AT&T
Copyright 1996, AT&T All Rights Reserved Issue June
Contents
Understanding the Mail System Features
Verifying System Operation and Troubleshooting
Upgrading the System
Mail System Planning
Communications System Planning
Mail System Factory Settings
Letter Key and Class of Service Table
GL Glossary Index Programming Hierarchy Diagrams
Terms
Purpose and Audience
Typographical Conventions
How to Use This Book
Toll Fraud Security
Safety Labels
Related Documents
Partner Mail Voice Messaging System Release
Partner Plus Communications System Release
Partner II Communications System Release
System Administrator’s Responsibilities
Introduction Partner Mail Services
Introduction
Partner Mail Services
Overview of System Services and Features
Automated Attendant Service
Attendant
Assignments
Fax Extension and Fax Message Receiver
Interactions with the Communications System
Immediate Call Handling
Call Answer Service
Interactions with the Communications System
Operator
Voice Mail Service
System Administrator’s Responsibilities
For more information, see Personal Mailbox Administration
System Security
Preventative Measures
Page
Security Policy and User Education
Routine Maintenance
Helpful Programming Hints
Installing the Mail System
Introduction Preparing for Installation
Important Safety Instructions
Preparing for Installation
Communications System Hardware
Mail System Hardware
Mail System Requirements ConditionRequirement
Mail System Site Requirements
Preparing for Installation
Mounting the System Unit
Installing the Mail System
Mounting the Cabinet
Connecting Cords to the System Unit
Connecting to the Communications System
System Unit Front and Right Side View
Remote Maintenance Device
Connecting to the Remote Maintenance Device
Introduction Before You Begin
Mail System Initial Programming
After Initial Programming
Comlpeting Planning Forms
Before You Begin
Hunt Group Extensions
Preparing the Communications System
Transfer Return Extension
Line Access Mode
Outgoing Call Restriction
Line Assignment for Remote Maintenance Device
Automatic Extension Privacy for Remote Maintenance Device
Logging In to System Administration
Page
Mail System Login
Programming the Mail System
Accessing the System Administration Menu
System Parmeters
Initial Programming Quick Reference
System Greetings
Programming System Parameters
Parameter Factory Setting
System Language
Maximum Digit Length
Single or Multiple Automated Attendant
Automated Attendant Line Assignments
Automated Attendant Line Assignments
Mailboxes
Programming Mailboxes
Creating Mailboxes
Considerations for Creating Mailboxes
Assigning a Group Mailbox Owner
Fax Extension and Fax Message Receiver
Specifying Fax Extensions and System Mailboxes
Call Answer Service Operator
System Administrator’s Mailbox
General Mailbox Owner
Programming the Schedule
Schedule Administration
Schedule Controller
System Date and Time
Business Schedule
Automated Attendant Administration
Setting the Touch-Tone Gate
Recording System Greetings
Recording Touch-Tone Gate Greetings
System Greetings Administration
Recording a Voice Mail Greeting
Programming the Automated Attendant Menus
Creating Submenus
Recording Announcements
Programming Day and Night Menus
+ Announcement number + #
Creating Group Lists
Group Lists Administration
Line Ownership Assignment
Assigning Line Ownership
10. System Security Administration
