Adit 3000 Series Multi-Service Router MSR Card
Customer Support
Corporate Contact Information
Supporting Software Versions
Preface
Preface
Table of Contents
Global Configuration Mode
Configuration LCC Controller Mode
Configuration T1 Controller Mode
Configuration Dial Peer FXS Mode
Configuration Dhcp Pool Ethernet Mode
Configuration Dial Peer Trunk Mode
Configuration Dial Peer VoIP Mode
Configuration Ethernet Interface Mode
Configuration Multilink Interface Mode
Configuration Serial Interface Mode
Configuration IPSec Mode
Configuration L2TPC Mode
Configuration Ospf Mode
Configuration Pptpc Mode
Configuration Radius Mode
Configuration Pptps Mode
Configuration Vlan Mode
Configuration Vlan Port Mode
Configuration Voice Port Mode
Configuration Voice Port FXS Mode
Configuration Voice Port Trunk Mode
Configuration Voice Service SIP Mode
Index
Xviii
Introduction
This Chapter
Overview
Prompt Identifier
Configuration Mode
Configuration Mode Link to Command Prompt Displayed
Example config# clock source 12 noneds1 1ds1 2ds1 3ds1
Example config# clock 12 source nonet1 port
Shortcuts
User Mode Commands
User Mode
Date Enable End Exit Help History Ping Show Traceroute
Enable
Example adit 3500 enable Password Adit 3500#
Date
End
Exit
Help
History
Ping
Syntax ping address -i time -l size -n count -w timeoutstop
Stop
Show
Show alarms
Show arp
Syntax show arp alladdressethernet port
All Display entire ARP table
Address
Show caclkcd
Show caclkcd Example Adit 3500 show caclkcd
Show config dynamic-dns
Show controller lcc
Syntax show controller lcc number
Example Adit MSR show controller lcc
Syntax show controller t1 port
Show controller t1
Example Adit 3500 show controller t1
Show digit-map
Show dhcp-leases
Syntax show digit-map Example Adit 3500 show digit-map
Show interface description
Show interface multilink
Show interface ethernet
Adit 3104, Adit 3200, Adit 3500 Value must be
Show interface serial
Syntax show interface serial port
Example Adit 3500 show interface serial
Example Adit MSR show interface serial
Show interface stats
Example Adit MSR show interface stats
Supported PlatformsAdit 3104, Adit 3200, Adit 3500, MSR
Show ip ospf
Syntax show ip ospf Example adit 3500 show ip ospf
Show ip ospf database
Example adit 3500 show ip ospf database
Example adit 3500 show ip ospf database self-originate
Show ip ospf interface
Ethernet port
Serial port
Multilink port
Show ip ospf neighbor
Interface address
Detail
Example adit 3500 show Ip ospf neighbor
Show licenses
Firewall
Pri
Sip
Show mac-address-table
Example Adit 3500 show log t1 1 minor
Show nat-fw
Syntax show nat-fw Example Adit 3500 show nat-fw
Show route
Show port-trigger
Syntax show route Example Adit 3500 show route
Show service
Syntax show service Example Adit 3500 show service
Show users
Show version
Syntax show users Example Adit 3500 show users
Syntax show version Example Adit 3500 show version
Example Adit MSR show version
Show voice-port fxs
Syntax show voice-port fxs
Example Adit 3500 show voice-port fxs
Example Adit MSR show voice-port fxs
Syntax show voice-port trunk port
Show voice-port trunk
Example Adit 3500 show voice-port trunk
Example Adit MSR show voice-port trunk
Traceroute
Syntax traceroute Syntax traceroute addresshostnamestop
User Mode
Privileged Mode
Privileged Mode Commands
Clear
Clear arp
Clear caclkcd
Clear ip ospf process
Configure terminal
Copy defaults
Copy
Copy path
Copy running-config
Syntax # copy running-config path destination-path
Destination-path
Example Adit 3500# date Wed Jan 12 103751
Debug
Debug portmon all
Debug portmon rxtxboth
Debug portmon detail
Both
Off
Ethernet
Debug portmon ethernet
Example adit 3500# debug portmon ethernet 1 all
Debug portmon management
Syntax # debug portmon management hushoff
Hush Off
Example adit 3500# debug portmon management hush
Debug portmon multilink
Syntax # debug portmon raw offon
Debug portmon raw
Example adit 3500# debug portmon raw off
Port
Debug portmon serial
Example adit 3500# debug portmon 1 rip
Syntax # debug trace casprisip enabletxrx
Example adit 3500# debug trace cas enable
Debug trace
Example adit 3500# end Username
Adit 3500# help
Syntax # history Example adit 3500# history
Log clear
Syntax # log clear allfirewallprisipsystemt1lcc
Lcc
Example adit 3500# log clear firewall
