Page
Table of Contents
Link DWS-1008 CLI Manual
Link Mobility System
Convention Use
DWS-mmmm-nnnnnn
DWS-mmmm-nnnnnn#
DWS-1008 DWS-1008#
Set port enable I disable port-list
Clear interface vlan-id ip
Clear fdb dynamic I port port-list v1 an vlan-id
Subnet Masks
Wildcard Masks
User Glob Users Designated
MAC Address Globs
Port Lists
DWS-1008#show port status 1-3,6
Command-Line Editing
Keyboard Shortcuts Function
Using CLI Help
Set ap dap name command has the following complete syntax
Set ap dap name
Set ap port-list dap dap-numname name
Defaults None Access Enabled
Disable
Enable
Syntax enable Access All
Syntax set enablepass Defaults None Access Enabled
Set enablepass
Syntax quit Defaults None Access All
Quit
Display
Configuration
Auto-Config
System Identification
Clear banner motd
Clear history
Clear prompt
Clears the system configuration of the specified information
Clear system
Help
History
Quickstart
Syntax set banner motd text Defaults None Access Enabled
Set banner motd
Syntax set confirm on off
Set confirm
Set length
DWS-1008#clear vlan red
Syntax set license activation-key
Set license
DWS-1008#set length
Activation-key
Set prompt
Syntax set prompt string
Set system country code
Stores a contact name for the DWS-1008 switch
Set system contact
Syntax set system contact string
Link DWS-1008 CLI Manual
Set system idle-timeout
Syntax set system idle-timeout seconds
Syntax set system ip-address ip-addr
Set system ip-address
Clear system Show system
Ip-addrIP address, in dotted decimal notation
Syntax set system location string
Set system location
Set system name
Syntax set system name string
Syntax show banner motd Defaults None Access Enabled
Show banner motd
Clear banner motd Link DWS-1008 CLI Manual
Show licenses
Syntax show licenses Defaults None Access All
Syntax show load Defaults None Access Enabled
Show load
Syntax show system Defaults None Access Enabled
Show system
Displays system information
Name
Configured with set system countrycode
Field Description
With set system location
Nvram size /SDRAM size percent of total
Show boot Show config Set licenses Link DWS-1008 CLI Manual
Show tech-support
Syntax show tech-support file subdirname/ filename
Interface Type
Port Type
State
Speed
Clear port counters
Syntax clear port counters Defaults None Access Enabled
Clear dap
Syntax clear dap dap-num
Clear port mirror
Syntax clear port mirror Defaults None Access Enabled
Clear port-group
Syntax clear port-group name name
Defaults None
Clear port name
Clear port type
STP
DWS-1008#clear port type
Monitor port counters
Syntax monitor port counters
Key Effect on monitor display
Displayed for All
Transmit-errors
Statistics Option Field Description
Set dap
Reset port
Details command
Serial id serial ID
Set port
Syntax set port enable disable port-list Enable
Disable
Port-list
Set port-group
Set reset port
Mode on off
Syntax set port-group name group-nameport-listmode on off
Clear port-group Link DWS-1008 CLI Manual
Set port mirror
Set port name
Name name
Set port negotiation
Syntax set port negotiation port-listenable disable
Enable disable
Clear port name
DWS-1008#set port negotiation 5 enable
DWS-1008#set port negotiation 1,2,4-6 disable
Following command enables autonegotiation on port
Syntax set port poe port-listenable disable
Set port speed
DWS-1008#set port poe 3,5 disable
DWS-1008#set port poe 2,4 enable
Syntax set port speed port-list10 100 auto
Enable
Disable
Set port trap
Configures a DWS-1008 switch port for an AP access point
Model Poe enable disable radiotype 11a 11b 11g
Set port type ap
DWS-1008#set port type ap 2 model DWL-8220AP poe enable
Port Parameter Setting
Wired Authentication Port Defaults Port Parameter Setting
Set port type wired-auth
Configures an DWS-1008 port for a wired authentication user
Port-list tag-list Num last-resort
Clear port type Set port type Link DWS-1008 CLI Manual
Port port-list
Defaults None Access All
Show port counters
Statistics for all ports
Show port-group
Show port mirror
Show port poe
Syntax show port poe port-list
DWS-1008# show port poe
Syntax show port status port-list
Displays configuration and status information for ports
Show port status
DWS-1008# show port status
Ports
FDB Aging Timeout
Creation
Restriction of Client Layer 2 Forwarding
Clear fdb
Deletes an entry from the forwarding database FDB
Port port-lis Vlan vlan-id Tag tag-value
Permit-mac
Clear security l2-restrict
Vlan-id Vlan name or number
All
Syntax clear security l2-restrict counters vlan vlan-id all
Clear security l2-restrict counters
Clear vlan
All
DWS-1008#clear vlan red port 4 tag
Set vlan port Show vlan config Link DWS-1008 CLI Manual
DWS-1008#clear vlan green port
DWS-1008#clear vlan marigold
Set fdb
Mac-addr
Port port-list
Set security l2-restrict
Mode enable disable
Set fdb agingtime
Syntax set fdb agingtime vlan-idage seconds
Creates a Vlan and assigns a number and name to it
Defaults Layer 2 restriction is disabled by default
Set vlan name
Syntax set vlan vlan-numname name
Set vlan port
Set vlan port
Syntax set vlan vlan-idport port-listtag tag-value
Show fdb
Syntax show fdb agingtime vlan vlan-id
Show fdb agingtime
DWS-1008# show fdb
DWS-1008#show fdb agingtime
Show security l2-restrict
Vlan vlan-id Defaults None. Access All
Show fdb count
DWS-1008#show fdb count dynamic
DWS-1008# show security l2-restrict
Show vlan config
Syntax show vlan config vlan-id
Displays Vlan information
DWS-1008# show vlan config burgundy
Vlan
Tunl Port Vlan Name Status State Affin Port Tag
From 0 to
Clear qos
From-qos
From-dscp
Dscp dscp-value
