|
|
| |
iSCSI Target 1 | iSCSI Target 2 |
| iSCSI Target 3 |
wwui1 | wwui2 |
| wwui3 |
Vol 1 | Vol 2 | Vol 3 | Vol 4 |
LU0 | LU0 | LU0 | LU1 |
|
|
| 10124n |
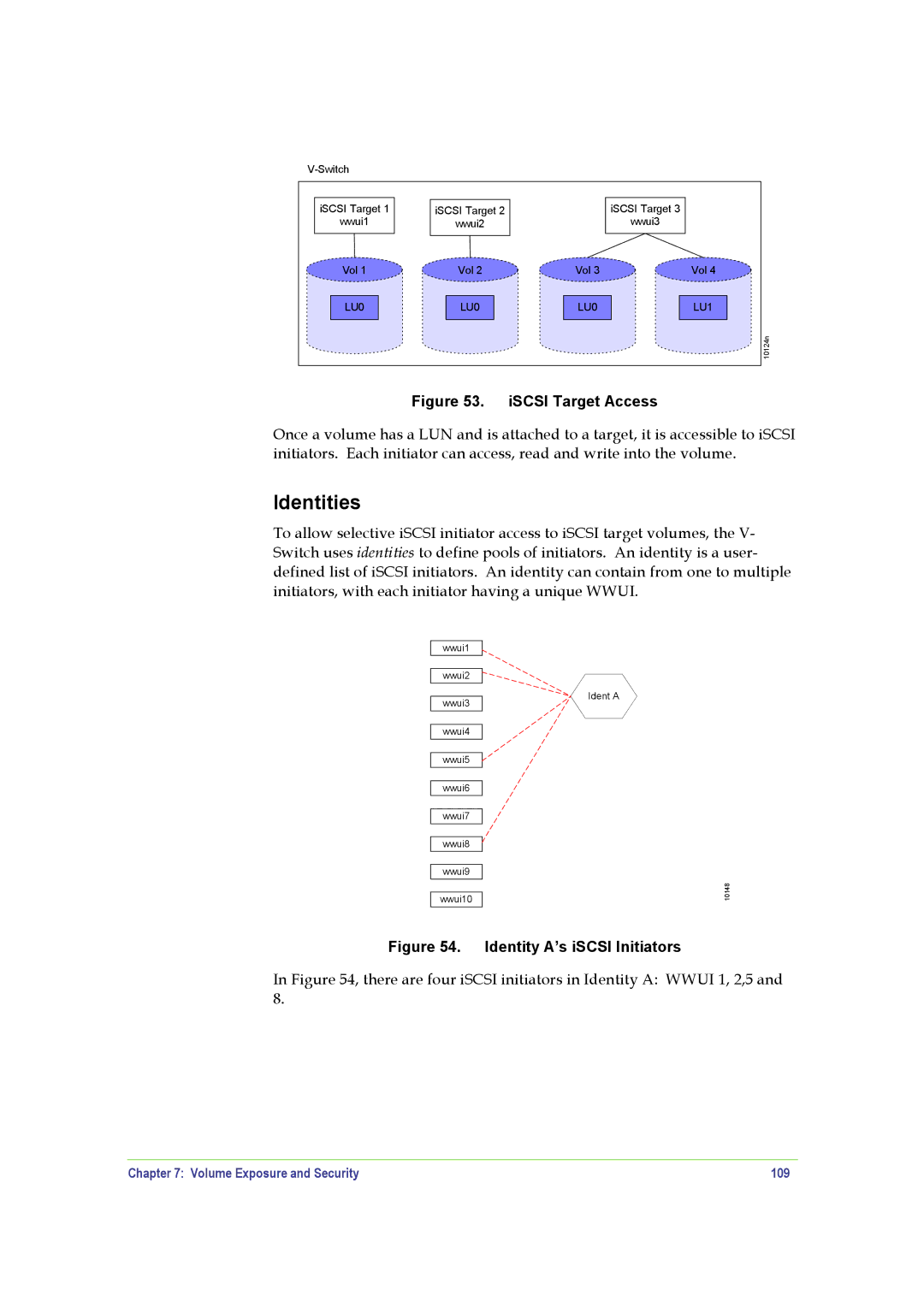
Figure 53. iSCSI Target Access
Once a volume has a LUN and is attached to a target, it is accessible to iSCSI initiators. Each initiator can access, read and write into the volume.
Identities
To allow selective iSCSI initiator access to iSCSI target volumes, the V- Switch uses identities to define pools of initiators. An identity is a user- defined list of iSCSI initiators. An identity can contain from one to multiple initiators, with each initiator having a unique WWUI.
wwui1
wwui2
wwui3
wwui4
wwui5
wwui6
wwui7
wwui8
wwui9
Ident A
wwui10
10148
Figure 54. Identity A’s iSCSI Initiators
In Figure 54, there are four iSCSI initiators in Identity A: WWUI 1, 2,5 and 8.
Chapter 7: Volume Exposure and Security | 109 |