Version 8.5 January 2015 3725-74300-000B
RealPresence Collaboration Server RMX
Page
Contents
Defining AVC-Based Conference Profiles
108
Sharing Content During Conferences
Defining SVC and Mixed CP and SVC Conference Profiles
131
Customized Content Rate 135
132
135
Implementing Media Encryption for Secured Conferencing
Setting Conferences for Telepresence Mode AVC CP
Additional Conferencing Information
Defining Cascading Conferences
239
Meeting Rooms
Entry Queues, Ad Hoc Conferences and SIP Factories
Address Book
Operator Assistance & Participant Move
Scheduling Reservations
Conference Templates
Using Audible Alarms 349
Start a Conference
349
Conference and Participant Monitoring
Conference and Participant Level Operations
Polycom Conferencing for Microsoft Outlook
Users, Connections, and Notes
Recording and Streaming Conferences
IP Network Services
Network Security 532
Defining ISDN/PSTN Network Services 522
Modifying an ISDN/PSTN Network Service 530
IVR Services 566
Gateway Calls
Call Detail Record CDR Utility
Starting the RMX Web Client
RMX Manager Application 651
Use the RMX Web Client 677
Administration and Utilities
714
Customizing the Multilingual Setting 734
716
717
System Configuration Flags 762
Ultra Secure Mode 812
Polycom, Inc Xxiii
Collaboration Server Hardware Monitoring
Appendix a Disconnection Causes 891
Appendix H Deployment Into Microsoft Environments
Restoring Defaults
Appendix I Polycom Open Collaboration Network Pocn
1023
Multipoint Calls using DMA 1039
1035
1036
Appendix M Homologation for Brazil
Appendix J Restore Defaults
Appendix K SIP RFC Support Appendix L Media Traffic Shaping
Overview
Who Should Read This Guide?
Administration menu
How This Guide is Organized
Prerequisites
About the RealPresence Collaboration Server System
IP Networks
Network Services Guidelines
Isdn Networks
Card Configuration Modes
Viewing the Card Configuration Mode
Differences Between MPMx and MPMRx Media Cards
Features Supported with MPMRx Cards
General RealPresence Collaboration Server Supported Features
Support for Microsoft Protocols, algorithms and workflows
Software Prerequisites and Guidelines
1500/1800/2000/4000 Getting Started Guide
Continuous Presence CP Conferencing
Conferencing Modes Overview
AVC Conferencing
AVC Continuous Presence CP video streams and built layouts
Video Protocol Support in CP Conferences
Video Switching VSW Conferencing
AVC Video Switching VSW video streams and Full Screen Layout
Video Switching VSW Conferencing Guidelines
Up to 2Mbps 160 130 320 260 4Mbps 6Mbps 100 200
AVC Basic Conferencing Parameters
Video resolution
Supplemental Conferencing Features
SVC video streams and Layouts
SVC-based Conferencing
Advantages of SVC Conferencing
SVC Conferencing Guidelines
Fecc
MCU Supported Resolutions for SVC Conferencing
Mixed CP and SVC Conferencing
MCU Resource Capacities for Mixed CP and SVC Conferences
Conferencing Modes Overview
Conferencing Parameters Defined in a Profile
Using Conference Profiles
Conferencing Capabilities in the Various Conferencing Modes
Conferencing Feature
Conference Type
IVR
MCU
Default Profile Settings in CP Conferencing Mode
Default CP Only Conference Profile Settings Value
Echo Suppression
Default SVC Only Conference Profile Settings Value
Default Profile Settings in SVC Only Conferencing Mode
Name Meeting Rooms
Entry Queue
Default SVC Only Conference Profile Settings Value
Default Mixed CP and SVC Conference Profile Settings Value
Default settings are as follows
Name
Viewing the List of Conference Profiles
RMX Management pane, expand the Rarely Used list
To list Conference Profiles
RMX Management pane, click the Conference Profiles button
Conference Profiles Pane Columns Field Description
To modify the Profile properties
Modifying an Existing Profile
Profiles Toolbar
Defining New Profiles
Deleting a Conference Profile
To delete a Conference Profile
To define a new Profile
Guidelines for Exporting and Importing Conference Profiles
Exporting and Importing Conference Profiles
Exporting Conference Profiles
Exporting All Conference Profiles from an MCU
To export selected Conference Profiles
Exporting Selected Conference Profiles
To import Conference Profiles
Importing Conference Profiles
Using Conference Profiles
Defining AVC CP Conferencing Profiles
Defining AVC-Based Conference Profiles
To define a new CP Profile
RMX Management pane, click Conference Profiles
Defining AVC-Based Conference Profiles
Field/Option Description
New AVC CP Profile General Parameters
Profile Support in Video Switching Conferences
Define the following parameters
Click the Advanced tab
New Profile Advanced dialog box opens
New AVC CP Profile Advanced Parameters
Video Quality Optimized
Resource Optimized
For CP Conferences only Click the Gathering Settings tab
Defining New Profiles
New AVC CP Profile Gathering Settings Parameters
New Profile Video Quality dialog box opens
Click the Video Quality tab
New AVC CP Profile Video Quality Parameters
Resolution Configuration dialog box
HD720
HD1080
Information, see Multiple Content Resolutions
Cascade Optimized
263
263 & H.264 Auto Selection
SVC
Video layout
Manual
Defining AVC-Based Conference Profiles
12+
Page
Defining AVC-Based Conference Profiles
Connection to improve call clarity
Participants pane
New AVC CP Profile Audio Settings Parameters
For more details, see Automatic Muting of Noisy Endpoints
New AVC CP Profile IVR Parameters Field/Option Description
New AVC CP Profile IVR Parameters
New Profile Recording dialog box opens
New AVC CP Profile Recording Parameters Description
Video/Voice Port Configuration MPMx
New AVC CP Profile Site Names Parameters
Click the Site Names tab
New Profile Site Names dialog box opens
New AVC CP Profile Site Names Parameters Field Description
Top RightTop LeftMiddle RightMiddle
Selection Site Names Position
Position sliders
Position adjustments using
Horizontal and Vertical
New AVC CP Profile Site Names Parameters
Define the following fields
Defining AVC-Based Conference Profiles
Service Name
Click the Layout Indications tab
Disableselfnetworkind Selfindlocation
Gathering Phase
Additional Information for Setting CP Profiles
Gathering Phase Guidelines
Partygatheringdurationseconds Range 0 3600 seconds
Gathering Phase Duration
Overlay Layouts
Enabling the Gathering Phase Display
Guidelines for using the Overlay Layouts
Selecting the Overlay Layouts
Site Names Definition
Guidelines
Shorten the Site Name Display
Site Names Display Position
Defining AVC-Based Conference Profiles
Same Layout mode
Send Text Message to Participant dialog box is displayed
Select the Enable check box
Click the Message Overlay tab
Selecting the Chinese Font for Text Display
To cancel the Message Overlay display
Selecting the Chinese Font
To send text to selected participants
Defining AVC-Based Conference Profiles
To Create a Video Switching Profile
Defining an AVC Video Switching Conference Profile
Define the New Profile General parameters
CIF
New AVC VSW Profile General Parameters
Minimum Threshold Line Rate System Flags
High Profile Support in Video Switching Conferences
Guidelines
Vswcifhpthresholdbitrate Vswsdhpthresholdbitrate
Defining AVC-Based Conference Profiles
Defining SVC and Mixed CP and SVC Conference Profiles
By default, the Conferencing Mode is set to CP
Defining SVC Conference Profiles
To define SVC Only Profile
New SVC Profile General Parameters Field/Option Description
New Profile Advanced dialog box opens
New SVC Profile Advanced Parameters Field/Option Description
Define the following supported parameters
New Profile Video Quality dialog box opens
Use this option when most of the endpoints support H.263
Click the Video Settings tab
Click the Audio Settings tab
Click the IVR tab
New SVC Profile IVR Parameters Field/Option Description
PCM
Polycom, Inc 106
Parameter Description
New SVC Profile Network Services Parameters
Defining Mixed CP and SVC Conferencing Profiles
To configure a mixed AVC and SVC conference
Polycom, Inc 109
Video Display with CIF, SD and HD Video Connections
Video Resolutions in AVC CP Conferencing
High Profile Guidelines
High Profile Support in CP Conferences
With Video Quality mode set to Motion
HD1080p60 Resolution Guidelines
CP Conferencing with H.263 4CIF
CP Resolution Decision Matrix
263 4CIF Guidelines
Qcif CIF
Video Resource Usage
Resource-Quality Balanced default
Resource Optimized
Video Quality Optimized
HD720p60
HD1080p30
HD720p30
CIF
Modifying the Resolution Configuration
Resolution Configuration for CP Conferences
Maximum Negotiated Line Rate for Resolutions
Guidelines
Resolution Configuration
Maximum CP Resolution Pane
Resolution Configuration Basic
Resolution Configuration Pane
Limiting Maximum Resolution
Sharpness and Motion
Resolution Configuration Detailed
Sharpness Resolution sliders Motion Resolution sliders
Resolution Configuration Sliders
Sharpness mode Motion mode
Polycom, Inc 122
Setting the Maximum CP Resolution for Conferencing
Flag Settings
Minimum Frame Rate Threshold for SD Resolution
Additional Video Resolutions
SIP
W448p Resolution
Content
Enabling Support of the w448p Resolution
Packet Loss Compensation
Isdn
Collaboration Server System Flag Settings
Additional Intermediate Video Resolutions
Content Control Protocols
Sharing Content During Conferences
Guidelines for Controlling Content
Supported Content Control Protocols
Guidelines for Using SIP Bfcp Content