Set qos cos-to-dscp-map
Syntax set qos cos-to-dscp-map level dscp dscp-valuelevel
DWS-1008#set qos cos-to-dscp-map 5 dscp
Show qos
Syntax show qos default
Set qos dscp-to-cos-map
Syntax set qos dscp-to-cos-map dscp-rangecos level
Show qos dscp-table
DWS-1008#show qos default
Syntax show qos dscp-table Defaults None Access Enabled
DWS-1008#show qos dscp-table
Clear interface
Removes an IP interface
Syntax clear interface vlan-idip
Clear ip dns domain
Syntax clear ip dns domain Defaults None Access Enabled
Clear ip alias
Syntax clear ip alias name
Clear ip route
Default
Clear ip dns server
Syntax clear ip dns server ip-addr
Set ip route Show ip route
Defaults The default Telnet port number is
Clear ip telnet
Syntax clear ip telnet
Clear ntp server
Clear ntp update-interval
Syntax clear ntp update-interval
Syntax clear ntp server ip-addr all
Syntax clear snmp community name comm-string
Clear snmp community
Clear snmp notify profile
Syntax clear snmp notify profile profile-name
Syntax clear snmp notify target target-num
Clear snmp notify target
Clear snmp usm
Target-num ID of the target
Clear summertime
Syntax clear summertime Defaults None Access Enabled
Syntax clear system ip-address Defaults None Access Enabled
Clear system ip-address
Dnf
Clear timezone
Ping
Flood
Is 8 bytes larger than the size you specify
Defaults
Size size
DWS-1008#ping
Ip-addr Mac-addr
Set arp
Set arp agingtime
Syntax set arp agingtime seconds
Configures an IP interface on a Vlan
Set interface
Set arp Show arp
Set interface dhcp-client
DWS-1008#set interface default ip 10.10.10.10/24
Syntax set interface vlan-idip dhcp-client enable disable
DWS-1008#set interface mauve ip 10.10.20.10
Disables the Dhcp server
Configures the MSS Dhcp server
Enables the Dhcp server
Set interface dhcp-server
Set ip dns domain Set ip dns server Show dhcp-server
Administratively disables or reenables an IP interface
Set interface status
Syntax set interface vlan-idstatus up down
Set ip alias
Set ip dns
Syntax set ip dns domain name
Set ip dns domain
Set ip dns server
DWS-1008#set ip dns domain example.com
Syntax set ip https server enable disable
Set ip https server
Is not available for the destination
Set ip route
Adds a static route to the IP route table
Ip-addr mask
Set ip snmp server
Enables or disables the Snmp service on the DWS-1008 switch
Syntax set ip snmp server enable disable
Clear ip route Show interface Show ip route
Set ip ssh
Syntax set ip ssh port port-num
Set ip ssh server Link DWS-1008 CLI Manual
Set ip telnet
Syntax set ip ssh server enable disable
Set ip ssh server
Syntax set ip telnet port-num
Enables the Telnet server on a DWS-1008 switch
Syntax set ip telnet server enable disable
Set ip telnet server
Set ntp server
Syntax set ntp enable disable
Set ntp
Syntax set ntp server ip-addr
Set ntp update-interval
Syntax set ntp update-interval seconds
DWS-1008#set ntp server See Also
Set snmp community
Drop send
Default profile-name
Set snmp notify profile
Notifications you specify with notification-type or all
Page
Page
DWS-1008#set snmp notify profile snmpprofrfdetect send
RFDetectInterferingRogueAPTraps success change accepted
RFDetectRogueDisappearTraps success change accepted
Set snmp notify target
SNMPv3 with Informs
Username
Ip hex hex-string
Authenticated encrypted
Snmp-engine-id
Security unsecured
Retries num
Timeout num
SNMPv2c with Informs
SNMPv2c with Traps
SNMPv1 with Traps
Success change accepted Link DWS-1008 CLI Manual 110
V2c
Syntax set snmp protocol v1 v2c usm all enable disable
Set snmp protocol
Usm
Encrypted
Authenticated
Set snmp security
Auth-req-unsecnotify
Set snmp usm
Creates a USM user for SNMPv3
Auth-key hex-string
Auth-type none md5 sha
Auth-pass-phrase string
Encrypt-type none des
Start of the time change period
Set summertime
Start
End
Defaults None Access Enabled
DWS-1008#set interface taupe ip 10.10.20.20/24
Syntax set timedate date mmm dd yyyy time hhmmss
Set timedate
Set timezone
DWS-1008#set timedate date feb 29 2004 time
Syntax show arp ip-addr
Show arp
DWS-1008#set timezone PST
Ip-addr IP address
DWS-1008#show dhcp-client
Syntax show dhcp-client Defaults None Access All
Show dhcp-client
Ifup
Verbose
Show dhcp-server
Syntax show dhcp-server interface vlan-id verbose
DWS-1008# show dhcp-server
DWS-1008#show dhcp-server verbose
Bound
Link DWS-1008 CLI Manual 121
Displays the IP interfaces configured on the switch
Show interface
Syntax show interface vlan-id
Set interface dhcp-client
Set interface dhcp-server
Set interface status
Set ip alias
Set ip dns domain
Set ip https server
Default-router
Ip-addr/mask-length
Metric
Enables or disables the Snmp service on the switch
Disables or reenables the SSH server on a DWS-1008 switch
Set ip telnet
Set ntp
Set ntp server
Set snmp community
Notification-type
To modify the default notification profile, specify default
Spaces
Name of the notification type
Page
Sends or drops all notifications
RFDetectAdhocUserTraps success change accepted
RFDetectSpoofedMacAPTraps success change accepted
RFDetectUnAuthorizedSsidTraps success change accepted
Ip hex hex-string
Authenticated encrypted
Snmp-engine-id
Security unsecured
SNMPv3 with Traps
By the target. You can specify from 0 to 3 retries
Specifies the number of times the MSS Snmp engine will
Resend a notification that has not been acknowledged
Specifies the number of seconds MSS waits for
SNMPv1 with Traps
144
Set snmp usm
Page
Auth-type none md5 sha auth-pass-phrase
String auth-keyhex-string
Link DWS-1008 CLI Manual 148
End
Set system ip-address
