Umncli
A50010-Y3-C150-2-7619
Surpass hiD 6615 S223/S323 R1.5
Important Notice on Product Safety
A50010-Y3-C150-2-7619
Reason for Update
Issue History
Summary System software upgrade added
Details
Contents
4.3
4.4
5.1
5.2
7.1
7.2
7.3
12.1
100
101
102
103
124
125
126
127
Surpass hiD 6615 S223/S323 R1.5 3.1
147
149
150
179
180
181
182
Surpass hiD 6615 S223/S323 R1.5 5.9
216
217
6.1
1.16
1.17
246
247
Surpass hiD 6615 S223/S323 R1.5 3.2
268
269
3.8
295
297
298
299
Surpass hiD 6615 S223/S323 R1.5 10.1.1
318
10.1.1.1
10.1.1.2
10.2.12
353
10.2.13
354
Illustrations
Igmp Snooping and PIM-SM Configuration Network 279
Tables
Tab
171
176
Audience
Document Structure
Tab .1 briefly describes the structure of this document
Tab .1 Overview of Chapters A50010-Y3-C150-2-7619
Tab .2 Command Notation of Guide Book
Document Convention
Document Notation
CE Declaration of Conformity
GPL/LGPL Warranty and Liability Exclusion
System Overview
System Features
Quality of Service QoS
Multicasting
IP Routing
Spanning Tree Protocol STP
Link Aggregation Trunking
System Management based on CLI
Broadcast Storm Control
Radius and TACACS+
Command Line Interface CLI
Command Mode
Shows hiD 6615 S323 software mode structure briefly
Privileged Exec View Mode
Privileged Exec Enable Mode
Global Configuration Mode
Tab .1 Main Commands of Privileged Exec View Mode
Bridge Configuration Mode
Tab .3 Main Commands of Global Configuration Mode
Tab .4 Main Commands of Bridge Configuration Mode
Rule Configuration Mode
Opens Rule Configuration mode
Dhcp Configuration Mode
Dhcp Option 82 Configuration Mode
Tab .6 Main Commands of Dhcp Configuration Mode
Command Mode Description Ip dhcp pool Pool
Rmon Configuration Mode
Interface Configuration Mode
Command Mode Description Interface Interface
Router Configuration Mode
Vrrp Configuration Mode
Tab .10 Main Commands of Router Configuration Mode
Command Mode Description
Route-Map Configuration Mode
Listing Available Commands
Variables following after the commands
Useful Tips
6615 S223/S323
Command
Calling Command History
Surpass hiD 6615 S223/S323 R1.5
Using Abbreviation
Using Command of Privileged Exec Enable Mode
Tab .13 Command Abbreviation
SWITCH# show clock
Exits to Privileged Exec enable mode
Exit Current Command Mode
Able mode, you will be logged out
System Connection
System Login
Step
Command Mode Description Passwd enable Password
Password for Privileged Exec Mode
Passwd enable 8 Password
Management for System Account
Changing Login Password
Creating System Account
Configuring Security Level
To display the created account, use the following command
SWITCH# show list
Command Mode Description No privilege
No privilege configure level
No privilege rmon-alarm level
No privilege bgp level
Command Mode Description Show privilege
Shows a configured security level
Telnet Access
SWITCH# write memory
SWITCH# disconnect ttyp0
Limiting Number of User
System Rebooting
Manual System Rebooting
SWITCHconfig# show exec-timeout
Auto Log-out
System Authentication
Auto System Rebooting
Auto-reset memory 1-120
No auto-reset cpu memory
Authentication Interface
Authentication Method
Primary Authentication Method
Radius Server for System Authentication
Timeout of Authentication Request
Radius Server
Radius Server Priority
Tacacs Server for System Authentication
Tacacs Server
Frequency of Retransmit
5.2 Tacacs Server Priority
Additional TACACS+ Configuration
TCP Port for the Authentication
Authentication Type
Command Mode Description Login tacacs timeout
Accounting Mode
Displaying System Authentication
Login accounting-mode none
Start stop both
Sample Configuration
Tacacs
Assigning IP Address
Interface Configuration Mode
To enable the interface, use the following command
Enabling Interface
Disabling Interface
Static Route and Default Gateway
Assigning IP Address to Network Interface
Ip address IP-ADDRESS/M
No ip route IP-ADDRESS/M
Displaying Forwarding Information BaseFIB Table
Forwarding Information BaseFIB Retain
② On Interface Configuration Mode
Displaying Interface
Show interface Interface