Content Sharing Using H.239 Protocol
Content Sharing Using Bfcp Protocol
Dial-out System Flags
Content Sharing Using People+Content Protocol
Bfcp support in dial-in Connections
UDP and TCP
MPMRx MPMx Base profile High profile
Content Media Protocols
AVC non-TIP conferences Content RMX 1500/2000/4000 Profile
Highest Common
Content Transmission Methods
Content Video Switching
Fixed Rate
Multiple Content Resolutions
Highest Common Calculation Depending on Content Settings
Page
MCU Usage Modes of Content Protocols
Content Settings
Customized Content Rate
263 263 & H.264 Auto Selection Cascade Optimized 264 HD
263
Content Sharing Properties
263 & H.264 Auto Selection
Cascade Optimized
HD System Flags Content Settings Flag Name Range Default
Guidelines for Sharing Content Using H.264 HD
H264HDGRAPHICSMINCONTENTRATE
H264HDHIGHRESMINCONTENTRATE
Sending Content to Legacy Endpoints
Content Sharing Related Issues
Sharing Content in Cascaded Environments
Sending Content to Legacy Endpoints in Telepresence Mode
Guidelines for Sending Content to Legacy Endpoints
Content Display on Legacy Endpoints
Guidelines for Sharing Content in Exclusive Content Mode
Exclusive Content Mode
Managing Noisy Content Connections
Forcing Other Content Capabilities
Defining Content Sharing Parameters for a Conference
Useful Procedures in Content Sharing
To set the content sharing parameters
Content sharing Options Field Description
Non-TIP Conferences
Content sharing Options
Cascade Optimized Content Sharing
Content Settings list, select Customized Content Rate
Selecting a Customized Content Rate
To Select the Customized Content Rate
To enable Multiple Content Resolutions
Sharing Content in Multiple Content Resolutions Mode
To give token ownership
Giving and Canceling Token Ownership AVC Participants
Select Change To Content Token Owner in the drop-down menu
To end the current Content session
Stopping a Content Session
To cancel token ownership
Resolutions and Content Rate Reference Tables
Content Sharing Reference Tables
Content Rate Table
Settings
For RMX1800-0, maximum content resolution is HD1080p30
Resolution per Content Rate Tables
Highest Common Content Bit Rate for H.264 Base Profile
Highest Common Content Rates Tables
Highest Common Content Bit Rate for H.264 High Profile
Cascade Optimized Content Bit Rate for H.264 Base Profile
Cascade Optimized Fixed Content Rates Tables
Cascade Optimized Content Bit Rate for H.264 High Profile
Media Encryption Guidelines
Implementing Media Encryption for Secured Conferencing
Implementing Media Encryption for Secured Conferencing
Direct Connection to the Conference
Connection to the Entry Queue
Profile Setting
Media encryption is enabled at three levels
Enabling Media Encryption for a Conference
Recording Link Encryption
To enable encryption at the conference level
Setting the Encryption Flags
Enabling Encryption in the Profile
To modify the Encryption flags
Enabling Encryption at the Participant Level
Monitoring the Encryption Status
To enable encryption at the participant level
Polycom, Inc 163
Collaboration Server Telepresence Mode Guidelines
Setting Conferences for Telepresence Mode AVC CP
Participants using two RealPresence RPX HD 400 Room Systems
System Level
Horizontal Striping
Automatic Detection of Immersive Telepresence ITP Sites
Cropping
Gathering Phase with ITP Room Systems
Aspect ratio for standard endpoints
Skins and Frames
10+
Polycom, Inc 168
Telepresence Display Decision Matrix
Room Switch Telepresence Layouts
Polycom, Inc 170
Reserved Screens
Speaker Priority in CP Video Layouts
Grid Screens
Video Layout Examples
Polycom, Inc 172
Polycom, Inc 173
AVC endpoints only
Telepresence Mode License
Selecting Speaker Priority
Polycom, Inc 175
Enabling Telepresence Mode
Manual
Monitoring Ongoing Conferences
Monitoring Telepresence Mode
None
Monitoring Participant Properties
Polycom, Inc 180
Enabling and Using Multiple Cascade Links
RMX Telepresence Layout Mode Room Switch
RMX Telepresence Layout Mode Continuous Presence figure
Creating a Link Participant
RMX Telepresence Layout Mode Continuous Presence
Link Participant in the Dial Out RMX
For more information see
To create a Link Participant in the dial-out RMX
An Undefined Participant Link
Participant Link in the Dial In RMX
Defined Participant Link
Monitoring Multiple Cascade Links
Disconnection Causes
Polycom, Inc 187
Video Preview Guidelines
Additional Conferencing Information
Video Preview
Workstation Requirements to Display Video Preview
Testing your Workstation
To preview the participant video
DirectX Diagnostic Tool dialog box opens
Previewing the Participant Video
Additional Conferencing Information
To enable Auto Scan
Guidelines for Using Auto Scan and Customized Polling
Auto Scan and Customized Polling in Video Layout
Enabling the Auto Scan and Customized Polling
Customized Polling dialog box is displayed
Customized Polling
To define the scanning order in the Customized Polling tab
Customized Polling Dialog Box Command Buttons Description
Packet Loss
Lost Packet Recovery
Packet Loss Compensation LPR and DBA
Enabling Lost Packet Recovery
Monitoring Lost Packet Recovery
Polycom, Inc 198
Network Quality Levels
Layout Indications
Network Quality Indication
Displaying the Network Quality icons
Indication Threshold Values
Customizing the Network Quality Icon Display
Network Quality Icon Indication Threshold Flags Description
Default no
Disable the display of the Network Quality icon
Disable the display of Network Quality icons displayed
Default YES
Audio Participants Indication
Recording Indications
Recording
Recording Paused
Layout Indications Icon Display Positions
Polycom, Inc 204
Selecting the Conference Lecturer
Lecture Mode
Enabling Lecture Mode
To automatically select the lecturer
To automatically select a defined participant
Enabling the Automatic Switching
Lecture Mode Monitoring
To control the Lecture Mode during an Ongoing Conference
When enabled, the following rules apply
Restricting Content Broadcast to Lecturer
Muting Participants Except the Lecturer
Enabling the Mute Participants Except Lecturer Option
SIP Encryption
Audio Algorithm Support
Audio Algorithm Support Guidelines
Mono
Supported Audio Algorithm vs Bitrate Minimum Bitrate kbps
Audio algorithms supported for Isdn
Stereo
722.1 16K 722 48K 722 56K 722 64K
To view the participant’s properties during a conference
Monitoring Participant Audio Properties
Guidelines for Automatically Muting Noisy Endpoints
Automatic Muting of Noisy Endpoints
YES
Automatic Muting of Noisy Endpoints
Automatic Muting of Noisy Endpoints at the Conference Level
Automatic Muting of Noisy Endpoints at the MCU Level
To modify the system flag setting
Permanent Conference
Enabling a Permanent Conference
Closed Captions Guidelines
Closed Captions
To change the flag value
New Flag field enter Enableclosedcaption
Enabling Closed Captions
Cascading Link Properties
Setting the Video Layout in Cascading conferences
Defining Cascading Conferences
Defining Cascading Conferences
Flags Controlling Cascading Layouts
Dtmf Forwarding
Play Tone Upon Cascading Link Connection
Basic Cascading
Possible Cascading Topologies
Dialing Directly to a Conference
Basic Cascading Using IP Cascaded Link
Dialing to an Entry Queue
Basic Cascading Topology IP Cascading Link
Automatic Identification of the Cascading Link
Basic Cascading Using Isdn Cascaded Link
Gateway to Gateway Topology
Gateway to MCU/ MCU to Gateway Topology
MCU to MCU
Cascading Between Two MCUs Using an Isdn Link
Gateway to Gateway Calls via Isdn Cascading Link
For example
Gateway to MCU Calls via Isdn Cascading Link
MCU to MCU Calls via Isdn Cascading Link
Polycom, Inc 234
LPR
Conference Profile Definition
MCU Interoperability Table
Defining Cascading Conferences
Suppression of Dtmf Forwarding
System Flag Settings
Command box, enter H239OlcPatch
Master-Slave Cascading
Star Cascading Topology
Master-Slave Star Cascading Topology
MGC VSW HD
To define the dial-out cascade participant link
Conferences pane, select the conference
New Participant Dial-out Cascade Link Field Description
New Participant Dial-out Cascade Link
Enablecascadedlinktojoinwithoutpassword flag to YES
New Participant Dial-in Cascade Link Field Description
To define a Dial-in Participant as the cascade link
If a gatekeeper is not used Select E.164 digits 0-9, *, #
If a gatekeeper is used This field is left empty
If a gatekeeper is used H.323 ID
Cascaded Conferences Star Topology
Cascading via Entry Queue
Enabling Cascading
To Define a Cascade-Enabled Entry Queue
Creating the Cascade-enabled Entry Queue
To define the Dial-out Cascaded Link
Creating the Dial-out Cascaded Link
Click OK New Entry Queue enabling cascading is created
Name field, enter a participant name
Method B
Method a
To enable cascaded links to connect without a password
Enabling Cascaded Conferences without Password
Set the Enablecascadedlinktojoinwithoutpassword flag to YES
Monitoring Star Cascaded Conferences
Polycom, Inc 251
Advanced tab, in the Node Type field, select MCU Click OK
Cascading Conferences H.239-enabled MIH Topology
Cascading Topologies
MIH Cascade a Sample 3-Level Cascading Configuration
MIH Cascading Levels
MIH Cascade Levels
MIH Cascading Guidelines in CP Licensing
Master Slave Conferences
MIH Cascading Master-Slave Relationship
Video Session Mode, Line Rate and Video Settings