Sets the time of day and date on the switch
Link DWS-1008 CLI Manual 151
Dynamic Resolved
Local Resolved
152
Show dhcp-client
Link DWS-1008 CLI Manual 154
Table below shows the output for show dhcp-server verbose
Link DWS-1008 CLI Manual 155
Ipv4
DWS-1008# show interface
YES
Link DWS-1008 CLI Manual 156
Name Alias string
Show ip alias
Syntax show ip alias name
DWS-1008#show ip alias
Displays the DNS servers the switch is configured to use
Syntax show ip dns Defaults None Access All
Show ip dns
Displays information about the Https management port
Syntax show ip https Defaults None Access All
Show ip https
DWS-1008 show ip https
DWS-1008# show ip route
Show ip route
Syntax show ip route destination
Multicast
Syntax show ip telnet Defaults None Access All
Show ip telnet
Displays information about the Telnet management port
Displays NTP client information
Syntax show ntp Defaults None Access All
Show ntp
Link DWS-1008 CLI Manual 162
Show snmp counters
Syntax show snmp counters Defaults None Access Enabled
Show snmp community
Show snmp notify profile
Defaults None Access Enabled See Also
Show snmp status
Show snmp usm
Show timedate
Syntax show timedate Defaults None Access All
Show summertime
Syntax show summertime
Telnet
Syntax show timezone Defaults None Access All
Show timezone
DWS-1008#show timezone
DWS-1008#telnet
Clear sessions Show sessions Link DWS-1008 CLI Manual 167
Traceroute
Ping Link DWS-1008 CLI Manual 169
Password Users
Authentication
Local Authorization for
Web authorization
Clear accounting
User-glob
Syntax clear authentication admin user-glob
Clear authentication admin
Clear authentication console
Syntax clear authentication console user-glob
Removes an 802.1X authentication rule
Clear authentication dot1x
DWS-1008#clear authentication console Regina
Wired
Removes a MAC authentication rule
Clear authentication mac
Clear authentication proxy
Syntax clear authentication proxy ssid ssid-nameuser-glob
Clear location policy
Clear authentication web
Removes a rule from the location policy on a switch
Removes a WebAAA rule
Syntax clear mac-user mac-addr
Clear mac-user
Clear mac-user attr
Syntax clear mac-user mac-addrattr attribute-name
Clear mac-user group
Set mac-user attr Show aaa
Syntax clear mac-user mac-addrgroup
Syntax clear mac-usergroup group-name
Clear mac-usergroup
Clear mac-usergroup attr
Group-name Name of an existing MAC user group
Clear mac-usergroup Set mac-usergroup attr Show aaa
Username Username of a user with a password
Clear user
Syntax clear user username
Clear user group
Username Username of a user with a password
Clear user attr
Syntax clear user username attr attribute-name
Syntax clear usergroup group-name
Clear usergroup
Clear usergroup Set user group Show aaa
Group-name Name of an existing user group
Set accounting admin console
Clear usergroup attr
Syntax clear usergroup group-nameattr attribute-name
Method1 method2 method3 method4
Set accounting dot1x mac web last-resort
Clear accounting Show accounting statistics
Link DWS-1008 CLI Manual 183
Web
Wired
Mac
Start-stop
Set accounting system
Syntax set accounting system method1 method2 method3 method4
Set authentication admin
Link DWS-1008 CLI Manual 186
Set authentication console
Link DWS-1008 CLI Manual 187
Link DWS-1008 CLI Manual 188
Set authentication dot1x
Authentication port
For details, see User Globs on Link DWS-1008 CLI Manual 189
Been authenticated
Bonded
Protocol
Access Enabled
Set authentication mac
Authentication port
Link DWS-1008 CLI Manual 192
Access Enabled
Set authentication proxy
User-glob Single user or a set of users
Set authentication web
See Also
Set location policy
User operator user-glob
Before rule-number
Modify rule-number
DWS-1008#set location policy deny if user eq *.theirfirm.com
Syntax set mac-user mac-addrgroup group-name
Set mac-user
Set mac-user attr
Syntax set mac-user mac-addrattr attribute-name value
Link DWS-1008 CLI Manual 201
Attribute Description Valid Values
Link DWS-1008 CLI Manual 202
YY/MM/DD-HHMM
Link DWS-1008 CLI Manual 203
Time-of-day tu1000-1600,th1000-1600
Clear mac-user attr Show aaa Link DWS-1008 CLI Manual 204
Set mac-usergroup attr
Syntax set mac-usergroup group-nameattr attribute-name value
Set user
Syntax set user username password encrypted string
DWS-1008#set user Nin password 29Jan04 See Also
Clear user Show aaa Link DWS-1008 CLI Manual 206
Set user attr
Clear user attr Show aaa Link DWS-1008 CLI Manual 207
Syntax set user username group group-name
Set user group
Set usergroup
Clear user group Show aaa
DWS-1008#set web-portal disable
Syntax set web-portal enable disable
Defaults Enabled Access Enabled
Set web-portal
Displays all current AAA settings
Syntax show aaa Defaults None Access Enabled
Show aaa
Acctport
Show accounting statistics
DWS-1008#show accounting statistics
AAAACCTSVCATTR=2
Show location policy
Clear accounting Set accounting admin console Show aaa
Syntax show location policy Defaults None Access Enabled
DWS-1008show location policy
PKCS#12 Certificate
Encryption Keys
PKCS#7 Certificates
Self-Signed Certificate
Crypto ca-certificate
Syntax crypto ca-certificate admin eap web
Admin
PEM-formatted-certificate
Crypto certificate
Begin Certificate
Crypto generate key
Ssh
Syntax crypto generate request admin eap web admin Eap Web
Crypto generate request
String
Are supported on your network. This field is required
DWS-1008#crypto generate request admin
Alphanumeric characters with no spaces
With no spaces
Begin Certificate Request
Syntax crypto generate self-signed admin eap web Admin
Crypto generate self-signed