Setting System Security Options
Security Violation Notification
Minimum Password Length
Assigning the System Administrator’s Mailbox Password
Assigning a System Administration Password
After Initial Programming
Page
Communications System Initial Programming
Call Answer Service
Telephone Button Programming
Introduction
Group Call Distribution
Entering Programming Mode
Automated Attendant Service
VMS Hunt Delay
Fax Machine Extensions
Fax Hunt Group
Line Ringing
VMS Hunt Schedule
Automatic Extension Privacy
Music on Hold
Night Service
To save the number in memory, you must press Enter
Disallowed Phone Numbers
Creating a Disallowed List
Assigning the Disallowed Phone Number List
Allowed Phone Numbers
Creating an Allowed Phone Number List
Assigning the Allowed Phone Number List
Call Answer Service
Line Coverage
VMS Line Cover
Exiting Programming Mode
Automatic VMS Cover
VMS Cover Rings Communications System Release 4.0 or later
Telephone Button Programming
VMS Cover
Do Not Disturb
Voice Mail Messages
Voice Mailbox Transfer
After Initial Programming
Bulletin Board
Administering Features
Automated Attendant Service Broadcast Message
Announcements Automated Attendant
Directory
Call Answer Service Operator
Dial 0/Timeout Action Automated Attendant
Business Schedule and Temporarily Closed
Line Assignments
Group Lists
Group Mailbox Owner
Language
Outcalling
Main Menus Automated Attendant
Maximum Digit Length
Open or Closed for Today
Schedule Controller
Passwords
Personal Mailbox Administration
Personal Operator
System Language
System Administrator’s Mailbox
Submenus Automated Attendant
System Date and Time
Administering Features
Logging In to Voice Mail
Logging In to System Administration
Announcements Automated Attendant
At a Glance
Description
Announcements and Bulletin Boards
Announcement Options
Applications
Related Mail System Features
Programming Recording an Announcement
For the secondary language
Monolingual mode
Bilingual mode
Procedure is complete
Enter the Announcement number 1-99 + #
Playing an Existing Announcement
Deleting an Announcement
Related Communications System Features
Related Mail System Features
Broadcast Messages and Group Lists
Broadcast Message
Programming Sending a Broadcast Message
Bulletin Board
Monolingual or Bilingual Mode
Bulletin Boards and Announcements
Dial 0 Destination
Other Bulletin Board Options
Bulletin Board Mailbox Password
Considerations and Constraints
Procedures Accessing a Bulletin Board Message
Programming
Mailbox
Go to Step
Bilingual mode only
Recording or Deleting a Bulletin Board Message
Message. Go to Step
20Bulletin Board
Enter extension number + #
Setting a Dial 0 Destination
Changing a Bulletin Board Mailbox Password
Changed. Procedure is complete
Business Schedule and Temporarily Closed
Temporarily Closed
Weekly Business Schedule
Today
Programming Playing the Business Schedule
Creating or Changing the Weekly Business Schedule
26Business Schedule and Temporarily Closed
Programming a Temporary Closing
Repeat Step
Confirm. Go to Step
Business Schedule and Temporarily Closed
Call Answer Service Operator
Dial 0/Timeout Action for Main Menus Automated Attendant
Dial 0/Timeout Action Automated Attendant
Menu. Go to Step
Programming Changing a Dial 0/Timeout Action
Prompt. Go to Step
Procedure is complete. Bilingual mode, primary language
Directory
Changing a Directory Listing
