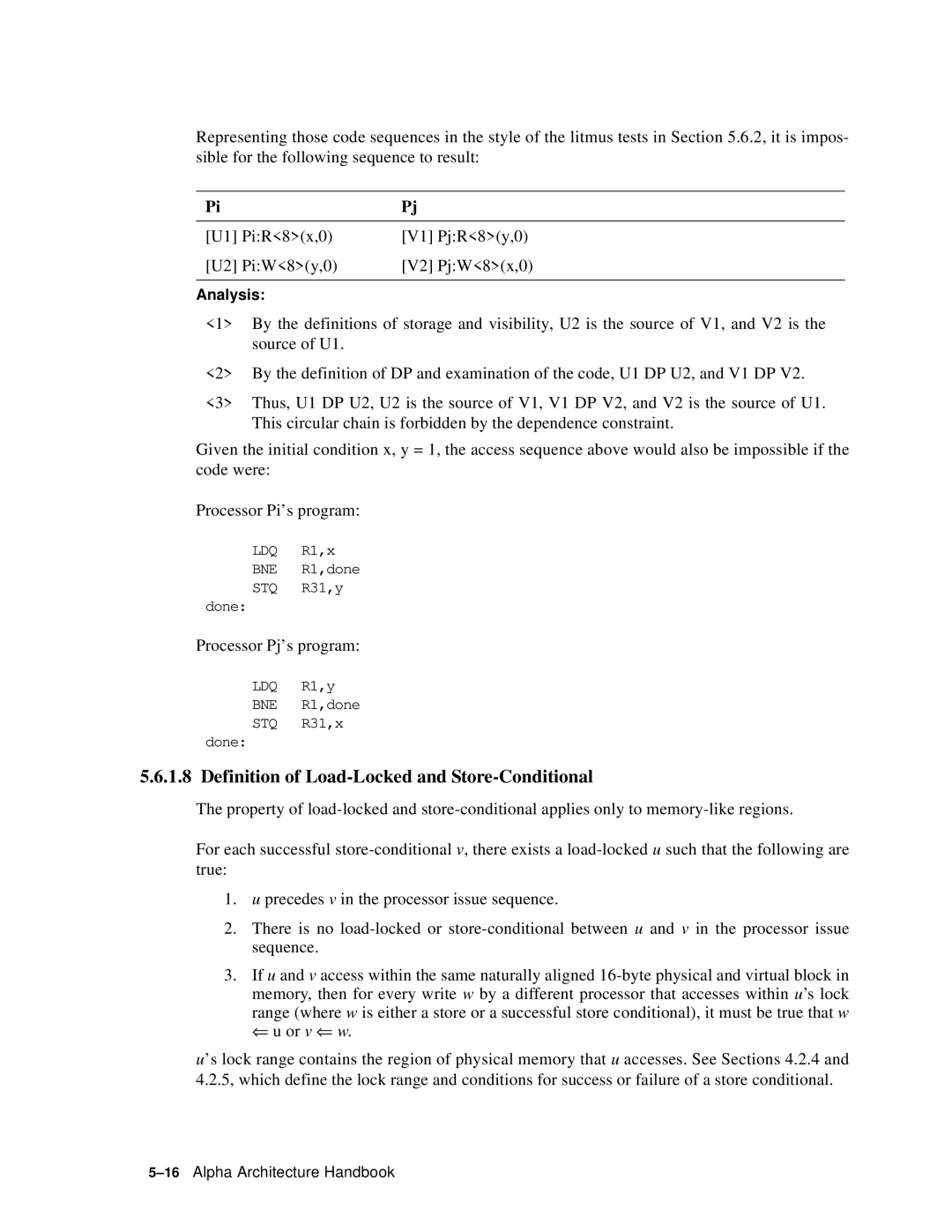
Representing those code sequences in the style of the litmus tests in Section 5.6.2, it is impos- sible for the following sequence to result:
Pi |
| Pj |
|
[U1] | Pi:R<8>(x,0) | [V1] | Pj:R<8>(y,0) |
[U2] | Pi:W<8>(y,0) | [V2] | Pj:W<8>(x,0) |
|
|
|
|
Analysis:
<1> | By the definitions of storage and visibility, U2 is the source of V1, and V2 is the |
| source of U1. |
<2> | By the definition of DP and examination of the code, U1 DP U2, and V1 DP V2. |
<3> | Thus, U1 DP U2, U2 is the source of V1, V1 DP V2, and V2 is the source of U1. |
| This circular chain is forbidden by the dependence constraint. |
Given the initial condition x, y = 1, the access sequence above would also be impossible if the code were:
Processor Pi’s program:
LDQ R1,x BNE R1,done STQ R31,y
done:
Processor Pj’s program:
LDQ R1,y BNE R1,done STQ R31,x
done:
5.6.1.8 Definition of Load-Locked and Store-Conditional
The property of
For each successful
1.u precedes v in the processor issue sequence.
2.There is no
3.If u and v access within the same naturally aligned
range (where w is either a store or a successful store conditional), it must be true that w ⇐ u or v ⇐ w.
u’s lock range contains the region of physical memory that u accesses. See Sections 4.2.4 and 4.2.5, which define the lock range and conditions for success or failure of a store conditional.