RMX
RMX CP HD
RMX CP CIF
RMX VSW HD
Method
MGC to RealPresence Collaboration Server Cascading
Method
H263ANNEXT=YES default
Setting Flags on the RealPresence Collaboration Server
FORCE1X1LAYOUTONCASCADEDLINKCONNECTION=YES default
To modify the flags
To define the Cascading Entry Queue in the MGC
Setting Flags in the MGC
Method II Defining the Cascading Entry Queue in the MGC
Polycom, Inc 261
For Example 1002##12001##1234
Polycom, Inc 263
HD VSW
Defining the Cascading Conferences
MGC HD VSW
To define the Dial-out Participant
Polycom, Inc 266
Polycom, Inc 267
Meeting Rooms
Meeting Rooms List
Use Time Out as Dtmf Delimiter
Meeting Rooms are listed in the Meeting Room list pane
Value / Description Flag Name
Meeting Rooms List Columns Field Description
To list Meeting Rooms
Use Time Out as Dtmf Delimiter
Automatic Password Generation Flags
Meeting Room Toolbar & Right-click Menu
To create a new meeting room
Creating a New Meeting Room
Meeting Rooms pane, click the New Meeting Room
Button or right-click an empty area
Entry Queues
Entry Queues, Ad Hoc Conferences and SIP Factories
Defining a New Entry Queue
Default Entry Queue properties
Default Entry Queue Properties Parameter Value
To define a new Entry Queue
Entry Queue Definitions Parameters Option Description
Shared Number Dialing
Modifying the EQ Properties
Listing Entry Queues
Transit Entry Queue
To view the list of Entry Queues
To cancel the Transit Entry Queue setting
Setting a Transit Entry Queue
To designate an Entry Queue as Transit Entry Queue
RMX Management pane, Rarely Used list, click Entry Queues
Configuring the Collaboration Server as IVR Provider
Guidelines for setting the Entry Queue as IVR Provider
Entry Queue IVR Service
IVR Provider Entry Queue Shared Number Dialing
Entry Queue
Using External IVR Services via the MCCF-IVR Package
Call Flow for Standalone TIP Endpoints
Call Flows
Call Flow for Standalone SIP Endpoints
Call Flow for TIP Endpoints from a Polycom ITP System
RMX Management pane, click Entry Queues
Configuring the Entry Queue to Use External IVR Services
To configure the Entry Queue for External IVR Services
Creating SIP Factories
SIP Factories
To create a new SIP Factory
RMX Management pane, Rarely Used list, click SIP Factories
New Factory Properties Option Description
Click OK New SIP Factory is added to the list
Monitoring Registration Status
Ad Hoc Conferencing
Gateway to Polycom Distributed Media Application DMA
Address Book
Viewing the Address Book
To expand the group to view the group members
Participants List Pane Information
To collapse a group
» Double-click the group name or click the Collapse button
Displaying and Hiding the Address Book
Adding Participants from the Address Book
Adding a Group from the Address Book to Conferences
Participant Groups
Managing Groups in the Address Book
To add a group to a new conference or an ongoing conference
Address Book Navigation Action Description
Select one of the following actions
Adding a Participant to the Address Book
Managing the Address Book
Adding a New participant to the Address Book Directly
To add a new participant to the Address Book
New Participant General Field Description
Only
New Participant General
IP only
SIP Only
New Participant Advanced Field Description
Dial-out SIP Only
AGC
Guidelines for Substituting E.164 Number in Dial String
Substituting E.164 Number in Dial String
To modify participant properties in the Address Book
When required, you can modify the participant’s properties
Modifying Participants in the Address Book
To delete participants from the Address Book
Deleting Participants from the Address Book
Copy / Move Participant Function Description
Copying or Moving a Participant
To copy or move a participant to another group
Paste Participant Function Description
Searching the Address Book
Filtering the Address Book
To filter the data in an address book group
Filtering Address Book Data Using a Predefined Pattern
Filtering Address Book Data Using a Custom Pattern
Polycom, Inc 310
To clear the filter and display all entries
Clearing the Filter
Obtaining the Display Name from the Address Book
Exporting an Address Book
Importing and Exporting Address Books
Importing an Address Book
To Export an Address Book
Integration with Resource Manager
Upgrading and Downgrading Considerations
RealPresence Collaboration Server Side
Guidelines for Scheduling Reservations
Scheduling Reservations
System
Resources
Reservations
Toolbar Buttons
Using the Reservation Calendar
To open the Reservation Calendar
RMX Management pane, click the Reservation Calendar button
Week View
Reservations Views
Day View
Single day is displayed
List View
Today View
To change between Week and Day views
Changing the Calendar View
To change to List View
To view Today the current date
Creating a New Reservation
Scheduling Conferences Using the Reservation Calendar
To return to Calendar View
Method III To interactively define the duration
Select a starting time slot
To create a new reservation
Open the Reservation Calendar
New Reservation Reserved Resources Field Description
All Reservations
New Reservation Schedule Tab Field Description
Recur every weeks field
You can add participants from the Participants Address Book
Viewing and Modifying Reservations
Using the Week and Day views of the Reservations Calendar
Managing Reservations
To change the Reservation’s Start time
To move the Reservation to another time slot
To change the Reservation’s End time
Reservation Properties General dialog box opens
Adjusting the Start Times of all Reservations
Scheduling Reservations
Deleting Reservations
Searching for Reservations using Quick Search
To delete a single reservation
To delete all recurrences of a reservation
Clear the Quick Search field
To clear the search and display all reservations
Click Search
All Reservations are displayed
Operator Conferences
Operator Assistance & Participant Move
Defining the Components Enabling Operator Assistance
Operator Conference Guidelines
New Conference IVR Service General dialog box opens
New Conference IVR Service Welcome dialog box opens
New Conference IVR Service Dtmf Codes dialog box opens
Click the Video Services tab
Click the Operator Assistance tab
New Entry Queue IVR Service Welcome dialog box opens
New Entry Queue IVR Service Conference ID dialog box opens
To define a Conference Profile for an Operator Conference
Click the Operator Conference check box
To start a conference from the Conference pane
Starting an Ongoing Operator Conference
New Conference General Options Field Description
Routing Name
New Conference General Options
To save an ongoing Operator conference as a template
Saving an Operator Conference to a Template
Click the Participants tab
New Conference Participants dialog box opens
Starting an Operator Conference from a Template
Requesting Help
Participant Alerts List
Using Audible Alarms
Audible Alarms
Conference Templates
Conference Templates Toolbar Buttons Description
Using Conference Templates
Conference Template toolbar includes the following buttons
Creating a new Conference Template from Scratch
Creating a New Conference Template
To create a new Conference Template
Conferences List toolbar includes the following button
Conference Templates
Polycom, Inc 354
New Participant General dialog box opens
Click the New button
New Participant Advanced dialog box opens
Specify the Display Name and Duration
New Conference Template Information dialog box opens
To start an ongoing conference from a Template
Starting an Ongoing Conference From a Template
Conference is started
To schedule a Reservation from a Conference Template
Scheduling a Reservation From a Conference Template
Polycom, Inc 362
Exporting and Importing Conference Templates
Deleting a Conference Template
To delete Conference Templates
Click the Delete Conference Template button. or
To export all Conference Templates from an MCU
Exporting Conference Templates
Exporting All Conference Templates from an MCU
To export selected Conference Templates
Exporting Selected Conference Templates
Conference Templates Import dialog box is displayed
Importing Conference Templates
To import Conference Templates
Polycom, Inc 367
Polycom, Inc 368
Start a Conference
To start an AVC CP conference from the Conference pane
Start an AVC CP Conference from the Conferences Pane
General Tab
Support
New Conference General tab parameters Field Description
System Configuration Flags
Polycom, Inc 374
New Conference Participants Tab Column / Button Description
Participants Tab
Option is disabled in SVC conferences
All Participants list opens
Information Tab
To add participants from the Address Book
New Conference Information Tab Field Description
Media Sources Tab
To start a SVC conference from the Conference pane
To start a conference from the Reservation Calendar
Scheduling an AVC-based Reservation
Starting an Ongoing Conference From a Template
This section is applicable for CP-AVC only conferences
Conference Operations
Conference and Participant Level Operations
Copy Conference
Paste Conference
To paste a conference as a new conference
Paste Conference As
Operational Buttons
Participant Operations
Participant Level Operations Menu Option Button Description
Resume Video button
Change to Regular
Copy Participant
Copy, Cut and Paste Participant
Cut Participant
Paste Participant
Paste Participant As
