Configuring Port Security mac-else-userlogin-secure-ext Mode 55
Configuring Port Security
In
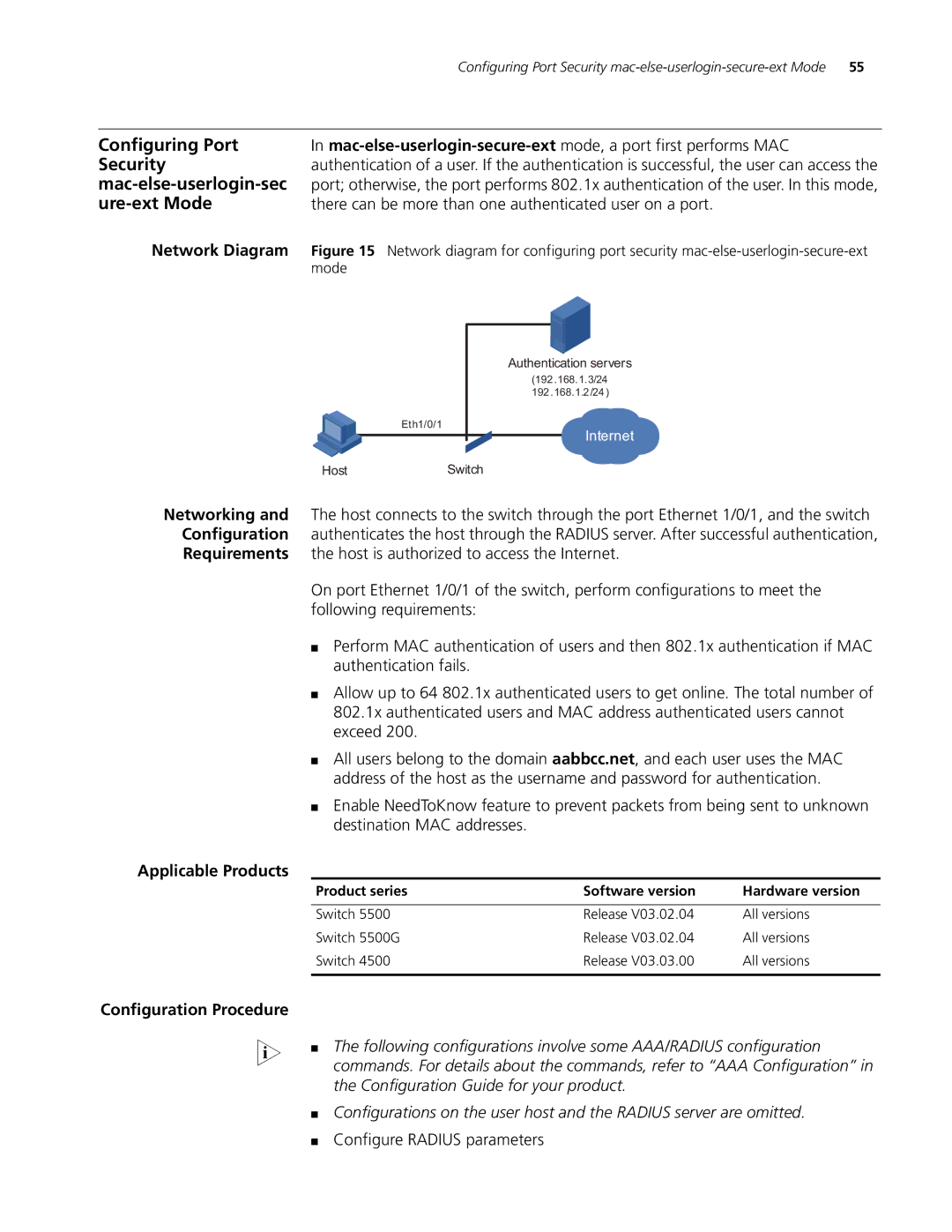
Network Diagram Figure 15 Network diagram for configuring port security
Eth1/0/1
Authentication servers
(192.168.1.3/24
192.168.1.2/24)
Internet
HostSwitch
Networking and The host connects to the switch through the port Ethernet 1/0/1, and the switch Configuration authenticates the host through the RADIUS server. After successful authentication, Requirements the host is authorized to access the Internet.
On port Ethernet 1/0/1 of the switch, perform configurations to meet the following requirements:
■Perform MAC authentication of users and then 802.1x authentication if MAC authentication fails.
■Allow up to 64 802.1x authenticated users to get online. The total number of 802.1x authenticated users and MAC address authenticated users cannot exceed 200.
■All users belong to the domain aabbcc.net, and each user uses the MAC address of the host as the username and password for authentication.
■Enable NeedToKnow feature to prevent packets from being sent to unknown destination MAC addresses.
Applicable Products
Product series | Software version | Hardware version |
|
|
|
Switch 5500 | Release V03.02.04 | All versions |
Switch 5500G | Release V03.02.04 | All versions |
Switch 4500 | Release V03.03.00 | All versions |
|
|
|
Configuration Procedure |
|
|
n | ■ The following configurations involve some AAA/RADIUS configuration | |
| commands. For details about the commands, refer to “AAA Configuration” in | |
|
| the Configuration Guide for your product. |
| ■ Configurations on the user host and the RADIUS server are omitted. | |
| ■ | Configure RADIUS parameters |