END Certificate Request
DWS-1008#crypto generate self-signed admin
Name. It simply needs to be formatted like one
Crypto otp
Syntax crypto otp admin eap web one-time-password Admin
One-time-password
DWS-1008#crypto generate otp eap hap9iN#ss
File-location-url
Syntax crypto pkcs12 admin eap web file-location-url
Crypto pkcs12
DWS-1008#crypto otp eap hap9iN#ss
Table below describes the fields in the display
Show crypto ca-certificate
DWS-1008#show crypto ca-certificate
Fields Description
Show crypto certificate
DWS-1008#show crypto certificate eap
Show crypto key ssh
Syntax show crypto key domain Defaults None Access Enabled
Show crypto key domain
Crypto generate key Link DWS-1008 CLI Manual 226
Server Groups
Radius Client
Radius Servers
Radius Proxy
Clear radius
Clear radius client system-ip
Clear radius proxy port
Removes Radius proxy ports configured for third-party APs
Clear radius proxy client
Removes Radius proxy client entries for third-party APs
Syntax clear radius server server-name
Clear radius server
Clear server group
Syntax clear server group group-nameload-balance
Deadtime minutes
Timeout seconds
Set radius
Encrypted-key string
Encrypted-key-No key
Syntax set radius client system-ip
Set radius client system-ip
Set radius proxy client
Clear radius client system-ip Set system ip-address
Set radius proxy port
Address
Author-password
Set radius server
Auth-port
Encrypted-key-No key Author-password-trapeze Access Enabled
Set server group
Configures a group of one to four Radius servers
Names of one or more configured Radius servers
Members
Set server group load-balance
Enable disable
Defaults Load balancing is disabled by default
Group-name Server group name of up to 32 characters
Reauthentication
Wired Authentication
Bonded Authentication
Port Control
Clear dot1x bonded-period
Clear dot1x max-req
Syntax clear dot1x max-req
Syntax clear dot1x port-control
Clear dot1x port-control
Clear dot1x quiet-period
Syntax clear dot1x quiet-period
Syntax clear dot1x reauth-max
Clear dot1x reauth-max
Clear dot1x reauth-period
Syntax clear dot1x reauth-period
Defaults The default is 30 seconds
Clear dot1x timeout auth-server
Clear dot1x timeout supplicant
Set dot1x timeout auth-server Show dot1x
Set dot1x authcontrol
Syntax set dot1x authcontrol enable disable enable Disable
Clear dot1x tx-period
Syntax clear dot1x tx-period
Set dot1x bonded-period
Syntax set dot1x bonded-period seconds
Set dot1x key-tx
Syntax set dot1x key-tx enable disable Enable
Defaults Key transmission is enabled by default
Set dot1x max-req
Set dot1x port-control
Clear dot1x max-req Show dot1x
Show port status Show dot1x Link DWS-1008 CLI Manual 248
Syntax set dot1x quiet-period seconds
Set dot1x quiet-period
Set dot1x reauth-max
Seconds Specify a value between 0 and 65,535
Set dot1x reauth-period
Set dot1x timeout auth-server
Syntax set dot1x timeout auth-server seconds
Syntax set dot1x reauth-period seconds
Clear dot1x timeout auth-server Show dot1x
Set dot1x timeout supplicant
Syntax set dot1x timeout supplicant seconds
Set dot1x tx-period
Set dot1x wep-rekey-period
Syntax set dot1X wep-rekey enable disable enable Disable
Set dot1x wep-rekey
Syntax set dot1x wep-rekey-period seconds
Displays a summary of the current configuration
Syntax show dot1x clients stats config clients Stats
Config
Show dot1x
Type the following command to display the 802.1X clients
DWS-1008#show dot1x config
Type the following command to display 802.1X statistics
DWS-1008# show dot1x stats
Link DWS-1008 CLI Manual 255
Clear sessions
Administrative Sessions
DWS-1008#clear sessions admin
Network Sessions
Clear sessions network
Show sessions
DWS-1008# show sessions console
DWS-1008# clear sessions admin
SSH
DWS-1008# show sessions telnet
Mac-addr
Show sessions network
Clear sessions
Link DWS-1008 CLI Manual 260
Verbose
Show sessions network command
Session-id
Show sessions network session-id display
DWS-1008# show sessions network mac-addr 00055d7e981a
DWS-1008# show sessions network user E
DWS-1008# show sessions network verbose
Ssid
DWS-1008#show sessions network session-id
Active
LAST-RESORT
Additional show sessions network verbose Output
Link DWS-1008 CLI Manual 264
Show sessions network session-id Output
Link DWS-1008 CLI Manual 265
Link DWS-1008 CLI Manual 266
Permitted Vendor List
Rogue Information
Countermeasures
Permitted Ssid List
Syntax clear rfdetect attack-list mac-addr
Clear rfdetect attack-list
Clear rfdetect ignore
Syntax clear rfdetect ignore mac-addr
Clear rfdetect ssid-list
Clear rfdetect vendor-list
Syntax clear rfdetect ssid-list ssid-name
Syntax set rfdetect attack-list mac-addr
Set rfdetect attack-list
Set rfdetect black-list
Syntax set rfdetect black-list mac-addr
Syntax set rfdetect ignore mac-addr
Set rfdetect ignore
Set rfdetect black-list Show rfdetect black-list
Mac-addr Bssid MAC address of the device to ignore
Set rfdetect log
Syntax set rfdetect log enable disable Enable
Syntax set rfdetect signature enable disable Enable
Set rfdetect signature
Set rfdetect ssid-list
Syntax set rfdetect ssid-list ssid-name
Set rfdetect vendor-list
Show rfdetect attack-list
Link DWS-1008 CLI Manual 274
DWS-1008# show rfdetect attack-list
Show rfdetect black-list
Show rfdetect clients
DWS-1008# show rfdetect black-list
AP MAC
DWS-1008# show rfdetect clients
Total number of entries Client MAC
DWS-1008#show rfdetect clients mac 000c4163fd6d
Bssid
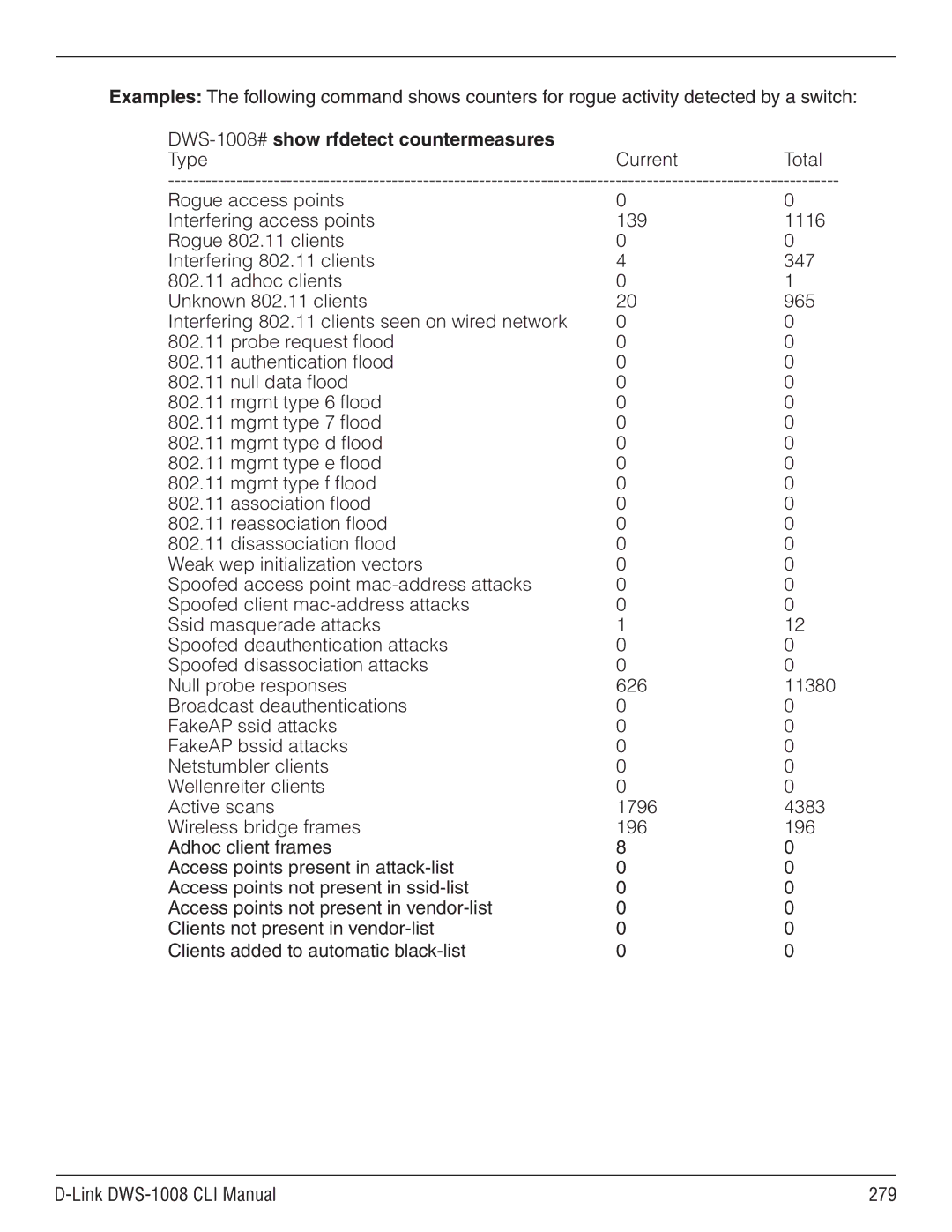
Show rfdetect countermeasures
Rssi
Link DWS-1008 CLI Manual 277
DWS-1008# show rfdetect countermeasures