Move Guidelines
Moving Participants Between Conferences
Moving a Participant Interactively
Moving Participants Options
Polycom Conferencing for Microsoft Outlook
Setting up the Calendaring Solution
Option 1 Using default Exchange Server settings
Exchange Integration Configuration Option Field Description
Option 2 Using an alternate Primary Smtp Mailbox
Exchange Integration Configuration Option
Option 3 Using modified Exchange Server settings
Calendaring Guidelines
Polycom, Inc 398
Creating a Conference
Creating and Connecting to a Conference
RealPresence Capture Server or
Connecting to a Conference
Collaboration Server Standalone Deployment
Polycom Solution Support
General Monitoring
Conference and Participant Monitoring
Multi-Selection
Using the Chairperson Password for Filtering
Conference Level Monitoring
To search for an ongoing conference by Chairperson Password
Click in the Chairperson Password field
Mixed
Monitoring the Conference in the Conference List Pane
Conferences Monitoring Information FieldDescription
Displays conference name and type of conference
To view the parameters of an ongoing CP conference
Conference Properties General Field Description
Following information is displayed in the General tab
SVC
Conference Properties General
Following information is displayed in the Advanced tab
Conference Properties Advanced dialog box opens
Conference Properties Advanced Parameters
End When Last Participant Remains parameters apply
None
Prefer TIP
Following information is displayed
Profile Gathering Settings Field/Options Description
Conference Properties Video Quality dialog box opens
Information, see Video Resolutions in AVC CP Conferencing
Customized Content Rate
Click the Video Settings tab to list the video parameters
Conference Properties Video Quality Parameters
AS-SIP
For more information, see Supplemental Conferencing Features
See Defining New
Customized Polling Buttons Description
Polycom, Inc 418
Conference Properties General Parameters Field Description
Viewing the Properties of Ongoing SVC Conferences
To view the parameters of an ongoing SVC conference
Conference Properties General Parameters
Last Participant Remains parameters apply
Server RMX Network Port Usage
Content Rate
Polycom, Inc 424
Requesting Help
Request to Speak is
Request to Speak
SDP
Participant Level Monitoring
Gatekeeper Status Call Admission Control
Participant’s connection no indication is displayed
Column Icon/Description
Participant Monitoring Indicators and Properties
Polycom, Inc 431
To view the participant Properties
Viewing the Properties of Participants
Following parameters are displayed for an IP participant
Monitoring IP Participants
Mute/Suspend
Conference. See Conference and Participant Monitoring
Polycom, Inc 436
Conference and Participant Monitoring Polycom, Inc 437
Milliseconds derived from the Rtcp report
From the endpoint
SIP Bfcp TCP
Participant Connections
Participant Properties Channel Status Advanced Parameters
Conference and Participant Monitoring
Conference and Participant Monitoring
Channel Status tab Channel Status Advanced tab
Monitoring SIP Bfcp Content
Default
Configuring the System Flag
Detecting Endpoint Disconnection
Detecting SIP Endpoint Disconnection
Endpoint Disconnection Detection
System Configuration Flag
Monitoring ISDN/PSTN Participants
Algorithm
To view the participant properties during a conference
Participant Properties H.221 Parameters Field Description
Causes
Polycom, Inc 451
ISDN/PSTN Participant Properties Channel Status
Monitoring Telepresence Participant Properties
Recording and Streaming Conferences
Configuring the Collaboration Server to Enable Recording
Defining the Dial Out Recording Link
Default Recording Link
To define a Dial Out Recording Link
Recording Link Parameters Description
Conference IVR Service Properties dialog box is displayed
Enabling the Recording Features in a Conference IVR Service
RealPresenceCaptureServerorRSS4000system IPAddress
Recording Link Parameters ParameterDescription
Enabling the Recording in the Conference Profile
Conference Profile Recording Parameters Description
To enable recording for a conference
Click OK Recording is enabled in the Conference Profile
Dial Out Recording Link Encryption Flag Setting
Dial Out Recording Link Encryption
Dial Out Recording Link Encryption Guidelines
Managing the Recording Process
Dial Out Recording Link Settings
Recording Layout
To manage the recording process using the right-click menu
Recording Participant Right-click Options Name Description
Server or RSS 4000 system User Guide
Monitoring the recording participant
Using Dtmf Codes to Manage the Recording Process
Conference Recording with Codian IP VCR
Users, Connections, and Notes
Administrator
Collaboration Server Users
User Types
Listing Users
Adding a New User
Administrators can add new users to the system
To add a new user to the system
RMX Management pane, click Users Users pane is displayed
To associate a user with a machine
Deleting a User
To change a user’s password
Changing a User’s Password
To disable a user
Disabling a User
Renaming a User
To enable a user
Machine Account
To rename a user
Active Directory
Guidelines for defining a machine account
Monitoring
Connections
Using Notes
Viewing the Connections List
To list the users who are currently connected to the MCU
To delete a note
To create a note
To open or edit a note
Collaboration Server IP Network Services Overview
IP Network Services
Management Network Primary
Default IP Service Conferencing Service
IPv6 Addressing Guidelines
Modifying the Management Network
To view or modify the Management Network Service
RMX Management pane, click the IP Network Services button
Management Network Properties Collaboration Server RMX
Default Management Network Service IP Field Description
Modify the following fields
Auto If selected, Site-Local and Global
Click the Routers tab
Default Management Network Service Routers Field Description
Click the DNS tab Modify the following fields
Default Management Network Service DNS Field Description
DNS
DNS Servers Addresses
Revocation Method
Click the Security tab Modify the following fields
URL
To view or modify the Default IP Service
Modifying the Default IP Network Service
RMX Management pane, click IP Network Services
Default IP Service Collaboration Servers RMX 1500/2000/4000
Default IP Network Service IP Field Description
Default IP Service Collaboration Server RMX
4000
2000/4000
Polycom, Inc 489
Optional. Click the DNS tab
IP Network Services
Aliases
To view or modify the ports values, click the Ports tab
Fixed Ports
If required, click the QoS tab
System.cfg file
View or modify the following fields
TOS
Click the SIP Servers tab
SIP Servers Primary / Alternate Server Parameter
Default IP Network Service SIP Servers Field Description
Outbound Proxy Servers Primary / Alternate Server Parameter
Username@domain name
Modify the following fields
To configure the ICE environment, click the SIP Advanced tab
Network Service V35 tab Field Description
Default IP Network Service SIP Advanced Field Description
LAN
Ethernet Settings
MNG B LAN
MNG LAN
To modify the automatic LAN port configuration
RealPresence Collaboration Server RMX 1500/4000
RealPresence Collaboration Server RMX 1500 Do not select
Ethernet Settings Parameters Field Description
RealPresence Collaboration Server RMX 4000 Do not select
RMX CS IP tab displays the following fields
To monitor signaling status
IP Network Monitoring
IP Network Services
Click the H.323 tab H.323 tab displays the following fields
IP Network Services
IP Network Services
IP Network Services
Media Redundancy on RealPresence Collaboration Server RMX
LAN Redundancy
Media Redundancy
Multipleservices = YES Lanredundancy
Multipleservices = no Lanredundancy
Multipleservices = no
Multipleservices = YES
Multipleservices = no Lanredundancy = YES
Signaling and Management Redundancy
LAN Connections to the IP ports IP Port Description
RMX 1800 Media Redundancy System Flags System Flag / Value
= no Management Signaling
LAN
Hardware Monitor Indications
Configuration Requirements
RealPresence Collaboration Server RMX
RealPresence Collaboration Server
RTM LAN Indications Status Description
Network Traffic Control
Http TCP
RealPresence Collaboration Server RMX Network Port Usage
Https
DNS UDP
UDP, TCP
SSH TCP
NTP
RTP
SIP-TLS
Rtcp
SIP -TLS
ISDN/PSTN Network Services Overview
Defining ISDN/PSTN Network Services
Non Supported Capabilities and Conferencing Features
Supported Capabilities and Conferencing Features
To Add an ISDN/PSTN Network Service
Adding/Modifying ISDN/PSTN Network Services
RMX Management pane, click ISDN/PSTN Network Services
Obtaining ISDN/PSTN required information
Isdn Service Settings Field Description
Unknown
Span Definition Field Description
Configured symmetrically
Click Save & Continue
Phones Settings Field Description
Click Save & Close
Modifying an ISDN/PSTN Network Service
To Modify an ISDN/PSTN Network Service
MCU CLI
Dial-in Phone Numbers
Network Security
Multiple Network Services
RealPresence Collaboration Server RMX 1500/4000
RealPresence Collaboration Server
Network Security
Polycom, Inc 534
That Include ICE
Cards Up to 2 per Media Card Services
Resource Allocation and Capacity
First Time Installation and Configuration
Upgrading to Multiple Services
RealPresence Collaboration Server RMX Hardware Installation