No debug
No debug portmon
No debug trace
Cas Pri Sip
Example Adit 3500# ping
Example Adit 3500# ping 192.168.1.1 -n 2 -l
Example adit 3500# reload Going to reboot Restarting system
Reload
Show
Example adit 3500# show alarms major
Syntax # show arp alladdressethernet port
Example adit 3500# show arp ethernet
Example adit 3500# show arp
Example adit 3500# show arp all
# show caclkcd Example adit 3500# show caclkcd
Show config access-control
Syntax # show config controller t1 port
Example adit 3500# show config controller t1
Dmz-host 192.168.1.200 enable
Syntax # show config interface ethernet port
Example adit 3500# show config interface ethernet
Syntax # show config interface multilink port
Example adit 3500# show config interface multilink
Syntax # show config interface serial port
Example adit 3500# show config interface serial
Syntax # show config ip dhcp ethernet port
Example adit 3500# show config ip dhcp ethernet
Network-object id 0 description NetworkObject1 ip-address
Security-default typical
Static-dns hostname test1 ip-address
Syntax # show config voice-port fxs port
Example adit 3500# show config voice-port fxs
Example adit 3500# show config voice-port trunk
Syntax # show config voice-port trunk port
Example adit MSR# show config voice-port trunk
Syntax # show controller lcc number
Syntax # show controller t1 port
Example adit 3500# show controller t1
Syntax # show digit-map Example adit 3500# show digit-map
Example Adit MSR# show interface description
Syntax # show interface ethernet port
Example adit 3500# show interface ethernet
Syntax # show interface multilink port
Example adit 3500# show interface multilink
Example adit 3500# show interface serial
Syntax # show interface serial port
Example adit MSR# show interface serial
Syntax # show ip ospf Example adit 3500# show ip ospf
Show ip ospf database
Example adit 3500# show ip ospf database
Example adit 3500# show ip ospf database self-originate
Example adit 3500# show ip ospf interface ethernet
Example adit 3500# show Ip ospf neighbor
Example adit 3500# show ip ospf neighbor detail
Syntax # show ipsec vpnipsecconnection-id
Example adit 3500# show l2tpc
Syntax # show l2tpc l2tpc connection-id
Example adit 3500# show l2tpc l2tpc
# show licenses
Example adit 3500# show licenses
Example adit 3500# show log t1 1 minor
Syntax # show nat-fw Example adit 3500# show nat-fw
Show port-trigger
Example adit 3500# show pptpc
Syntax # show pptpc pptpc connection-id
Example adit 3500# show pptpc pptpc
Syntax # show pptps Example adit 3500# show pptps
Syntax # show route Example adit 3500# show route
Show running-config
Privileged Mode
Example adit MSR# show running-config
Privileged Mode
Privileged Mode
Privileged Mode
Supported Platforms Adit 3104, Adit 3200, Adit 3500, MSR
# show service Example adit 3500# show service
Syntax # show users Example adit 3500# show users
Syntax # show version Example adit 3500# show version
Example Adit MSR# show version
Example adit 3500# show voice-port fxs
Syntax # show voice-port fxs
Example adit MSR# show voice-port fxs
Syntax # show voice-port trunk port
Example adit 3500# show voice-port trunk
Example adit MSR# show voice-port trunk
Upgrade
Syntax # upgrade ip-address address file filename check
Syntax # traceroute Syntax # traceroute addresshostnamestop
Example Adit 3500# traceroute to
Privileged Mode
Global Configuration Mode
Commands for Entering Configuration Submodes
Global Configuration Commands
Access
Access-control
Lan Wan
Lan
Access-list
Authentication login
Syntax config# clock 12 source nonet1 port
Example config# clock 1 source t1
Clock source
Controller lcc
Controller t1
Date auto-time-update
Date set
Ntp
Tod
Example config# date summer-time 03 28 0000 10 28 0100
Date summer-time
Delete local-server
Date timezone
Dial-peer voice
Dial-peer voice pots fxs
Dial-peer voice pots trunk
Adit 3500 Range =
Dmz-host
Dial-peer voice voip
User Mode Commands
Privileged Mode Commands
Dynamic-dns backup-mx
Syntax config# dynamic-dns interface eth-2mlink-1ser-n
Example config# dynamic-dns interface ser-1
Dynamic-dns
Dynamic-dns offline
Dynamic-dns mail-exchanger
Dynamic-dns username
Syntax config# exit Example config# exit
Syntax config# end Example config# end
Dynamic-dns wildcard
Config# help Or config# ?