Syntax show rfdetect counters Defaults None Access Enabled
Show rfdetect counters
Link DWS-1008 CLI Manual 278
DWS-1008#show rfdetect countermeasures
Type Current
Show rfdetect data
Displays information about the APs detected by a switch
Syntax show rfdetect data Defaults None Access Enabled
Vendor Type Port/Radio Flags
Syntax show rfdetect ignore Defaults None Access Enabled
Show rfdetect ignore
Show rfdetect visible
Syntax show rfdetect ssid-list Defaults None Access Enabled
Show rfdetect ssid-list
Show rfdetect vendor-list
Showapdapstatus command
Show rfdetect visible
Radio
Test rflink
Show rfdetect data
Syntax test rflink mac mac-addr session-id session-id
RTT micro-secs
DWS-1008# test rflink mac 000e9bbfad13
Rssi SNR
976
Software Version
Boot Settings
Configuration File
File Management
Dir command output
Backup
Syntax backup system tftp/ip-addr/filenameall critical
Critical
Clear boot backup-configuration
Clear boot config
Syntax clear boot config Defaults None Access Enabled
DWS-1008#clear boot config
DWS-1008#reset system force
Copy
DWS-1008#copy tftp//10.1.1.1/closetmx closetmx
Delete Dir Link DWS-1008 CLI Manual 290
For example subdira/filea
Delete
Syntax delete url
Copy Dir Link DWS-1008 CLI Manual 291
Dir
Boot0
Boot1
File
Page
This command may take up to 20 seconds
Install soda agent
DWS-1008#install soda agent soda.ZIP agent-directory sp1
Table below describes the fields in the dir output
Backupconfigs/configc
Load config
Syntax load config url
DWS-1008#load config
Md5
Syntax md5 boot0 boot1filename
DWS-1008#md5 boot0MX040003.020
Mkdir
Syntax reset system force
Reset system
Restarts a switch and reboots the software
Dir Rmdir
Restore
DWS-1008#reset system
Save config Show boot Show version
Rmdir
DWS-1008#restore system tftp/10.10.20.9/sysabak
Backup
Removes a subdirectory from nonvolatile storage
DWS-1008#save config
Save config
Syntax save config filename
DWS-1008#save config testconfig1
Syntax set boot backup-configuration filename
Set boot backup-configuration
Set boot configuration-file
Syntax set boot configuration-file filename
Syntax set boot partition boot0 boot1 Boot0
Set boot partition
Show boot
Boot1
Clear boot config Reset system Set boot configuration-file
Show config
Table below describes the fields in the show boot output
Displays the configuration running on the switch
Spantree System Trace Vlan Vlan-fdb
DWS-1008#show config area vlan
Show version
Syntax show version details Details
DWS-1008#show version
DWS-1008#show version details
DWS-1008#uninstall soda agent agent-directory sp1
Uninstall soda agent
Syntax uninstall soda agent agent-directory directory
Table below describes the fields in the show version output
Access Point Commands
Clear ap dap radio
Clear dap boot-configuration
DWS-1008#clear dap 1 boot-configuration
DWS-1008#clear ap 3 radio
Clear radio-profile
DWS-1008#set radio-profile rp1 mode disable
DWS-1008#set radio-profile rptest mode disable
Syntax clear radio-profile name parameter
Clear service-profile
Restarts an access point
Reset ap dap
DWS-1008#set radio-profile rp6 mode disable
Syntax reset ap port-list dap dap-num
Syntax set dap auto Defaults None Access Enabled
Set dap auto
Link DWS-1008 CLI Manual 312
Enables the AP configuration profile
Set dap auto mode
Syntax set dap auto mode enable disable Enable
Disables the AP configuration profile
Syntax set dap auto persistent dap-num all
Set dap auto persistent
Set dap auto radiotype
Dap-num
Set ap dap bias
Set dap auto Set dap auto mode Set dap auto persistent
Low Defaults Access
Dap dap-num dap auto high
Dap dap-num dap auto enable disable Defaults Access Enabled
Set ap dap blink
Set dap boot-ip
Enables or disables the static IP address for the AP
Set dap boot-switch
Switch ip ip-addr
Link DWS-1008 CLI Manual 319
Syntax set ap port-list dap dap-num contact string
Set ap dap contact
Specifies contact information for an AP
Contact string
Set dap fingerprint
Syntax set dap dap-numfingerprint hex
Set ap dap force-image-download
Force-image-download enable
Force-image-download disable
Dap auto
Syntax set ap port-list dap dap-num auto group name
Defaults AP access points are not grouped by default
Set ap dap group
Ap port-list dap dap-num dap auto
Syntax set ap port-list dap dap-num location string
Set ap dap location
Specifies location information for an AP
Ap port-list Dap dap-num location string
Syntax set ap port-list dap dap-num name name
Set ap dap name
Set ap dap radio antenna-location
Ap port-list
Outdoors
Set ap dap radio antennatype
Indoors
Ap port-list Dap dap-num
Power-level
Set ap dap radio auto-tune max-power
Configuration template
Radio 1 of the DWL-8220AP
Set ap dap radio channel
Sets an DWS-8220AP radio’s channel
Dap dap-num radio 1 radio Channel-number
Set ap dap radio mode
Radio 1 radio 2 enable disable
Dap dap-num dap auto
Set ap dap radio radio-profile
Mode enable
Mode disable
Radio-profile name
Access Enabled
Defaults By default, encryption keys are optional
Set dap security
Dap auto enable disable Defaults Access Enabled
Set ap dap upgrade-firmware
Set dap fingerprint Show ap dap config Show ap dap status
DWS-1008#set ap 2 upgrade-firmware disable
Set radio-profile active-scan
Set radio-profile auto-tune channel-config
Syntax set radio-profile name active-scan enable disable
Link DWS-1008 CLI Manual 334
Name
Enable Disable No-client
Set radio-profile auto-tune channel-holddown
Link DWS-1008 CLI Manual 335
Set radio-profile auto-tune channel-interval
Name Rate
Name Radio profile name
Set radio-profile auto-tune channel-lockdown