Procedure Using the Directory to Reach a Subscriber
Using the Directory to Address a Message
Transferred. Procedure is complete
Fax Extension and Fax Message Receiver
Description Fax Extension
Fax Message Receiver
Considerations and Constraints
Receiver. Go to Step
Hunt Group. Procedure is complete
Enter Fax Message Receiver + #
Deleting a Fax Extension or Fax Message Receiver
Extension. Procedure is complete
General Mailbox
Automated Attendant
Programming Changing the General Mailbox Owner’s Extension
Procedure Forwarding a Message from the General Mailbox
Extension. Go to Step
Enter General Mailbox Owner + # Single Automated Attendant
List. Repeat Step
Group List. Repeat Step
Greetings Personal
Call Answer Service Operator
Procedures Recording a Personal Greeting
For Bilingual Mode, primary language
For Monolingual Mode, procedure is
Greeting. Go to Step
Complete
Deleting a Personal Greeting
Activating a Personal Greeting
Monolingual Mode, procedure is
Voice Mail Greeting
Greetings System
Automated Attendant Touch-Tone Gate Greeting
Examples
Monolingual Mode-Touch-Tone Gate On
Main Menu, Primary Language
Monolingual Mode-Touch-Tone Gate Off
Greetings Personal
Programming Recording the Voice Mail Greeting
Repeat for the secondary
Recording a Touch-Tone Gate Greeting
Menu. Return to Step
New greeting. Repeat Step
Group Lists
Group Lists and Broadcast Messages
Repeat until all extensions are
Programming Creating Group Lists
Scanning Group Lists
Enter Group List number + #
Modifying or Reviewing a Group List
For each mailbox to be added to
Group List. When finished, go to
Deleting Group Lists
If desired, return to Step
Procedure Sending a Message to a Group List
Forwarding a Message to a Group List
Under Personal Mailbox Administration
Group Mailbox Owner
Programming Assigning or Deleting the Group Mailbox Owner
No owner. Return to Step
Enter Group Mailbox Number
If the mailbox has an owner
If the mailbox has no owner
Language
Mode only
Programming Recovering from a Language Choice Error
Announcements Automated Attendant
Main Menus Automated Attendant Submenus Automated Attendant
Language. Repeat Step
Changing the Language Mode or the Language
Line Assignments
Adding Line Assignments
Programming Reviewing Line Assignments
Repeat until finished
Removing Line Assignments
If the line is not currently assigned to
Automated Attendant 2 or
76Line Assignments
Line Ownership
Programming Scanning Line Ownership
If no owner is assigned
If a line owner is assigned
If the line number has an owner
Modifying Line Ownership
Deleted.Return to Step
Deallocating Line Ownership
Mailbox
Class of Service COS
Mailbox Storage
Class of Service Table
Mailbox Type
Message Length
Greeting Length
Transfer Permitted
Page
Outcalling Permission
Mailbox Language Bilingual Mode only
Letter Key
Mailbox Name
Considerations and Constraints
Group Mailbox Owner
Administration
Enter Mailbox Number + #
Programming Playing a Mailbox Configuration
Monolingual mode only
Class of Service + #
Number. Go to Step
Bilingual mode only. Choose an option
Deleting a Mailbox
Changing a Mailbox Name
Mailbox and any messages in it
Mailbox number. Return to Step
Changing the Class of Service
Initializing a Mailbox Password
Enter Class of Service + #
Only
Changing the Mailbox Language Bilingual Mode
Main Menus Automated Attendant
Language Bilingual Mode only
Menu Prompt
Monolingual Mode Example with Touch-Tone Gate On
