Configuring Port Security
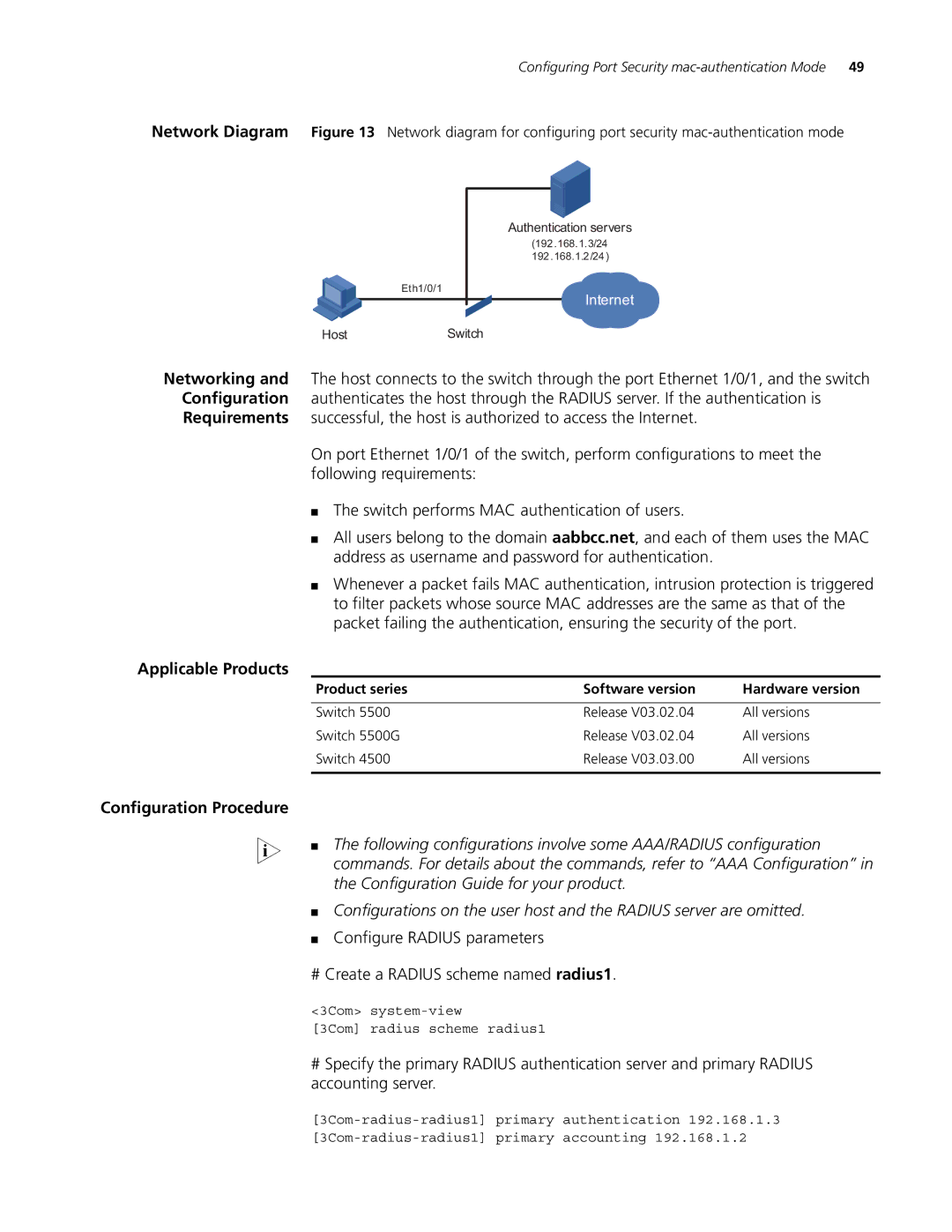
Network Diagram Figure 13 Network diagram for configuring port security
Authentication servers
(192.168.1.3/24
192.168.1.2/24)
Eth1/0/1
Internet
HostSwitch
Networking and The host connects to the switch through the port Ethernet 1/0/1, and the switch Configuration authenticates the host through the RADIUS server. If the authentication is Requirements successful, the host is authorized to access the Internet.
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
■The switch performs MAC authentication of users.
■All users belong to the domain aabbcc.net, and each of them uses the MAC address as username and password for authentication.
■Whenever a packet fails MAC authentication, intrusion protection is triggered to filter packets whose source MAC addresses are the same as that of the packet failing the authentication, ensuring the security of the port.
Applicable Products
Product series | Software version | Hardware version |
|
|
|
Switch 5500 | Release V03.02.04 | All versions |
Switch 5500G | Release V03.02.04 | All versions |
Switch 4500 | Release V03.03.00 | All versions |
|
|
|
Configuration Procedure |
|
|
n | ■ The following configurations involve some AAA/RADIUS configuration | |
| commands. For details about the commands, refer to “AAA Configuration” in | |
|
| the Configuration Guide for your product. |
| ■ Configurations on the user host and the RADIUS server are omitted. | |
| ■ | Configure RADIUS parameters |
# Create a RADIUS scheme named radius1.
<3Com>
[3Com] radius scheme radius1
# Specify the primary RADIUS authentication server and primary RADIUS accounting server.