Syntax set radio-profile name auto-tune channel-lockdown
Set radio-profile auto-tune power-config
Set radio-profile auto-tune power-interval
Set radio-profile auto-tune power-lockdown
Set radio-profile auto-tune power-ramp-interval
Syntax set radio-profile name auto-tune power-lockdown
Defaults The default interval is 60 seconds
Set radio-profile beacon-interval
Syntax set radio-profile name beacon-interval interval
Rogue
Configured
Set radio-profile countermeasures
None
Set radio-profile dtim-interval
Set radio-profile frag-threshold
Syntax set radio-profile name frag-threshold threshold
Syntax set radio-profile name max-rx-lifetime time
Set radio-profile max-rx-lifetime
Set radio-profile max-tx-lifetime
Syntax set radio-profile name max-tx-lifetime time
Set radio-profile mode
Syntax set radio-profile name mode enable disable
Link DWS-1008 CLI Manual 347
MMS
Access Enabled
Long
Set radio-profile preamble-length
Syntax set radio-profile name preamble-length long short
Short
Syntax set radio-profile name qos-mode svp wmm
Set radio-profile qos-mode
Set radio-profile rfid-mode
Svp
Defaults The default is disable Access Enabled
Syntax set radio-profile name rfid-mode enable disable
Enables radios to function as asset location receivers
Set radio-profile rts-threshold
DWS-1008#set radio-profile rp1 rts-threshold
Table Defaults for Radio Profile Parameters
Link DWS-1008 CLI Manual 353
Link DWS-1008 CLI Manual 354
Portal-acl setting
Link DWS-1008 CLI Manual 355
Set radio-profile wmm-powersave
Syntax set service-profile name attr attribute-name value
Set service-profile attr
Syntax set radio-profile name wmm-powersave enable disable
Link DWS-1008 CLI Manual 357
Access Enabled
Name Service profile name
Set service-profile auth-dot1x
Syntax set service-profile name auth-dot1x enable disable
Enables 802.1X authentication of WPA clients
Set service-profile auth-fallthru
Enables PSK authentication of WPA clients
Set service-profile auth-psk
Syntax set service-profile name auth-psk enable disable
Disables PSK authentication of WPA clients
Syntax set service-profile name beacon enable disable
Set service-profile beacon
Set service-profile cac-mode
Syntax set service-profile name cac-mode none session
CAC is not used
Set service-profile cac-session
Syntax set service-profile name cac-session max-sessions
Session
Enables Ccmp encryption for WPA clients
Set service-profile cipher-ccmp
Syntax set service-profile name cipher-ccmp enable disable
Disables Ccmp encryption for WPA clients
Enables 104-bit WEP encryption for WPA clients
Set service-profile cipher-tkip
Set service-profile cipher-wep104
Disables 104-bit WEP encryption for WPA clients
Set service-profile cipher-wep40
Defaults 104-bit WEP encryption is disabled by default
Sets the Class-of-Service CoS level for static CoS
Set service-profile cos
Defaults 40-bit WEP encryption is disabled by default
Syntax set service-profile name cos level
Enables Dhcp Restrict
Set service-profile dhcp-restrict
Set service-profile static-cos Show service-profile
Disables Dhcp Restrict
Enables keepalives
Set service-profile idle-client-probing
Set service-profile keep-initial-vlan
Disables keepalives
Defaults This option is disabled by default
Set service-profile long-retry-count
Configures radios to reassign a roamed user’s Vlan
Syntax set service-profile name long-retry-count threshold
Set service-profile no-broadcast
Syntax set service-profile name no-broadcast enable disable
Link DWS-1008 CLI Manual 371
Set service-profile proxy-arp
Enable Disable Defaults Access Enabled
Syntax set service-profile name proxy-arp enable disable
Set service-profile psk-phrase
Defaults Proxy ARP is disabled by default
Syntax set service-profile name psk-phrase passphrase
Set service-profile psk-raw
Syntax set service-profile name psk-raw hex
Enables the RSN IE
Set service-profile rsn-ie
Syntax set service-profile name rsn-ie enable disable
Disables the RSN IE
Enables shared-key authentication, in a service profile
Set service-profile shared-key-auth
Set service-profile short-retry-count
Syntax set service-profile name short-retry-count threshold
Set service-profile soda agent-directory
Set service-profile soda enforce-checks
Set service-profile soda mode Link DWS-1008 CLI Manual 378
Set service-profile soda failure-page
Syntax set service-profile name soda failure-page
Set service-profile soda logout-page
Syntax set service-profile name soda logout-page
Syntax set service-profile name soda mode enable disable
Set service-profile soda mode
Set service-profile soda remediation-acl
Defaults Disabled Access Enabled
Set service-profile soda success-page
Syntax set service-profile name soda success-page
Syntax set service-profile name ssid-name ssid-name
Set service-profile ssid-name
Configures the Ssid name in a service profile
Name Ssid-name
Clear
Set service-profile ssid-type
Syntax set service-profile name ssid-type clear crypto
Crypto
Enables static CoS on the service profile
Set service-profile static-cos
Syntax set service-profile name static-cos enable disable
Disables static CoS on the service profile
Syntax set service-profile name tkip-mc-time wait-time
Set service-profile tkip-mc-time
Set service-profile transmit-rates
Link DWS-1008 CLI Manual 386
Mandantory rate-list
Disabled rate-list
11a 11b 11g
Beacon-rate rate
Set service-profile user-idle-timeout
Defaults This command has the following defaults
Syntax set service-profile name web-portal-acl aclname
Set service-profile web-portal-acl
Syntax set service-profile name user-idle-timeout seconds