Polycom, Inc 539
Connecting the cables to the RTM LAN
Connecting the cables to the RTM IP
LAN Connections to the RTM IP RTM IP Port Description
LAN Connections to the RTM LAN RTM LAN Port Description
Polycom, Inc 541
LAN Connections to the RTM LAN RTM IP Port Description
Management, media and signaling for Network Service
MNG MNG B
Collaboration Server Configuration
System Flags and License Settings
IP Network Service Definition
Device Management pane, click IP Network Services
To add new/additional Network Services
Polycom, Inc 547
IP Network Service IP Parameters Field Description
IP Network Service IP Parameters
Following flags can be defined per service
Service Configuration dialog box opens
H263ANNEXT
Defined and the IP Network Service
Default IP Network Service SIP Advanced FieldDescription
Default IP Network Service Icons IconDescription
Setting a Network Service as Default
Ethernet Settings
Conference Profile
Signaling Host IP Address and MCU Prefix in GK Indications
Video/Voice Port and Resolution Configuration
Gateway Profiles
Hardware Monitor
Signaling Monitor
Conferencing
Defining Dial Out Participants
Reserving Video Resources for a Conference
Monitoring Conferences
Resource Report
Port Usage Gauges
NAT Network Address Translation Traversal
Remote Connection Using the Internet
Deployment Architectures
Following Remote Connection call flow options are supported
Remote Connections Enterprise Client Environment Registered
Business to Business Connections
Registered Environment
VBP
FW Firewall NAT Keep Alive
To enable and modify FW NAT Keep Alive
SIP TCP Keep-Alive
System Configuration in SBC environments
To view the IVR Services list
IVR Services
IVR Services List
IVR Toolbar buttons Button Button Name Descriptions
IVR Services Toolbar
To add a language
Adding Languages
To upload messages to the MCU
Uploading a Message File to the Collaboration Server
Properties General Voice Messages
IVR Message Types by Message Category
To define a new Conference IVR Service
Defining a New Conference IVR Service
Defining a New Conference IVR Service
Default is
Conference IVR Service Properties Global Parameters
Polycom, Inc 574
Chairperson Identifier
Polycom, Inc 576
Message Type Description
Conference IVR Service Properties General Voice Messages
Indicating the recording status of the conference
Followed by the Reorder Tone and disconnection
Polycom, Inc 580
Ivrrollcallusetonesinsteadofvoice is set to YES ,
Ivrrollcallusetonesinsteadofvoice is set to YES,
IVR Services
Polycom, Inc 583
Low
4SIF
SIF
Dtmf
Video Services Description
New Conference IVR Service Dtmf Codes dialog box opens
IVR Services
IVR Services
Change to Chairperson
Defining a New Entry Queue IVR Service
Entry Queue IVR Service
To set up a new Entry Queue IVR Service
RMX Management pane, click IVR Services
Fill in the following parameters
Ad Hoc Conferencing and External Database Authentication
Polycom, Inc 592
Select the voice messages
New Entry Queue IVR Service General dialog box opens
IVR Services
Polycom, Inc 596
Default Conference IVR Service
To select the default Conference IVR Service
To modify the properties of an IVR Service
To select the Default Entry Queue IVR Service
To replace the Music file
Replacing the Music File
Adding a Music File
To define the format settings for audio messages
Defining the format settings for audio messages
Creating Audio Prompts and Video Slides
Recording an Audio Message
Attributes list, select 16.000 kHz, 16Bit, Mono
Click Convert Now
Sound Selection dialog box opens Format field, select PCM
To record a new audio message
Recording a new audio message
IVR Services
To create a welcome video slide
Creating a Welcome Video Slide
Error Handling
Inviting Participants using Dtmf
Invite Call Flow
Entering Additional Dtmf Codes
General Video Services Dtmf Codes
Enabling the Invite Participants using Dtmf Option
Conference IVR Services dialog boxes
Conference IVR Services General tab is displayed
Disabled set to Off
Disabling the Invite Participant Option
To disable the Invite Participant option
Guidelines for TIP Support with IVR Services
External IVR Service Control
IVR Services Support with TIP Protocol
Default IVR Prompts and Messages
Change
Password IVR
Requests Chairperson help Menu
IVR Services
Default IVR Messages Flag Description
Volume Control of IVR Messages, Roll Call and Music
To control the volume of IVR music, Roll Call and messages
IVR Services in TIP-Enabled Conferences Guidelines
IVR Services in TIP-Enabled Conferences
Entry Queue and Virtual Entry Queue Access
Configuring the Conference and Entry Queue IVR Services
CDR File Properties
Call Detail Record CDR Utility
CDR File Formats
Unformatted CDR File
Formatted CDR File
Multi-Part CDR Files
CDR File Contents
Viewing the Conference Records
Viewing, Retrieving and Archiving Conference Information
To open the CDR utility
Conference Record Fields Description
Multi-part CDR File display
Retrieving and Archiving Conference CDR Records
Refreshing the CDR List
To refresh the CDR list
To retrieve and archive CDR records
Gateway Functionality
Gateway Calls
Direct Dialing
Call Flows
IP Participants
Dialing from H.323 Endpoints
Dialing from SIP Endpoints
Optional
Gateway IVR Dialing For IP Participants
Dial-out Calls
Direct Dialing Using IP Addresses
Dial-in Calls
Enabling or Disabling Direct IP Dialing
Calling a SIP Endpoint in a Remote Domain
Dialing via Gateway IVR for Isdn Participants
Isdn Participants
Dialing from ISDN/PSTN Endpoints
Two dialing methods are available to ISDN/PSTN participants
Calling an IP Endpoint via Gateway
Pstn Dial-in Using GK Prefix
Interoperability with DMA
To define a new Conference IVR Service for gateway calls
Defining the IVR Service for Gateway Calls
Roll Call disabled
Operator Assistance disabled
Gateway Calls
Details, see Disconnect on Busy
DefaultGWWelcomeSlide
To define a Conference Profile for Gateway Sessions
Define the required settings for Encryption and LPR
Defining the Conference Profile for Gateway Calls
To define a new Gateway Profile
Defining the Gateway Profile
Gateway Calls Redialing
System Configuration
Call Failure Reasons H.323, SIP, Isdn
Wrong Destination Number
Wrong Destination Number Time-out
Connection Indications
Monitoring Ongoing Gateway Sessions
Disconnect on Busy
Disconnect on No Answer
Conference ID
Gateway Session Parameters
Gateway Session Name
Connected Participant Parameters
To set up the Meeting Room for direct dialing
Polycom, Inc 645
Example
Dialing to Polycom RealPresence DMA System
Manual Dial String Entry
Calling the RealPresence DMA via Gateway IVR
Automatic Dial String Generation
Enabling Pstn dial-in using GK prefix
Pstn Dial-in Using GK Prefix
Configuration
Pstn Participant input via Dtmf
Deploying a Polycom RMX Serial Gateway S4GW
RMX Manager Application
Installing the RMX Manager Application
Accessing or Downloading the RMX Manager Installer
Click Install
Downloading the Installation files from Polycom Support Site
Click the Install RMX Manager link
Installing the RMX Manager on Your Workstation
Accessing the RMX Manager Installer from the Login screen
Polycom, Inc 655
To install the RMX Manager for Multiple Users
Installing the RMX Manager for Multi-User Capability
Polycom, Inc 657
Starting the RMX Manager Application
To use the Windows Start menu
To use the browser
Click Start Programs
Click All Programs Polycom RMX Manager
To connect the RMX Manager to an MCU
Connecting to the MCU
MCUs pane includes a list of MCUs and a toolbar
RMX Manager Main Screen
MCUs Pane
MCU Icons and Statuses Icon Description
To add a Collaboration Server unit
Adding MCUs to the MCUs List
Use Other RMX Manager UI Components
MCU IP
MCU Properties Field Description
Grouping the Participants by MCU
Start Monitoring/Stop Monitoring
Removing an MCU from the MCUs Pane
Disconnecting an MCU
Modifying the MCU Properties
To select a language
Import/Export RMX Manager Configuration
Changing the RMX Manager Language
To Import the RMX Manager Configuration
To Export the RMX Manager Configuration
Export RMX Manager Configuration dialog box opens
Import RMX Manager Configuration dialog box opens
To install the RMX Manager
Installing RMX Manager in Secure Communication Mode
Clear the Secured Communication check box Click the DNS tab
Click on the Security tab Security dialog box is displayed
DNS dialog box is displayed
Enter the Local Domain Name
Create a Certificate Request
Select the Secured Communication check box
Management Network Properties dialog box is displayed
Click the Security tab Security dialog box is displayed
RMX Management pane, click Hardware Monitor
Using an Internal Certificate Authority
Click OK Reset the Collaboration Server
Certificate Export Wizard is displayed
Click the Copy to File button
Click Next Export File Format dialog box is displayed
Select Base-64 encoded X.509 .CER
Polycom, Inc 676
Starting the RMX Web Client
Use the RMX Web Client
To start the Collaboration Server Web Client
Viewing and System Functionality Permissions
RMX Web Client Screen Components
Auditor
If you are logged in as a User with Chairperson permissions
Conferences List
Status Bar
List Pane
RMX Management Pane
Participant Alerts
System Alerts
Port Usage Gauges
Address Book
MCU State
Dialing Direction Dial-in or Dial-out
Displaying and Hiding the Address Book
Displaying and Hiding Conference Templates
