide
Administration Guide
100
Activate a Wi-Fi enabled BlackBerry device
Click Enterprise Activation
Check the health of a BlackBerry Enterprise Server
Configuring BlackBerry Enterprise Server high Availability
Click High availablity summary
101
How the BlackBerry Enterprise Server uses health parameters
Defining when failover occurs
Administration Guide
Changing the promotion threshold and failover threshold
Health parameter Description
Click Edit Automatic Failover settings
Attachment viewing
Provide services for attachment viewing
This health parameter
Threshold so that they are below this health parameter
107
108
Administration Guide
Verify that the failover event occured
Click Manual Failover
Click Yes Failover to standby instance
111
112
Click Turn on automatic connections failover
113
Click Edit instance
Click Save all
Create a BlackBerry Router pool for high availability
Related information
118
119
Restart the BlackBerry Administration Service instances
Related information
Availability state for the instances changes automatically
122
Remove a BlackBerry Attachment Service instance from a pool
124
Remove a BlackBerry Router instance from a pool
Click Edit instance or Edit host instance
Verify that the DNS server is running 125
Stop the BlackBerry Enterprise Server instances
Configuring database mirroring
Start the BlackBerry Enterprise Server instances
128
129
Click Resend database mirroring parameters
Stop the BlackBerry Enterprise Server instances
131
Select Overwrite the existing database
Click Replication
Right-clickLocal Publications. Click New Publication
Accept or change the default schedule. Click Next
Select By impersonating the process account
Click OK. Click Next
Click Finish 133
Right-click the server. Click Properties
Start the BlackBerry Enterprise Server instances
135
Configuring a new mirror BlackBerry Configuration Database
136
137
Preparing to distribute BlackBerry Java Applications
138
Click BlackBerry Administration Service Click Edit component
Add a collaboration client to the application repository
Click Add or update applications
Click Add application
Click Publish application
Specify keywords for a BlackBerry Java Application
Configuring application control policies
Standard application control policies
Click Manage applications
Change a standard application control policy
Click Manage default application control policies
Application control policy Description
Click Edit application control policy
Create an application control policy
Perform any of the following tasks
For required BlackBerry Java Control policy Applications
Policy
IT policy rules take precedence on smartphones
Application control policies for unlisted applications
144
Click the application control policy that you created
145
Creating software configurations
Click Manage software configurations
Create a software configuration
Click Create a software configuration
Click Add to software configuration Click Save all
Assign a software configuration to a group
Click a group
147
148
Assign a software configuration to multiple user accounts
Assign a software configuration to a user account
Complete the instructions on the screen 149
View the status of a job
Error messages BlackBerry Java Application tasks
View the status of a task
Click Manage deployment jobs
Device timed out waiting for module
QueueModule failed, processing stopped
Device reported insufficient privileges to install module
Device reported insufficient memory to install module
Incomplete ACK data for Appd request
152
Error messages BlackBerry Device Software tasks
Available upgrade rejected
Upgrade prompt deferred
Available upgrade deferred by user
Upgrade rejected
Upgrade failed, rollback complete
Restore failed -- error getting value
Error messages Standard application settings tasks
Failed to backup data to database
Failed to set properties for item
Error messages IT policy tasks
Invalid password Set Password Failed
Reject Security Violation Reject Authentication Failed
Stopping a job that is running
158
Stop a job that is running
Click View users with application
Administration Guide
On the BlackBerry device
Reconciliation rules BlackBerry Java Applications
Scenario Rule
Reconciliation rules BlackBerry Device Software
Reconciliation rules Standard application settings
Scenario
Reconciliation rules Application control policies
If unlisted applications are defined as disallowed in a
You ranked highest in the BlackBerry Administration
As disallowed is assigned to a user account. a software
Unlisted applications are not permitted on the BlackBerry
168
Device to the computer
Loader
Loader tool
Desktop Software
170
BlackBerry device
User’s computer
BlackBerry APIs and Java ME standard on BlackBerry devices
BlackBerry Java Application
171
Windows 2000 or later, Windows XP, or Windows Vista 172
Web server
Enable the BlackBerry Application Web Loader on a web server
Administration Guide
175
Before you begin
Administration Guide
BlackBerry device
179
Install the BlackBerry Java Application on a web server