Name Seconds
Syntax set service-profile name web-portal-form url
Set service-profile web-portal-form
Set service-profile auth-fallthru Show service-profile
Defaults The D-Link Web login page is served by default
Success change accepted
Set service-profile web-portal-session-timeout
Set service-profile wep active-multicast-index
Set service-profile wep active-unicast-index
Set service-profile wep key-index
Key-index num key value
Set service-profile wpa-ie
Syntax set service-profile name wpa-ie enable disable
DWS-1008#show ap config
Show ap dap config
Shows configuration information for radio
DWS-1008#show dap config
Following Table describes the fields in this display
Link DWS-1008 CLI Manual 397
Show ap dap counters
Shows statistics counters for radio
DWS-1008# show dap counters
Totl
Link DWS-1008 CLI Manual 399
Link DWS-1008 CLI Manual 400
Ccmp
MIC
Link DWS-1008 CLI Manual 402
Displays statistics for DWL-8220AP forwarding queues
DWS-1008#set service-profile sp2 wpa-ie enable
Show ap dap qos-stats
Clear
Show ap dap etherstats
Syntax show ap dap etherstats port-list dap-num
Link DWS-1008 CLI Manual 404
DWS-1008# show dap etherstats
Link DWS-1008 CLI Manual 405
Name Name of an AP group or Distributed AP group
Show ap dap group
Syntax show ap dap group name
Link DWS-1008 CLI Manual 406
DWS-1008# set service-profile sp2 wpa-ie enable
Link DWS-1008 CLI Manual 407
Radio2
Show ap dap status
Radio1
DWS-1008#show dap status
DWS-1008#show ap status
Link DWS-1008 CLI Manual 410
Link DWS-1008 CLI Manual 411
Radio1 Radio2 radio all Defaults Access
Show auto-tune attributes
Mp-num Dap-num
DWS-1008# show auto-tune attributes ap 2 radio
Show auto-tune neighbors
DWS-1008#show auto-tune neighbors ap 2 radio
Show dap boot-configuration
Syntax show dap boot-configuration dap-num
Link DWS-1008 CLI Manual 415
DWS-1008#show dap boot-configuration
DNS IP
Link DWS-1008 CLI Manual 416
DWS-1008#show dap connection
Show dap connection
Syntax show dap connection dap-num serial-id serial-ID
DAP
Show dap global
Syntax show dap global dap-num serial-id serial-ID
DWS-1008#show dap global
High
LOW
DWS-1008#show dap unconfigured
Show dap unconfigured
Syntax show dap unconfigured Defaults None Access Enabled
Link DWS-1008 CLI Manual 420
Syntax show radio-profile name ?
DWS-1008# show radio-profile default
Show radio-profile
Name Displays information about the named radio profile
Link DWS-1008 CLI Manual 422
See Also
Show service-profile
Name
Link DWS-1008 CLI Manual 425
Soda
Link DWS-1008 CLI Manual 426
Link DWS-1008 CLI Manual 427
Bridge Priority
Timers
STP State
Port Cost
Syntax clear spantree portcost port-list
Clear spantree portcost
Clear spantree portpri
Syntax clear spantree portpri port-list
Clear spantree portvlancost
Resets the cost for all VLANs
Resets the priority for all VLANs
Clear spantree portvlanpri
Clear spantree statistics
Syntax clear spantree statistics port-listvlan vlan-id
Show spantree statistics Link DWS-1008 CLI Manual 431
Set spantree backbonefast
Syntax set spantree backbonefast enable disable Enable
Set spantree
Vlan vlan-id Port port-list vlan-id
Set spantree fwddelay
Syntax set spantree fwddelay delay all vlan vlan-id Delay
Set spantree hello
Set spantree maxage
Syntax set spantree maxage aging-timeall vlan vlan-id
Set spantree portcost
Syntax set spantree portcost port-listcost cost
Set spantree portpri
Syntax set spantree portfast port port-listenable disable
Set spantree portfast
Syntax set spantree portpri port-listpriority value
Set spantree portvlancost
Set spantree portvlanpri
Changes the priority on all VLANs
Set spantree priority
Show spantree Link DWS-1008 CLI Manual 438
Show spantree
Syntax set spantree uplinkfast enable disable
Set spantree uplinkfast
Active
DWS-1008# show spantree vlan default
PVST+
Ieee
Show spantree blockedports Link DWS-1008 CLI Manual 441
Vlan ID
Show spantree backbonefast
Syntax show spantree backbonefast Defaults None Access All
DWS-1008#show spantree blockedports vlan default
Show spantree blockedports
DWS-1008#show spantree portfast
Show spantree portfast
Syntax show spantree portfast port-list
Set spantree portfast Link DWS-1008 CLI Manual 443
Syntax show spantree portvlancost port-list
Show spantree portvlancost
Show spantree statistics
Port-list List of ports
DWS-1008#show spantree statistics
False
Inactive
Topology change time Topology change detected
Num of similar BPDU’s to process Receivedinferiorbpdu
Link DWS-1008 CLI Manual 446
Link DWS-1008 CLI Manual 447
Clear spantree statistics
Defaults None Access All
Show spantree uplinkfast
Syntax show spantree uplinkfast vlan vlan-id
DWS-1008#show spantree uplinkfast
Set spantree uplinkfast Link DWS-1008 CLI Manual 449
Pseudo-querier
Igmp Snooping State
Proxy Reporting
Router Solicitation
Set igmp
Syntax set igmp enable disable vlan vlan-id
Clear igmp statistics
DWS-1008#clear igmp statistics
Set igmp oqi Set igmp qi Set igmp mrouter
Set igmp lmqi
Set igmp mrouter
Link DWS-1008 CLI Manual 452
Set igmp mrsol
Show igmp mrouter
Set igmp mrsol mrsi Link DWS-1008 CLI Manual 453
Syntax set igmp mrsol mrsi seconds vlan vlan-id
Set igmp mrsol mrsi
Set igmp oqi
Set igmp mrsol
Defaults Proxy reporting is enabled on all VLANs by default
Set igmp proxy-report
Show igmp Link DWS-1008 CLI Manual 455
Defaults The default query interval is 125 seconds
Set igmp qi
Syntax set igmp qi seconds vlan vlan-id qi seconds
Set igmp qri
Syntax set igmp qri tenth-secondsvlan vlan-id
Show igmp querier
Set igmp querier
Set igmp receiver
Link DWS-1008 CLI Manual 458
Show igmp receiver-table