Conference Templates
Customizing the Main Screen
To adjust column width
To resize a pane
To sort the data by any field column heading
Increasing and Decreasing the Text Size
To switch between Toolbar and List Views
Customizing the RMX Management Pane
To increase or decrease the text size
Polycom, Inc 690
Collaboration Server 1500/1800/2000/4000 Status Bar
Administration and Utilities
System and Participant Alerts
To view the System Alerts list
System Alerts
Active Alarms Pane Columns
Error occurred
An identifying number assigned to the system alert
System Alerts Buttons
To view the Participants Alerts list
Participant Alerts
Altering the clock
RMX Time
To Alter the MCU Time
RMX Time Fields Properties Description
RMX Time Fields Properties
Resource Capacity
Resource Management
MPMx MPMRx-D
Resource Usage in AVC CP Conferencing
Resource Usage in SVC Conferencing
MCU Capacities in Mixed CP and SVC Conferencing
Audio
Mode
Resource Usage in Mixed CP and SVC Conferencing
AVC Conferencing Video Switching Resource Capacity
MPMRx 3333 Mixed CP
MPMx Mixed CP
AVC Conferencing Voice
Resource Usage in AVC CP Conferencing
Resource Capacity Modes
MPMx MPMRx
Flexible Resource Capacity Mode
Video/Voice Port Configuration MPMRx
Video/Voice Port Configuration MPMx
To allocate Voice resources
Configuring the Video/Voice Resources
Forcing Video Resource Allocation to CIF Resolution
Resource Reports
To cancel the forcing of CIF resource
To force CIF resource
Mcmsparameters tab, click New Flag
Resource Report Fields Parameters Column Description
Main toolbar, select Administration Resource Report
Displaying the Resource Report
Port Gauges
Port Gauge
AVC HD AVC SD AVC CIF SVC
Collaboration Server 1800 Resource Capacity
AVC HD AVC SD AVC CIF
Port consumption ratios of different calls HD720p HD1080p
Resource Capacity in Non-Mixed Conferences
Resource Capacity in Mixed Conferences
Collaboration Server 2000/4000 Resource Capacity
ISDN/PSTN
Polycom, Inc 711
To Set the Port Usage Threshold
Setting the Port Usage Threshold
Port Usage Threshold
SIP Dial-in Busy Notification
Port Usage Gauges
Polycom, Inc 715
System Information FieldDescription
System Information
To view the System Information properties box
MIBs Management Information Base
Snmp Simple Network Management Protocol
Traps
MIB Files
Support for MIB-II Sections
Alarm-MIB
MIB H.341 H.323
Standard MIBs
Unified MIB Snmp Fields Name Type Description
Unified MIB
Code
An Example of a ColdStart Trap
An Example of an Authentication Failure Trap
An Example of an Alarm Fault Trap
RMX MIB entities that do not generate traps
Status Trap
Administration and Utilities
Defining the Snmp Parameters in the Collaboration Server
To enable Snmp option
Snmp Properties Traps dialog box opens
Select the Traps tab
SHA
SNMPv3 Traps Field Description
Snmp
SNMPv3 Traps Field Description Version
Authentication Password
Snmp Properties Security dialog box opens
Select the Security tab
Default MD5 Authentication
Default Empty
Enter an Authentication Password
Default DES
Snmp Properties Security dialog box, click OK
Using Audible Alarms
Accepted Host IP Address dialog box opens
Audible Alarm Permissions
Configuring the Audible Alarms
Audible Alarm Permissions Option Operator Administrator
Stop Repeating Message
Audible Alarm User Customization Options Description
Replacing the Audible Alarm File
Download Audible Alarm File window opens
Multilingual Setting
Customizing the Multilingual Setting
Banner Display and Customization
To customize the Multilingual Setting
Sample 1 Banner
Non-Modifiable Banner Text
Sample 4 Banner
Sample 2 Banner
Sample 3 Banner
Customizing Banners
Banners Configuration dialog box opens
To customize the banners
Customize the banners by modifying the following fields
Banner Display
Login Screen Banner
Main Screen Banner
Software Management
Backup and Restore Guidelines
To backup configuration files
Using Software Management
To restore configuration files
Select the Backup Directory Path and then click Backup
Ping the Collaboration Server
Using Ping
To Ping a network entity from the Collaboration Server
OK or
Notification Settings Parameters Field Description
Notification Settings
To configure the notifications
Following tasks can be performed
Logger Diagnostic Files
To access the Logger Diagnostic Files
To Retrieve the Logger Files
Logger Diagnostic Files dialog box, click Browse
Diagnostic File Button Options Description
Information Collector
Standard Security Mode
To View the Logger Files
Click Retrieve Files
Network Intrusion Detection System Nids
Ultra Secure Mode
To create the compressed file
Using the Information Collector
Creating the Information Collector Compressed File
Click Collect Information
Saving the Compressed File
Auditor Files
Auditor
Viewing the Compressed File
To view the compressed file
Name
To access Auditor Files
Retrieving Auditor Files
To retrieve files for storage on a workstation
Auditor File Viewer
To open the file in the Auditor File Viewer
StartUp
To open the Auditor File Viewer from the Administration Menu
Auditor Event Columns Field Description
Alerts and Faults that are recorded by the Auditor
Alerts and Faults
Alerts and Faults recorded by the Auditor Event
Audit Events
Alerts and Faults recorded by the Auditor Event
Transactions recorded by the Auditor
Transactions
Transactions that are recorded by the Auditor
ActiveX Bypass
Installing ActiveX
Click Reset
Resetting the Collaboration Server
To reset the RMX
Administration and Utilities
To modify system flags
System Configuration Flags
Modifying System Flags
Mcmsparametersuser Flags Description
Manually Added and Deleted System Flags
RealPresence Capture Server or RSS 4000 system recorder
Disableinactiveuser
Contentspeakerintrasup
Enableacceptingicmpredi
Enableagc
Enablecascadedlinktoj
Enableautoextension
Oinwithoutpassword
Enablecyclicfilesystem
Olume
Forcesystembroadcastv
Forcesystemlisteningvo
Lume
Isdnresourcepolicy
Fillfromfirstconfiguredspan
Fillfromlastconfiguredspan
Itpcropping
Legacyepcontentdefault
Lastloginattempts
Maxconfpasswordrepeat
Layout
Maxpasswordrepeapedc
Maxcpresolution
Maxpasswordrepeatedch
Maxintrarequestsperin
Multipleservices
Minpasswordlength
Mcudisplayname
Minpwdchangefrequenc
Numofspecialchar
Numofnumeric
Numofuppercasealphab
Numericchairpassdefaul
Numericconfidmaxlen
Numericconfpassdefault
Numericconfidminlen
LEN
Passwordexpirationwarni
Passwordexpirationdays
Passwordhistorysize
Restrictcontentbroadca
Example
Ultrasecuremode
Systemlisteningvolume
Usegkprefixforpstnca
LLS
Acceptvoipdtmftype
To add a flag
Manually Added, Modified, Deleted System Flags Description
Is the preferred codec for SIP/Lync calls
42Kbps, fail, thus disconnecting the call
Manually Added, Modified, Deleted System Flags
Flag Description
Bytimers
Blockcontentlegacyfor
Bondinggroupdelay
Burnbios
Cascadelinkplaytoneon
Cfgkeyenableflowcont
Connection
Cellindlocation
DELAYBETWEENH320DIALO
Timer
Disablecellsnetworkind
Disabledummyregistratio
Disableselfnetworkind
Disablegwoverlayindicat
Disablewiderestosipdi
Enableciscogk
Enableepc
ENABLECONTENTOF768FOR
Enableflowcontrolrein
Enableexternaldbacces
Enablenovideoresource
Enablemsfec
Enablerecording
Enablertptrafficshapin
Enablesirenlpr
Enablesipppcforallus
Enablesirenlprsipencry
Enabletcpackage
Externaldbpassword
Externaldblogin
Externaldbdirectory
Externaldbip
Forceaudiocodecforms
Forceresolution
Singlecore
Forceencryptionforund
G728ISDN
Numericconfpassdefault LEN Numericchairpass Defaultlen
H239FORCECAPABILITIES
H264HDGRAPHICSMINCONT
Ignoreaim
IPV6AUTOADDRESSCONFIGU
Iplinkenvironment
Ipresponseecho
Transcoding
For single MCU conferences
For cascaded conferences
Possible values
Default n
Medianicmtusize
Maximumrecordinglinks
Minimumframeratethres
Holdforsd
Possible Values YES / no
Portgaugealarm
Passwordfailurelimit
Pcmfecc
Pcmlanguage
Pstnringingdurationsec
Nnovideotimer REMOVEH323EPCCAPTON
Qosipaudio
Qosipvideo
Enable
Rtcpfirenable
REMOVEH323HIGHPROFILE
Captononpolycomvend
Interval
Rtcpplienable
Rtcpqosisequaltortp
Rtvmaxbitrateforforc
Sendwiderestoisdn
Sendsrtpmki
Sendwiderestoip
Setaudioplc
Setaudioclarity
Setautobrightness
Setdtmfsourcediffins
Sipfastupdateintervale
Sipenablefecc
Sipbfcpdialoutmode
Sipdualdirectiontcpco
Sipfreevideoresources
Socketactivitytimeout
Sipomitdomainfrompart
Yname
Tclatencysize
V35MULTIPLESERVICES
Tcpretransmissiontimeou
Trafficshapingmtufacto
Manually Added Csmoduleparameters System Flags Description
Manually Adding Flags to the Csmoduleparameters Tab
Qosipsignaling
Msupdatecontac
Siptcptlstimer
Tremove
Deleting a Flag
Auto Layout Configuration
To delete a flag
Available Layouts No. of Cells Layout Layout Flag Value
Default Auto Layout is controlled by 13 flags
Customizing the Default Auto Layout
Polycom, Inc 807
Example
Legacyepcontentdefaultlayout Flag
Csenableepc Flag
Enabling the Automatic Generation of Passwords
Automatic Password Generation Flags
Automatic Password Generation Flags Description
Hideconferencepassword
Default in Ultra Secure Mode Conference password must be
Default in non-secured mode means no minimum length
Default in Ultra Secure Mode, Chairperson password must
16, 6 default non-secured mode
Numericchairpass Default LEN
Ultra Secure Mode Flag
Ultra Secure Mode
Polycom, Inc 813
Enabling Ultra Secure Mode
PCM
Modifying the Ultra Secure Mode System Flag Value
Ultrasecuremode System Flag