Selector Codes
Monolingual Mode Example with Touch-Tone Gate Off
Page
Caller Options
Recommendation
Programming Playing a Main Menu Prompt or Definition
Recording the Main Menu Prompt Only
Menu. Go to Step Multiple Automated Attendant only
Definition. Repeat Step
Monolingual mode
106Main Menus Automated Attendant
If the Selector Code is not already assigned
Change the Dial 0/Timeout Action
Modifying a Day or Night Main Menu
If the Selector Code is already assigned
Selector Code. Return to Step
Monolingual mode
110Main Menus Automated Attendant
Programming Changing the Maximum Digit Length
Maximum Digit Length
Enter Maximum Digit Length
Menu. Procedure is complete
Open for Today
Open or Closed for Today
Resume Regular Schedule
Close for Today
Default Temporary Closure Greetings
Spanish Primary/English Secondary
French Primary/English Secondary
Programming Programming Open or Closed for Today
118Open or Closed for Today
Resuming the Regular Schedule
Outcalling
Outcalling List
Minimum Time Between Outcalling Attempts
Outcalling Schedule
Outcalling Cycles
Creating or Changing the Outcalling List
Procedures Turning Outcalling On/Off
Reviewing the Outcalling List
Listening to Instructions for Outcalling
Enter Outcalling number + #
Pager. Go to Step
Set to all hours
Setting Up the Outcalling Schedule
Not set to all hours
Schedule. Go to Step
Setting the Minimum Time Between Outcalling Attempts
Setting the Number of Outcalling Cycles
System Administrator’s Passwords
Passwords
Password Initialization
Password Cautions
Setting the Minimum Password Length
Programming Initializing a Mailbox Password
Changing the System Administration Password
Procedures Changing a Mailbox Password
Enter Minimum Password Length + #
Changing a Bulletin Board Mailbox Password
Transfer-Only Mailboxes
Personal Mailbox Administration
Old and New Messages
Personal Greetings
Personal Operator
From Automated Attendant
Ss System Features
Outcalling
Programming Logging In to Voice Mail
Activity Menu. Procedure is complete
Recording and Sending a Message
Message. Repeat Step
Use 7 for the letter Q 9 for the letter Z
Names. Go to Step
Group List. Return to Step
Listening to Messages
Replying to a Message
Forwarding a Message
Use 7 for the letter Q 9 for Letter Z
Recording a Mailbox Name
Recording and Activating Personal Greetings
Choosing a Personal Operator
Personal Operator
Programming Administering a Personal Operator
Schedule Controller
Follow the Switch Mode
Business Schedule
Follow the Partner Mail Business Schedule
Programming Setting the Schedule Controller
No Security Violation Notification
Security Violation Notification
Unsuccessful Login Attempts
Mailbox Unlock
Notification
Programming Changing the Security Violation Notification
Length
Attempts. Go to Step
Single/Multiple Automated Attendant
For each Automated Attendant, you can program the following
Programming Setting Single or Multiple Automated Attendants
Submenus Automated Attendant
Selector Codes and Selector Code Actions
Other Submenu Options
Submenu Creation
Submenu Modification
Programming Playing a Submenu Prompt or Definition
Press 3 for Submenus Submenu Administration Menu
Submenu number + #
Creating a Submenu
160Submenus Automated Attendant
Recording the Submenu Prompt Only
Repeat to Step
Modifying a Submenu
164Submenus Automated Attendant
Choose an option # to use the existing Submenu