Show ip interface Interface
SSH Secure Shell
SSH Server
Assigning Specific Authentication Key
Login to SSH Server
2.3 Configuring Authentication Key
SSH Client
Connect to SSH server with the authentication key
Configure the authentication key in the switch
Ssh keygen rsa1 rsa dsa
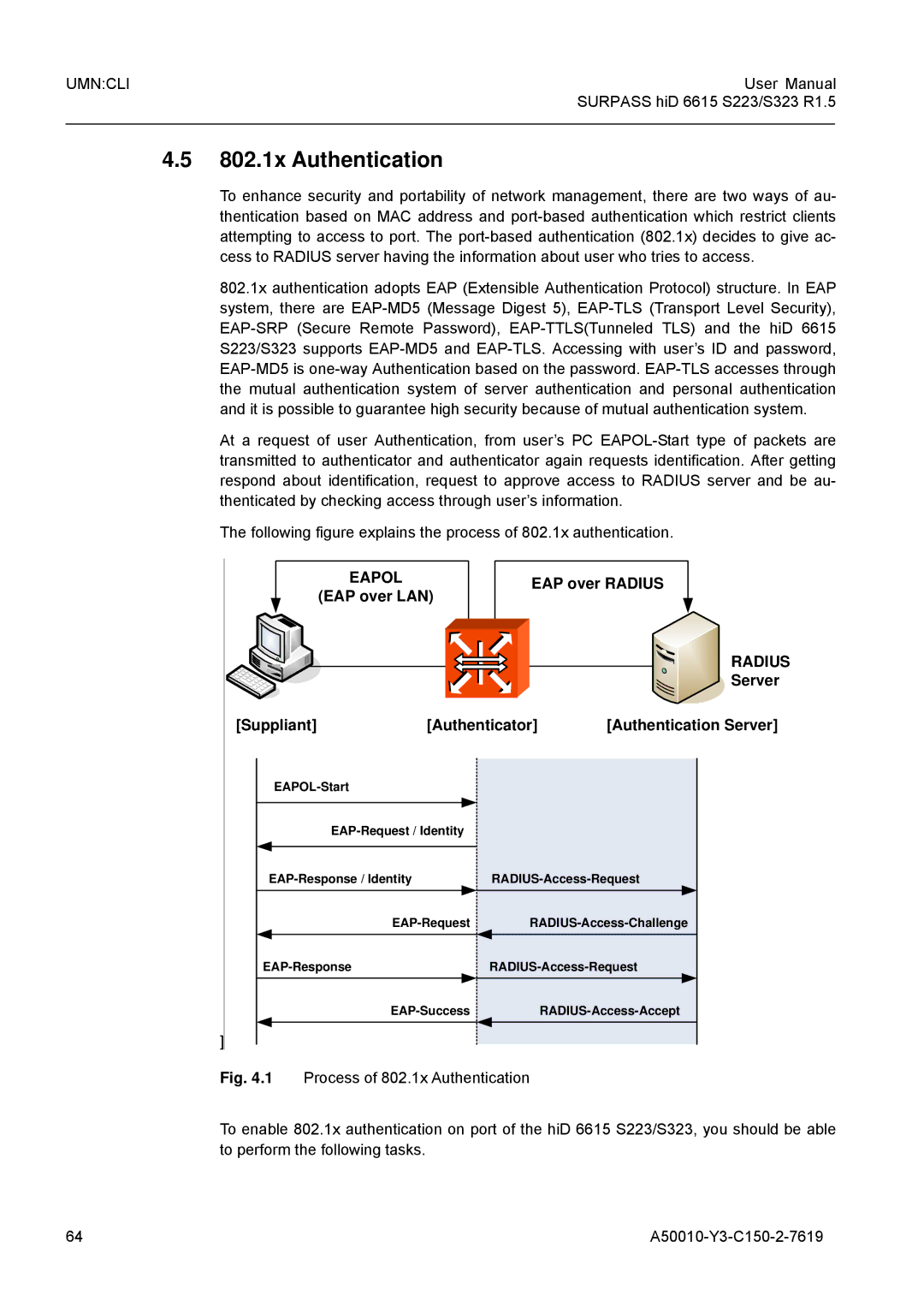
Server Suppliant Authenticator Authentication Server
802.1x Authentication
EAP over LAN EAP over Radius
1 802.1x Authentication
Configuring Radius Server
Authentication Server
Designate as default Response
Command Mode Description Dot1x radius-server move IP
Configuring Authentication Mode
Dot1x radius-server host
Authentication Port
Force Authorization
Mode Description Dot1x port-control auto force
Command Mode Description Dot1x timeout tx-period
2 802.1x Re-Authentication
1.7 Configuring Number of Request to Radius Server
1.8 Configuring Interval of Request to Radius Server
Enabling 802.1x Re-Authentication
Configuring the Interval of Requesting Re-authentication
Configuring the Interval of Re-Authentication
2.4 802.1x Re-authentication
Initializing Authentication Status
Applying Default Value
Displaying 802.1x Configuration
6 802.1x User Authentication Statistic
SWTICHconfig# dot1x system-auth-control
SWTICHconfig# dot1x auth-mode mac-base
PortAuthed
Selecting Port Type
Port Basic
Show port Ports
Ethernet Port Configuration
To enable/disable a port, use the following command
Command Mode Description Port medium Port sfp rj45
Enabling Ethernet Port
Command Mode Description Port nego Ports on off
Auto-negotiation
Transmit Rate
Port speed Ports 10 100
Duplex Mode
Command Mode Description Port duplex Ports full half
Flow Control
Half
Following is an example of configuring flow control to port
To view description of port, use the following command
SWITCHbridge# port flow-control 25 on
SWITCHbridge# show port description
SWITCHbridge# show port statistics avg-pkt
SWITCHbridge# show port statistics rmon
Traffic Statistics
Packets Statistics
CPU statistics
To enable/disable protocol statistics
Protocol statistics
To display a port status, use the following command
SWITCH# show port
Port Mirroring
Port Status
Activate the port mirroring, using the following command
Designate the monitor port, use the following command
Designate the mirrored ports, use the following command
Command Mode Description Mirror add Ports ingress
To disable monitoring function, use the following command
Connect a motoring PC to the monitor port of the switch
Enable mirroring function
Configure the monitor port 1 and mirroring port 2, 3, 4
Host Name
Environment Configuration
Time and Date
Time Zone
Network Time Protocol
Tab .1 shows the world time zone
Tab .1 World Time Zone
Simple Network Time Protocol Sntp
NTP Network Time Protocol
Following is an example of releasing NTP and showing it
To display Sntp configuration, use the following command
Terminal Configuration
No sntp
Login Banner
To restore a default banner, use the following command
To set a DNS server, use the following command
DNS Server
Fan Operation
Disabling Daemon Operation
System Threshold
CPU Load
Mode Description Threshold Port
Port Traffic
Fan Operation
No threshold Port Ports rx
System Temperature
Enabling FTP Server
System Memory
Threshold temp Value Value
Configuration Management
Displaying System Configuration
Assigning IP Address of FTP Client
All Option History router bgp pim rip
Saving System Configuration
System Configuration File
SWITCH# show running-config syslog
Auto-Saving
To delete backup file, use the following command
Restoring Default Configuration
SWITCHconfig# copy running-config SURPASShiD6615
System Management
SWITCHconfig# restore factory-defaults
Network Connection
Figured time interval. Default is 2 seconds
Type of service
Items Description Source address or interface
Set DF bit in IP header? no
Data pattern 0xABCD
IP Icmp Source-Routing
IP Source Routing A50010-Y3-C150-2-7619
Tracing Packet Route
Following is the basic information to trace packet routes
SWITCH# traceroute