To modify the Ultrasecuremode System flag value
System Flags affected by Ultra Secure Mode
Login and Session Management
Range Default Network Security
Strong Passwords
User Management
Enablecyclicfilesystemalarms YES/NO
Range Default
Certificate Management
PKI Public Key Infrastructure
PKCS#7/P7B
To access the Certification Repository
Adding Certificates to the Certificate Repository
To add a certificate to the repository
Trusted Certificates
Send Certificate File
Paste Certificate and Send Certificate
Paste Certificate and Send Certificate
Send Certificate File
Polycom, Inc 822
To add a Personal Certificate to the Certificate Repository
Personal Certificates
Click Send Certificate
Certificate Validation
General Error message from the SSL library
Adding a CRL
CRL Certificate Revocation List
Select the Certificate File Format PEM or DER
To add a CRL to the repository
To remove a CRL
Removing a CRL
Revocation Method
Certificate Revocation
One of three Certificate Revocation Methods can be selected
Global Responder URL
No Certificate Validation is performed
Self-signed Certificate
Self-signed Certificate Creation
SHA1
Self-signed Certificate Field Values Creation
To perform an Emergency CRL Update procedure
Emergency CRL Certificate Revocation List Update
Download and save the updated CRL files from the CA Server
Disable Secure Communications mode
Open the Certification Repository and Update the CRL files
Re-connect to the RMX
Update the repository
Re-enable Secured Communications Mode
Polycom, Inc 835
Siptcpkeepalivetype None
SIP TCP Keep-Alive
RFC5626
If its value is Reregistrationwhennopongresponse
System Flags Siptcpkeepalivetype / Behavior
Donotreregistrationwhennopongresponse Default
Flag Possible Flag Values
Siptcpkeepalivebehavior
User and Connection Management
Managing the user login process includes
Keep Alive Frequency
Managing system users includes
User Types
Managing the System Users
Disabling/Enabling Users
Renaming Users
Password Character Composition
Managing the User Login Process
Implementing Strong Passwords
Defining Password Aging
Password Length
Implementing Password Re-Use / History Rules
Maximum Repeating Characters
Defining Password Change Frequency
Forcing Password Change
User Lockout
User Login Record
Temporary User Lockout
Session Timeout
Connection Timeout
Controlling User Sessions
Management Sessions per System
Erase Session History After Logout
Guidelines for Customizing the Login Page Banner
Polycom, Inc 847
Polycom, Inc 848
Polycom, Inc 849
Securing an External Database
Standard Security Mode
Ultra Secure Mode
MS Active Directory Integration
Directory and Database Options
Guidelines
Enabling Active Directory Integration
To configure Directory Services
Directory Services Configuration Field Description
Directory Services Role Mapping dialog box is displayed
Restoring the Collaboration Server Using the USB Port
Directory Services Role Mapping Field Description
Click the Role Mapping tab
Precedence Levels
Mlpp Multi Level Precedence and Preemption
FLASH-OVERRIDE-OVERRIDE Classified Networks only
SIP Message
Enabling Precedence
Dial-in calls
FLASH-OVERRIDE-OVERRIDE
Flash Immediate Priority Routine None
Domain Name = UC Sub Domain = r-priority =
Incoming SIP
No Default
Message
UCC
Precedence Level Change
Dial-out calls
Default Cleared Precedence disabled
To configure Precedence Settings
Optional Modify the values if required
Possible Values 1
System Flags
Precedence Settings Domains, Levels and Dscp Values
Monitoring Precedence Level
Following 802.1X Authentication methods are supported
Ieee 802.1X Authentication
Certificate Repository
PEAPv0 MSCHAPv2
802.1X Authentication Configuration Field Description
Enabling and Configuring 802.1X Authentication
Disable the 802.1X Authentication method
EAP-MD5
Range YES/NO
802.1X Authentication System Flags Flag name Description
Default Disabled
Ethernet Monitoring
White List Access
Disabling 802.1X Authentication
Enabling, Disabling and Modifying the White List
To enable, disable, view or modify the White List
Workstation / Device
Iii Click Yes to apply the modified White List
IP Address Modes
System Flag
Disabled
Alternative Network Address Types Anat
Bfcp Over UDP AS-SIP Content
Enabling AS-SIP Content
Internet Control Message Protocol Icmp
System Flag Enableacceptingicmpredirect
System Flag Enablesendingicmpdestinationunreachable
Modifying the flag values
Password Encryption
Upgrade / Downgrade Guidelines
SIP UDP
Polycom
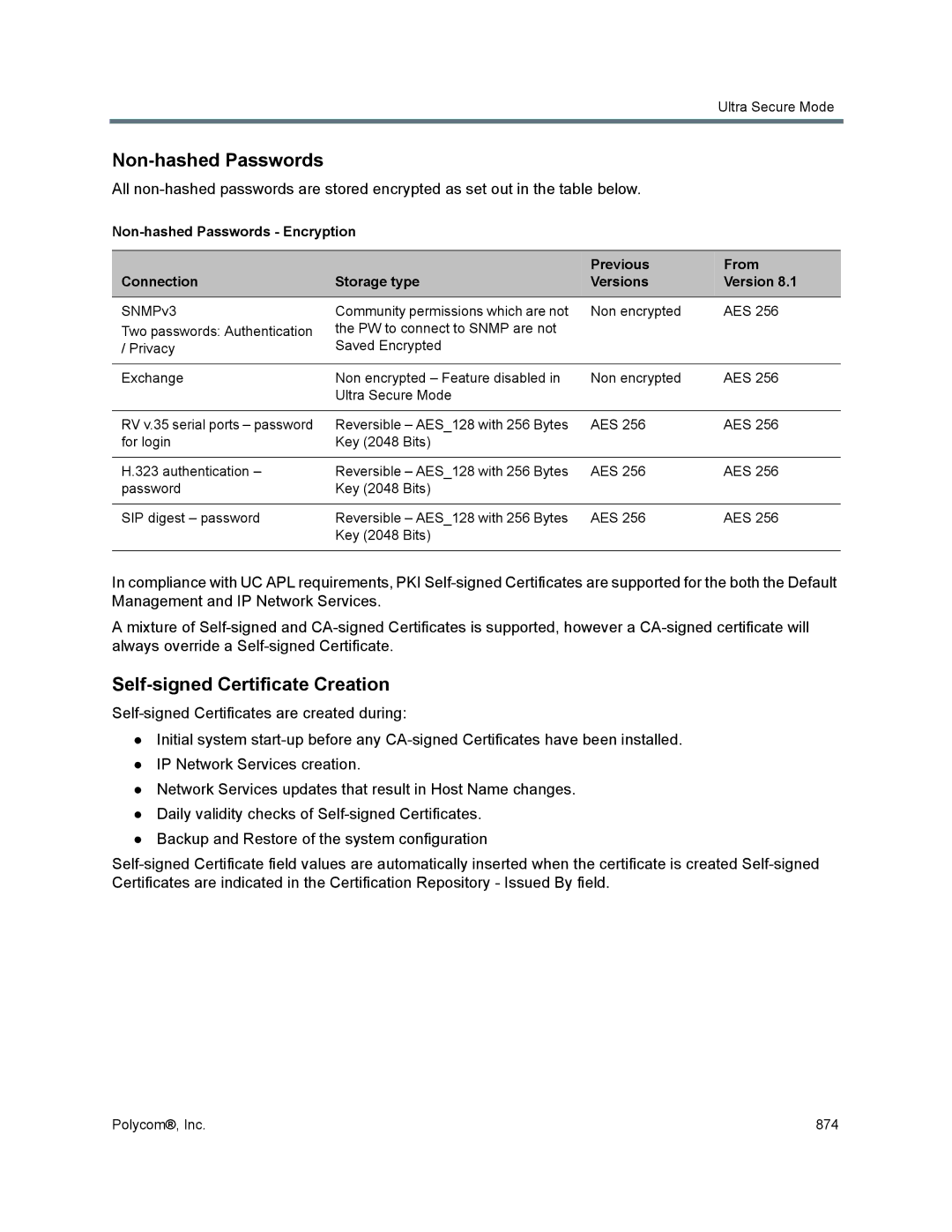
Non-hashed Passwords
Self-signed Certificate Creation Field Value
Media Encryption and Authentication
Negotiation Protocol Authentication Tag Length
Privacy Protocols Flag Settings
Range 80, 32
NGH Flag Value
Viewing the Status of the Hardware Components
Collaboration Server Hardware Monitoring
HW Monitor Pane Status Columns Field Description
To access Hardware Monitor
Viewing the Properties of Hardware Components
Diagnostics , or Empty
HW Monitor Pane Toolbar
Critical
Properties
To view the MCU Properties
Hardware Properties dialog box has the following structure
MCU 1800 Properties General Info
General information is displayed
MCU Properties Event Log Column Description
To view a card properties
Mezzanine
Card Properties General Info Field Description
View Backplane Properties
To view the supporting hardware components properties
View FAN Properties
Click Close to return to the Hardware Monitor pane
Fans
View LAN Properties
Temperature Thresholds
To view a LAN connector properties
To run Diagnostics on a card
Diagnostic Mode
Polycom, Inc 889
To exit the Diagnostics Mode
Call Disconnection Causes Description
Appendix a Disconnection Causes
IP Disconnection Causes
ARQ
Call Disconnection Causes Description
Is longer than the server is willing to interpret
Request
Isdn Disconnection Causes Number Summary Description
Isdn Disconnection Causes
Enquiry
CUG
Isdn Disconnection Causes Number Summary Description
Mandatory information elements containing invalid content
ULTRASECUREMODE=YES
Appendix B Active Alarms
Active Alarms Alarm Code Alarm Description
Appendix B Active Alarms
Active Alarms Alarm Code Alarm Description
Active Alarms Alarm Code Alarm Description
Active Alarms Alarm Code Alarm Description
Active Alarms Alarm Code Alarm Description
Active Alarms Alarm Code Alarm Description
Install the appropriate media card
Active Alarms Alarm Code Alarm Description
Failure
Active Alarms Alarm Code Alarm Description
Active Alarms Alarm Code Alarm Description
Conference Summary Record Fields Description
Appendix C CDR Fields, Unformatted File
Conference Summary Record
Conference Summary Record Fields
Event Types
Event Records
Standard Event Record Fields
CDR Event Types Event Code Event Name Description
Event Specific Fields
Participant Connected Recording
Update
Link SIP Private
Extensions Gatekeeper
User SET END
User Update
Time
Operator
Start
Event Fields for Event 1 Conference Start
Event Fields for Event 2001 Conference Start Continue
Event Fields for Event 1 Conference Start Description
Appendix C CDR Fields, Unformatted File
Event Fields for Event 5001 Conference Start Continue
Event Fields for Event 2 Conference END
Event Fields for Event 6001 Conference Start Continue
Event Fields for Event 11001 Conference Start Continue
NTI TIE Trunk ATT Accunet
Any other number Unknown
Event fields for Event 4 ISDN/PSTN Channel Disconnected
Event fields for Event 5 ISDN/PSTN Participant Connected
Appendix C CDR Fields, Unformatted File
Appendix C CDR Fields, Unformatted File
Appendix C CDR Fields, Unformatted File
Number of MCU Phone Numbers
Terminal
SIP URI
Event fields for Event 15 H323 Call Setup
Event fields for Event 15 H323 Call Setup
Changed
MCU
Terminal
Event Fields for Event 20 Billing Code
Event Fields for Event 18 NEW Undefined Participant
Event fields for Event 26 Recording Link
Event Fields for Event 22 Dtmf Code Failure
Event Fields for Event 30 Gatekeeper Information
Event Fields for Event 28 SIP Private Extensions
Event fields for Event 31 Participant Connection Rate
Event Fields for Event FieldDescription
Characters
Appendix C CDR Fields, Unformatted File
Event Fields for Event 106 User SET END Time
Is currently supported
Isdn
Polycom, Inc 946
Event Fields for Events 2011, 2012,
Disconnection Cause Values
Event Fields for Event 3010 Participant Information
VIP
Disconnection Cause Values Value Call Disconnection Cause
Disconnection Cause Values Value Call Disconnection Cause
Disconnection Cause Values Value Call Disconnection Cause
Conference is started using one of the following method
Ad Hoc Conferencing without Authentication
Ad Hoc Conference Initiation without Authentication
Ad Hoc Conferencing with Authentication
Polycom, Inc 953
Conference Access with External Database Authentication
Conference Access Validation All Participants Always
Conference Access Validation Chairperson Only Upon Request
Ad Hoc Settings
Authentication Settings
Click OK Reset the MCU for flag changes to take effect
To set the System Configuration flags
Enableexternaldbaccess
Modify the values of the following flags
Set the External Server Authentication field to
» Set the External Server Authentication field to Numeric ID
Page
RTP Statistics
Endpoint
Details
Following details are displayed
Processing, but is not considered a fault
Number of packets arriving out of order.