Submenu number + # Prompt to confirm deletion
Deleting a Submenu
System Administrator’s Mailbox
Changing the System Administrator’s Mailbox
Programming Re-assigning the System Administrator’s Mailbox
Changing the System Administrator’s Mailbox Password
Enter new extension + #
Personal Mailbox Administration
System Date and Time
Programming Updating the System Date and Time
Time. Go to Step
If System Administrator’s mailbox Language is English
System Language
Touch-Tone Gate
Touch-Tone Gate Setting
Considerations and Constraints
Programming Turning the Touch-Tone Gate On or Off
Verifying System Operation
Troubleshooting
Contents
Verify Mail Service Greeting
Verifying System Operation
Dealer
Immediate Call Handling
Delayed Call Handling
Night Menu
Day Menu
Fax Machines
VMS Extension Coverage
VMS Line Coverage
Authorized Dealer
Troubleshooting
Callers hear ringing, but the mail system does not answer
Mail system does not answer immediately
Calls are routed to the wrong Automated Attendant
Calls are not transferred properly
Message cannot be left in a mailbox
Touch-tones are entered but not detected
Subscriber receives a busy signal when calling Voice Mail
Caller is cut off while leaving a message in a mailbox
Subscriber is unable to log in to Voice Mail
Subscriber is unable to log in to Voice Mail
Possible Cause Corrective Action
12Verifying System Operation and Troubleshooting
Possible Cause Corrective Action
Outcalling is not working
Outcalling is delayed
On next
Outcalling is not working
Press 1 for English, 2 for French, or 3 for Spanish
Upgrading the System
Introduction
Captive Retaining Screw Location
Disconnecting the Mail System
Removing the Mail System Unit from the Wall
Removing the Cover Screws
Removing the Cover
Adding a Voice Processing Card
Voice Processing Card DIP Switch Settings
Installing the Voice Processing Card
Putting the System Unit Back Together
Security Alert
Introduction Planning Responsibilities
Mail System Planning
Table A-1. Partner Mail Mail System Planning Forms Name
When to Fill Out the Forms
How to Fill Out the Forms
Planning Responsibilities
Information for the Installer
Form a System Parameters-Part 1 Description
Maximum Digit Length =
Single or Multiple Automated Attendant = Single
Page
Class of Service
Form B Mailboxes Description
Security Alert
Mail System Planning A-7
COS
Instructions
Page
General Mailbox Owner =
Call Answer Service Operator =
System Administrator’s Mailbox =
Form C System Parameters-Part 2 Description
Weekly Business Schedule = Closed
Form D Schedule Description
System Date and Time
Multiple Automated Attendant only
Touch-Tone Gate Greetings
Form E Touch-Tone Gate Description
Page
Form F Voice Mail Greeting Description
Form G Main Menu Prompt Description
Day or Night Main Menu
Main Menu Prompt
Page
Main Menu Definition
Form H Main Menu Definition Description
Multiple Automated Attendant only
Submenu Prompt
Form I Submenu Prompt Description
Submenu Number
Submenu Name
Submenu Definition
Form J Submenu Definition Description
Announcement
Form K Announcement Description
Announcement Number
Announcement Name
Group List Members
Form L Group List Description
Group List Number
Group List Name
Line Ownership
Form M Line Ownership Description
Minimum Password Length =
Form N System Security Description
Security Violation Notification
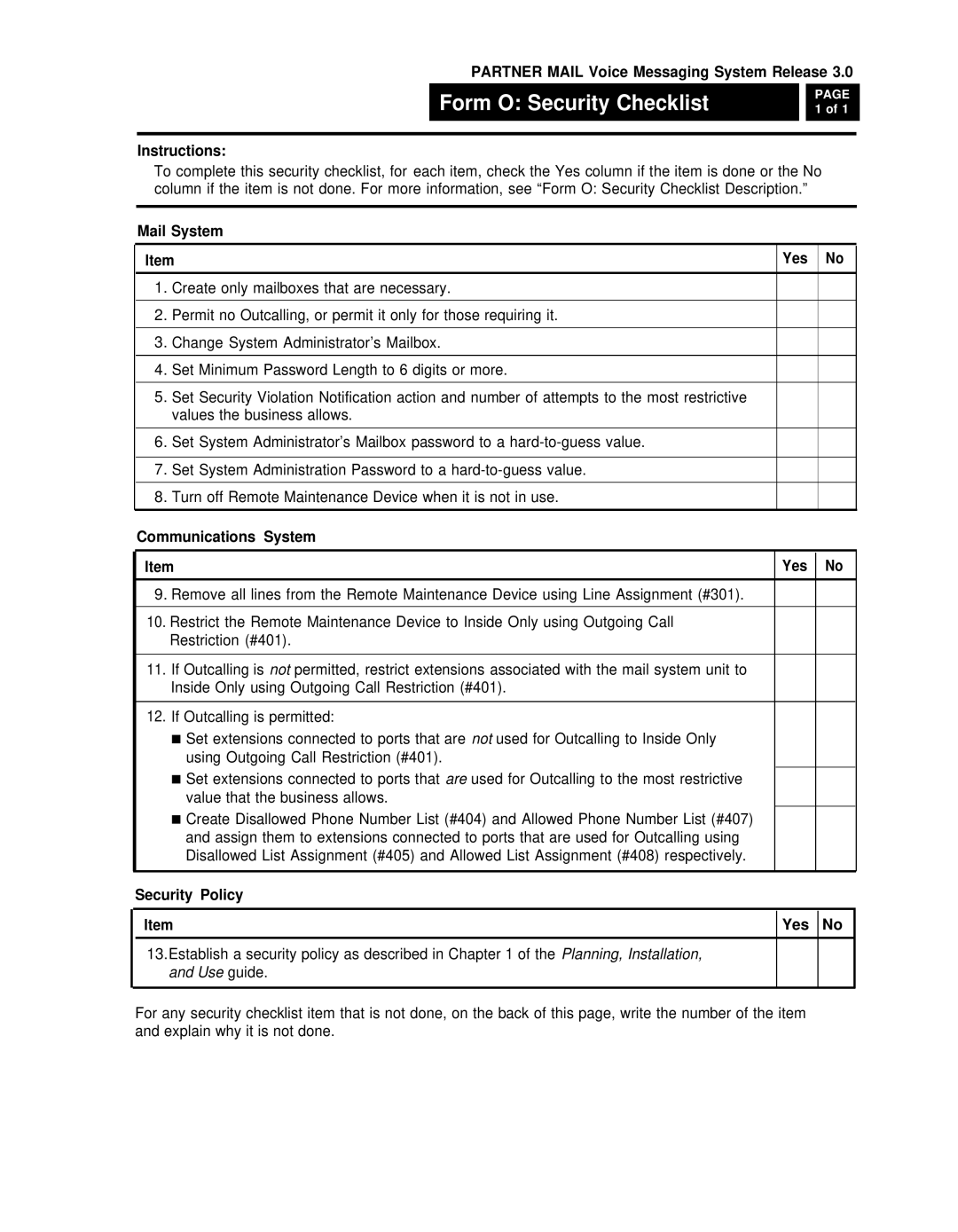
