•Prevent ARP spoofing via packet content ACL
Concerning the common DoS attack today caused by the ARP spoofing,
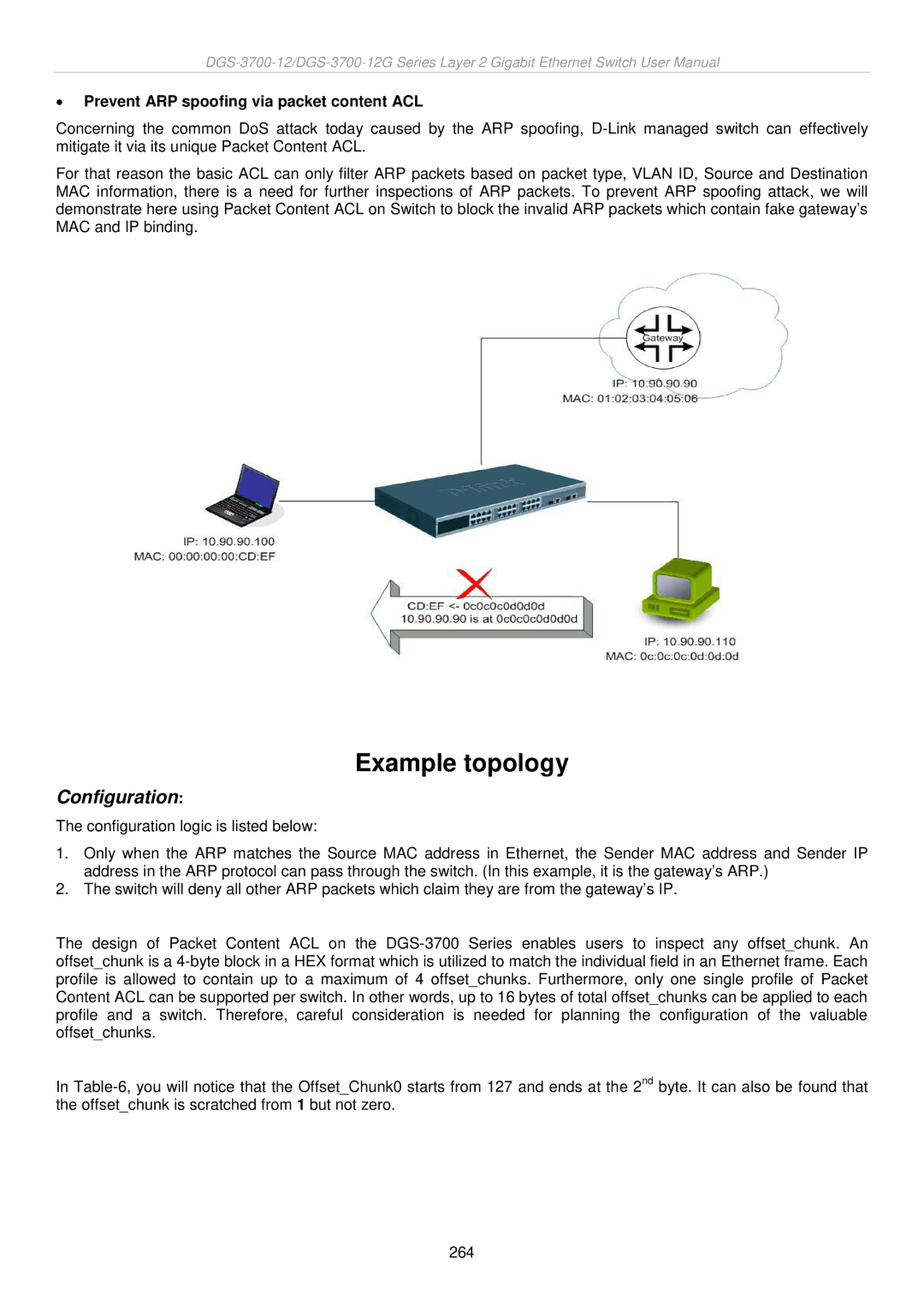
For that reason the basic ACL can only filter ARP packets based on packet type, VLAN ID, Source and Destination MAC information, there is a need for further inspections of ARP packets. To prevent ARP spoofing attack, we will demonstrate here using Packet Content ACL on Switch to block the invalid ARP packets which contain fake gateway’s MAC and IP binding.
Example topology
Configuration:
The configuration logic is listed below:
1.Only when the ARP matches the Source MAC address in Ethernet, the Sender MAC address and Sender IP address in the ARP protocol can pass through the switch. (In this example, it is the gateway’s ARP.)
2.The switch will deny all other ARP packets which claim they are from the gateway’s IP.
The design of Packet Content ACL on the
In
264