Displaying User Connecting to System
MAC Table
Configuring Ageing time
SWITCH# show uptime
Running Time of System
System Information
System Memory Information
CPU packet limit
Average of CPU Load
Running Process
Default OS
Displaying Installed OS
Displaying System Image
Switch Status
Tech Support
Ber of display lines of terminal screen
A50010-Y3-C150-2-7619 103
Command Mode Description Snmp community ro rw Community
Simple Network Management Protocol Snmp
Snmp Community
No snmp community ro rw Community
Following is an example of creating 2 Snmp communities
Information of Snmp Agent
A50010-Y3-C150-2-7619 105
Following is an example of configuring Snmp com2sec
SWITCHconfig# show snmp com2sec
Snmp Com2sec
Snmp Group
Permission to Access Snmp View Record
SWITCHconfig# snmp view Test included
Snmp View Record
Following is an example of creating an Snmp view record
Lowing command
To display Snmp version 3 user, use the following command
Snmp access
Snmp Version 3 User
Snmp Trap Mode
To set an Snmp trap host, use the following command
To select an Snmp trap-mode, use the following command
Snmp Trap Host
Enabling Snmp Trap
110 A50010-Y3-C150-2-7619
Disabling Snmp Trap
To disable Snmp trap, use the following command
Node
Snmp Alarm
Enabling Alarm Notification
SWITCHconfig# snmp inform-trap-host
Displaying Snmp Trap
Alarm Severity Criterion
Default Alarm Severity
To configure a priority of alarm, use the following command
Generic Alarm Severity
114 A50010-Y3-C150-2-7619
Adva Alarm Severity
Snmp Alarm-severity adva-if-sfp-mismatch
A50010-Y3-C150-2-7619 115
Critical major minor warning intermedi
ERP Alarm Severity
116 A50010-Y3-C150-2-7619
STP Guard Alarm Severity
Displaying Snmp Configuration
A50010-Y3-C150-2-7619 117
SWITCHconfig# show snmp alarm-history
To disable Snmp feature, use the following command
Disabling Snmp
Operation, Administration and Maintenance OAM
Disables local OAM
OAM Loopback
A50010-Y3-C150-2-7619 119
OAM Unidirection
Local OAM Mode
Remote OAM
To display OAM configuration, use the following command
Displaying OAM Configuration
A50010-Y3-C150-2-7619 121
122 A50010-Y3-C150-2-7619
Link Layer Discovery Protocol Lldp
Lldp Operation
Lldp Operation Type
Basic TLV
Lldp Message
Interval and Delay Time
124 A50010-Y3-C150-2-7619
To display Lldp configuration, use the following command
Displaying Lldp Configuration
A50010-Y3-C150-2-7619 125
To open RMON-historymode, use the following command
SWITCHconfig# show rmon-history config
Command Mode Description Rmon-history
Remote Monitoring Rmon
Source Port of Statistical Data
Subject of Rmon History
Number of Sample Data
Interval of Sample Inquiry
Activating Rmon History
Deleting Configuration of Rmon History
Displaying Rmon History
Rmon Alarm
Subject of Rmon Alarm
Command Mode Description Rmon-alarm
A50010-Y3-C150-2-7619 129
Object of Sample Inquiry
Absolute Comparison and Delta Comparison
Upper Bound of Threshold
130 A50010-Y3-C150-2-7619
Configuring Standard of the First Alarm
Lower Bound of Threshold
Activating Rmon Alarm
Deleting Configuration of Rmon Alarm
Displaying Rmon Alarm
Rmon Event
Event Description
Subject of Rmon Event
Event Type
Activating Rmon Event
Deleting Configuration of Rmon Event
Displaying Rmon Event
134 A50010-Y3-C150-2-7619
Activates Rmon event
To set a syslog output level, use the following command
Syslog
Syslog Output Level
Syslog Output Level without a Priority
Syslog Output Level with a Priority
136 A50010-Y3-C150-2-7619
Local5 local6 local7 lpr mail news sys
Log user uucp emerg alert crit err
Syslog Bind Address
Facility Code
A50010-Y3-C150-2-7619 137
Displaying Syslog Configuration
Debug Message for Remote Terminal
Disabling Syslog
Displaying Syslog Message
How to Operate Rule and QoS
Rule and QoS
Rule Configuration
Rule Creation
Rule Priority
140 A50010-Y3-C150-2-7619
Packet Classification
A50010-Y3-C150-2-7619 141
142 A50010-Y3-C150-2-7619
Tcp
Rule Action
A50010-Y3-C150-2-7619 143
144 A50010-Y3-C150-2-7619
Overwrites 802.1p CoS field in the packet same as IP
Modifying and Deleting Rule
Applying Rule