Click Download
180
181
Click Save all After you finish
Click Save all
183
Administration Guide
Related information
Click Save all Related information
187
Administration Guide
Add a certificate for the BlackBerry MDS Connection Service
Task Steps
Administration Guide
Click MDS Connection Service Click Edit component
193
194
Click MDS Connection Service
Click the Edit icon beside the Ldap server
Service URL
Default base query for some Ldap servers
Base Query
Each query
Change a configuration for an
Use to authenticate with the Dsml certificate server
Authenticate with the Dsml certificate server
Click Save all
Type the CRL server name and the web address for the server
199
200
201
Configure global login information for intranet site access
On the Http tab, click Edit component
Click Edit instance
203
Specify the maximum number of scalable socket connections
204
205
Creating email message filters
Setting up the messaging Environment
Click Save all
Click Continue to user information edit Click Save all
209
Enabled drop-down list, click Yes
Save the .xml file
Export email message filters for a user account
Copying existing email message filters to user accounts
Import email message filters for a user account
Click Import email message filters Click Save all
Click OK Perform one of the following actions 211
Install an extension plug-in application
Extension plug-ins for processing messages
212
Add an extension plug-in to a BlackBerry Messaging Agent
213
Search for a user account 214
215
216
Configure the certificate information using IT policies
218
Click an IT policy
Click Save all After you finish
Click Save all After you finish
Click Manage Wi-Fi profiles
Add certificate information to a Wi-Fi profile
Click the name of the Wi-Fi profile that you want to change
Managing an enrolled certificate
222
Property Description
Properties in the rimpublic.properties file
224
Making the BlackBerry Web Desktop Manager available to Users
Click OK 225
Deploy Software window, click Advanced
Click Include OLE class and product information
Expand Group Policy Management Forest Domains
Click Add Click OK
Click Create a GPO in this domain, and link it here
226
Each dialogue box, click OK
Configure the Microsoft ActiveX Installer on Windows Vista
Enter the value of the item to be added field, type 2,2,1,0
228
Name the file EnableActiveXInstallFromAD.adm and save it
Make the BlackBerry Web Desktop Manager available to users
Click Enabled Click OK
230
Configuring the BlackBerry Web Desktop Manager
231
Change the text colors in the BlackBerry Web Desktop Manager
BlackBerry Web Desktop Manager text colors
Parameter Description Default
234
Display a custom image in the BlackBerry Web Desktop Manager
Prerequisites Creating Wi-Fi profiles and VPN profiles
Creating and configuring Wi-Fi 19 profiles and VPN profiles
Creating and configuring Wi-Fi profiles
Port assignments might vary by mobile network provider 236
Connection types and port numbers for a Wi-Fi network
Create a Wi-Fi profile based on an existing Wi-Fi profile
Create a Wi-Fi profile
Connection type Default port number Where to configure
Click Create Wi-Fi profile
Assign a Wi-Fi profile to a group
Configure a Wi-Fi profile on a BlackBerry device
Assign a Wi-Fi profile to a user account
Click Set Up Wi-Fi Network
Configure a Wi-Fi profile
Creating and configuring VPN profiles
Click the name of a Wi-Fi profile
Click Edit profile
Create a VPN profile
Configure a VPN profile
Create a VPN profile based on an existing VPN profile
Click Create VPN profile
On the VPN profiles tab, click Edit group
Assign a VPN profile to a group
Assign a VPN profile to a user account
Associate a VPN profile with a Wi-Fi profile
Delete a Wi-Fi profile
Click the name of the Wi-Fi profile
Click Delete profile Click Yes Delete the profile
Click the name of a VPN profile
Delete a VPN profile
Importing profile information from a .csv file
244
Example Adding profile information to user accounts
Example Removing profile information from user accounts
Fields in the .csv file that contains profile information
Import profile information from a .csv file
Enterprise Wi-Fi network or VPN, if a user name is required
Quotation marks in the password
BlackBerry devices do not support a WEP passphrase
Configuring WEP encryption
Configuring PSK encryption
Configuring Leap authentication
Configuring Peap authentication
251
Click Place all certificates in the following store
Select the Inner link security type
Possible cause
Configuring EAP-TLS authentication
255
Configuring EAP-TTLS authentication
257
258
Security Type list, select EAP-TTLS
Inner link security type list, select EAP-MS-CHAPv2
259
Configuring EAP-FAST authentication
Configure EAP-FAST authentication
Click Manage Wi-Fi profiles
Security Type list, select EAP-FAST
Configuring software tokens for 21 BlackBerry devices
Configure BlackBerry devices for RSA authentication
Click the name of the VPN profile that you want to change
265
Assign software tokens to a user account
266
267
Before you begin
269
270
Click Save all