Defaults The default robustness value for all VLANs is
Set igmp rv
Syntax set igmp rv num vlan vlan-id
Show igmp
DWS-1008# show igmp vlan orange
Dvmrp PIM
Link DWS-1008 CLI Manual 461
Show igmp mrouter
Syntax show igmp mrouter vlan vlan-id
Link DWS-1008 CLI Manual 462
DWS-1008# show igmp mrouter vlan orange
DWS-1008# show igmp querier vlan orange
DWS-1008#show igmp querier vlan default
Show igmp querier
DWS-1008#show igmp querier vlan red
DWS-1008# show igmp receiver-table vlan orange
Show igmp receiver-table
Group group-ip-addr/mask-length
Vlan orange Session Port Receiver-IP Receiver-MAC
Set igmp receiver
Show igmp statistics
DWS-1008#show igmp receiver-table group 237.255.255.0/24
Displays Igmp statistics
DWS-1008# show igmp statistics vlan orange
Link DWS-1008 CLI Manual 467
Clear igmp statistics Link DWS-1008 CLI Manual 468
Map Security ACLs
Create Security ACLs
Commit Security ACLs
Monitor Security ACLs
Clears all security ACLs
Clear security acl
Syntax clear security acl acl-name all editbuffer-index
DWS-1008#clear security acl acl133
Clear security acl map
Commits all security ACLs in the edit buffer
Commit security acl
Syntax commit security acl acl-name all
Link DWS-1008 CLI Manual 472
ACL
DWS-1008#show security acl
ACL table
Type Class Mapping
DWS-1008#show security acl info all editbuffer
Rollback security acl
Syntax rollback security acl acl-name all
ACL edit-buffer information for all
Set security acl
Before editbuffer-index modify editbuffer-index hits
Link DWS-1008 CLI Manual 475
Permit
Cos cos
Deny
Precedence
Precedence
Tos tos
Established
Hits
DWS-1008#set security acl ip acl123 deny 192.168.2.11
Set security acl map
Clear security acl Commit security acl Show security acl
Link DWS-1008 CLI Manual 479
Assigns the security ACL to traffic coming from the switch
Out
Set security acl hit-sample-rate
Syntax set security acl hit-sample-rate seconds
DWS-1008#set security acl hit-sample-rate
Displays a summary of the security ACLs that are mapped
Syntax show security acl Defaults None Access Enabled
Show security acl
DWS-1008# show security acl
Show security acl editbuffer
Show security acl info
Syntax show security acl hits Defaults None Access Enabled
Show security acl hits
Syntax show security acl info acl-name all editbuffer
Defaults None Access Enabled
Syntax show security acl map acl-name
Show security acl map
Show security acl resource-usage
DWS-1008#show security acl map acl111
DWS-1008#show security acl resource-usage
Link DWS-1008 CLI Manual 488
Link DWS-1008 CLI Manual 489
Syntax clear log trace Defaults None Access Enabled
Clear log trace
DWS-1008#clear log trace See Also
Deletes running trace commands and ends trace processes
Clear trace
Syntax clear trace trace-area all
Syntax save trace filename
Set trace authentication
Save trace
DWS-1008#save trace traces/trace1
Set trace dot1x
Set trace authorization
Traces authorization information
Clear trace Show trace
Set trace sm
Traces session manager activity
Link DWS-1008 CLI Manual 494
Show trace
Syntax show trace all
Syntax clear snoop filter-name
Clear snoop
Remote monitoring snooping
DWS-1008#clear snoop snoop1 See Also
Examples clear snoop map filter-namedap dap-numradio 1
Clear snoop map
Set snoop
Radio 1 of the AP
Channel eq neq channel
Frame-type eq neq beacon control data management
Probe
Bssid eq neq bssid
DWS-1008#set snoop snoop1 observer 10.10.30.2 snap-length
Defaults Snoop filters are unmapped by default
Set snoop map
Examples set snoop map filter-namedap dap-numradio 1
Disables the snoop filter
Set snoop mode
Enable stop-after num-pkts
Defaults Snoop filters are disabled by default
Show snoop info
Syntax show snoop Defaults None Access Enabled
Show snoop
Syntax show snoop filter-name
Syntax show snoop map filter-name
Show snoop map
Show snoop stats
DWS-1008#show snoop map snoop1 filter ‘snoop1’ mapping
Link DWS-1008 CLI Manual 504
Clear log
System Logs
Current
Set log
Buffer
Sessions
Enables messages to the specified target
Disables messages to the specified target
Show log config Clear log Link DWS-1008 CLI Manual 507
Set log mark
Severity level
Interval interval
Show log buffer
Facility facility-name
Matching string
DWS-1008#show log config
Show log config
Syntax show log config Defaults None Access Enabled
DWS-1008#show log buffer facility ?
Show log trace
Number-of-messages
Clear log Show log config Link DWS-1008 CLI Manual 512
DWS-1008#show log trace facility ?
DWS-1008#show log trace +5 facility Rogue
Boot Profile Management
Command Information
Booting
Diagnostics
Syntax autoboot on on OFF off
Autoboot
Boot
Boot autoboot
Boot boot FN=MX010101.020 DEV=boot1
Change
Syntax change
Syntax create
Creates a new boot profile
Create
Change Delete Next Show Link DWS-1008 CLI Manual 517
Dhcp
Removes the currently active boot profile
Syntax delete Defaults None
Change Create Next Show
Diag
Accesses the diagnostic mode
Syntax dir c d e f boot0 boot1
Syntax diag
Bload
Syntax fver c d e f boot0 boot1 filename
Fver
Bstrap
Command-name Boot prompt command
Boot fver boot1
Syntax help command-name
Boot help fver
Displays a list of the boot prompt commands
Syntax ls Defaults None
Help Link DWS-1008 CLI Manual 522
Syntax next Defaults None
Next
Syntax reset Defaults None
Reset
Resets a DWS-1008 switch’s hardware
Boot Link DWS-1008 CLI Manual 524
Syntax show Defaults None
Boot Type
Show
Boot Type
Change Create Delete Dhcp Next Link DWS-1008 CLI Manual 526
Version
Syntax version Defaults None
Test
Syntax test on on OFF off
Boot version
Dir Fver Link DWS-1008 CLI Manual 528