Remedy Select another name for the rule e.g. add a prefix
3 QoS
Displaying Rule
Weighted Fair Queuing WFQ
Weighted Round Robin WRR
Scheduling Algorithm
Weighted Fair Queuing
Strict Priority Queuing SP
Qos Weight
3.3 802.1p Priory-to-queue Mapping
Admin Access Rule
To configure a queue parameter, use the following command
To display a configuration of QoS, enter following command
Queue Parameter
Command Mode Description Rule Name create admin
Command Mode Description Priority low medium high
A50010-Y3-C150-2-7619 151
Highest Defaul low
152 A50010-Y3-C150-2-7619
Command Mode Description No-match deny
Command Mode Description Apply
Applies an admin access rule to the system
Match permit Permits a packet
Shows a current configuration of a rule
154 A50010-Y3-C150-2-7619
Internet
NetBIOS Filtering
A50010-Y3-C150-2-7619 155
Martian Filtering
SWITCHbridge# show netbios-filter
Max Host
Following is an example of displaying configured max hosts
To display configured max host, use the following command
Max New Hosts
To configure max new hosts, use the following command
Enable port security on the port
Port Security
Port Security on Port
Set the violation mode and the action to be taken
Set the maximum number of secure MAC address for the port
Enter a secure MAC address for the port
A50010-Y3-C150-2-7619 159
This is an example of configuring port security on port
Port Security Aging
Port
Maximum
MAC Table
A50010-Y3-C150-2-7619 161
Command Mode Description Clear mac
Command Mode Description No mac
Clear mac Name
Clear mac Name Port
Default Policy of MAC Filtering
Sample Configuration
MAC Filtering
Adding Policy of MAC Filter
Listing of MAC Filter Policy
Deleting MAC Filter Policy
Displaying MAC Filter Policy
Following is an example of displaying one configuration
Address Resolution Protocol ARP
ARP Table
Displaying ARP Table
Registering ARP Table
166 A50010-Y3-C150-2-7619
To display ARP alias, use the following command
ARP Alias
ARP Inspection
A50010-Y3-C150-2-7619 167
168 A50010-Y3-C150-2-7619
Gratuitous ARP
Icmp Message Control
Proxy-ARP
Blocking Echo Reply Message
Interval for Transmit Icmp Message
Tab
Type Value
Type Status
Command Mode Description Ip icmp interval rate-limit
Enable Shows Icmp interval configuration Global
Transmitting Icmp Redirect Message
172 A50010-Y3-C150-2-7619
IP TCP Flag Control
RST Configuration
Policy of unreached messages
Packet Dump
SYN Configuration
Verifying Packet Dump
Packet Dump with Option
Packet Dump by Protocol
A50010-Y3-C150-2-7619 175
Tab .4 Options for Packet Dump 176 A50010-Y3-C150-2-7619
Tab .4 shows the options for packet dump
Option Description
Debug Packet Dump
Displaying the usage of the packet routing table
A50010-Y3-C150-2-7619 177
Vlan
Enlarged Network Bandwidth
Cost-Effective Way
Strengthened Security
Port-Based Vlan
Creating Vlan
Specifying Pvid
Assigning Port to Vlan
Deleting Vlan
MAC address-based Vlan
Protocol-Based Vlan
Displaying Vlan
Subnet-based Vlan
Tagged Vlan
Vlan Tag
Macbase MAC-ADDRESS
Displaying Vlan Information
Vlan Description
Mapping Frames to Vlan
QinQ
Tunnel Port
Trunk Port
Tagged
Double Tagging Configuration
To disable double tagging, use the following command
Double Tagging Operation
Designate the QinQ port
Tpid Configuration
Layer 2 Isolation
Private Vlan Edge
Private Vlan
Command Mode Description Port protected Ports
Port Isolation
Shared Vlan
No port protected Ports
188 A50010-Y3-C150-2-7619
Vlan fid Vlans FID
Open Rule Configuration mode using rule Name create command
Open Bridge Configuration mode using the bridge command
Sample Configuration 1 Configuring Port-based Vlan
Vlan Translation
Sample Configuration 2 Deleting Port-based Vlan
Following is deleting vlan id 3 among configured Vlan
Sample Configuration 3 Configuring Protocol-based Vlan
Default br2 br3 br4
Sample Configuration 4 Configuring QinQ
Switch
Sample Configuration 5 Configuring Shared Vlan with FID
SWITCHbridge# vlan dot1q-tunnel enable
SWITCHbridge# vlan add br5 1-42untagged
Link Aggregation
Configuring Port Trunk
Port Trunk
Trunk distmode