Config# help
History
Syntax config# interface ethernet port
Example config# interface ethernet Config-int-eth-1#
Host-filter
Interface ethernet
Interface multilink
Interface serial
Adit 3104, Adit 3200, Adit 3500 Value must be
Adit 3200, Adit 3500 Range =
Ipsec authentication-retries
Example config# ipsec authentication-retries 10 delay
Ipsec
Ipsec key generate key
Example config# ipsec log ike msg-outp
Ipsec log ike
Ipsec net-to-host
Ipsec log ipsec
Any
Ipsec net-to-net
Ipsec replay
Ipsec vpnipsec
Remote-ip
Ip domain-name
Ip dhcp pool ethernet
Ip host
Key
L2tpc
Key-code
Ipsec
Local-server
New
Log lcc buffer
Log
Log lcc notify
Log pri
Log security buffer
Example config# log security notify warn
Example config# log sip buffer-fill
Log security notify
Log sip
Syntax config# log system buffer kilobytes
Example config# log system buffer
Example config# log system notify error
Log system buffer
Syntax config# log t1 buffer kilobytes
Example config# log t1 buffer
Example config# log t1 notify warn
Log t1 buffer
Mail-server authentication enable
Mail-server
Mail-server from-address
Mail-server host
Syntax config# mail-server port port
Example config# mail-server port
Mail-server port
Mail-server username
Enable
Example config# nat-bypass ip-address 10.10.2.1 mask
Nat-bypass
Network-object
No access
No commands
No access-control
No authentication login
No access-list
No date auto-time-update
No date summer-time
No dial-peer voice pots fxs
No dial-peer voice pots trunk
Adit 3500 Range =
No dmz-host
No dial-peer voice voip
No dynamic-dns
No host-filter
No ipsec authentication-retries
No ipsec log ike
No ipsec log ipsec
Example config# no ipsec log ipsec tc
No ipsec replay
No interface multilink
No ipsec vpnipsec
No interface serial
No key
No ip dhcp pool ethernet
No l2tpc
No mail-server authentication
No local-server
No log sip
No nat-bypass
No network-object
No port-trigger-service
No pptpc
No remote-admin icmp
No remote-admin snmp
Syntax config# no pptps Example config# no pptps
No pptps
No remote-admin udp-trace
No remote-admin telnet
Example config# no remote-admin telnet primary-port
Example config# no remote-admin web primary-port
No remote-admin web
No router ospf
Setting
Syntax config# no security-log setting
No security-log
No service
Syntax config# no service service-id
Example config# no service-id
No snmp-server
No time-range
No static-dns
No username
No voice-codec
No vlan
No voice-port trunk
Pptpc
Port-trigger service
Pptps
Remote-admin
Remote-admin icmp
Remote-admin snmp
Radius-client
Remote-admin telnet
Remote-admin udp-trace
Example config# remote-admin telnet primary-port enable
Primary-port
Example config# remote-admin web primary-port enable
Remote-admin web
Router ospf
Security-default
Typical default
Maximum
Minimum
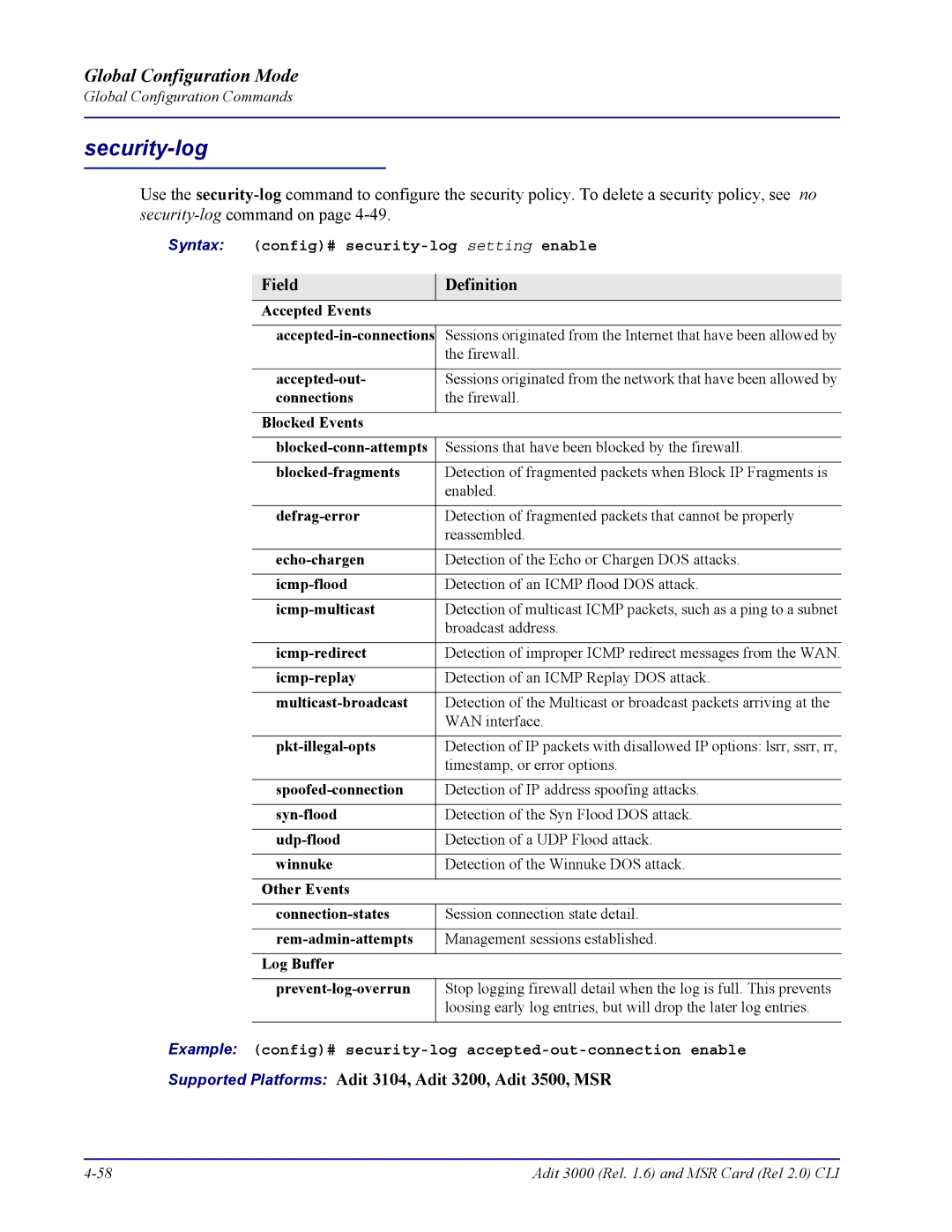
Security-log
Service
Snmp-server enable
Snmp-server
Snmp-server community
Server-src-port
Snmp-server traps enable
Snmp-server host
Snmp-server trusted-ip
Version
Static-dns
Time-range
Admin
Username
Vlan global
Monitor
Vlan vlan-id
Voice-codec
Syntax config# voice-port fxs port
Example config# voice-port fxs 1 config-vport-fxs-1#
Voice-port global
Voice-port fxs
Voice-service sip
Syntax config# voice-port trunk port
Example config# voice-port trunk 1 config-vport-trk-1#
Voice-port trunk
LCC Controller Commands
Configuration LCC Controller Mode
Description End Exit History No command Shutdown
Example config-cont-lcc-1# description LCC#1
Syntax config-cont-lcc-n# description text
Description
User Mode Commands
Syntax config-cont-lcc-n# end Example config-cont-lcc-1# end
No command
No shutdown
Shutdown
Configuration T1 Controller Mode
T1 Controller Commands
Syntax config-cont-t1-n# description text
Example config-cont-t1-1# description T1#1
User Mode Commands
Syntax config-cont-t1-n# ds0-group timeslots range
Example config-cont-t1-1# ds0-group timeslots
Syntax config-cont-t1-n# end Example config-cont-t1-1# end
Ds0-group
Fdl
Framing
None T1.403
Esf
Example config-cont-t1-1# idle-pattern 0x7f
Syntax config-cont-t1-n# idle-pattern number
Idle-pattern
Lbo long
Lbo
Lbo short
Loopback
Linecode
Ami B8zs
Loopdetect
No ds0-group
No pri-group
Csu Niu None
No tdm-group
Pri-group
In-out
Example config-cont-t1-1# tdm-group timeslots 1-4 dir in-out
Tdm-group
Threshold
Configuration Dhcp Pool Ethernet Mode
Dhcp Pool Commands
Configuration Dhcp Pool Ethernet Mode
Example config-dhcp-eth-1# end-address
