17
802.1X CONFIGURATION GUIDE
n | The following configurations involve most AAA/RADIUS configuration commands. |
Refer to “AAA Configuration” in the Configuration Guide for your product for | |
| information about the commands. Configurations on the user host and the |
| RADIUS servers are omitted. |
|
|
Configuring 802.1x | As a |
Access Control | of users at the port level. A user host connected to an |
| access control device can access the resources on the LAN only after passing |
| authentication. |
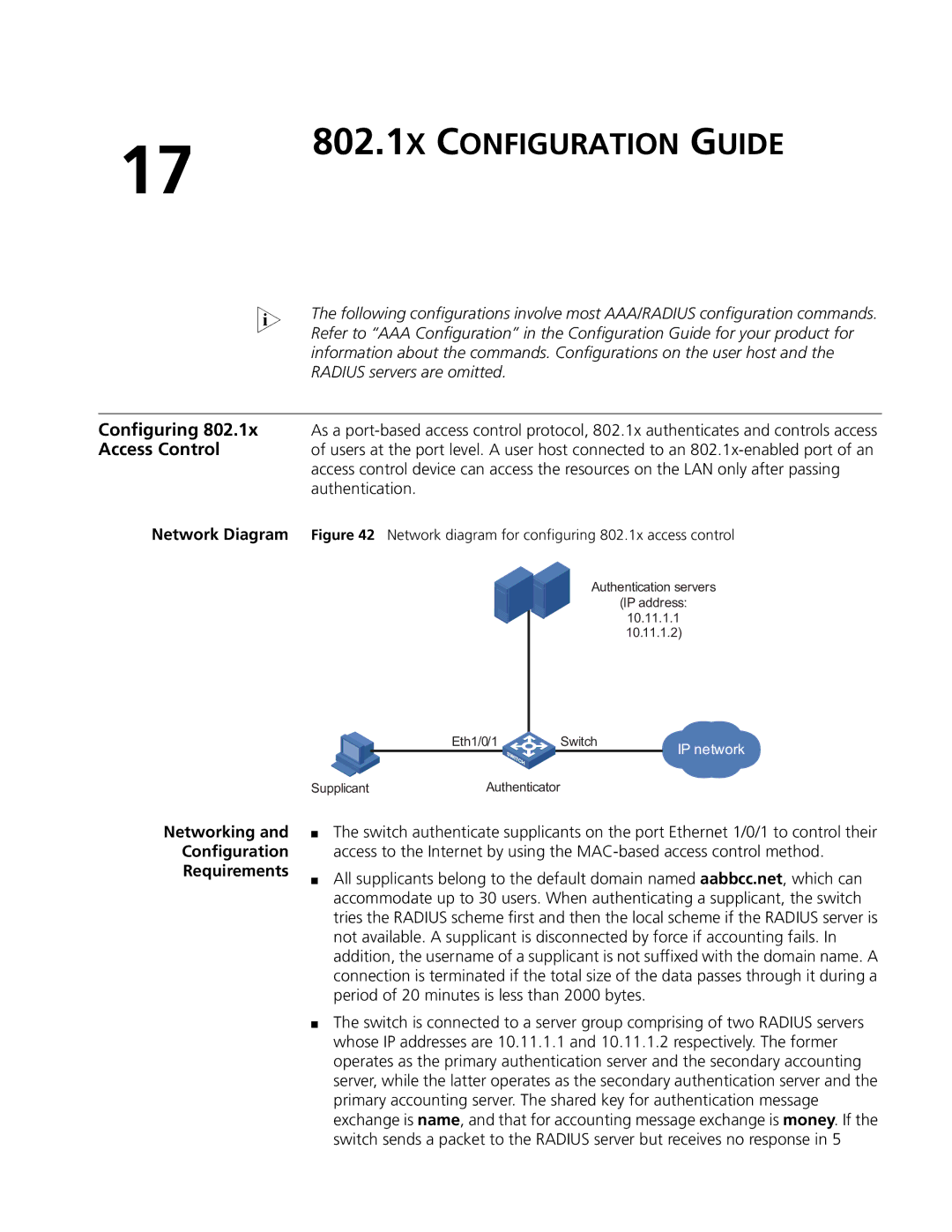
Network Diagram | Figure 42 Network diagram for configuring 802.1x access control |
Networking and
Configuration
Requirements
Authentication servers
(IP address:
10.11.1.1
10.11.1.2)
| Eth1/0/1 | Switch | IP network |
Supplicant | Authenticator |
| |
|
|
■The switch authenticate supplicants on the port Ethernet 1/0/1 to control their access to the Internet by using the
■All supplicants belong to the default domain named aabbcc.net, which can accommodate up to 30 users. When authenticating a supplicant, the switch tries the RADIUS scheme first and then the local scheme if the RADIUS server is not available. A supplicant is disconnected by force if accounting fails. In addition, the username of a supplicant is not suffixed with the domain name. A connection is terminated if the total size of the data passes through it during a period of 20 minutes is less than 2000 bytes.
■The switch is connected to a server group comprising of two RADIUS servers whose IP addresses are 10.11.1.1 and 10.11.1.2 respectively. The former operates as the primary authentication server and the secondary accounting server, while the latter operates as the secondary authentication server and the primary accounting server. The shared key for authentication message exchange is name, and that for accounting message exchange is money. If the switch sends a packet to the RADIUS server but receives no response in 5