Dstip dstmac Srcdstip
Link Aggregation Control Protocol Lacp
Displaying Port Trunk Configuration
Disabling Port Trunk
Activate Lacp function, using the following command
Configuring Lacp
Packet Route
To disable configuring packets, use the following command
Operating Mode of Member Port
196 A50010-Y3-C150-2-7619
Identifying Member Ports within Lacp
Bpdu Transmission Rate
Key value of Member Port
A50010-Y3-C150-2-7619 197
Priority of Switch
Command Mode Description Lacp port priority Ports
Priority of Member Port
198 A50010-Y3-C150-2-7619
To display a configured LACP, use the following command
Displaying Lacp Configuration
A50010-Y3-C150-2-7619 199
Spanning-Tree Protocol STP
STP Operation
Root Switch
A50010-Y3-C150-2-7619 201
Designated Switch
Switch
Designated Port and Root Port
Port Priority
Disabled
Port States
Listening
Learning
Switch B Switch C
Backup
Port Path Switch D
Rstp Operation
Bpdu Policy
Rapid Network Convergence
17 Network Convergence of 802.1w A50010-Y3-C150-2-7619 207
19 Network Convergece of 802.1w 208 A50010-Y3-C150-2-7619
Mstp Operation
Compatibility with 802.1d
Operation
Switch D Switch E
Region B IST
Region a IST
Configuring STP/RSTP/MSTP/PVSTP/PVRSTP Mode Required
A50010-Y3-C150-2-7619 211
Configuring STP/RSTP/MSTP
Root Switch
Activating STP/RSTP/MSTP
Path-cost
Tab STP Path-cost
Port-priority
A50010-Y3-C150-2-7619 213
MST Region
Mstp Protocol
Point-to-point MAC Parameters
Edge Ports
A50010-Y3-C150-2-7619 215
Displaying Configuration
To delete the edge port mode, use the following command
Configuring PVSTP/PVRSTP
Command Mode Description Stp pvst enable VLAN-RANGE
Activating PVSTP/PVRSTP
A50010-Y3-C150-2-7619 217
Ally. To configure port priority, use the following command
6.3 Path-cost
6.4 Port-priority
218 A50010-Y3-C150-2-7619
Root Guard
Root Guard Configuration
Restarting Protocol Migration
Bridge Protocol Data Unit Configuration
Forward Delay
Hello Time
Hello Time
Forward Delay
Max Age
To delete a configured max age, use the following command
Following command
9.4 Bpdu Hop
9.5 Bpdu Filter
Configure Bpdu Guard
Configure the specific port as edge-port
Self Loop Detection
Displaying Bpdu Configuration
224 A50010-Y3-C150-2-7619
Backup Route
SWITCHbridge# stp force-version mstp
Mstp Configuration
226 A50010-Y3-C150-2-7619
Virtual Router Redundancy Protocol Vrrp
Internet
Configuring Vrrp
To delete the Vrrp configuration, use the following command
Associated IP Address
228 A50010-Y3-C150-2-7619
Master Router and Backup Router
Access to Associated IP Address
A50010-Y3-C150-2-7619 229
Layer 3 Switch 2 IP Address 10.0.0.2/24
SWTICH1config# router vrrp default
Vrrp Track Function
Authentication Password
To configure Vrrp Track, use the following command
SWITCHconfig-vrrp#authentication cleartext network
Preempt
Following is an example of disabling Preempt
A50010-Y3-C150-2-7619 233
Rate Limit
Configuration mode
Vrrp Statistics
To set a port bandwidth, use the following command
Configuring Rate Limit
A50010-Y3-C150-2-7619 235
Flood Guard
Configuring Flood-Guard
236 A50010-Y3-C150-2-7619
Following is an example of configuration to bandwidth as
SWITCHbridge# show mac-flood-guard
Bandwidth
A50010-Y3-C150-2-7619 237
Dynamic Host Configuration Protocol Dhcp
Saving Cost
Efficient IP Management
IP Packet Broadcast Dhcp Server or Relay Agent
Dhcp Server
Dhcp Subnet
Dhcp Pool Creation
Range of IP Address
Default Gateway
Following is an example of specifying the default gateway
IP Lease Time
A50010-Y3-C150-2-7619 241
DNS Server
Manual Binding
Following is an example of specifying a DNS server
242 A50010-Y3-C150-2-7619
Domain Name
Dhcp Server Option
Static Mapping
Recognition of Dhcp Client
Command Mode Description Ip dhcp arp ping packet
Command Mode Description Ip dhcp arp ping timeout
IP Address Validation
Authorized ARP
Ignoring Bootp Request
Prohibition of 1N IP Address Assignment
Dhcp Packet Statistics
A50010-Y3-C150-2-7619 245
Displaying Dhcp Pool Configuration
SWITCHconfig# show ip dhcp server statistics
Command Mode Description Show ip dhcp pool Pool
