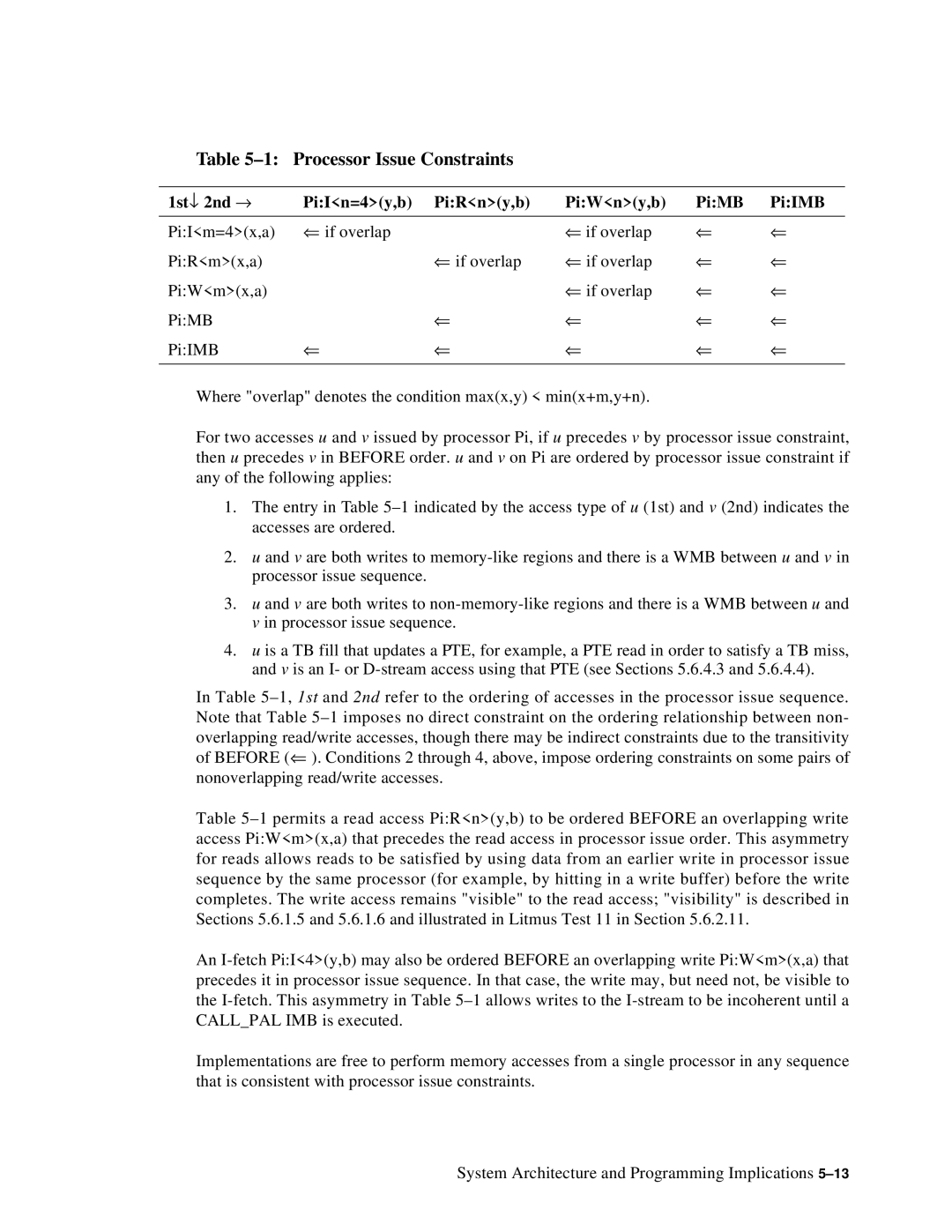
Table 5–1: Processor Issue Constraints
1st↓ 2nd → | Pi:I<n=4>(y,b) | Pi:R<n>(y,b) | Pi:W<n>(y,b) | Pi:MB | Pi:IMB |
|
|
|
|
|
|
Pi:I<m=4>(x,a) | ⇐ if overlap |
| ⇐ if overlap | ⇐ | ⇐ |
Pi:R<m>(x,a) |
| ⇐ if overlap | ⇐ if overlap | ⇐ | ⇐ |
Pi:W<m>(x,a) |
|
| ⇐ if overlap | ⇐ | ⇐ |
Pi:MB |
| ⇐ | ⇐ | ⇐ | ⇐ |
Pi:IMB | ⇐ | ⇐ | ⇐ | ⇐ | ⇐ |
|
|
|
|
|
|
Where "overlap" denotes the condition max(x,y) < min(x+m,y+n).
For two accesses u and v issued by processor Pi, if u precedes v by processor issue constraint, then u precedes v in BEFORE order. u and v on Pi are ordered by processor issue constraint if any of the following applies:
1.The entry in Table
2.u and v are both writes to
3.u and v are both writes to
4.u is a TB fill that updates a PTE, for example, a PTE read in order to satisfy a TB miss, and v is an I- or
In Table
Table
An
Implementations are free to perform memory accesses from a single processor in any sequence that is consistent with processor issue constraints.
System Architecture and Programming Implications