272
273
274
Protecting and redistributing Devices
Preparing a device for redistribution to a new user
Click Associate user
Deleting only work data from a device
On the Devices menu, click Attached devices Device software
275
Deleted when you delete work data
Are deleted when you delete work data
Device permanently deletes the following work data
Call logs
277
Delete only work data from a device
Delete only the organization data
IT administration command Description
Protection, you cannot use this command
Application data
Protect a stolen device
Protect a lost device
Click Specify new device password and lock device
Protect a lost device that a user might not recover
281
Change role permissions
Managing administrator Accounts
Change the roles for an administrator account
Click Delete role Click Yes Delete the role
Delete an administrator account
Delete a role
284
Status list, click Delete user
Click Yes Delete the user
285
Managing groups and user Accounts
Managing groups
Click Remove from group membership
Default group Description of the default group
Remove a user account from a group
Rename a group
Change the properties of a group
Delete a group
Click Edit group
288
Managing user accounts
Move a user account to a different group
Delete a user account from the BlackBerry Enterprise Server
Add an administrator role to a user account
Update a user account manually
Update the contact list manually
Click Back to search
Communications list, click Resend service books to a device
Resend service books to a BlackBerry device
Click Refresh available user list from company directory
291
292
Managing the default distribution settings for jobs
Change default settings for a job schedule
Start time drop-down list, click the appropriate option. If
Change how IT policies are sent to BlackBerry devices
Necessary, set the start time and end time
293
Perform any of the following tasks 294
Default value is
295
296
BlackBerry Device Software
Recurrence days cannot overlap
297
If necessary, change the start time and end time
Managing the distribution settings for a specific job
Click Edit job
Specify the start time and priority for a job
Change how a job sends IT policies to BlackBerry devices
Scheduled deployment days drop-down list, click
301
302
303
304
Managing BlackBerry Java Applications on BlackBerry devices
Click Edit software configuration
Click a software configuration
Click Add applications to software configuration
305
Remove a software configuration from multiple user accounts
Managing software configurations
Remove a software configuration from a group
307
Remove a software configuration from a user account
Delete a software configuration
Restricting user access to content on web servers
Create a pull rule
Specify web address patterns
Control type drop-down list, click Pull Click the Add icon
Assign a pull rule to user accounts
Assign a pull rule to the members of a group
Click Manage users Click View more criteria
Search for a group
Click Add Click Save
Prevent users from accessing specific media types
Configure download limits for media content types
313
Default download limits for media content types
Mime type Maximum number of bytes per connection KB
Configure download limits for media content types
Administration Guide
After you finish
317
318
319
Click a BlackBerry MDS Connection Service instance
Pull Authorization drop-down list, click Yes
320
Create push initiators for push applications
321
Turn on push authorization
After you finish Create a push rule
Assign push initiators to a push rule
Create a push rule
After you finish Assign push initiators to the push rule
322
Assign a push rule to user accounts
Assign a push rule to the members of a group
Specify device ports for application-reliable push requests
Managing push application requests
325
Click Save all Click Restart instance Related information
326
327
328
Managing the wireless backup and recovery of organizer data
Managing organizer data Synchronization
329
Turning off organizer data synchronization
330
331
Changing how organizer data synchronizes
Click Continue to user information edit Click Save all
333
Synchronizing contact pictures
334
335
Managing message forwarding
Click Continue to user information edit Click Save all
337
Turn off email message forwarding to a user account
338
339
Managing the incoming message queue
Managing wireless message reconciliation
Managing access to remote message data
Click Edit instance
343
Managing email messages that contain Html and rich content
Click Save All
345
Resend the updated IT policy to the BlackBerry devices
Click the name of the IT policy that you want to change
346
Synchronizing folders on the BlackBerry device
Click Continue to user information edit Click Save all
348
Configuring access to documents on remote file systems
Click Save all Examples for step
Click the instance that you want to change 350
351
Managing signatures and disclaimers in email messages
Click Edit instance
353
Specify conflict rules for disclaimers
Turn off disclaimers for email messages