246 A50010-Y3-C150-2-7619
Dhcp Address Allocation with Option
Dhcp Class Capability
Dhcp Class Creation
Relay Agent Information Pattern
Associating Dhcp Class
Range of IP Address for Dhcp Class
Text String
No address range A.B.C.D
Dhcp Lease Database
Dhcp Database Agent
Displaying Dhcp Lease Status
A50010-Y3-C150-2-7619 249
Dhcp Relay Agent
Deleting Dhcp Lease Database
Dhcp Server Relay Agent Subnet
PC= Dhcp Client
Smart Relay Agent Forwarding
Packet Forwarding Address
C.D all
Dhcp Option
Enabling Dhcp Option
Option 82 Sub-Option
Option 82 Reforwarding Policy
Default Trust Policy
Option 82 Trust Policy
To specify a trusted remote ID, use the following command
Simplified Dhcp Option
Trusted Remote ID
Trusted Physical Port
Dhcp Client
Enabling Dhcp Client
6.2 Dhcp Client ID
6.3 Dhcp Class ID
Displaying Dhcp Client Configuration
Requesting Option
Forcing Release or Renewal of Dhcp Lease
A50010-Y3-C150-2-7619 257
Dhcp Snooping
Enabling Dhcp Snooping
Dhcp Trust State
258 A50010-Y3-C150-2-7619
Mode Description Ip dhcp snooping Limit-lease
Dhcp Rate Limit
Dhcp Lease Limit
Source MAC Address Verification
Dhcp Snooping Database Agent
Specifying Dhcp Snooping Database Agent
Specifying Dhcp Snooping Binding Entry
260 A50010-Y3-C150-2-7619
Displaying Dhcp Snooping Configuration
IP Source Guard
Enabling IP Source Guard
Source IP Address Filter
Displaying IP Source Guard Configuration
Source port-security commands together
Command Mode Description Ip dhcp verify source Ports
Static IP Source Binding
Command Mode Description Ip dhcp filter-address
Dhcp Filtering
Dhcp Packet Filtering
Dhcp Server Packet Filtering
Command Mode Description Debug dhcp filter
Packet service all
Debugging Dhcp
264 A50010-Y3-C150-2-7619
Ethernet Ring Protection ERP
ERP Operation
Normal Node
Send Link Down Message
RM Node
Normal Node RM Node
Loss of Test Packet Lotp
Configuring ERP
ERP Domain
RM Node
Port of ERP domain
Protected Vlan
Protected Activation
Manual Switch to Secondary
Wait-to-Restore Time
Learning Disable Time
Test Packet Interval
Stacking
Displaying ERP Configuration
Show erp all DOMAIN-ID
Switch Group
Designating Master and Slave Switch
Designate Mater switch using the following command
A50010-Y3-C150-2-7619 271
Accessing to Slave Switch from Master Switch
To disable stacking, use the following command
Sample Configuration 1 Configuring Stacking
Disabling Stacking
SWITCHA# configure terminal
SWITCHAconfig# stack device default
SWITCHBconfig# stack device default
A50010-Y3-C150-2-7619 273
Broadcast Storm Control
To disconnect, input as below
Storm-control broadcast mul
Ticast dlf Rate Ports
Jumbo-frame Capacity
Command Mode Description Jumbo-frame Ports
A50010-Y3-C150-2-7619 275
Maximum Transmission Unit MTU
Blocking Direct Broadcast
276 A50010-Y3-C150-2-7619
SWITCHconfig-if#show running-config interface
A50010-Y3-C150-2-7619 277
Layer 2 Network
Layer 3 Network
Command Mode Description Ip multicast route-limit
Multicast Routing Information Base
Enabling Multicast Routing Required
Limitation of Mrib Routing Entry
Clearing Mrib Information
Clearing Total or Partial Group Entry of Mrib
Clearing Statistics of Multicast Routing Table
280 A50010-Y3-C150-2-7619
Multicast Time-To-Live Threshold
Displaying Mrib Information
Mrib Debug
Multicast Aging
282 A50010-Y3-C150-2-7619
Igmp Basic Configuration
Internet Group Management Protocol Igmp
Igmp Version per Interface
Igmp Version
Igmp Static Join Setting
Igmp Version
Removing Igmp Entry
Igmp Debug
Igmp Query Configuration
Command Mode Description Ip igmp static-group
Maximum Number of Groups
Vlan Vlan port Port reporter
Igmp Maximum Response Time
286 A50010-Y3-C150-2-7619
Igmp v2 Fast Leave
Displaying the Igmp Configuration
A50010-Y3-C150-2-7619 287
Igmp Snooping Basic Configuration
Step Execute the ip multicast-routing command
3 L2 Mfib
Enabling Igmp Snooping per Vlan
Enable Igmp snooping on a Vlan interface
Command Mode Description Ip igmp snooping vlan Vlans
Command Mode Description Show ip igmp snooping Vlan
Igmp v2 Snooping
Multicast Packet