Syntax config-dhcp-eth-n# end-address address
End-address
Example config-dhcp-eth-1# lease
Syntax config-dhcp-eth-n# lease time
Lease
No relay
No option
No static-lease
Option
Relay
Syntax config-dhcp-eth-n# start-address address
Example config-dhcp-eth-1# start-address
Start-address
Static-lease
Subnet-mask
Wins server
Configuration Dial Peer FXS Mode
Dial Peer FXS Commands
Block-out-caller-id
Call-wait-caller-id
Call-waiting
Calling-party-disc
Codec preference
Destination-pattern
123
G711alaw
User Mode Commands
Syntax config-dpeer-fxs# end Example config-dpeer-fxs# end
Syntax config-dpeer-fxs# fax-protocol nonepass-throught38
Example config-dpeer-fxs# fax-protocol none
Fax-protocol
Pass-through
Example config-dpeer-fxs# modem-protocol pass-though
Syntax config-dpeer-fxs# modem-protocol nonepass-through
Modem-protocol
No block-out-caller-id
No call-wait-caller-id
No call-waiting
No calling-party-disc
No sip-authentication
Syntax config-dpeer-fxs# no codec preference
Example config-dpeer-fxs# no codec preference
No codec preference
Sip-authentication
Sip-authentication enable
Sip-authentication password
Sip-authentication username
Configuration Dial Peer Trunk Mode
Dial Peer Trunk Commands
Syntax config-dpeer-trk# destination-pattern dest-pattern
Example config-dpeer-trk# codec preference 1 g711alaw
Example config-dpeer-trk# destination-pattern 555$
User Mode Commands
Syntax config-dpeer-trk# fax-protocol nonepass-throught38
Syntax config-dpeer-trk# end Example config-dpeer-trk# end
Example config-dpeer-trk# fax-protocol none
Syntax config-dpeer-trk# modem-protocol nonepass-through
Example config-dpeer-trk# modem-protocol pass-though
Example config-dpeer-trk# no codec preference
Syntax config-dpeer-trk# no codec preference
No destination-pattern
Syntax config-dpeer-trk# prefix prefix
Example config-dpeer-trk# prefix
Prefix
Prefix
Example config-dpeer-trk# strip-digits
Syntax config-dpeer-trk# strip-digits number
Strip-digits
Configuration Dial Peer VoIP Mode
Dial Peer VoIP Commands
Syntax config-dpeer-voip# destination-pattern number
Example config-dpeer-voip# destination-pattern
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 10-3
Syntax config-dpeer-voip end Example config-dpeer-voip# end
No prefix
No session-target
Syntax config-dpeer-voip# prefix prefix
Example config-dpeer-voip# prefix
Example config-dpeer-voip# session-target ip-address
Session-target
Syntax config-dpeer-voip# strip-digits number
Example config-dpeer-voip# strip-digits
Syntax config-dpeer-voip# user-id user-id
Example config-dpeer-voip# user-id testname
10-8 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Ethernet Interface Mode
Ethernet Interface Commands
Syntax config-int-eth-n# description text
Example config-int-eth-1# description Eth#1
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 11-3
Syntax config-int-eth-n# end Example config-int-eth-1# end
Firewall
Full-duplex
Half-duplex
Example config-int-eth-1# ip address 192.168.2.100 mask
Ip address
Auto
Secondary
Ip default-gateway
Ip default-route
Syntax config-int-eth-n# ip default-gateway address
Example config-int-eth-1# ip default-gateway
Syntax config-int-eth-n# ip mtu sizeauto
Example config-int-eth-1# ip mtu auto
Ip mtu
Auto
Message-digest
Ip ospf authentication
Null
Ip ospf cost
Ip ospf authentication-key
Ip ospf dead-interval
Ip ospf disable
Syntax config-int-eth-n# ip ospf hello-interval seconds
Example config-int-eth-1# ip ospf hello-interval
Ip ospf hello-interval
Ip ospf priority
Ip ospf transmit-delay
Ip ospf retransmit-interval
Syntax config-int-eth-n# ip primary-dns address
Example config-int-eth-1# ip primary-dns
Ip primary-dns
Ip proxy-arp
Ip rip enable
Ip rip
Ip rip receive-version
Ip rip send-version
Syntax config-int-eth-n# ip route-mode naptroute
Example config-int-eth-1# ip route-mode napt
Ip route
Ip route-mode
Ip secondary-dns
Metric
No ip default-route
No firewall
No ip address
No ip dhcp
No ip ospf authentication
No ip ospf authentication-key
No ip ospf cost
No ip ospf dead-interval
No ip ospf disable
Example config-int-eth-1# no ip ospf message-digest-key
No ip ospf hello-interval
No ip ospf message-digest-key
No ip ospf transmit-delay
No ip ospf priority
No ip ospf retransmit-interval
No ip primary-dns
No ip proxy-arp
No ip rip
No ip route
No ip secondary-dns
No schedule-availability
No remote-admin
No sip-alg
Renew
Release
No tos ip
Syntax config-int-eth-n# schedule-availability time-range