Form O Security Checklist Description
Maximum Digit Length 2 3
Instructions
Form B Mailboxes
Fax Message Receiver
Call Answer Service Operator Ext
System Administrator’s Mailbox Mailbox No Security Alert
Fax Extension
Weekly Business Schedule
Form D Schedule
Form E Touch-Tone Gate
Voice Mail Greeting
Form F Voice Mail Greeting
Day or Night Main Menu 1 Day
Form G Main Menu Prompt
Form H Main Menu Definition
Form H Main Menu Definition
Form I Submenu Prompt
Submenu Number 01-99 Submenu Name Submenu Definition
Form J Submenu Definition
Form K Announcement
Group List Number Group List Name Group List Members
Form L Group List
Form M Line Ownership
Form N System Security
Minimum Password Length
Mail System Yes No
Communications System Yes
Security Policy Yes
Form C Phone
Introduction Form a System Configuration,
Form B2 Customized Extension Settings
Form B1 System Extensions
Order Number
Communications System
Form a Page 1 Description
Form a System Configuration,
Method
VMS-Mail
Receptionist answers calls during business hours?
Form a Page 2 Description
Music on Hold 602 = Active
VMS Hunt Delay #506 = Immediate
VMS Cover Rings #117 =
Ring on Transfer #119 = Active
Form B1 System Extensions
Form B1 Description
Write Name/Description
Write Transfer Return Ext. No. #306
FAX Machine Extensions #601
Form B2 Customized Extension Settings
Form B2 Description
Automatic Extension Privacy #304 = Not Assigned
Outgoing Call Restriction #401 = No Restriction
Automatic VMS Cover #310 = Not Assigned
No Ring
Lines/Pools Not Assigned
Allowed List Assignment #408
Disallowed List Assignment #405
Form C Description
Night Service Button #503 = Not Assigned
Do Not Disturb Feature 0
Form C Phone
VMS Cover Feature 1
Voice Mailbox Transfer Feature 1
Voice Mail Messages Intercom 7 7
Form D Number Lists
Form D Description
Disallowed Phone Number Lists #404
Allowed Phone Number Lists #407
Default Menus
Introduction Factory Settings Default Greetings
Factory Settings
Feature Factory Setting Valid Entries
System Parameters
Schedule
Mailboxes
Automated Attendant Service
Security System
Personal Operator
Outcalling
Messages
Mail Setting Value
Group Lists
System Greetings
Touch-Tone Gate On-Monolingual
Default Greetings
Touch-Tone Gate On-Bilingual
Temporary Closure Greetings Touch-Tone Gate Off-Monolingual
Touch-Tone Gate Off-Bilingual
Voice Mail Greetings
Personal Mailbox Greetings
Spanish Default Mailbox Name Buzón General
Default Menus
English Default Mailbox Name General Mailbox
French Default Mailbox Name Boîte Vocale Centrale
French Day/Night Menu
Day/Night Main Menu
Touch-Tone Gate On-Monolingual Bilingual
English Day/Night Menu
Spanish Primary/English Secondary-Spanish Day/Night Menu
English Primary/French Secondary-English Day/Night Menu
English Primary/Spanish Secondary-English Day/Night Menu
French Primary/English Secondary-French Day/Night Menu
Letter Key Class of Service Table
Table D-1. Letter Key
Letter Key
Table D-2. Class of Service
Class of Service Table
Glossary
GL-2Glossary
See Dial Plan
Group Mailbox Owner
GL-4Glossary
See Primary language and Secondary language
See Automated Attendant Touch-Tone Gate Greeting
See Subscriber
Index
Index
IN-2 Index
Index IN-3
IN-4 Index
Index IN-5
IN-6 Index
Index IN-7
IN-8 Index
Index IN-9
IN-10 Index
Index IN-11
IN-12 Index
Index IN-13
IN-14 Index
Index lN-15
IN-16 Index
Nota
Remarque
Page
Page
AT&T Comcode Issue