Igmp v2 Snooping Fast Leave
290 A50010-Y3-C150-2-7619
To disable Igmp querier, use the following command
Igmp v2 Snooping Querier
Enabling Igmp Snooping Querier
A50010-Y3-C150-2-7619 291
Timeout Value of Igmp v2 Snooping Querier’s General Query
To disable the max-response-time, use the following command
Query Interval of Igmp v2 Snooping Querier
292 A50010-Y3-C150-2-7619
Igmp v2 Snooping Last-Member-Interval
A50010-Y3-C150-2-7619 293
Vlans querier detail
Last-member-query-interval
Configuring Mrouter Port per Vlan
Igmp v2 Snooping Report Method
Mrouter Port
294 A50010-Y3-C150-2-7619
Multicast TCN Flooding
Displaying Mrouter Configuration
Mrouter Port Learning Method
Command Mode Description Ip igmp snooping tcn query
296 A50010-Y3-C150-2-7619
Vlans flood
Nected to on a Vlan interface
Igmp v3 Snooping
Igmp Snooping Version
Join Host Management
A50010-Y3-C150-2-7619 297
Multicast Vlan Registration MVR
To display a configuration, use the following command
Immediate Block
Enabling MVR
MVR Group Address
MVR IP Address
A50010-Y3-C150-2-7619 299
Igmp Filtering and Throttling
7.5 Displaying MVR Configuration
Send and Receive Port
Creating Igmp Profile
Policy of Igmp Profile
Group Range of Igmp Profile
A50010-Y3-C150-2-7619 301
To return to the default setting, use the following command
Applying Igmp Profile to the Filter Port
Max Number of Igmp Join Group
302 A50010-Y3-C150-2-7619
Displaying Igmp Snooping Table
PIM-SM Protocol Independent Multicast-Sparse Mode
RPT and SPT
PIM Common Configuration
Packet for the request
PIM-SM and Passive Mode
DR Priority
To configure a query hold time, use the following command
Filters of Neighbor in PIM
PIM Hello Query
306 A50010-Y3-C150-2-7619
Bootstrap Router BSR
To activate PIM-SM debugging, use the following command
BSR and RP
PIM Debug
RP Information
Static RP for Certain Group
Ip pim bsr-candidate
Global Clears all RP sets Set
Enabling Transmission of Candidate RP Message
A50010-Y3-C150-2-7619 309
PIM-SM Registration
4.3
4.4 Ignoring RP Priority
Rate Limit of Register Message
Configure filtering out multicast sources
Command Mode Description Ip pim register-suppression
Filters for Register Message from RP
Source Address of Register Message
SPT Switchover
This command is disabled by default
Reachability for PIM Register Process
312 A50010-Y3-C150-2-7619
Cisco Router Interoperability
PIM Join/Prune Interoperability
Checksum of Full PIM Register Message
With older Cisco IOS versions, use the following command
8.2 Candidate RP Message with Cisco BSR
8.3 Excluding GenID Option
With older Cisco IOS versions
PIM-SSM Group
PIM Snooping
Displaying PIM-SM Configuration
316 A50010-Y3-C150-2-7619
IP Routing Protocol
Border Gateway Protocol BGP
Configuration Type of BGP
Basic Configuration
Enabling BGP Routing
Go back to Global Configuration mode using the exit command
Advanced Configuration
Disabling BGP Routing
Command Mode Description Aggregate-address A.B.C.D/M
Summary of Path
Automatic Summarization of Path
As-set summary-only
Multi-Exit Discriminator MED
Choosing Best Path
Bgp deterministic-med
No bgp deterministic-med
Command Mode Description Bgp bestpath as-path ignore
Command Mode Description Bgp bestpath compare-confed
Selects the best path using the router ID for identical
Aspath
Configures the router to consider the MED in choosing
Graceful Restart
IP Address Family
Restart Time
Stalepath Time
324 A50010-Y3-C150-2-7619
BGP Neighbor
Default Route
Peer Group
Route Map
To create a BGP Peer Group, use the following command
Force Shutdown
Session Reset of All Peers
BGP Session Reset
Word shutdown
Session Reset of Peers within Particular AS
328 A50010-Y3-C150-2-7619
Session Reset of External Peer
Session Reset of Specific Route
A50010-Y3-C150-2-7619 329
Session Reset of Peer Group
330 A50010-Y3-C150-2-7619
Displaying and Managing BGP
A50010-Y3-C150-2-7619 331
332 A50010-Y3-C150-2-7619
NEIGHBOR-IP routes
Open Shortest Path First Ospf
Enabling Ospf
334 A50010-Y3-C150-2-7619
Command Mode Description Router ospf
No router ospf
ABR Type Configuration