Example config-int-eth-1# schedule-availability time-range
Schedule-availability
Sip-alg
Tos
Speed
100 Auto
11-26 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Multilink Interface Mode
Multilink Interface Commands
Syntax config-int-mlink-n# description text
Example config-int-mlink-1# description MLPPP1
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 12-3
12-4 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Example config-int-mlink-1# ip address 192.168.2.100 mask
Unnumbered
Syntax config-int-mlink-n# ip mtu sizeauto
Example config-int-mlink-1# ip mtu auto
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 12-7
Syntax config-int-mlink-n# ip ospf cost cost
Example config-int-mlink-1# ip ospf cost
Syntax config-int-mlink-n# ip ospf dead-interval seconds
Example config-int-mlink-1# ip ospf dead-interval
Syntax config-int-mlink-n# ip ospf hello-interval seconds
Example config-int-mlink-1# ip ospf hello-interval
Syntax config-int-mlink-n# ip ospf priority priority
Example config-int-mlink-1# ip ospf priority
Example config-int-mlink-1# ip ospf retransmit-interval
Syntax config-int-mlink-n# ip ospf transmit-delay seconds
Syntax config-int-mlink-n# ip primary-dns address
Example config-int-mlink-1# ip primary-dns
Example config-int-mlink-1# ip rip receive-version none
121or2
Example config-int-mlink-1# ip rip send-version 2-bcast
Syntax config-int-mlink-n# ip route-mode naptroute
Example config-int-mlink-1# ip route-mode napt
Syntax config-int-mlink-n# ip secondary-dns address
Example config-int-mlink-1# ip secondary-dns
Syntax config-int-mlink-n# no ip address address
Example config-int-mlink-1# no ip address
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 12-15
Example config-int-mlink-1# no ip ospf message-digest-key
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 12-17
No ppp authentication
Syntax config-int-mlink-n# no ip route dest-ip-addr gateway
Example config-int-mlink-1# no ip route 192.168.100.200
No ppp encryption
No ppp password
No ppp on-demand
No ppp qos interleaving
No ppp username
12-20 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Ppp exec-timeout
Ppp authentication
Ppp encryption
Ppp link-fragmentation
Ppp password
Ppp on-demand
Ppp qos-interleaving
Ppp restart-timer
Ppp time-btwn-reconnect
Syntax config-int-mlink-n# ppp username username
Example config-int-mlink-1# ppp username test-user-name
Syntax config-int-mlink-n# schedule-availability time-range
Ppp username
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 12-25
12-26 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Serial Interface Mode
Serial Interface Commands
Syntax config-int-ser-n# description text
Example config-int-ser-1# description Serial1
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 13-3
Syntax config-int-ser-n# end Example config-int-ser-1# end
Encapsulation ppp
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 13-5
Syntax config-int-ser-n# ip mtu sizeauto
Example config-int-ser-1# ip address 192.168.2.100 mask
Example config-int-ser-1# ip mtu auto
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 13-7
Syntax config-int-ser-n# ip ospf cost cost
Example config-int-ser-1# ip ospf cost
Syntax config-int-ser-n# ip ospf dead-interval seconds
Example config-int-ser-1# ip ospf dead-interval
Syntax config-int-ser-n# ip ospf hello-interval seconds
Example config-int-ser-1# ip ospf hello-interval
Syntax config-int-ser-n# ip ospf priority priority
Example config-int-ser-1# ip ospf priority
Example config-int-ser-1# ip ospf retransmit-interval
Syntax config-int-ser-n# ip ospf transmit-delay seconds
Syntax config-int-ser-n# ip primary-dns address
Example config-int-ser-1# ip primary-dns
Syntax config-int-ser-n# ip rip receive-version 121or2none
Example config-int-ser-1# ip rip receive-version none
Example config-int-ser-1# ip rip send-version 2-bcast
Syntax config-int-ser-n# ip route-mode naptroute
Example config-int-ser-1# ip route-mode napt
Syntax config-int-ser-n# ip secondary-dns address
Example config-int-ser-1# ip secondary-dns
Syntax config-int-ser-n# multilink-group group-number
Example config-int-ser-1# multilink-group
Multilink-group
No encapsulation ppp
Syntax config-int-ser-n# no ip address address
Example config-int-ser-1# no ip address
13-16 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Example config-int-ser-1# no ip ospf message-digest-key
Syntax config-int-ser-n# no ip route dest-ip-addr gateway
