5
Clustering Example With Non-Check Point VPN
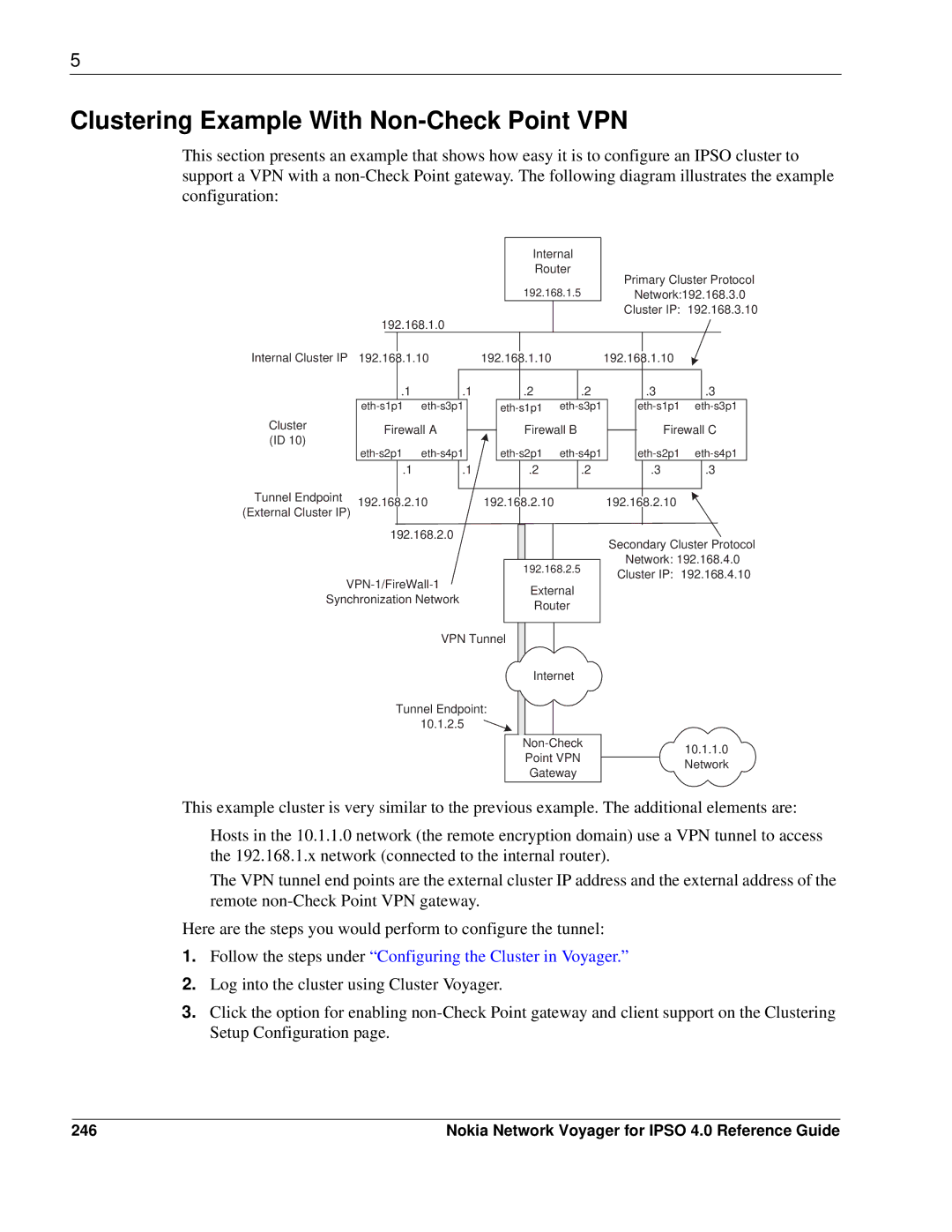
This section presents an example that shows how easy it is to configure an IPSO cluster to support a VPN with a
Internal Cluster IP
Cluster (ID 10)
|
|
|
|
|
|
|
|
|
|
|
| Internal |
|
|
|
|
|
|
|
| |
|
|
|
|
|
|
|
|
|
|
|
| Router |
| Primary Cluster Protocol | |||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |||||||
|
|
|
|
|
|
|
| 192.168.1.5 |
| Network:192.168.3.0 | |||||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| Cluster IP: 192.168.3.10 | ||||||
192.168.1.0 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||||
192.16 |
| .1.10 |
|
| 192.16 |
|
| .1.10 |
| 192.16 |
|
| .1.10 |
|
|
| |||||
8 |
| 8 |
|
| 8 |
|
|
| |||||||||||||
.1 |
| .1 |
|
|
|
| .2 | .2 |
|
|
| .3 |
|
| |||||||
|
|
|
|
|
|
|
|
| .3 |
| |||||||||||
|
|
|
|
| |||||||||||||||||
| Firewall A |
|
|
|
|
| Firewall B |
|
|
|
| Firewall C |
| ||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| ||
|
|
|
|
| |||||||||||||||||
| .1 | |||
Tunnel Endpoint |
|
|
| |
192.16 | 8 | .2.10 | ||
(External Cluster IP) | ||||
|
|
| ||
.1 | .2 | .2 | .3 |
|
|
|
|
|
|
|
|
192.168.2.10 192.168.2.10
.3
192.168.2.0 |
| |
| 192.168.2.5 | |
External | ||
Synchronization Network | ||
Router | ||
| ||
VPN Tunnel |
| |
| Internet | |
Tunnel Endpoint: |
| |
10.1.2.5 |
|
Point VPN
Gateway
Secondary Cluster Protocol
Network: 192.168.4.0
Cluster IP: 192.168.4.10
10.1.1.0
Network
This example cluster is very similar to the previous example. The additional elements are:
Hosts in the 10.1.1.0 network (the remote encryption domain) use a VPN tunnel to access the 192.168.1.x network (connected to the internal router).
The VPN tunnel end points are the external cluster IP address and the external address of the remote
Here are the steps you would perform to configure the tunnel:
1.Follow the steps under “Configuring the Cluster in Voyager.”
2.Log into the cluster using Cluster Voyager.
3.Click the option for enabling
246 | Nokia Network Voyager for IPSO 4.0 Reference Guide |