Certificate Template Requirements
Appendix F- Secure Communication Mode
Certificate Configuration and Management
Configure Certificate Management
Switching to Secure Mode
Purchasing and Installing a Certificate
Certificate Requirements
To enable secure communications mode
Enabling Secure Communication Mode
Default for U.S. Federal licenses TLSV1
Creating/Modifying System Flags
Polycom, Inc 967
Alternate Management Network
Restoring Defaults
Alternate Management Network 1500/2000/4000
Configure the Workstation
Management Network Primary
To modify the workstation’s IP addresses
Polycom, Inc 971
Page
Collaboration Server RMX
Connect to the Management Network
To connect directly to the Collaboration Server
Polycom, Inc 974
Collaboration Server RMX
Connect to the Alternate Management Network 1500/2000/4000
To connect to the Alternate Management Network
Procedure 2 Configure the Modem
Procedure 1 Install the RMX Manager
Procedure 3 Create a Dial-up Connection
Configure the modem with the following settings
When the New Connection Wizard is displayed, click Next
Polycom, Inc 979
Polycom, Inc 980
Connection Wizard
Click All Programs
Procedure 4 Connect to the Collaboration Server
To Connect using the RMX Manager To use the browser
Overview
Appendix H Deployment Into Microsoft Environments
Deployment Architecture 2 RealConnect Cascaded Conferences
Backward Compatibility to Lync
Video Resource Requirements and Implications
Support for HD1080p Resolution
Limit Maximum Resolution for MS SVC Using a System flag
FEC Forward Error Correction
Default Auto
IPv6 Support
System Flags for Cropping Control
Range Default
RealPresence CSS Gateway
Sharing Content During a Conference
RealPresence CSS Plug
CSS Gateway Usage Guidelines
Lync
CSS Behavior by Lync Content Type CSS Plug CSS Gateway
Cisco TIP Support
MLA Mode Collaboration Server Side Lync 2013 Avmcu Side
Lync 2013 Participant Monitoring
Mainandinslave
Monitoring Participant Properties Channel Status Tab
Polycom, Inc 994
Look and Feel
Deployment Architecture 1 RealPresence Hosted Conferences
Deployment Architecture 2 RealConnect Cascaded Conferences
Look and Feel for Legacy Endpoints
Look and Feel for Lync Clients and Group Series Endpoints
Video Optimized
Remove Empty Cells From the Video Layout
Handle Low Bit Rate Calls From the Avmcu
Case
Range
Polycom, Inc 1000
Meet Now Lync Conference
Initiate and Connect to a Conference
RealConnect for Lync
To connect to an Avmcu conference
Call Admission Control
Video Switching Conferences
Conferencing Behavior
Continuous Presence Conferences
Monitoring Participant Connections
Active Alarms
Active Alarms and Troubleshooting
ICE Active Alarms
URI
Troubleshooting
Known Issues
Polycom, Inc 1007
Appendix I Polycom Open Collaboration Network Pocn
Single Company Model Polycom and Cisco Infrastructure
Deployment Architectures
IOS
Ctms
Solution Architecture Components Version Description
VCS
Polycom Equipment
MLA
Multipoint call with DMA
Call Flows
Multipoint call without DMA
Model
Company to Company Models Using a Service Provider
Model
Collaboration Server
Cisco telephony and desktop endpoints
Company to Company via Service Provider Model
Call Flow
Multipoint call via Service Provider Model
Polycom, Inc 1018
Company a
Company B Solution Architecture Components Cisco Equipment
Company B
Deployment architecture includes
Polycom, Inc 1020
Gatekeepers
Administration
Configuring the Cisco and Polycom Equipment
Polycom Equipment
Cisco Equipment
Supported Polycom products Polycom TIP and SIP Versions
SIP only no TIP support Versions
Configuring DMA
Configuring the Collaboration Server
Configuring Endpoints
Set the Mintipcompatibilitylinerate System Flag
Configuring the Conference and Entry Queue IVR Services
Configuring Entry Queues and IVR Services
Entry Queue and Virtual Entry Queue Access
Endpoints Registered to Cucm
Procedure 1 Set the Mintipcompatibilitylinerate System Flag
Outbound Proxy Servers table
TIP HD Video Resolution by Line Rate
SIP Server field, select Specify
Polycom, Inc 1027
Polycom, Inc 1028
Polycom, Inc 1029
Polycom, Inc 1030
Polycom, Inc 1031
Polycom, Inc 1032
Polycom Immersive Telepresence Systems ITP Version
Content Sharing Behavior
Polycom video conferencing endpoints HDX Version
Cisco TelePresence System CTS Versions 1.7
Polycom, Inc 1034
Collaboration with Microsoft and Cisco
Cucm
RTV 720p Cisco TelePresence System CTS Versions CTS
HDX RSS
RealPresence Capture Server
DMA Cmad ITP OTX, RPX, ATX, TPX
Microsoft
Cisco
Multipoint Calls using DMA
Microsoft Lync Server
Solution Interoperability Table
SP2
CU4
Supported Resolutions
Supported TIP Resolutions and Resource Allocation
TIP Layout Support & Resource Usage
Resource Allocation
To configure the Microsoft, Cisco and Polycom components
Configuring the Microsoft, Cisco and Polycom Components
Appendix H Integration Into Microsoft Environments
Register the ITP endpoints to the Lync server
Polycom, Inc 1046
Polycom, Inc 1047
Flow Control Via H.239
Encryption
TIP Compatibility Prefer TIP Content Receiver
A new or existing Profile, click the Advanced tab
To enable Dtls negotiation for content encryption
Polycom, Inc 1051
Resolution Configuration
Content XGA,5fps No Content
Video and Content Endpoint Registration Lync
Endpoints
HDX to Collaboration HD H.264 Video Server
Monitoring
Operations During Ongoing Conferences
CTS Participants
Participant Properties General dialog box opens
Polycom, Inc 1055
Lync Participants RTV
Known Limitations
Polycom, Inc 1058
Standard restore deletes the following files
Appendix J Restore Defaults
Perform a Standard Restore
Restore Factory Defaults dialog, select Standard Restore
To perform a Standard Restore using the RMX Web Client
Perform a Comprehensive Restore
To perform a comprehensive restore using the RMX Web Client
Optional. Back up the system configuration
Select Open Folder to view files using Windows Explorer
To perform a comprehensive restore using the USB key
MD5
Appendix K SIP RFC Support
Rsvp
Srtp
Appendix K SIP RFC Support
Traffic Shaping Guidelines
Appendix L Media Traffic Shaping
HD1080p Audio Only
System Flags
Capacity Reduction During Traffic Shaping
Flag name Siptimerssetindex
323 & SIP Flag Settings
Appendix M Homologation for Brazil
323 & SIP Protocol Flag Options
Flag name Disabledummyregistration
Flag name H323TIMERSSETINDEX