Example config-int-ser-1# no ip route 192.168.100.200
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 13-19
13-20 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Ms-chap
Syntax config-int-ser-n# ppp link-fragmentation number
Example config-int-ser-1# ppp link-fragmentation
Syntax config-int-ser-n# ppp password password
Example config-int-ser-1# ppp username test-user-pswrd
Syntax config-int-ser-n# ppp restart-timer seconds
Example config-int-ser-1# ppp restart-timer
Syntax config-int-ser-n# ppp time-btwn-reconnect seconds
Example config-int-ser-1# ppp time-btwn-reconnect
Syntax config-int-ser-n# schedule-availability time-range
Example config-int-ser-1# schedule-availability time-range
Configuration IPSec Mode
IPSec Commands
Authentication
Aggressive-mode
Pre-shared
Rsa-sig
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 14-3
Dpd-enable
Dpd-delay
Dpd-timeout
Encryption
Hash
Group
Md5 Sha
Example config-ipsec-1# ip route metric
Syntax config-ipsec n# ip route metric metric
Ip route metric
Ipsec-conn
Ipsec-manual
Lifetime
Local-subnet
Single ip
Subnet ip
Max-retries
Mode
Transport
Tunnel
Net-type
Netbios remote-brc-addr
Dmz lan wan
No dpd-delay
No dpd-enable
No dpd-timeout
No aggressive-mode
Example config-ipsec-1# no encryption aes
Syntax config-ipsec-n# no group
Example config-ipsec-1# no group
No encryption
No netbios
Syntax config-ipsec-n# no hash md5sha
Example config-ipsec-1# no hash md5
No hash
No reconnect
No set-pfs
No transform-set
Rekey
Reconnect
Remote-ip
Example config-ipsec-1# schedule-availability rule1
Syntax config-ipsec-n# schedule-availability rule-id
Remote-subnet
Set-pfs
Session-key
Example config-ipsec-1# transform-set esp-aes
Transform-set
Example of IPSec Connection Configuration
14-22 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration L2TPC Mode
L2TPC Commands
Configuration L2TPC Mode
Syntax config-l2tpc-n# end Example config-l2tpc-1# end
Example config-l2tpc-1# host-ip
Syntax config-l2tpc-n# host-ip address
Host-ip
Syntax config-l2tpc-n# ip mtu sizeauto
Example config-l2tpc-1# ip address 192.168.2.100 mask
Example config-l2tpc-1# ip mtu auto
15-6 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-l2tpc-n# ip ospf authentication-key password
Example config-l2tpc-1# ip ospf authentication-key pass777
Syntax config-l2tpc-n# ip ospf cost cost
Example config-l2tpc-1# ip ospf cost
Syntax config-l2tpc-n# ip ospf hello-interval seconds
Example config-l2tpc-1# ip ospf hello-interval
Syntax config-l2tpc-n# ip ospf priority priority
Example config-l2tpc-1# ip ospf priority
Syntax config-l2tpc-n# ip ospf retransmit-interval seconds
Example config-l2tpc-1# ip ospf retransmit-interval
Syntax config-l2tpc-n# ip primary-dns address
Example config-l2tpc-1# ip primary-dns
Syntax config-l2tpc-n# ip rip receive-version 121or2none
Example config-l2tpc-1# ip rip receive-version none
Example config-l2tpc-1# ip rip send-version 2-bcast
Local-secret
Syntax config-l2tpc-n# metric metric
Example config-l2tpc-1# metric
Syntax config-l2tpc-n# no ip address address
Example config-l2tpc-1# no ip address
15-14 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 15-15
Syntax config-l2tpc-n# no ip ospf message-digest-key key-id
Example config-l2tpc-1# no ip ospf message-digest-key
Syntax config-l2tpc-n# no ip route dest-ip-addr gateway
Example config-l2tpc-1# no ip route 192.168.100.200
No ppp exec-timeout
No ppp restart-timer
No ppp time-btwn-reconnect
15-20 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Example config-l2tpc-1# ppp authentication chap
Syntax config-l2tpc-n# ppp encryption 40-bit128-bit
Example config-l2tpc-1# ppp encryption 40-bit
Syntax config-l2tpc-n# ppp exec-timeout minutes
Syntax config-l2tpc-n# ppp password password
Example config-l2tpc-1# ppp password test-user-pswrd
Syntax config-l2tpc-n# ppp restart-timer seconds
Example config-l2tpc-1# ppp restart-timer
Syntax config-l2tpc-n# ppp time-btwn-reconnect seconds
Example config-l2tpc-1# ppp time-btwn-reconnect
Syntax config-l2tpc-n# ppp username username
Example config-l2tpc-1# ppp username test-user-name
15-24 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Ospf Mode
Router Ospf Commands
Area authentication
Area commands
Message-digest
Compatible rfc1583
16-4 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-ospf# end Example config-ospf# end
Syntax config-ospf# exit Example config-ospf# exit Config#