Command Mode Description Network A.B.C.D/M area
Compatibility Support
Ospf Interface
Authentication Key
Authentication Type
336 A50010-Y3-C150-2-7619
Interface Cost
A50010-Y3-C150-2-7619 337
Blocking Transmission of Route Information Database
Routing Protocol Interval
To configure a transmit delay, use the following command
To configure a dead interval, use the following command
A50010-Y3-C150-2-7619 339
Ospf Priority
Ospf Maximum Transmission Unit MTU
340 A50010-Y3-C150-2-7619
Ospf Network Type
Non-Broadcast Network
A50010-Y3-C150-2-7619 341
Ospf Area
Area Authentication
342 A50010-Y3-C150-2-7619
Default Cost of Area
Area 0-4294967295filter-list access LIST-NAMEin out
No area 0-4294967295filter- list access LIST-NAMEin out
Area 0-4294967295filter-list prefix LIST-NAMEin out
Default-information-originate
Not So Stubby Area Nssa
No-redistribution
No-summary
To delete configured NSSA, use the following command
Originate metric Router Configures Nssa with one option
A50010-Y3-C150-2-7619 345
Originate
Area Range
Shortcut Area
346 A50010-Y3-C150-2-7619
C.D/M advertise not Advertise
Stub Area
Virtual Link
Dead-interval
Transmit-delay
348 A50010-Y3-C150-2-7619
Default Metric
To delete the configuration, use the following command
Graceful Restart Support
Hello-interval
Helper
Grace-period
350 A50010-Y3-C150-2-7619
Default Route
Opaque-LSA Support
Metric
Metric-type
Metric-type Router Deletes the configuration
Finding Period
Route-map
Metric-type Always Route-map MAP-NAME
Metric-type Route-map MAP-NAME
External Routes to Ospf Network
A50010-Y3-C150-2-7619 353
To delete the default metric, use the following command
Router Deletes the default metric
Ospf Distance
External Inter-area Intra-area
To make it as a default, use the following command
Host Route
Passive Interface
A50010-Y3-C150-2-7619 355
Summary Routing Information
Blocking Routing Information
Ospf Monitoring and Management
To display the Ospf database, use the following command
Displaying Ospf Protocol Information
A50010-Y3-C150-2-7619 357
As A.B.C.D
Command Mode Description Show ip ospf interface Interface
358 A50010-Y3-C150-2-7619
Limiting Number of Database
Displaying Debugging Information
A50010-Y3-C150-2-7619 359
Command Mode Description Overflow database
Maximum Process of LSA
360 A50010-Y3-C150-2-7619
Overflow database external
To use RIP protocol, you should enable RIP
Routing Information Protocol RIP
Enabling RIP
A50010-Y3-C150-2-7619 361
Configure the network to operate as RIP
RIP Neighbor Router
RIP Version
Creating available Static Route only for RIP
Redistributing Routing Information
Command Mode Description Route-map TAG deny permit
Metrics for Redistributed Routes
Originating Default Information
Administrative Distance
Routing Information Filtering
Disabling the transmission to Interface
Filtering Access List and Prefix List
Offset List
RIP Network Timer
Update
Timeout
Maximum Number of RIP Routes
Authentication Key
To adjust the timers, use the following command
No timers basic Update Time
Split Horizon
Restarting RIP
To disable RIP authentication, use the following command
UDP Buffer Size of RIP
Monitoring and Managing RIP
372 A50010-Y3-C150-2-7619
Command Mode Description Copy ftp tftp os Download
General Upgrade
A50010-Y3-C150-2-7619 373
Boot Mode Upgrade
374 A50010-Y3-C150-2-7619
To configure a subnet mask, use the following command
To configure a default gateway, use the following command
To the boot mode only
A50010-Y3-C150-2-7619 375
Boot load os1 10.27.41.82 V5212G.3.18.x
376 A50010-Y3-C150-2-7619
Uploads the new system software using the following command
FTP Upgrade
A50010-Y3-C150-2-7619 377
Exit the FTP client using the following command
Command! For more information, see Section
Command Mode Description Exit
378 A50010-Y3-C150-2-7619
Access Control List
Address Resolution Protocol
Command Line Interface
CoS Class of Service
Internet Service Provider
Loss of Signal
Loss of Power
Medium Access Control
Type of Service
Spanning Tree Protocol
Software
Transmission Control Protocol

 Server
Server