354
Sending notification messages to users
Click Select from mail address list
Type the message that you want to send
Send a notification message to group members
Click Send message
Click Send message to users in group
Send a notification message to a user
Change the size of the message state database
Click Send message to user
356
Related information
358
Format and extension Limitations
Limitations for supported attachment file formats
Format Extension
Connector shape route that connects to shapes
Table of contents
OpenOffice Format version 1.1 .odp
Files IBM Lotus Symphony only
Style effects for cells shadow, borders
Charts
Headers and footers
Drawing objects and Fontwork objects
Setting Description Range
BlackBerry Attachment Service optimization settings
Default value is Server busy time
ZIP archives Less than 2000 KB
Suggested file sizes for attachments
File format Suggested size
365
Administration Guide
Prevent users from sending large attachments
368
369
Managing calendars
Turn off client throttling in Microsoft Exchange
Type the following command
Type New-ThrottlingPolicy BESPolicy
370
After you finish
372
Example
373
Administration Guide
Global Setting that you specify applies to all users
Correcting calendar synchronization errors on devices
Setting that you specify applies to a specific user
Level Description
Example Turning off the process for a specific user
Turn off corrective calendar synchronization
Example Turning off the process for all users
Example Viewing the global calendar synchronization settings
Administration Guide
379
Configure when corrective calendar synchronization runs
380
Logging information for corrective calendar synchronization
Email application
381
Delete a setting for corrective calendar synchronization
Specifies that a calendar item is missing on the device
Communications list, click Synchronize calendar
Type regedit
Managing instant messaging
Installing a collaboration client on BlackBerry devices
Click Edit instance
Option Description
Access server
For Microsoft Office
386
387
Managing instant messaging sessions
388
Managing instant messaging features
Prevent users from saving instant messaging conversations
Back up the UserInfoConfig.xml file
Save the UserInfoConfig.xml file
Managing a BlackBerry Domain
Component Administration Service
Restarting BlackBerry Enterprise Server components
BlackBerry Enterprise Server
Administration GuideManaging a BlackBerry Domain
Use the BlackBerry Enterprise Trait Tool
Using the BlackBerry Enterprise Trait Tool
BlackBerry Enterprise Trait Tool traits
Trait Description
Calendar contents on the device. When the amount of time
For proxy authentication
Default value is false 0, the BlackBerry Messaging Agent
If you configure the EWSServiceAccount trait
BlackBerry Messaging Agent, all BlackBerry Messaging Agent
EWSEnable
SP1
Instances on all BlackBerry Enterprise Server instances
Users status using Microsoft Exchange public folders
Users status using Microsoft Exchange Web Services or by
ExchangeDisableConfirmEmailDelivery
ExchangeEnableMLangConversion
For calendar errors on devices
ExchangeSmartSyncEnable
Mailboxes, change the value to true
Might be an impact on the performance of your organizations
Default value is true 1, the BlackBerry Messaging Agent
Default value is Daily
Corrects calendar synchronization errors automatically
Calendar synchronization errors on devices at 1200 AM
Function, you can access the BlackBerry Messaging Agent
Default value is true 1, the BlackBerry Mail Store Service
Default value
Disabled on the device
Service can synchronize at the same time during a full
Default value is true 1, the BlackBerry Enterprise Server
Services that the device can connect to, type the SRP IDs
Services. Separate the SRP IDs with a comma
Policies and service books
Change the default value of this trait
Additional processes for IT policies or service books
Books, change the value to false
Default value is 75%
Uses to update the list of BlackBerry Router instances
Processes for PIN encryption keys
RouterAutoDiscoveryMethod
Environment
UserHealthPercentage
BlackBerry Dispatcher uses this trait to change the User
407
Managing BlackBerry CAL keys
Add or delete a BlackBerry CAL key
408
Copy a BlackBerry CAL key to a text file
409
Configuring a Hosted BlackBerry services environment
Related information
411
Before you begin
Configuring a Hosted BlackBerry services environment
Restarting BlackBerry Enterprise Server components
Before you begin
Configuring BlackBerry Policy Service throttling
417
Type traittool -global -list
Administration Guide
Trait PolicyThrottlingP2PKeyRate -set
420
Delete a BlackBerry Policy Service throttling setting
421
422
Administration Guide
Click Controller
MaxUserDumpPerDay value field to
Click BBAttachServer
Click BlackBerry Collaboration Service
Change how the BlackBerry
Click BlackBerryRouter
Click BlackBerry Mobile Data Server
Click MailStore
Click PolicyServer
Click SyncServer
Change the default event monitoring level
BlackBerry Enterprise Server Alert Tool