Example config-ospf# network 192.168.1.1 0.0.0.255 area
Network area
No area
No area authentication
No area stub
Example config-ospf# no network 192.168.1.1 0.0.0.255 area
No compatible rfc1583
No network area
No router-id
Router-id
Syntax config-ospf# router-id address
Example router-ospf# router-id
Sample Configuration
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 16-11
16-12 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Pptpc Mode
Pptp Client Commands
Configuration Pptpc Mode
Syntax config-pptpc-n# end Example config-pptpc-1# end
Syntax config-pptpc-n# host-ip address
Example config-pptpc-1# host-ip
Syntax config-pptpc-n# ip mtu sizeauto
Example config-pptpc-1# ip address 192.168.2.100 mask
Example config-pptpc-1# ip mtu auto
17-6 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-pptpc-n# ip ospf authentication-key password
Example config-pptpc-1# ip ospf authentication-key pass777
Syntax config-pptpc-n# ip ospf cost cost
Example config-pptpc-1# ip ospf cost
Syntax config-pptpc-n# ip ospf hello-interval seconds
Example config-pptpc-1# ip ospf hello-interval
Syntax config-pptpc-n# ip ospf priority priority
Example config-pptpc-1# ip ospf priority
Syntax config-pptpc-n# ip ospf retransmit-interval seconds
Example config-pptpc-1# ip ospf retransmit-interval
Syntax config-pptpc-n# ip primary-dns address
Example config-pptpc-1# ip primary-dns
Syntax config-pptpc-n# ip rip receive-version 121or2none
Example config-pptpc-1# ip rip receive-version none
Example config-pptpc-1# ip rip send-version 2-bcast
Syntax config-pptpc-n# ip route-mode naptroute
Example config-pptpc-1# ip route-mode napt
Syntax config-pptpc-n# ip secondary-dns address
Example config-pptpc-1# ip secondary-dns
Syntax config-pptpc-n# no ip address address
Example config-pptpc-1# no ip address
17-14 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-pptpc-n# no ip ospf message-digest-key key-id
Example config-pptpc-1# no ip ospf message-digest-key
17-16 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-pptpc-n# no ip route dest-ip-addr gateway
Example config-pptpc-1# no ip route 192.168.100.200
17-18 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 17-19
Syntax config-pptpc-n# ppp encryption 40-bit128-bit
Example config-pptpc-1# ppp authentication chap
Example config-pptpc-1# ppp encryption 40-bit
Syntax config-pptpc-n# ppp exec-timeout minutes
Example config-pptpc-1# ppp exec-timeout
Syntax config-pptpc-n# ppp password password
Example config-pptpc-1# ppp password test-user-pswrd
Syntax config-pptpc-n# ppp restart-timer seconds
Example config-pptpc-1# ppp restart-timer
Syntax config-pptpc-n# ppp time-btwn-reconnect seconds
Example config-pptpc-1# ppp time-btwn-reconnect
Example config-pptpc-1# schedule-availability time-range
17-24 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Pptps Mode
Pptp Server Commands
Configuration Pptps Mode
Syntax config-pptps# end Example config-pptps# end
Syntax config-pptps# end-address end-ip-address
Example config-pptps# end-address
End-ip-address
Syntax config-pptps# idle-time seconds
Example config-pptps# idle-time
Idle-time
Seconds
Example config-pptps# no ppp authentication
Example config-pptps# no ppp encryption
No idle-time
40-bit
Syntax config-pptps# ppp encryption 40-bit128-bitstateful
Example config-pptps# ppp authentication chap
Example config-pptps# ppp encryption stateful
Syntax config-pptps# start-address start-address
Example config-pptps# start-address
Start-ip-address
Enter the start IP address of the range
18-8 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Radius Commands
Configuration Radius Mode
Authentication End Exit History Host Key
Syntax config-radius# authentication chapms-chapms-chapv2pap
Example config-radius# authentication chap
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 19-3
Syntax config-radius# end Example config-radius# end
Syntax config-radius# host address auth-port port
Example config-radius# host 192.168.1.1 auth-port
Syntax config-radius# key password
Example config-radius# key testpswd
19-6 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Vlan Mode
Vlan Global Commands
Configuration Vlan Mode
Syntax config-vlan# end Example config-vlan# end
Syntax config-vlan# exit Example config-vlan# exit Config#
Syntax config-vlan# no port-dot1q ethernet port
Example config-vlan# no port-dot1q ethernet
Syntax config-vlan# no vlan entry
Example config-vlan# no vlan
Adit 3104 and Adit 3200 1.1, 1.2, 1.3, 1.4
