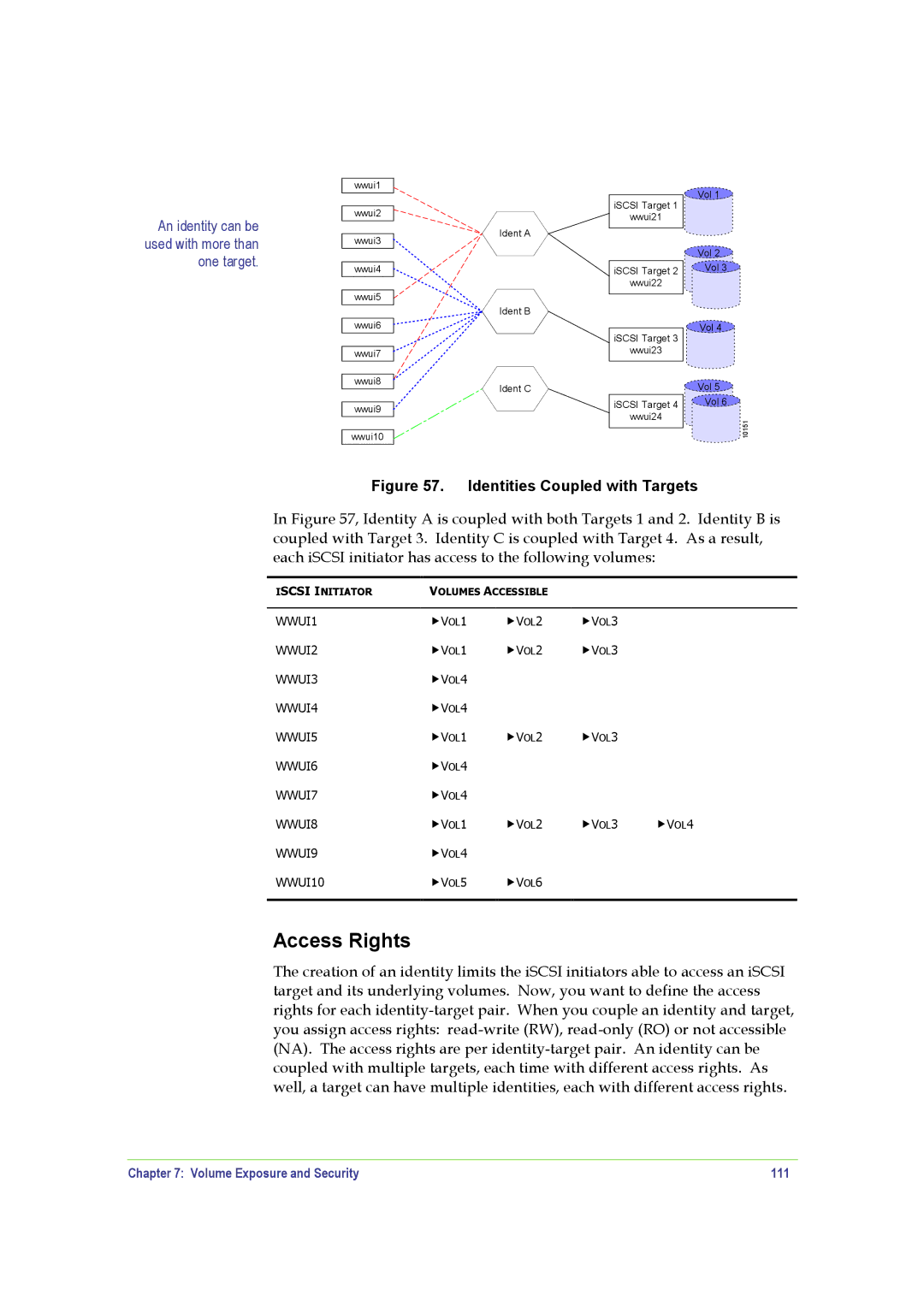
An identity can be used with more than one target.
wwui1
wwui2
wwui3
wwui4
wwui5
wwui6
wwui7
wwui8
wwui9
wwui10
Ident A
Ident B
Ident C
iSCSI Target 1
wwui21
iSCSI Target 2
wwui22
iSCSI Target 3
wwui23
iSCSI Target 4
wwui24
Vol 1
Vol 2
Vol 3
Vol 4
Vol 5
Vol 6
10151
Figure 57. Identities Coupled with Targets
In Figure 57, Identity A is coupled with both Targets 1 and 2. Identity B is coupled with Target 3. Identity C is coupled with Target 4. As a result, each iSCSI initiator has access to the following volumes:
ISCSI INITIATOR | VOLUMES ACCESSIBLE |
|
| |
|
|
|
|
|
WWUI1 | fVOL1 | fVOL2 | fVOL3 |
|
WWUI2 | fVOL1 | fVOL2 | fVOL3 |
|
WWUI3 | fVOL4 |
|
|
|
WWUI4 | fVOL4 |
|
|
|
WWUI5 | fVOL1 | fVOL2 | fVOL3 |
|
WWUI6 | fVOL4 |
|
|
|
WWUI7 | fVOL4 |
|
|
|
WWUI8 | fVOL1 | fVOL2 | fVOL3 | fVOL4 |
WWUI9 | fVOL4 |
|
|
|
WWUI10 | fVOL5 | fVOL6 |
|
|
|
|
|
|
|
Access Rights
The creation of an identity limits the iSCSI initiators able to access an iSCSI target and its underlying volumes. Now, you want to define the access rights for each
Chapter 7: Volume Exposure and Security | 111 |