Define a notification recipient
430
Monitor PIN messages
BlackBerry Enterprise Server Log files
Monitoring PIN messages, SMS text messages, and calls
Turn off call logging
Monitor SMS text messages
List of IT policies, click the appropriate IT policy
432
433
Log files for BlackBerry Enterprise Server components
434
On the Logging details tab, click Edit instance
Each section, in the Log auto-rolldrop-down list, click True
437
438
UTF-8 UTF-16LE Click Save all
Component identifier Logging component
Component identifiers for log files
On the Logging tab, click Edit instance
BlackBerry MDS Connection Service log files
Click Save all Related information
On the Logging tab, click Edit instance
Trace how data packets travel inside the gateway
Logging section, perform any of the following tasks
Click Yes
BlackBerry device retrieves from the PGP server 443
Attribute Description
Connects using a proxy server
BlackBerry device connections
Domain that requests the BlackBerry device connection
False
BlackBerry Collaboration Service log files
On the Instance information tab, click Edit instance
446
Trace how data packets travel inside the GME network
1433 Windows registry
Configuration Database Windows
On a 32-bit version
\BlackBerry
Incoming data connections from, and outgoing data
21099 BlackBerry Configuration Panel 448
Connection Default port
Data connections between BlackBerry Administration
2000 BlackBerry Administration Attachment Service 449
Type Number Connection
On a 64-bit version of Windows
Outgoing conversion results of large attachments to
Outgoing syslog connections to the Snmp agent
1433 for
4071 Windows registry On a 32-bit version
451
\Research In Motion\
1433 for BlackBerry Configuration
\BlackBerrySNMPAgent
\Parameters\UDPPort
BlackBerry Controller connection types and port numbers
Port number Agent That BlackBerry Messaging Provides
BlackBerry Dispatcher connection types and port numbers
5096 Windows registry Agent On a 32-bit version
\TcpPortDispatcher
Server\Database\Port
Microsoft SQL Server hosts Windows
Incoming data connection from the BlackBerry database
\SOFTWARE\Research Motion 455
456
Outgoing data connections to the BlackBerry Dispatcher
5096 Windows registry On a 32-bit version
457
4070 Windows registry On a 32-bit version
Incoming data connections from the BlackBerry database
\UDPPort
Server\Agents\UDPPort
459
If access control for push applications is turned on
Database Incoming data connections from, and outgoing data
7874 BlackBerry Administration Service
Incoming data connections for reliable pushes
3200 Connections to, the BlackBerry Dispatcher
BlackBerry Policy Service connection types and port numbers
55503 BlackBerry Configuration Service console Panel
BlackBerry Router connection types and port numbers
\ServicePort
\BlackBerryRouter
462
463
464
\DevicePort
Port number Agent That BlackBerry Messaging Provides 465
CalHelper connection type and port number
Microsoft Exchange connection types and port numbers
IBM Lotus Sametime connection type and port number
TLS
Novell GroupWise Messenger connection type and port number
Connections to, the BlackBerry Collaboration Service
Snmp agent connection types and port numbers
8300
Syslog connection type and port number
470
Troubleshooting36
Possible cause Possible solution
Press Enter 471
Troubleshooting BlackBerry Enterprise Server Performance
Troubleshooting Setting up user accounts
Messages are not delivered to BlackBerry devices
Troubleshooting Messaging
Text does not appear correctly in Unicode email messages
Troubleshooting Instant messaging
475
476
Does not support the version
Troubleshooting BlackBerry Web Desktop Manager
Click Wi-Fi Options
Troubleshooting Connections to the Wi-Fi network
BlackBerry device cannot connect to a Wi-Fi network
BlackBerry device is not assigned
Click Wi-Fi Tools Wi-Fi Diagnostics
Indicator Description
Status fields for Wi-Fi connections
Status indicators are the following icons
Device is associated with the access point
To a specific access point
Connection to an access point
Cipher
Group Cipher
Group ciphers have one of the following values
None
Status fields for VPN connections
Status fields for UMA or GAN connections
Arfcn
Status fields for BlackBerry Infrastructure connections
Status fields for Enterprise connections
BlackBerry device cannot open a VPN connection
BlackBerry device is connected to a Wi-Fi network
Correctly Verify that Wi-Fi Preferred is selected
Issue on the Wi-Fi network
Is displayed
Look up a computer name to resolve an IP address
Verify whether a BlackBerry device can resolve an IP address
Troubleshooting BlackBerry Administration Service pools
User cannot log in to the BlackBerry Monitoring Service
Troubleshooting BlackBerry Monitoring Service connections
492
Troubleshooting IT policies
Glossary37
DSML-enabled
Content protection
Enterprise Service
Device transport key
Command
IT administration
IP address
IPsec
Principal database
Messaging server
Mirror database
Witness
Triple DES
VoIP
498
Legal notice
499
Administration Guide