Adit 3500 and MSR 1.1
Adit 3104 and Adit 3200 1.1, 1.2, 1.3, 1.4
Disable
Adit 3500 and MSR 1.1
Syntax config-vlan# tag-all disableenable
Example config-vlan# tag-all enable
Syntax config-vlan# vlan-feature disableenable
Disable Disable Vlan feature Enable Enable Vlan feature
20-8 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Vlan Port Commands
Configuration Vlan Port Mode
End Exit History No commands Port Priority Voip-interface
Configuration Vlan Port Mode
Syntax config-vlan-n# end Example config-vlan-100# end
No port
No voip-interface
Syntax config-vlan-n# priority priority
Example config-vlan-100# priority
21-6 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Voice Port Commands
Configuration Voice Port Mode
Digit-map global End Exit History No digit-map global Tos
Long-timeout
Short-timeout
Example config-vport# digit-map mode long-timeout
Digit-map global
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 22-3
Syntax config-vport# end Example config-vport# end
Syntax config-vport# exit Example config-vport# exit Config#
No digit-map global
Pattern number
Rtp value hex-value
Sip value hex-value
22-6 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Voice Port FXS Mode
Voice Port FXS Commands
Example config-vport-fxs-1# description VoiceP-#2
Syntax config-vport-fxs-n# description text
Comfort-noise
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 23-3
23-4 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Syntax config-vport-fxs-n# input-gain value
Example config-vport-fxs-1# input-gain
No comfort-noise
No echo-cancel
No per-line-logging
Syntax config-vport-fxs-n# output-gain value
Example config-vport-fxs-1# output-gain
Syntax config-vport-fxs-n# signal ground-startloop-start
Example config-vport-fxs-1# signal ground-start
Configuration Voice Port Trunk Mode
Voice Port Trunk Commands
Connection lcc
Connection t1
Digit-map
Default
Custom
24-4 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Use the end command to exit the current Configuration mode
Syntax config-vport-trk-n# input-gain value
Example config-vport-trk-1# input-gain
Isdn switch-type PRI
Example config-vport-trk-1# isdn switch-type pri-ni2
No connection lcc
No connection t1
No registration enable
No digit-map
No registration line
No registration line enable
No registration line logging
Syntax config-vport-trk-n# output-gain value
Example config-vport-trk-1# output-gain
Registration line authentication
Registration enable
Registration
Registration line enable
Registration line first-phone-number
Example config-vport-trk-1# signal immediate
Registration line logging
Example config-vport-trk-1# trunk VPtrunk1
Syntax config-vport-trk-n# trunk trunk-id
Trunk
24-16 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Configuration Voice Service SIP Mode
Voice Service SIP Commands
Example config-voice-serv-sip# calling-party-disc
Syntax config-voice-serv-sip# calling-party-disc duration
Conference
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 25-3
Dtmf
Early-media
Inband
Rfc2833
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI 25-5
Fax-protocol-t38 ecs
Fax-protocol-t38 redundancy
Hs-redundancy
Ls-redundancy
Fax-protocol-t38 signaling
Feature-mode
Example config-voice-serv-sip# gateway-ip
Syntax config-voice-serv-sip# gateway-ip address
Gateway-ip
No conference
No outbound-proxy
No prack
No proxy-server
No redundancy rollback-timer
No session-timer mode
No redundancy filter-incoming
No registration ignore-negotiated
Phone-number
Outbound-proxy
Prack
Proxy-server
Privacy-mode
Rfc3325
Example config-voice-serv-sip# proxy-type generic
Example config-voice-serv-sip# redundancy advance-retries
Proxy-type
Redundancy advance-retries
Redundancy advance-timeout
Example config-voice-serv-sip# redundancy advance-timeout
Example config-voice-serv-sip# redundancy primary-address
Redundancy filter-incoming
Redundancy rollback-timer
Example config-voice-serv-sip# redundancy rollback-timer
Example config-voice-serv-sip# redundancy secondary-address
Redundancy secondary-address
Redundancy type
Redundancy ttl
None Srv User
Rtp-base-port
Session-timer mode
Session-timer
Session-timer refresher
Session-timer timeout
Sip-port
Transport
Tcp Udp
25-20 Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI
Index
Index
Adit 3000 Rel .6 and MSR Card Rel 2.0 CLI Index
Index
Index
Index
Index
FXS
Index
Index
Index
Encapsulation ppp
Index
Index
FXS
63,4-64